Embed presentation
Download to read offline



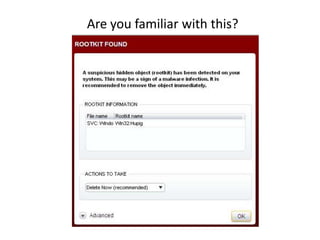





Deepsafe technology, a collaboration between Intel and McAfee, enhances security by leveraging hardware-assisted capabilities to monitor kernel-level threats beyond the operating system. It focuses on detecting elusive threats like rootkits and advanced persistent threats (APTs) at system boot-up, enabling real-time protection. This innovative approach aims to provide a deeper security footprint that traditional solutions cannot achieve.








