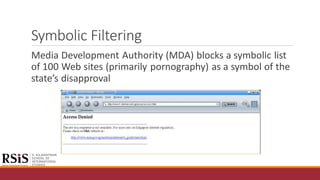
The document discusses Singapore's approach to internet governance, highlighting its regulation measures to maintain social values and public order, including censorship and licensing requirements for internet service providers and online news sites. It outlines the historical context, such as the 1964 racial riots, prompting content filtering to avoid national disunity. Furthermore, it emphasizes the balance between open access to the internet for innovation and the enforcement of laws to prevent harmful behavior and protect the community.




![Access should be denied …
… to content that "undermines public order and the nation's
security, denigrates race and religion, or erodes moral
values.“
… includes "pornography, deviant sexual practices, sexual
violence, child pornography, [and] bestiality.“
◦ Ministry of Information, Communications and the Arts,
Censorship Review Committee: Report of 2003 26](https://image.slidesharecdn.com/openinternetinsingapore-161015010258/85/Open-internet-in-singapore-7-320.jpg)