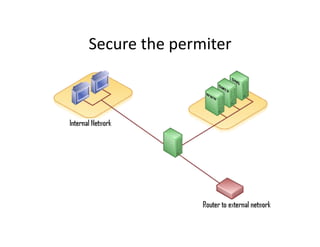
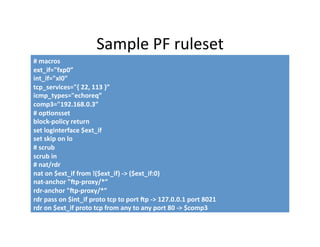
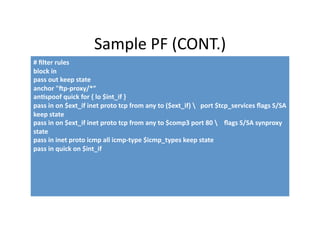
This document discusses strategies for maintaining security in open source systems. It recommends using open source operating systems that have security as a core focus, such as OpenBSD, and disabling unnecessary services. Firewalls are crucial for securing the perimeter, and intrusion detection systems like Snort can monitor for attacks. Logs should be analyzed to detect any issues and ensure the security of the system.