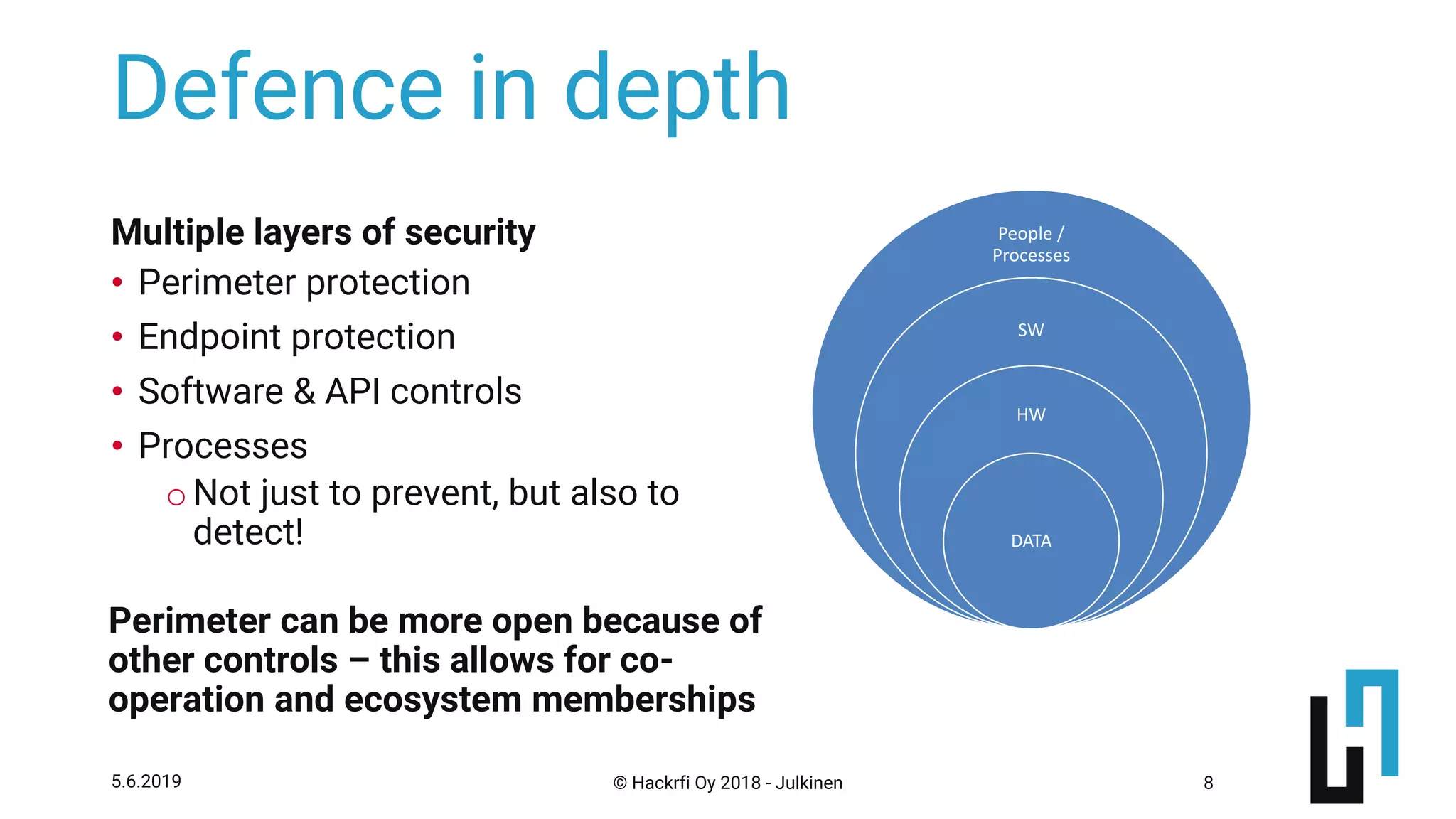
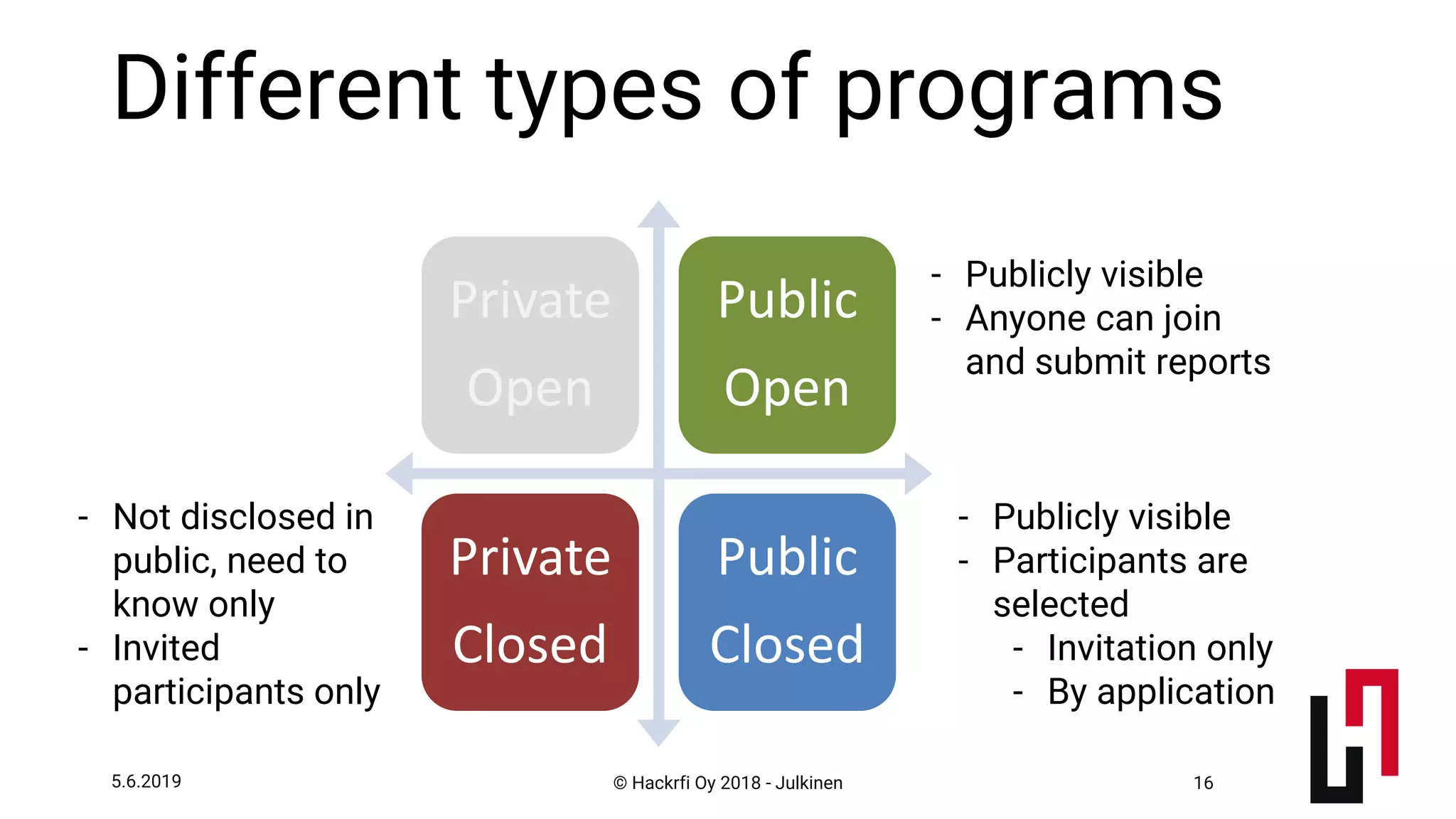
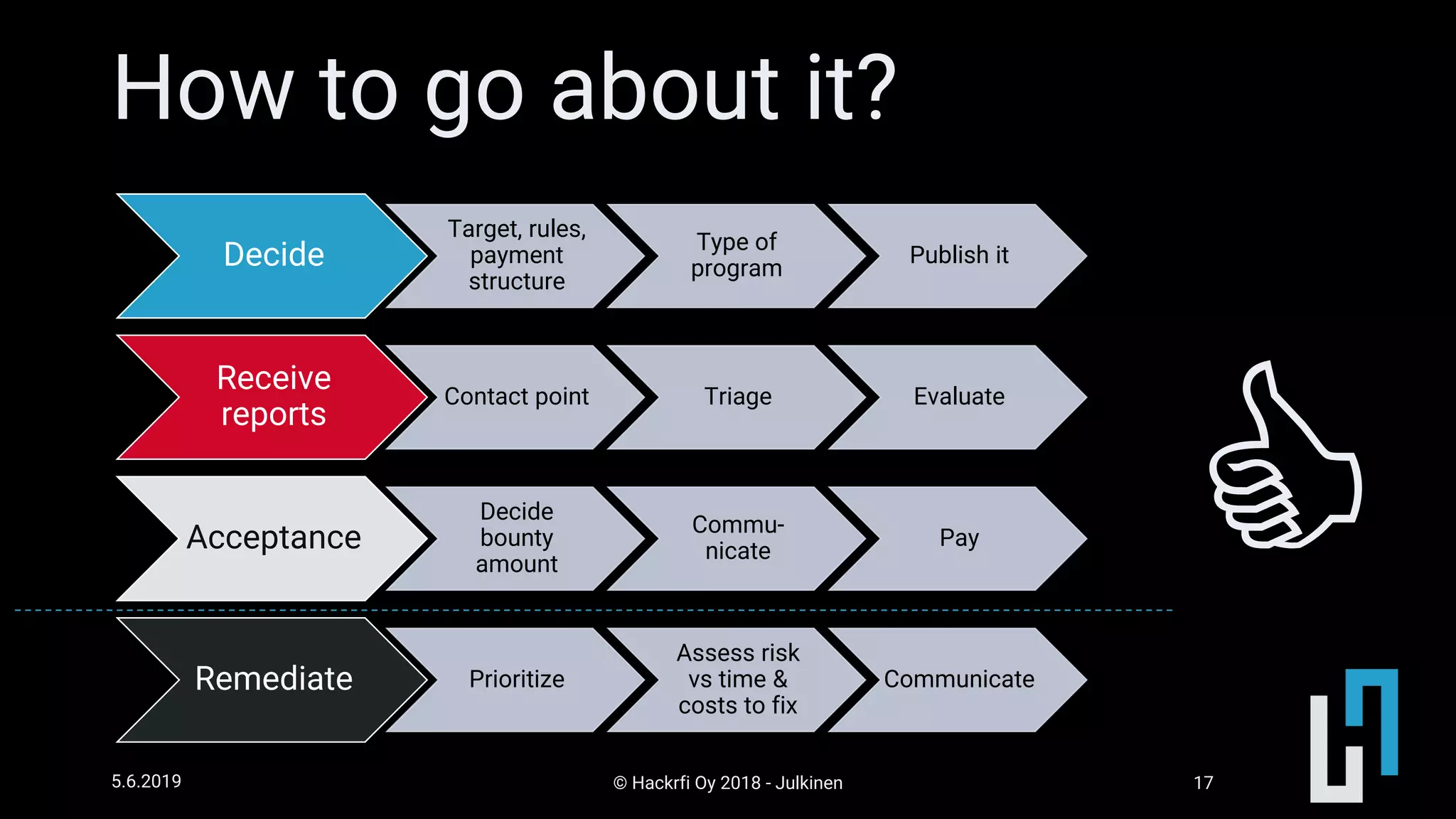
This document discusses API security risk management through the use of bug bounty programs. It begins by outlining some key risks of exposing APIs, such as fraudulent transactions, privacy leaks, and denial of service attacks. It then presents bug bounty programs as an agile way to discover vulnerabilities by paying security researchers to report issues. The benefits of bug bounties are that they encourage early reporting of bugs, are cost-effective if only real issues receive payment, and increase trust through transparency. The document provides advice on setting up different types of bug bounty programs and managing the process of receiving and addressing reports.