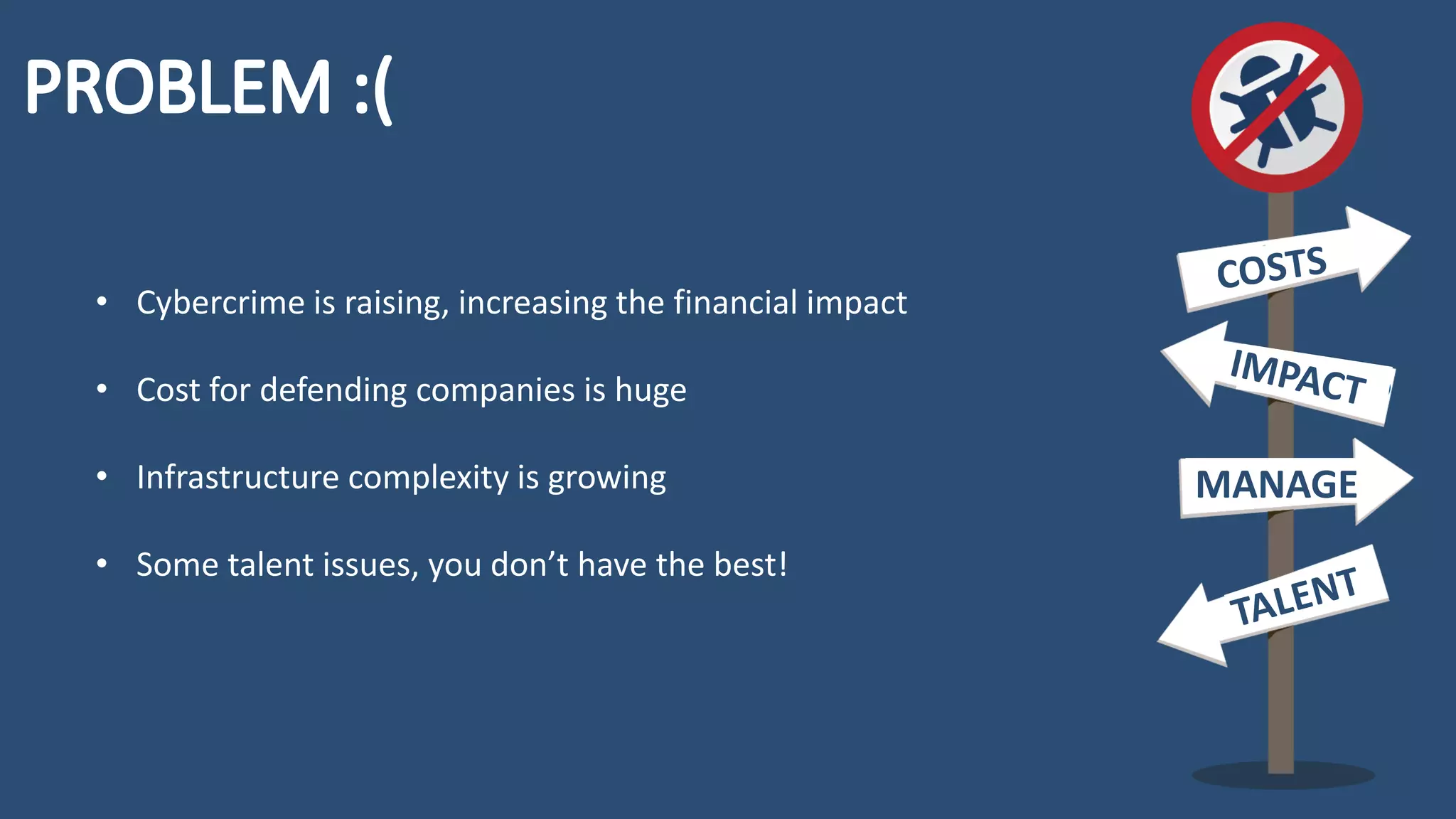
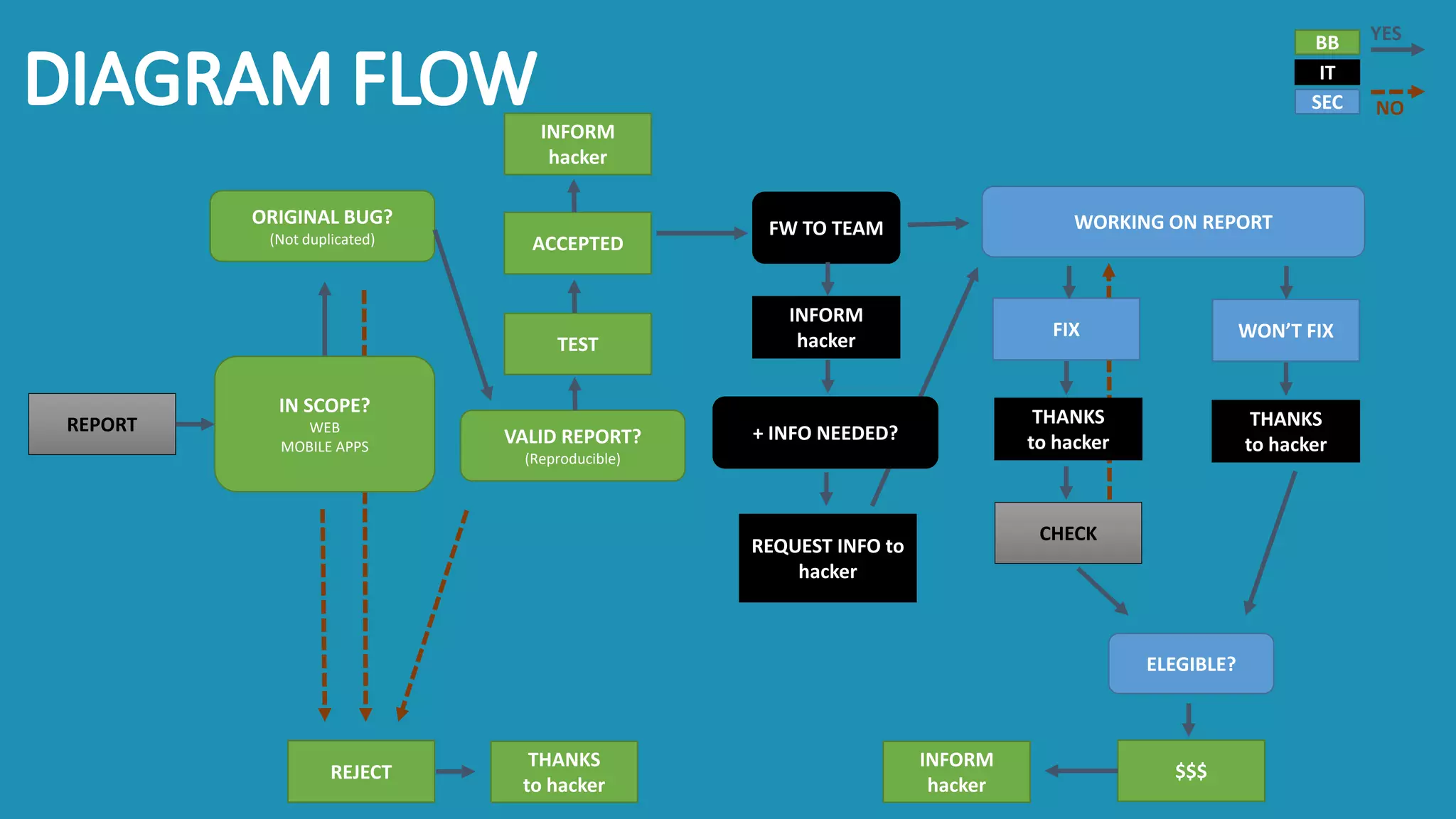
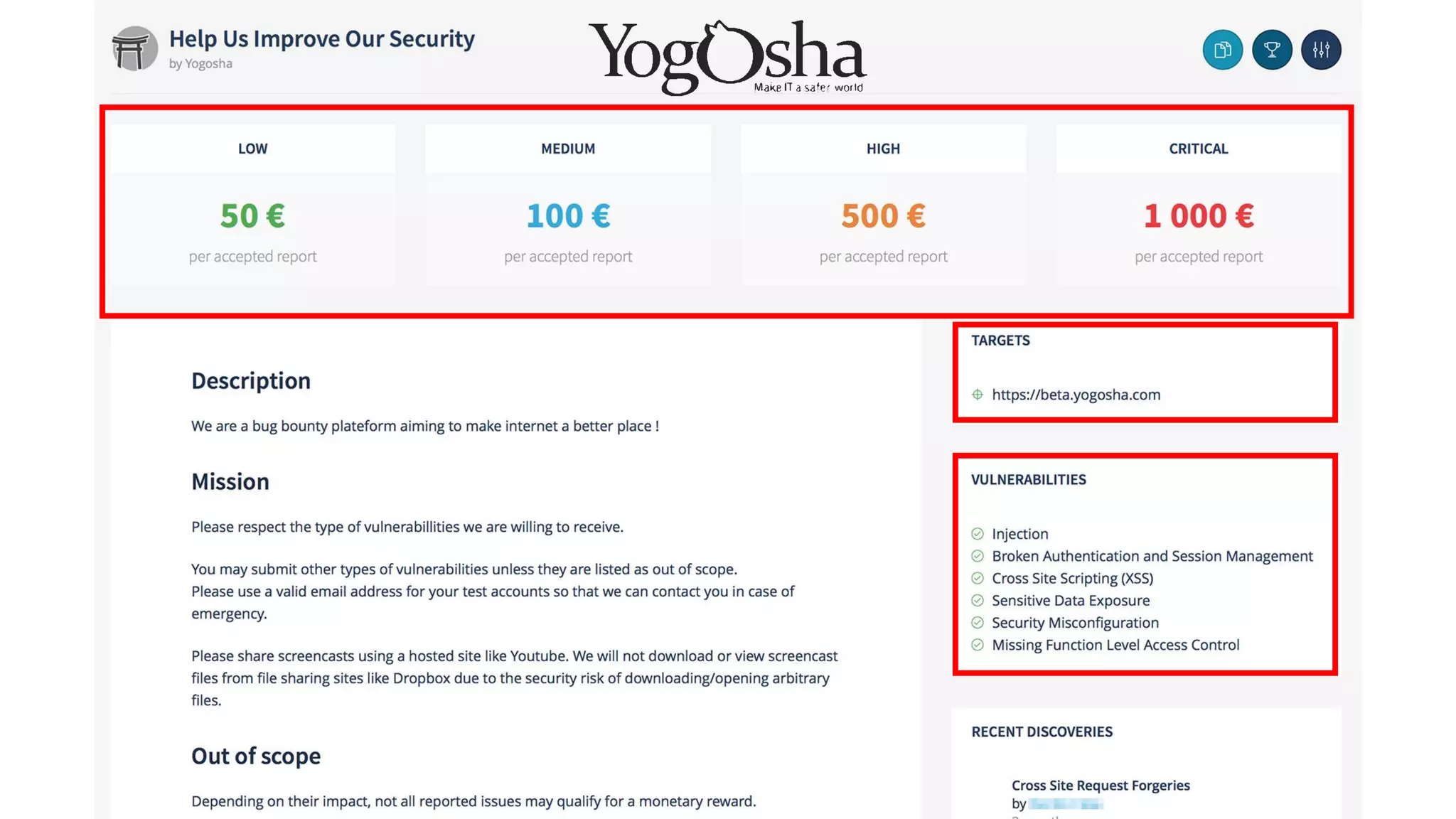
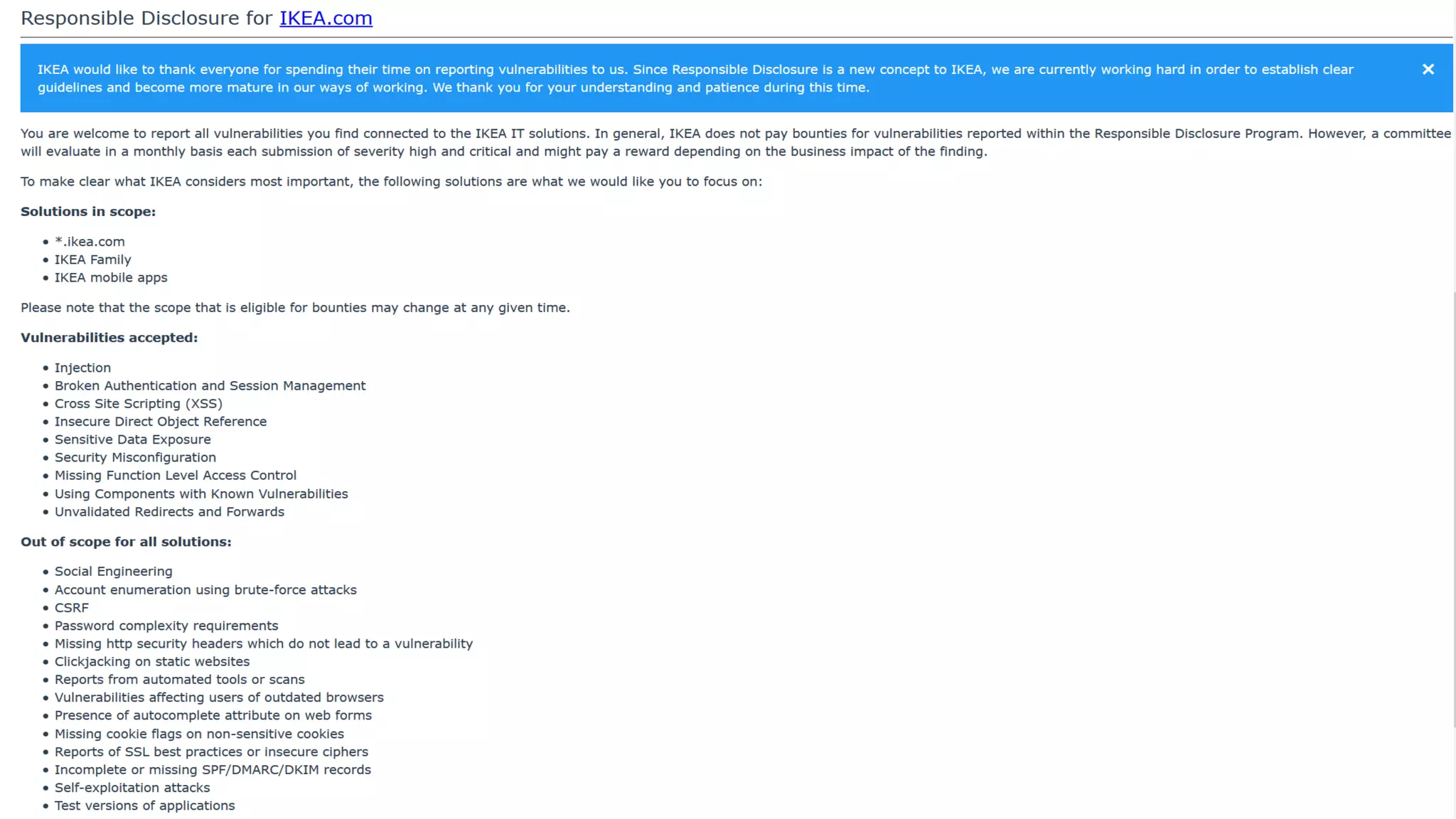
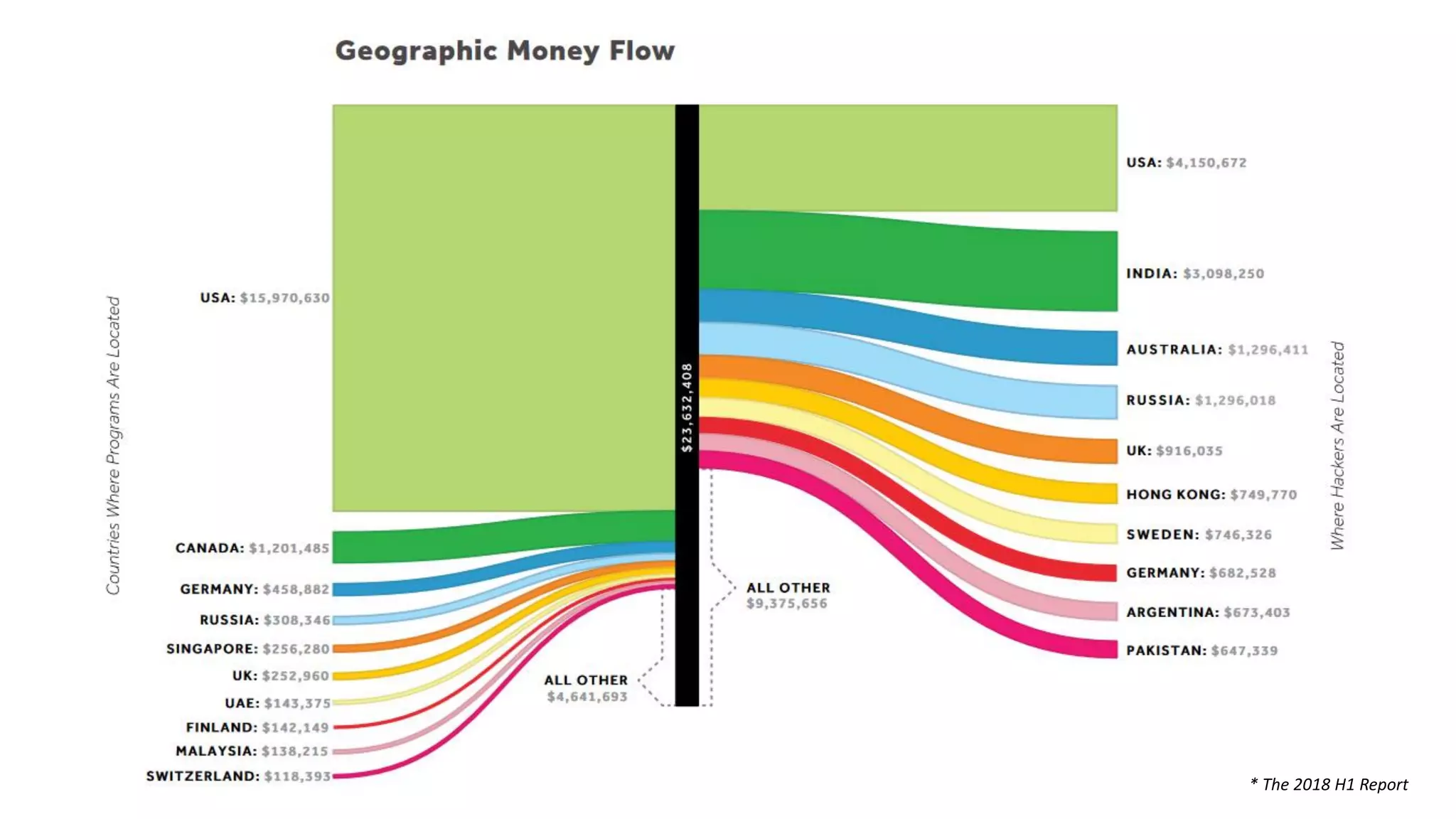
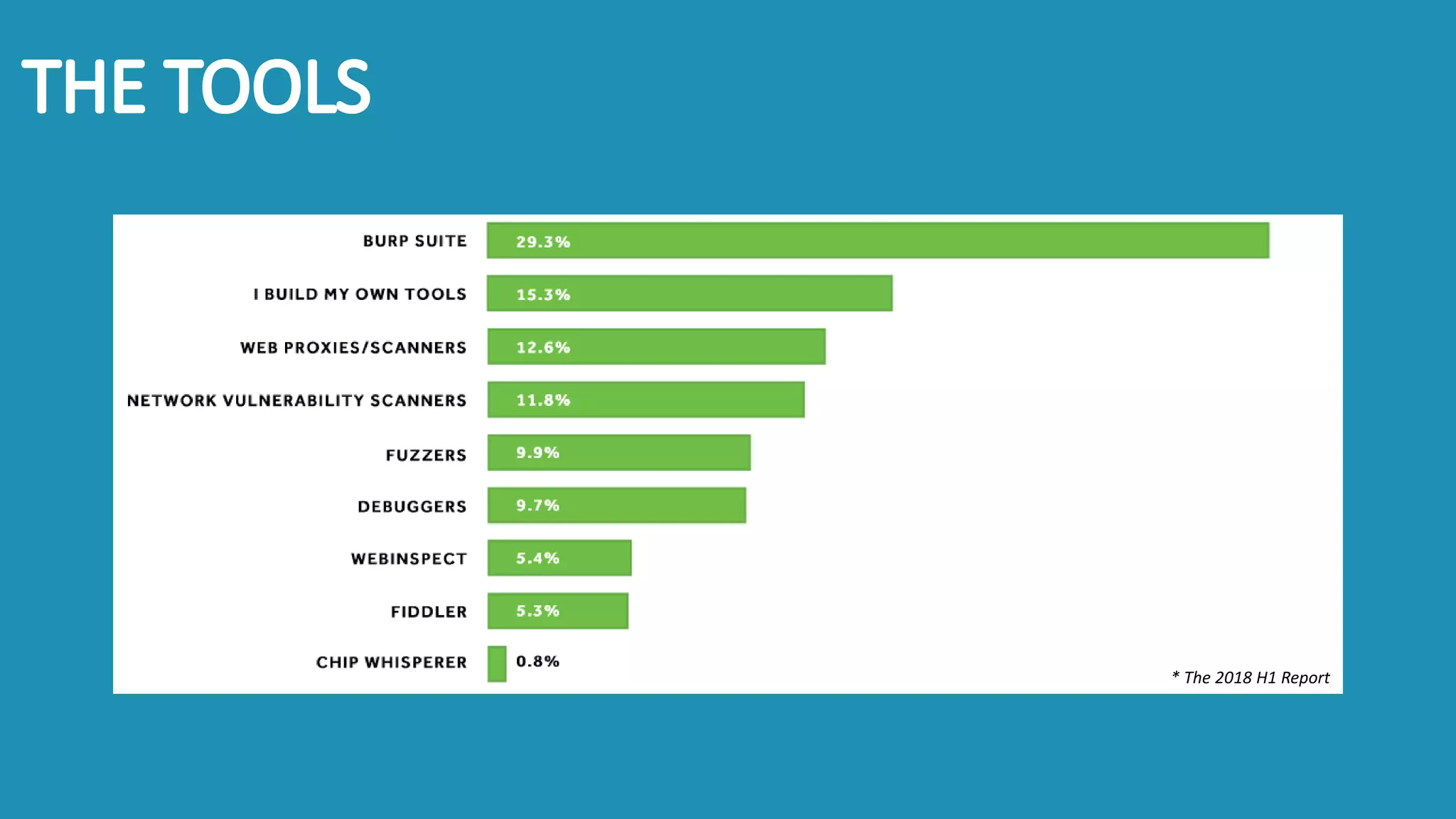
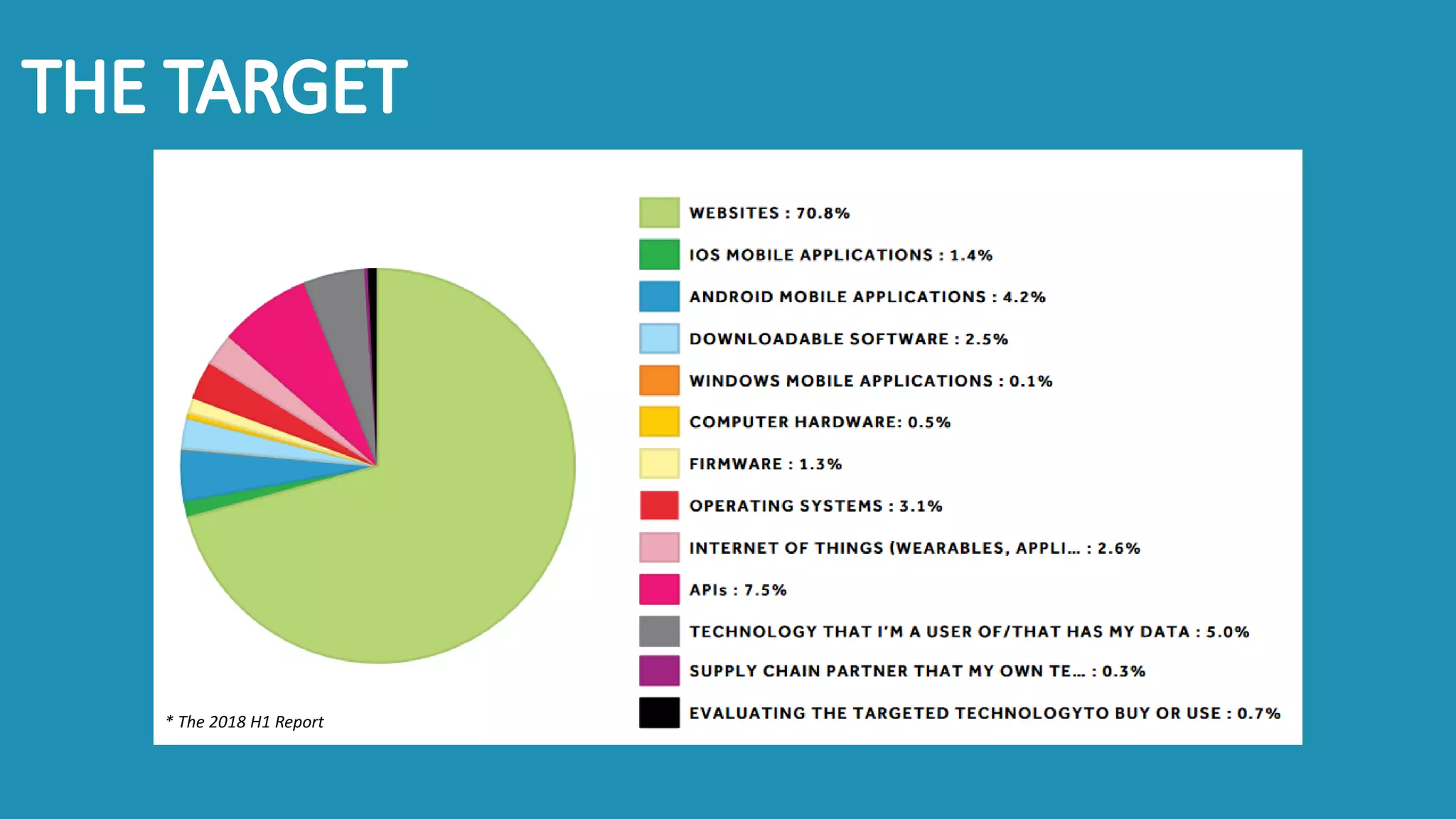
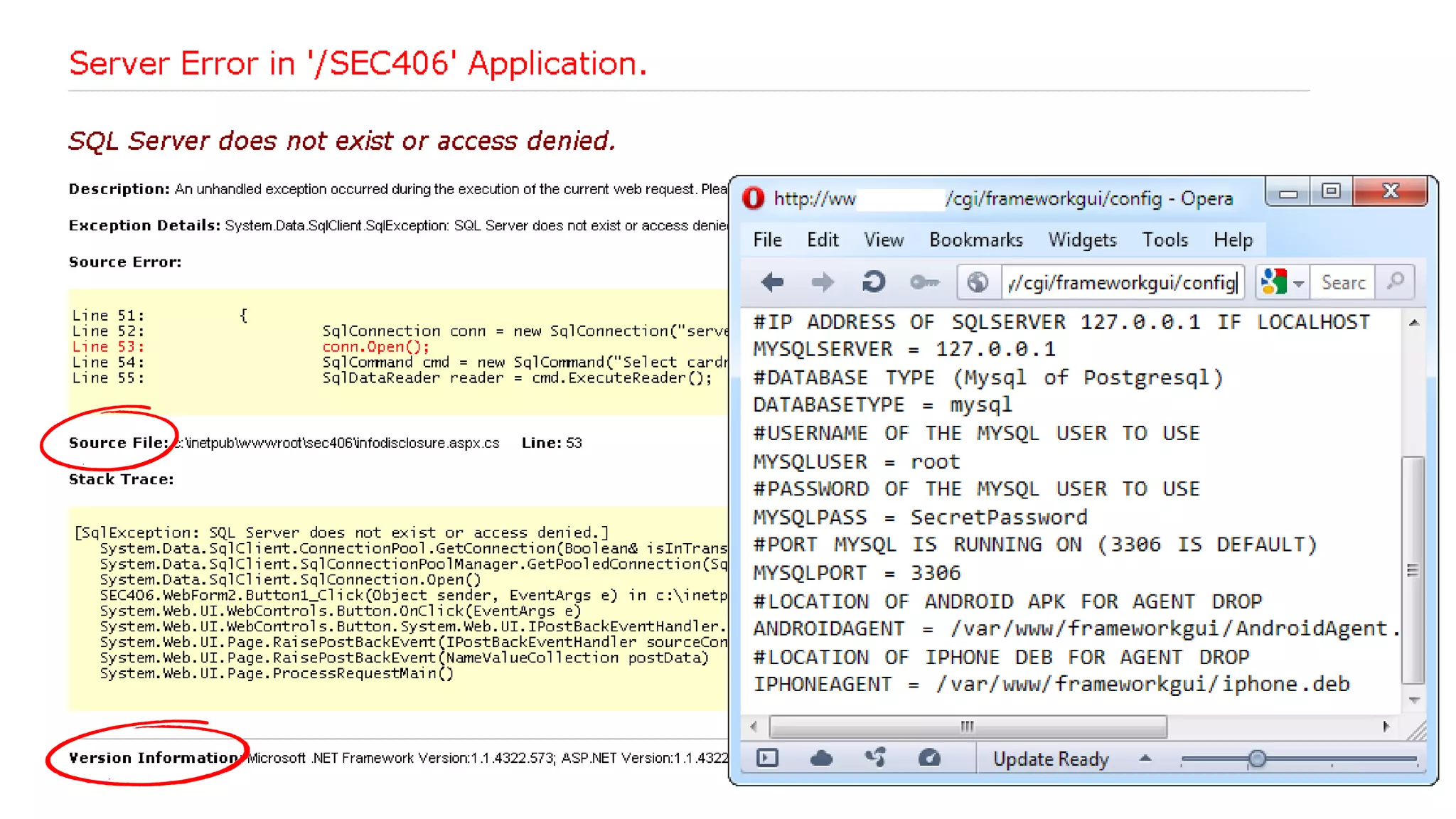
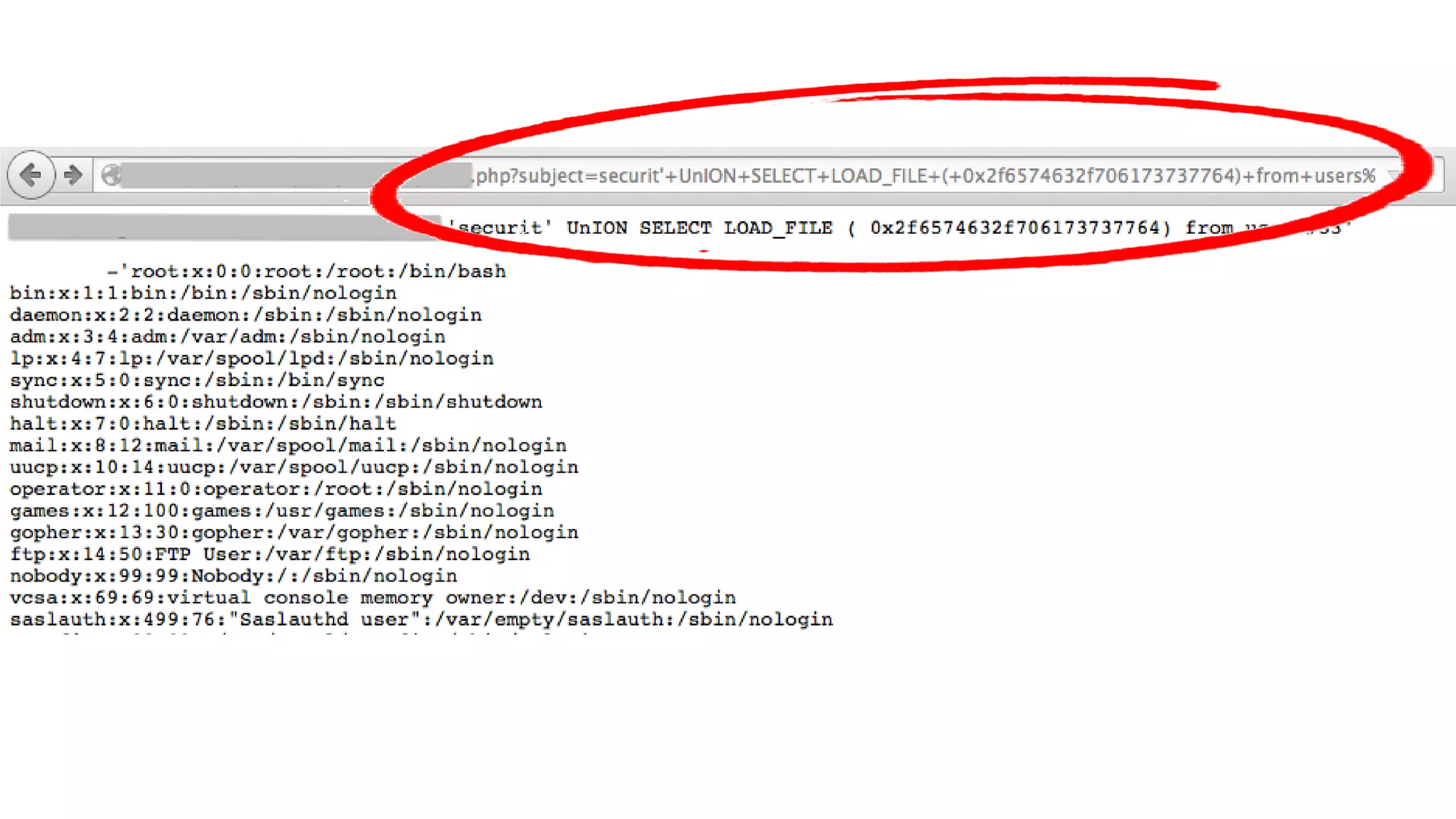
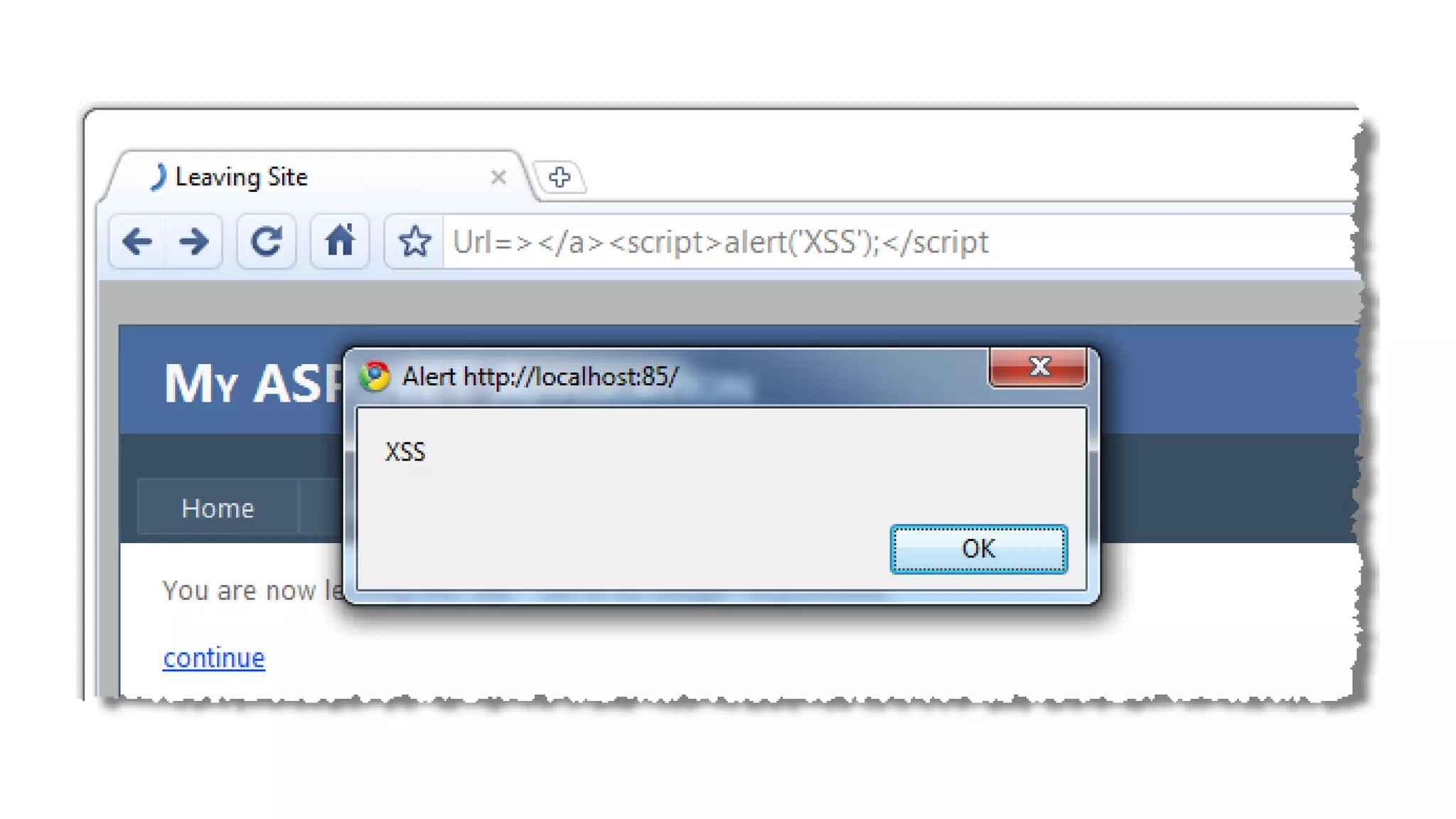
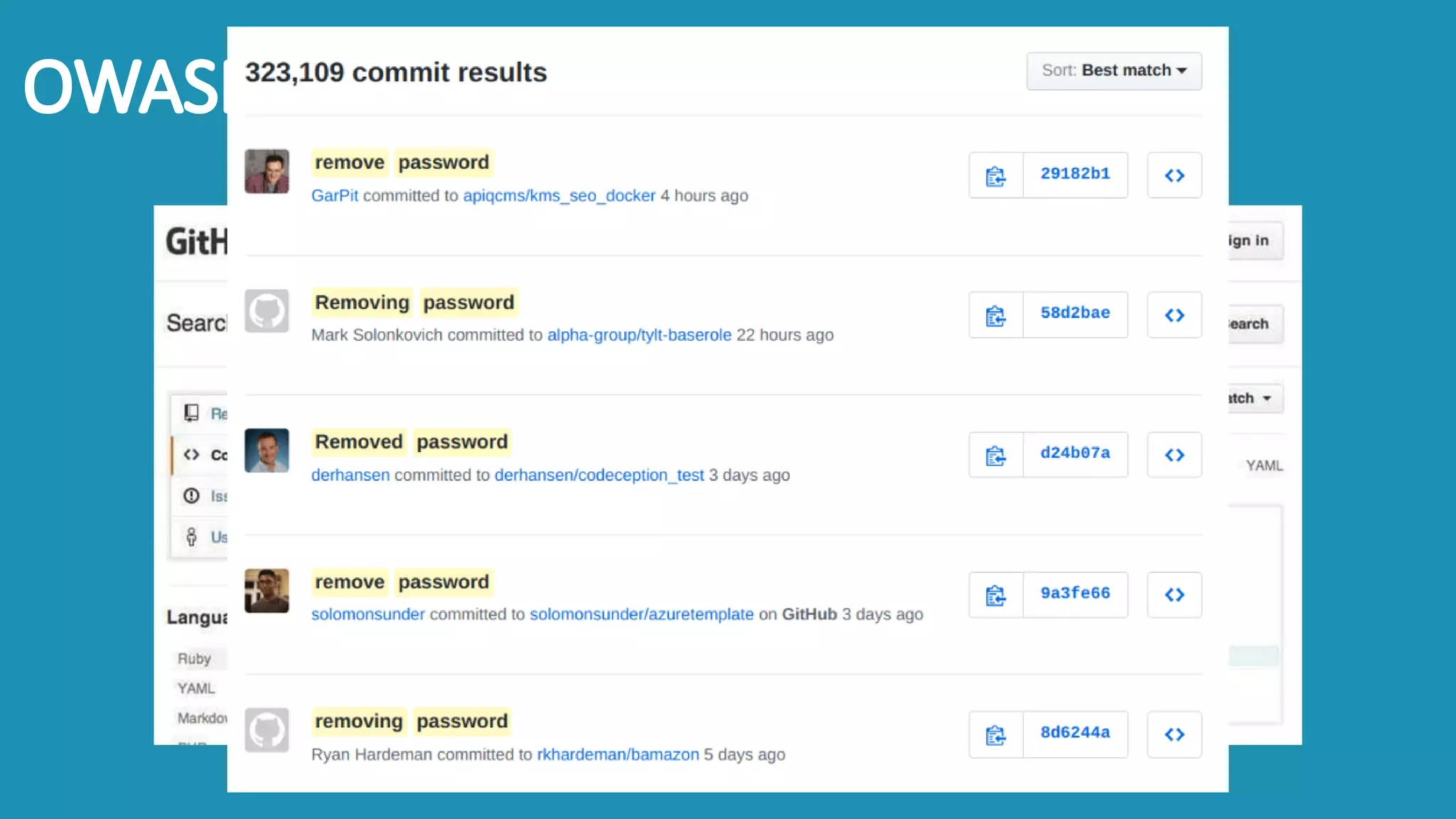
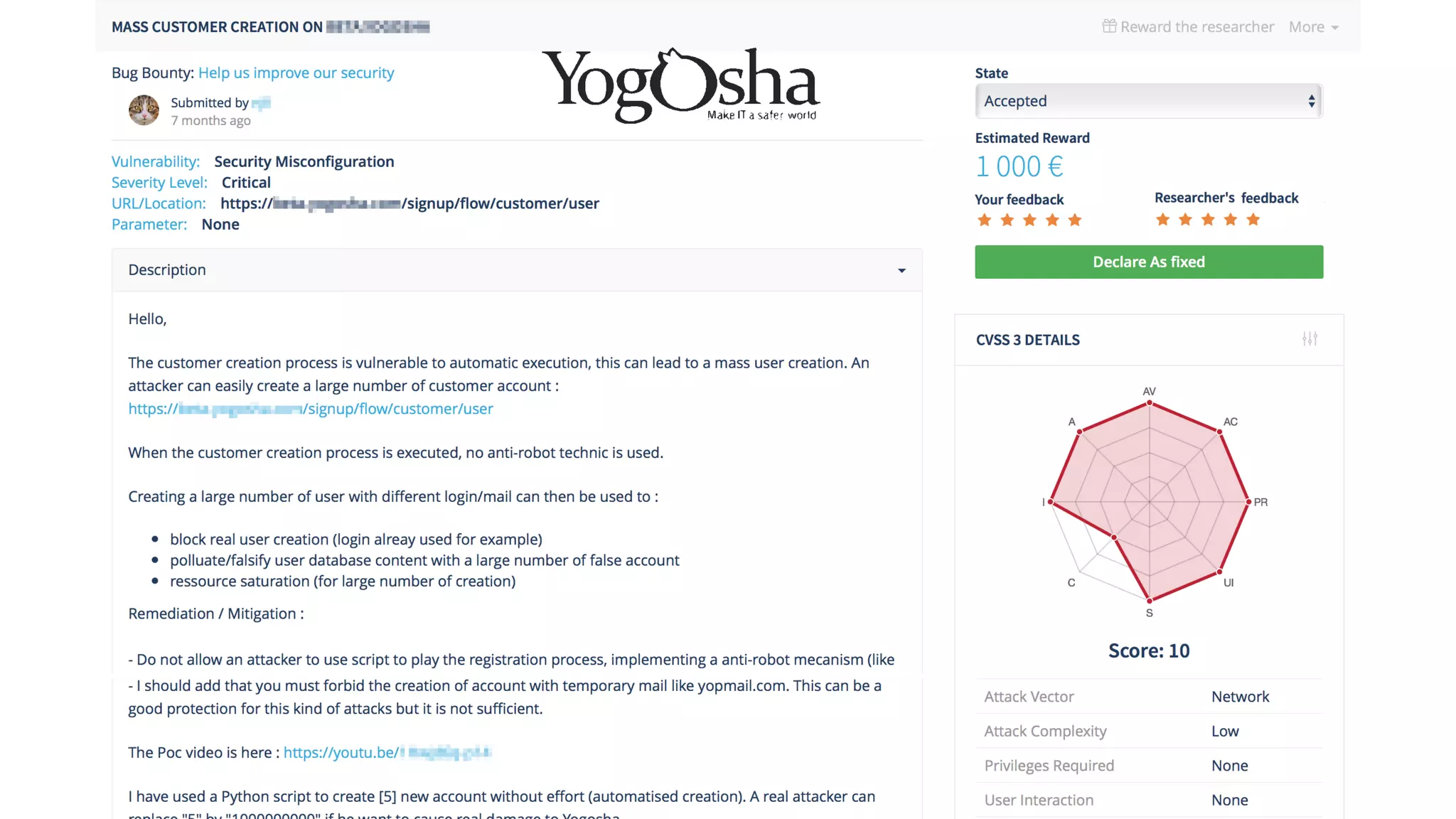
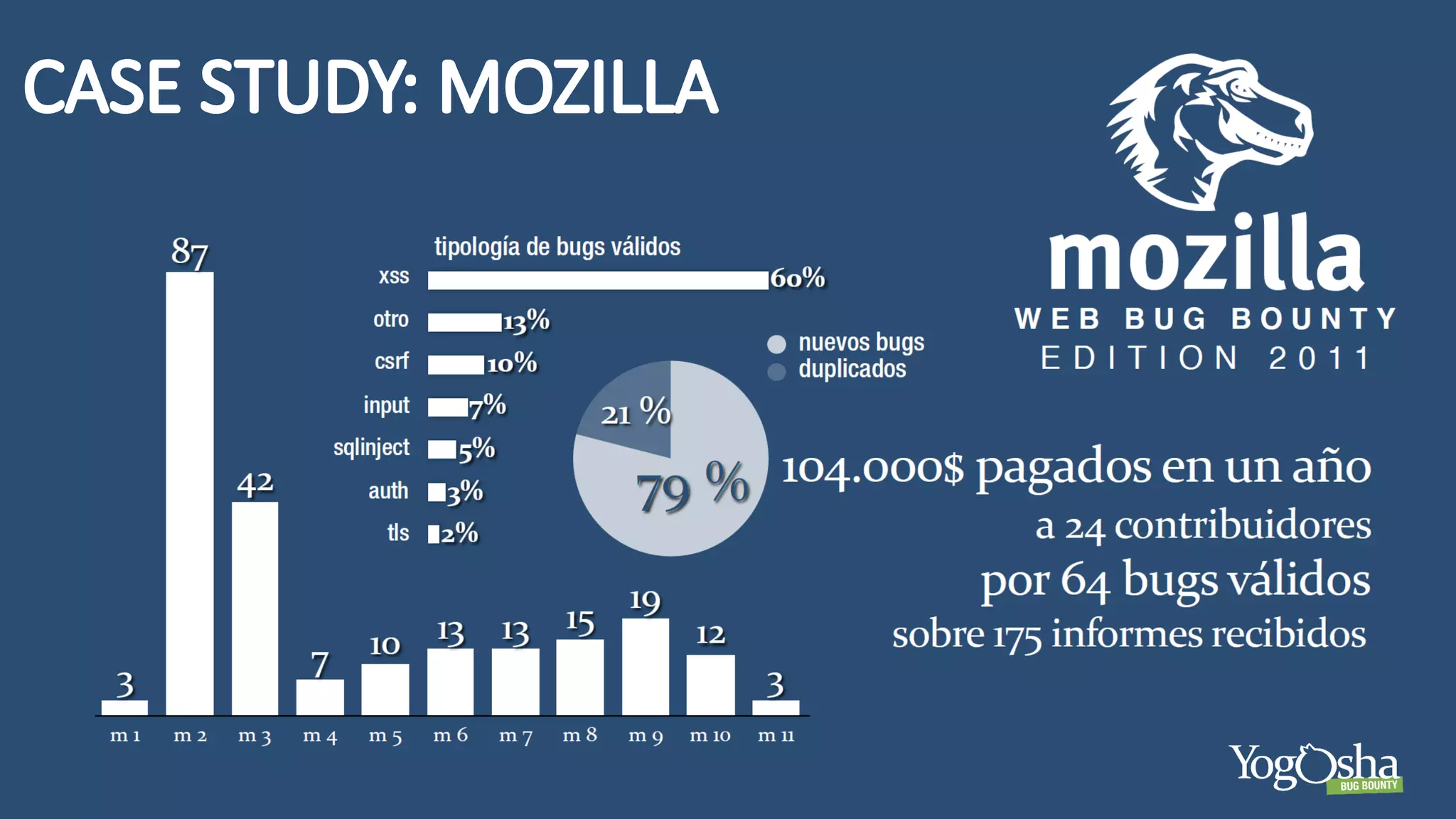
The document discusses the importance and management of bug bounty programs, emphasizing their role in improving company security amidst rising cybercrime and complex infrastructure. It outlines best practices for implementing such programs, including budget planning, setting criteria for payments, and ensuring responsible disclosure. The document also highlights the collaborative relationship between companies and hackers in enhancing cybersecurity.