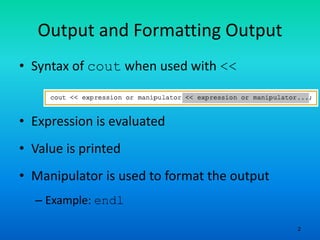
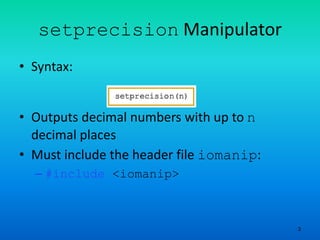
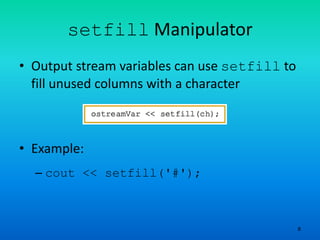
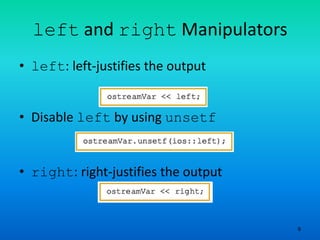
The document provides an overview of output formatting in C++ using manipulators, detailing various manipulators such as 'setprecision', 'fixed', 'showpoint', and 'setw' that control the appearance of output. It also covers additional formatting tools and explains the two types of manipulators, along with a brief discussion on input/output with strings and file handling in C++. The material serves as an assignment prompt to explain the formatting of output using these manipulators.