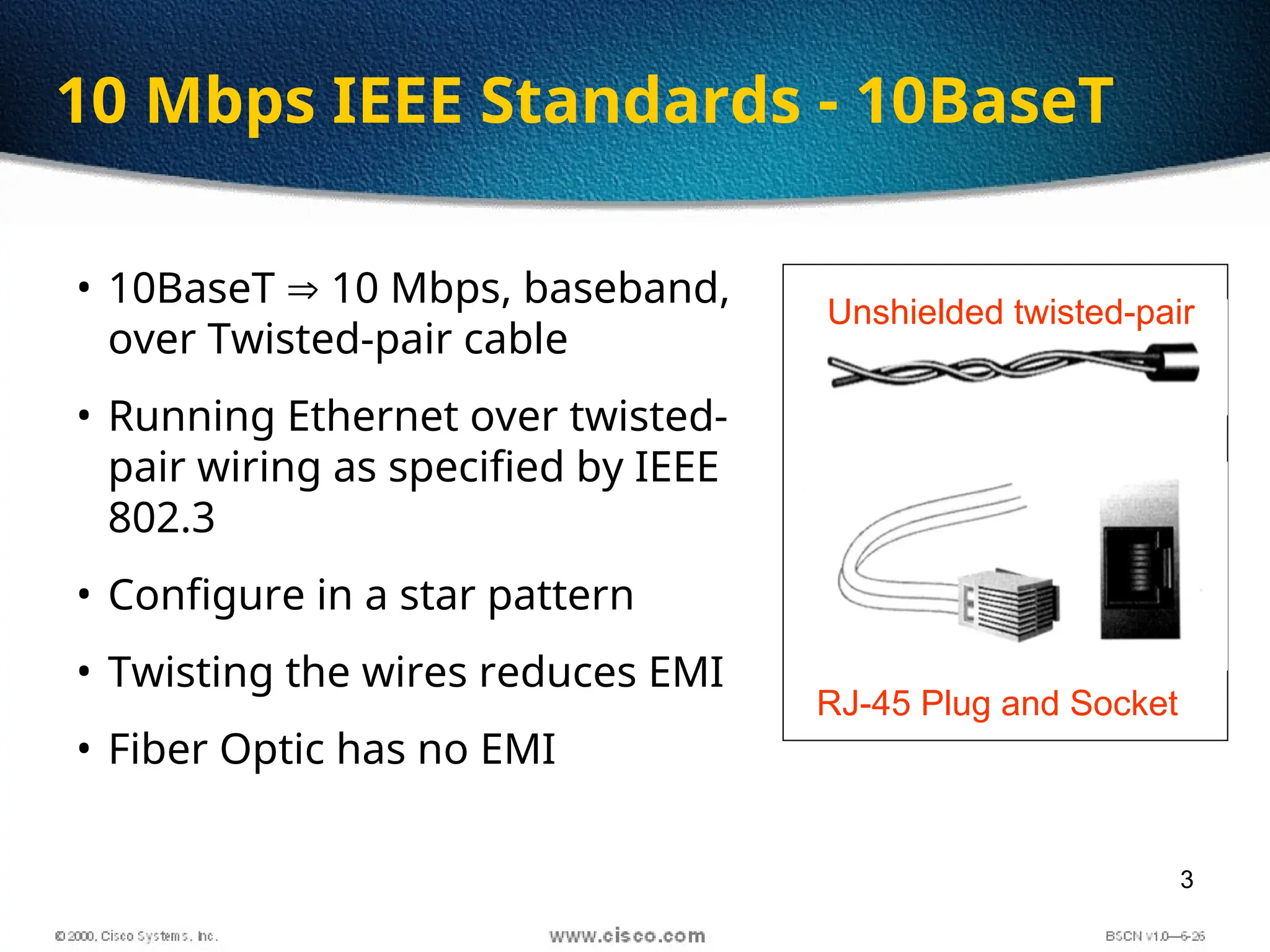
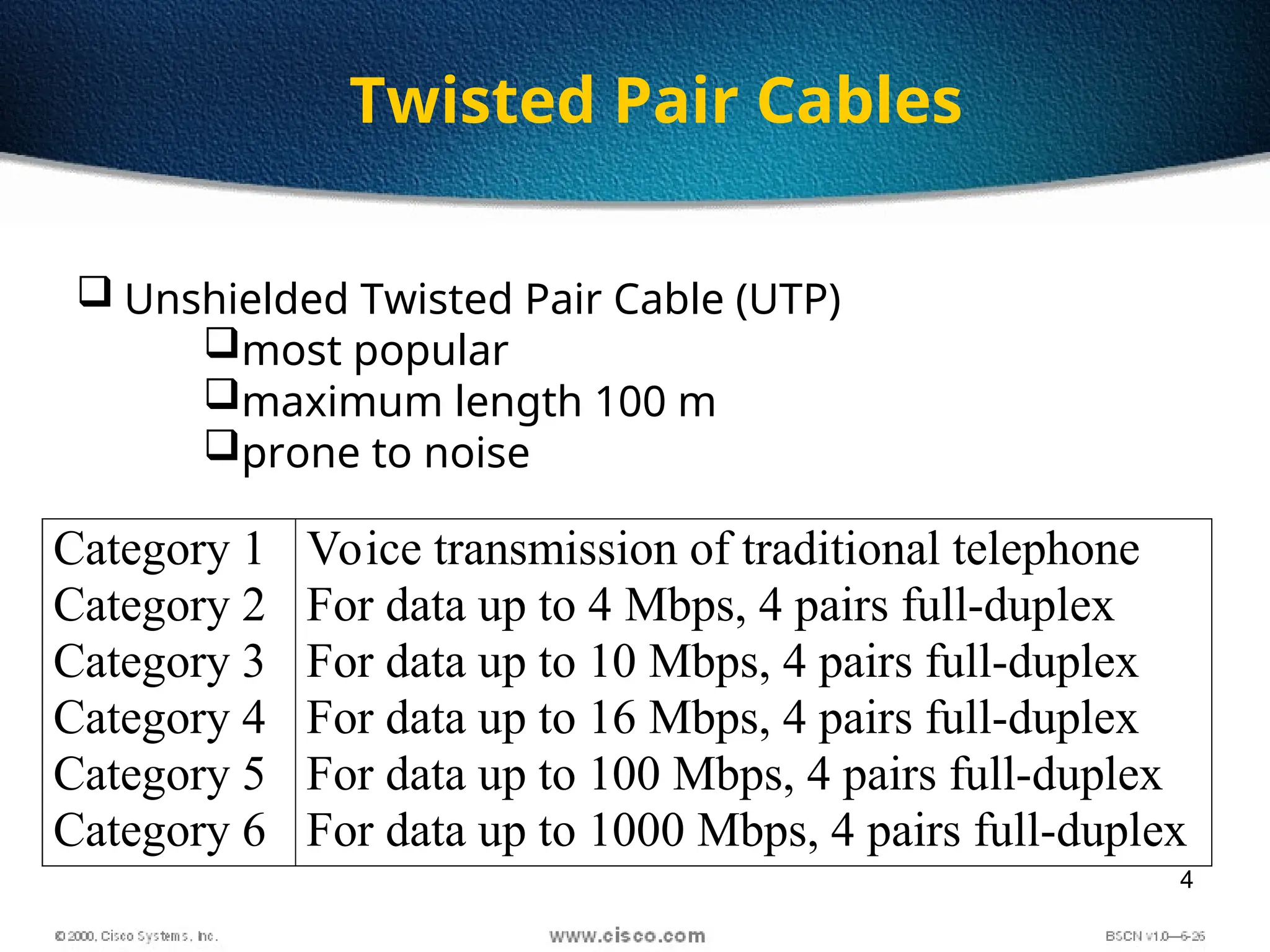
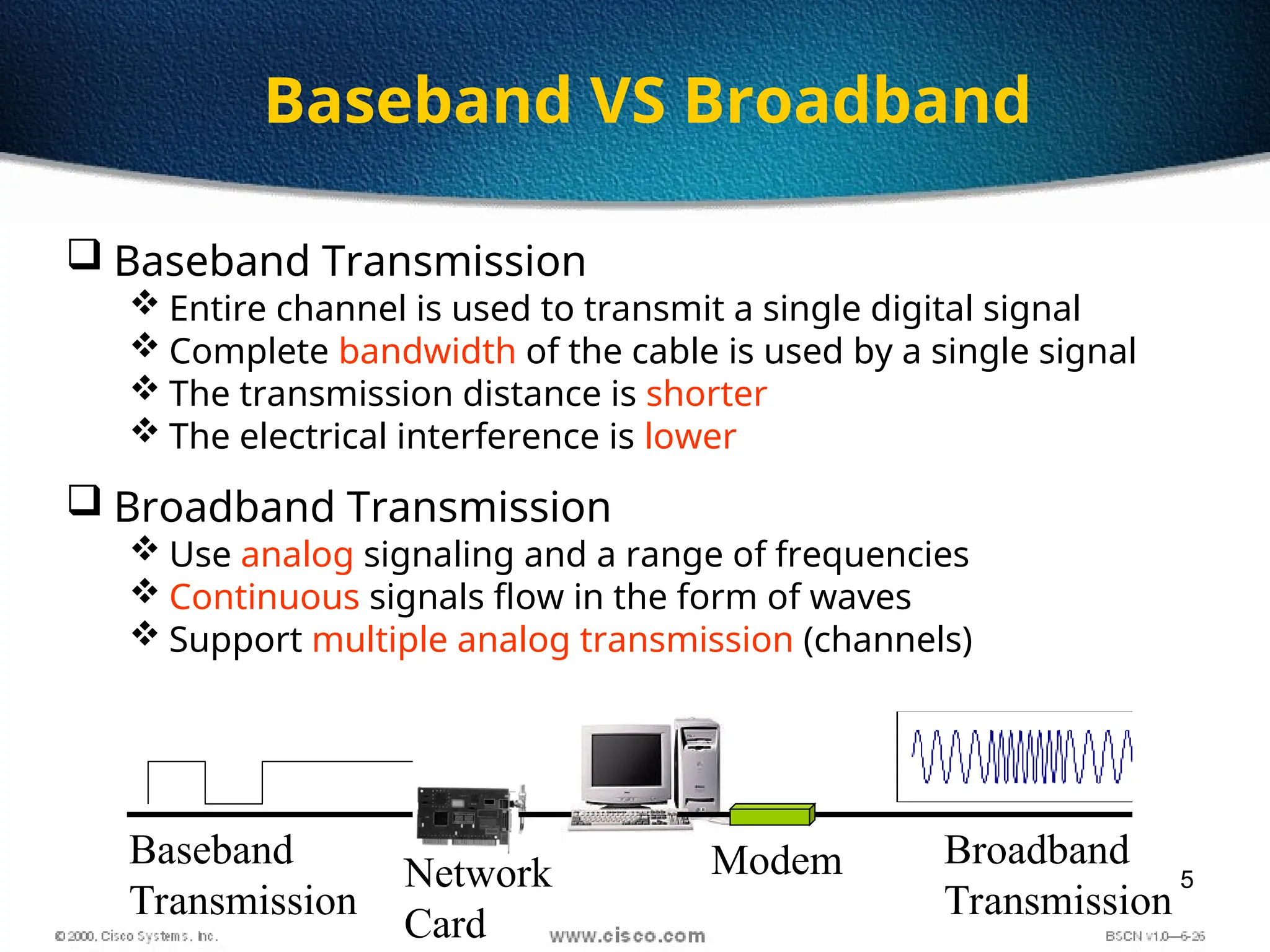
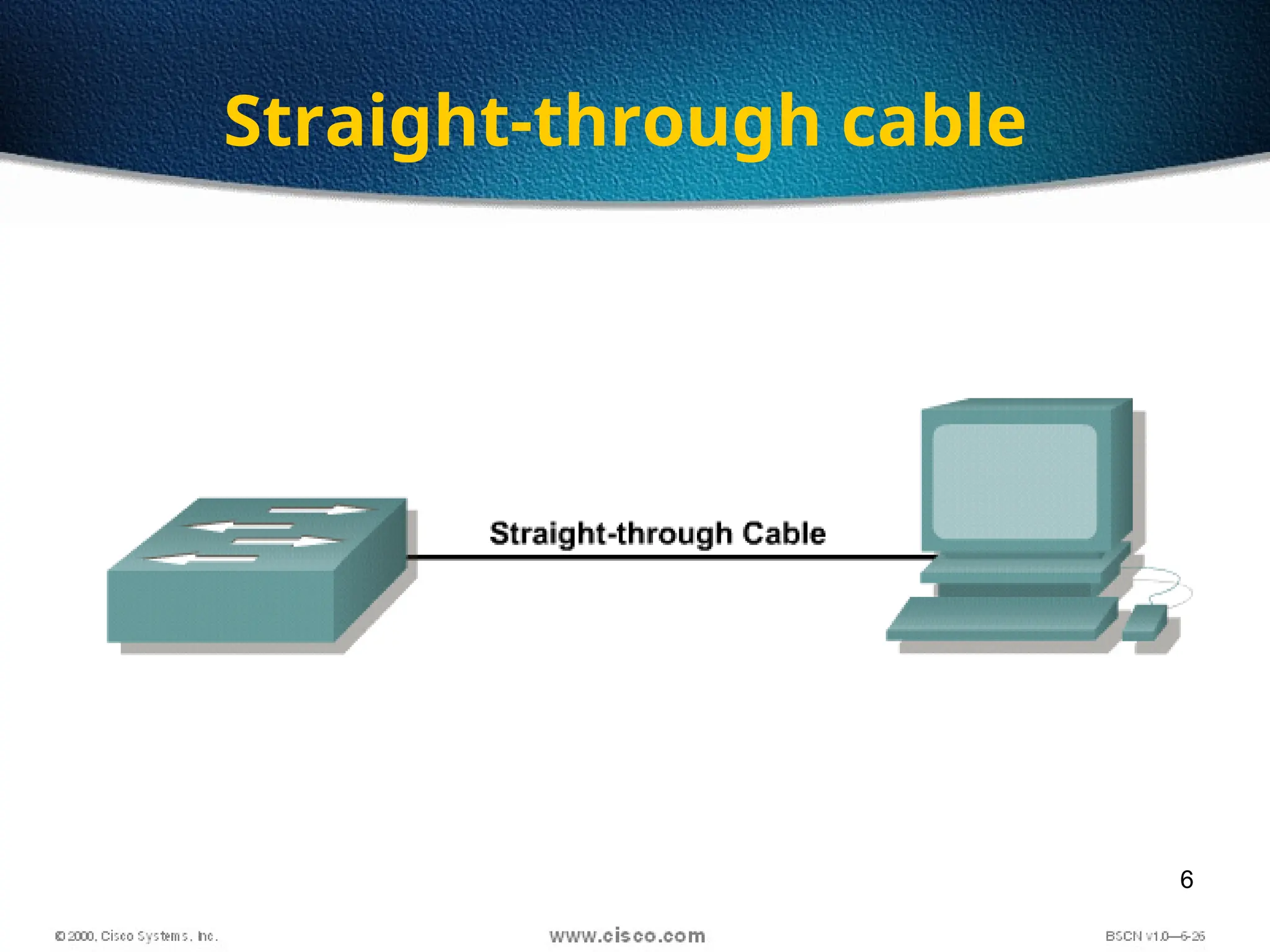
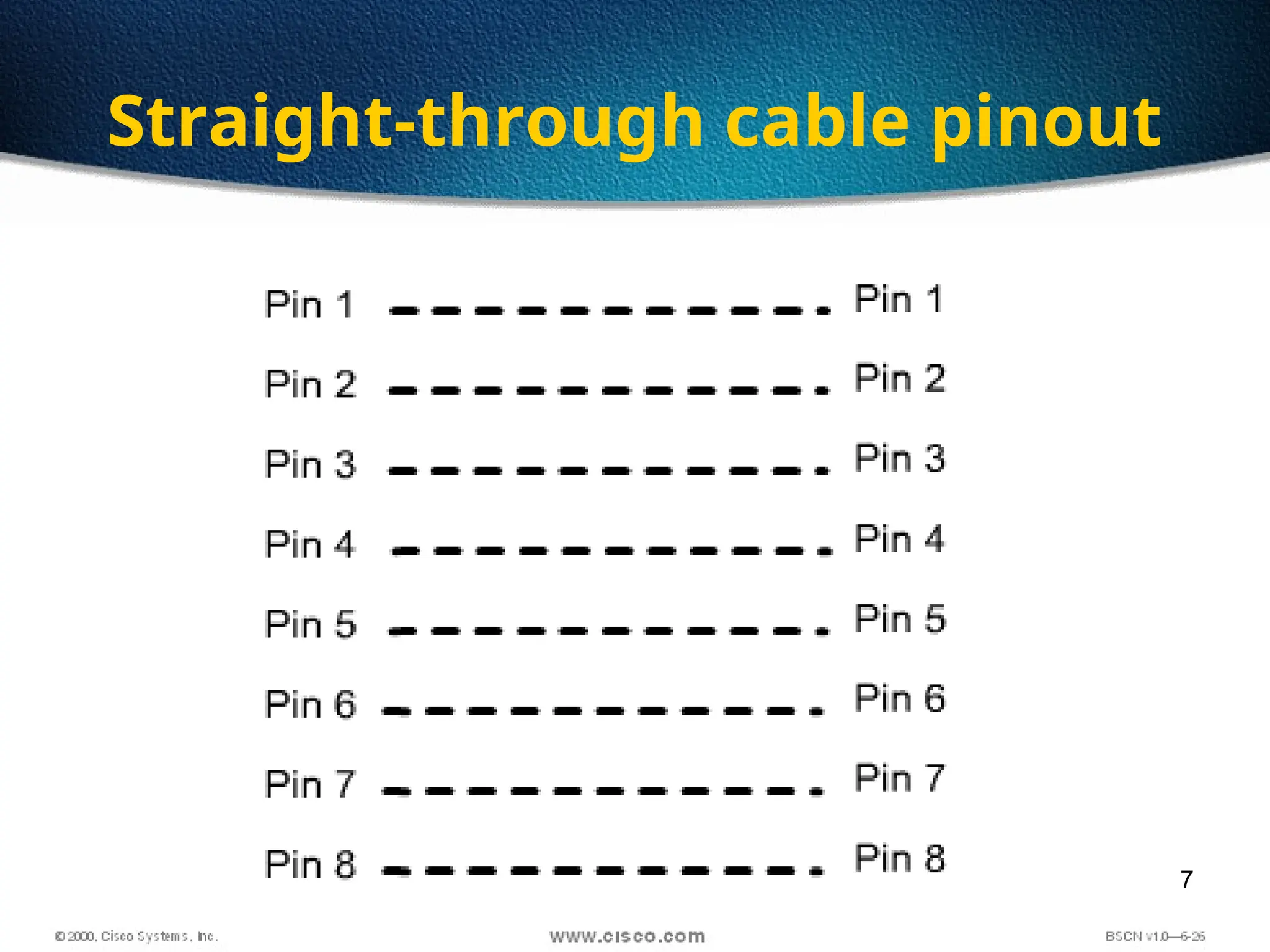
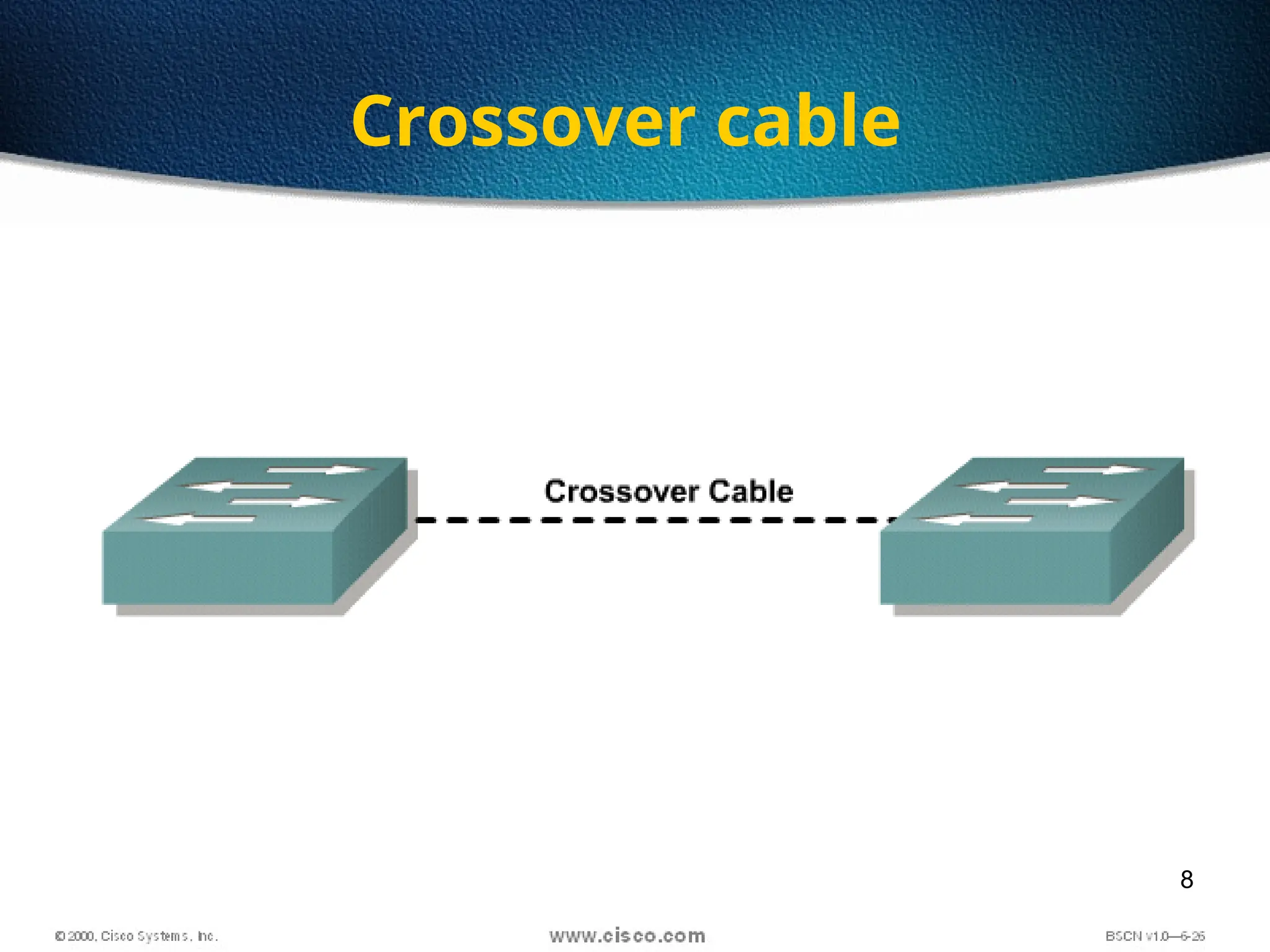
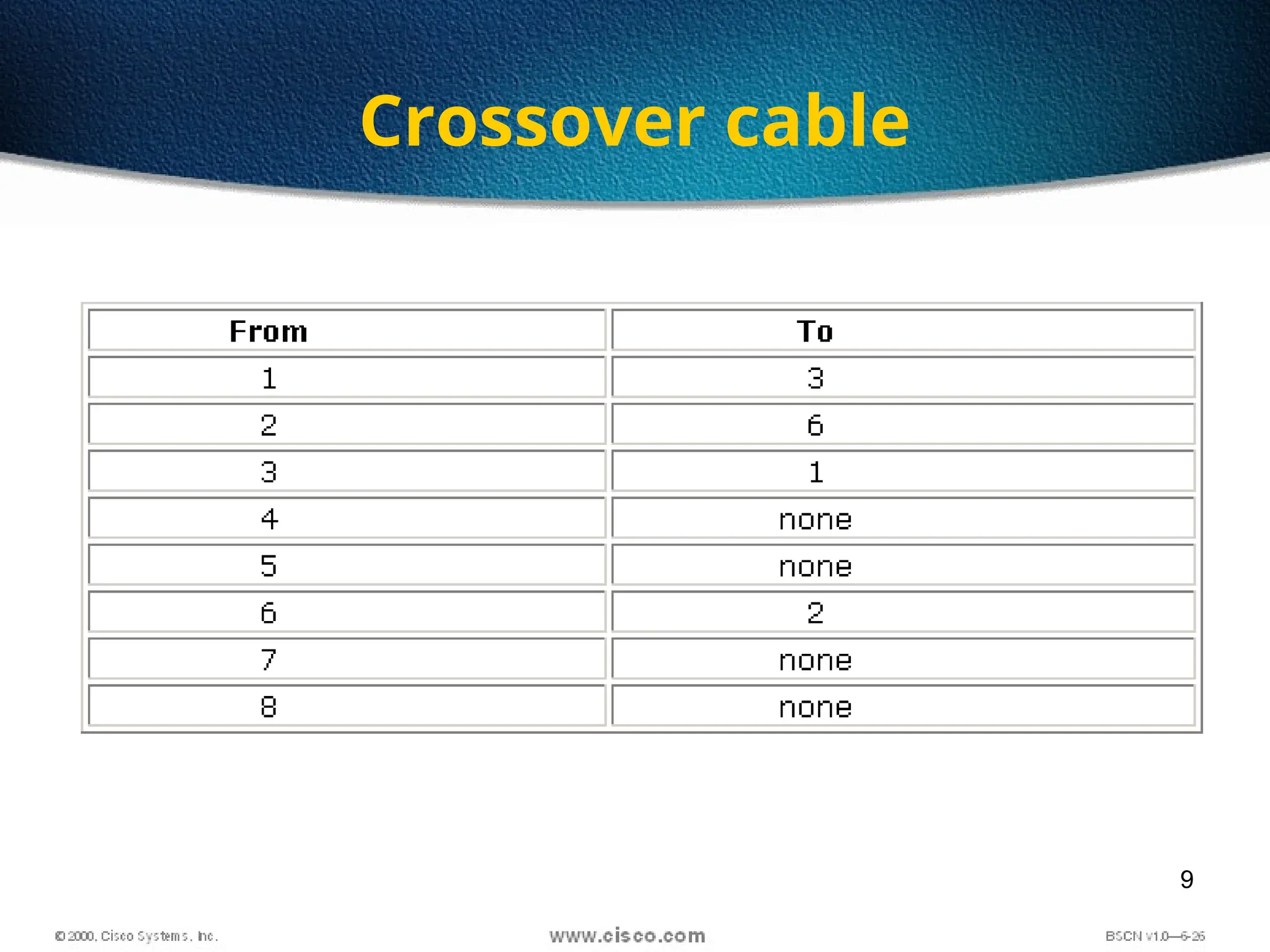
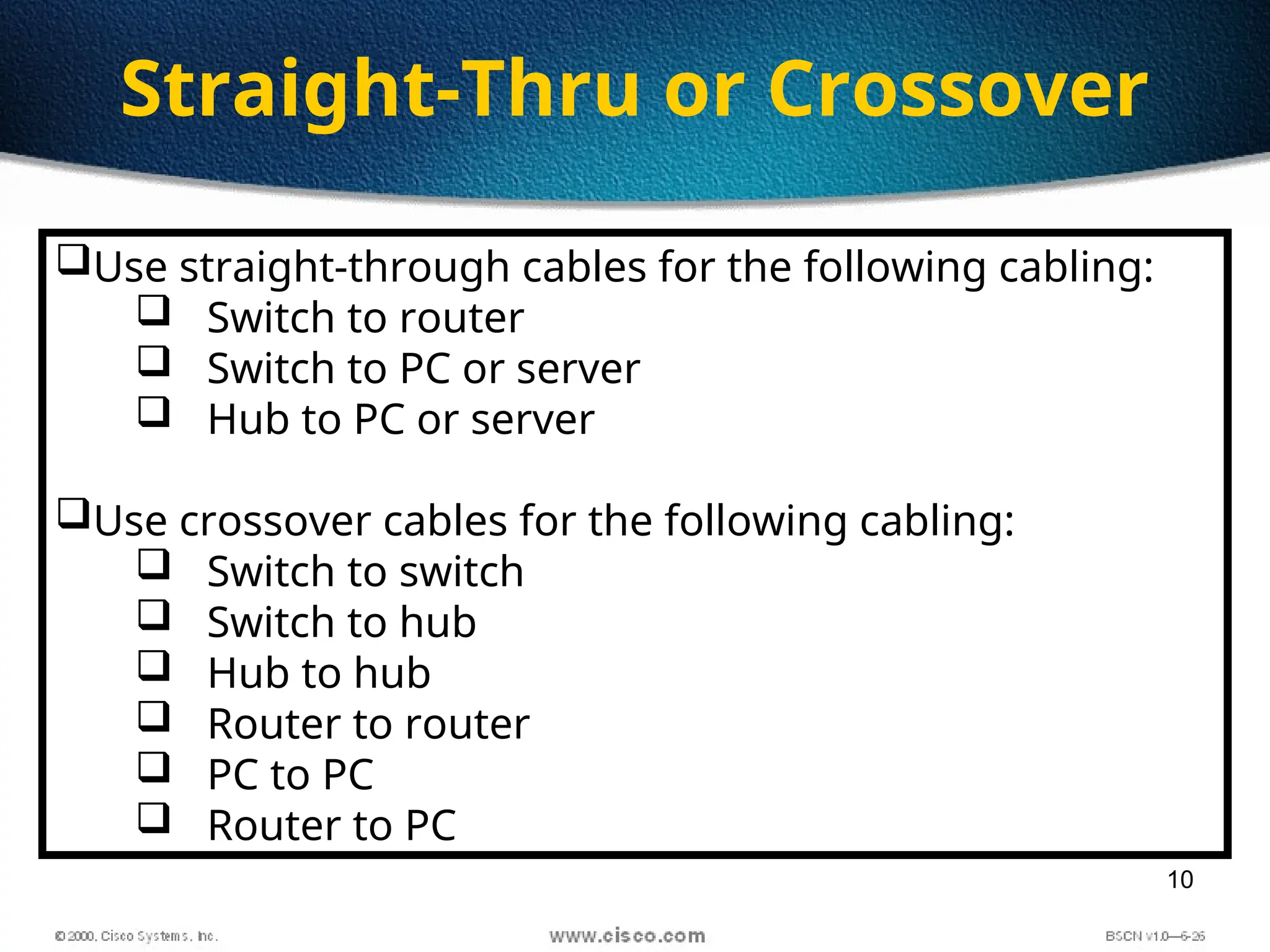
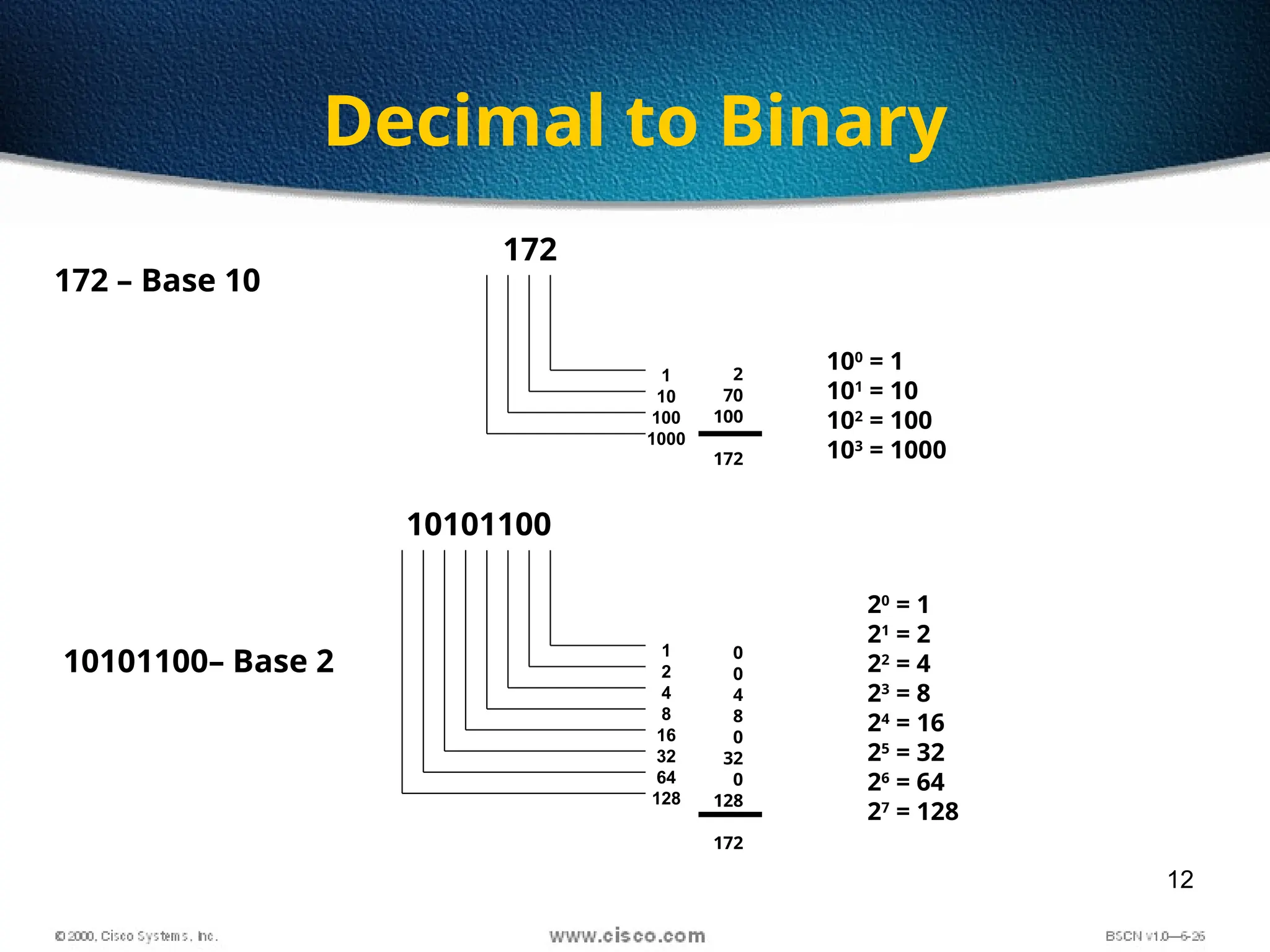
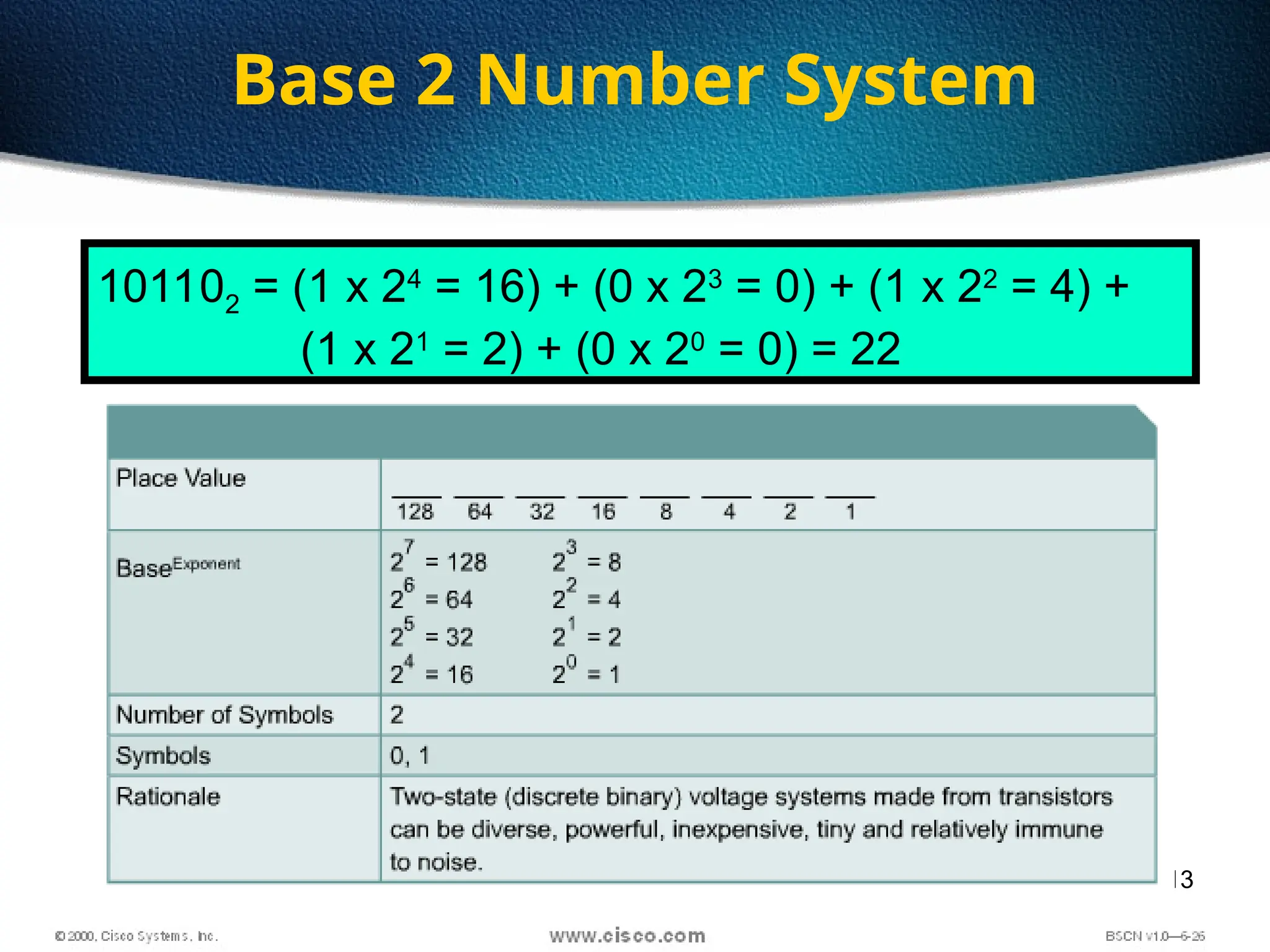
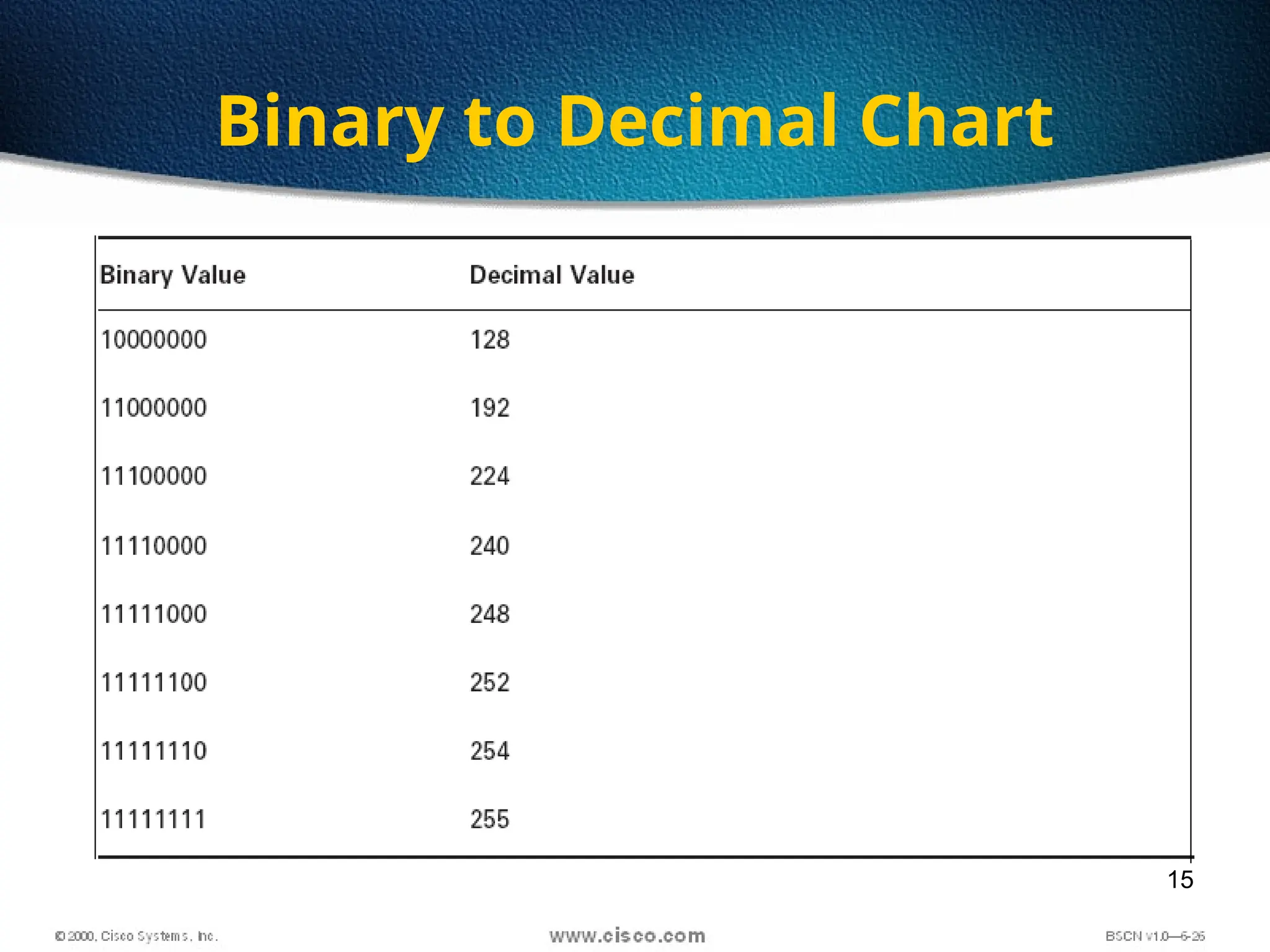
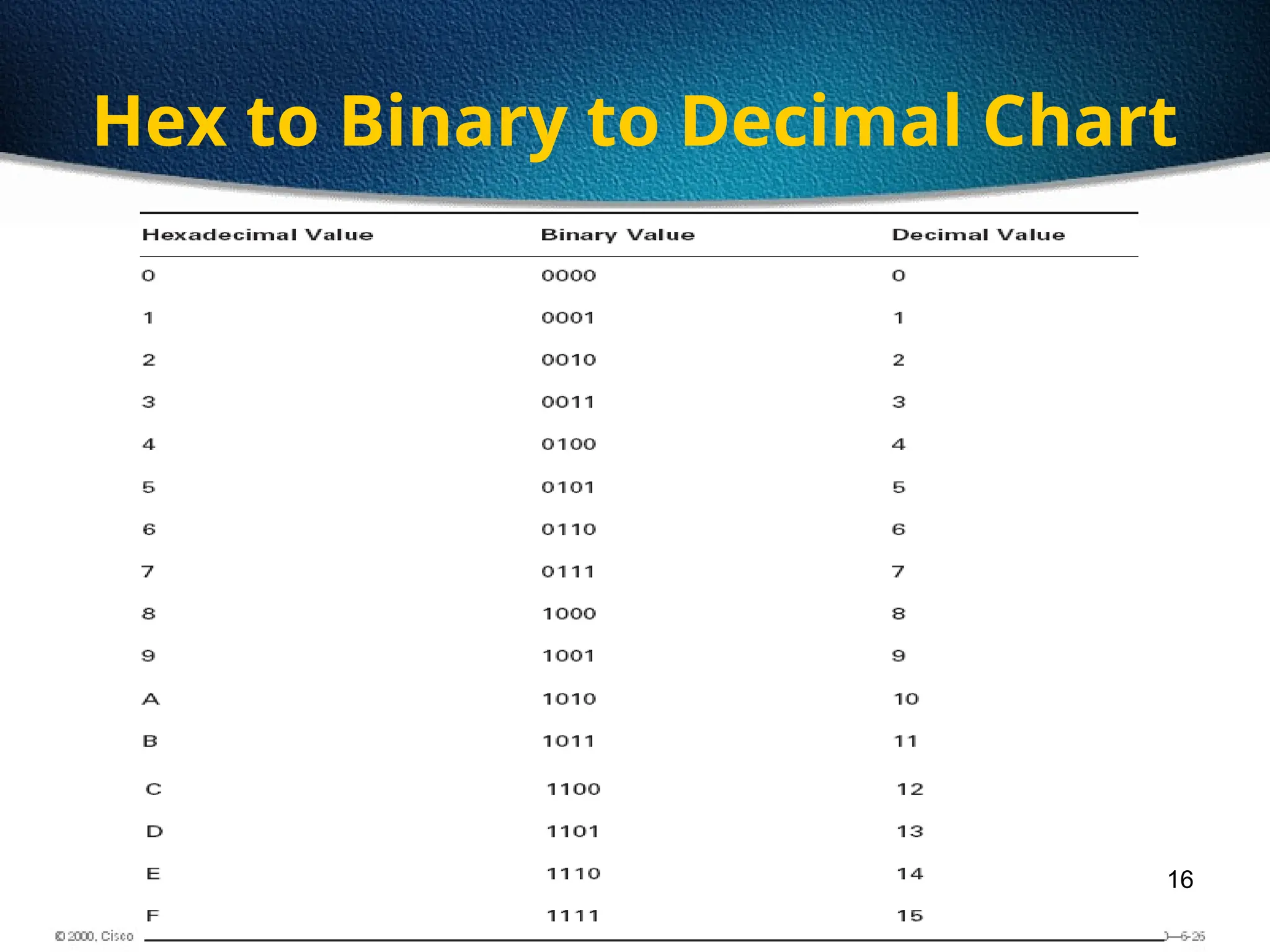
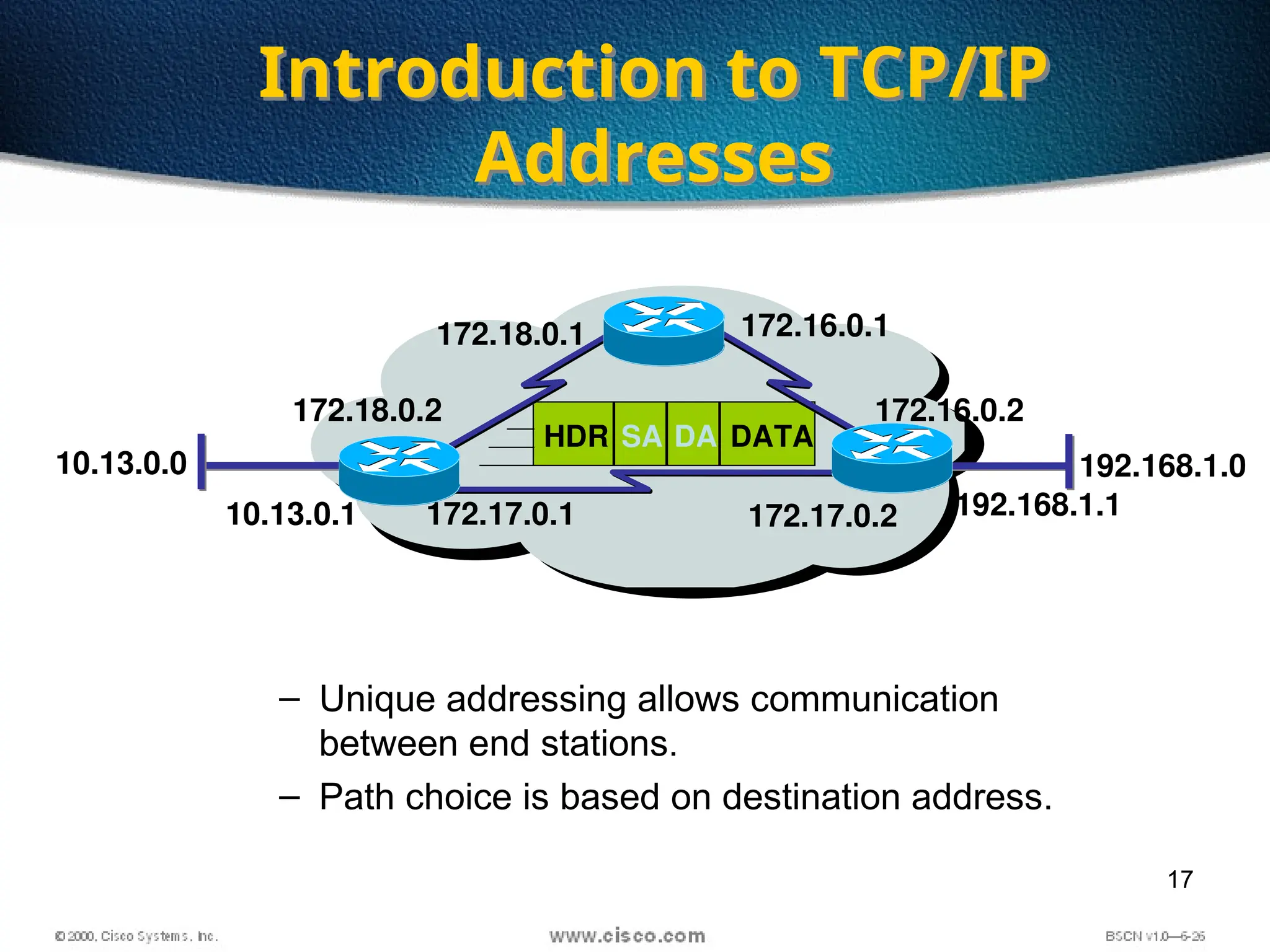
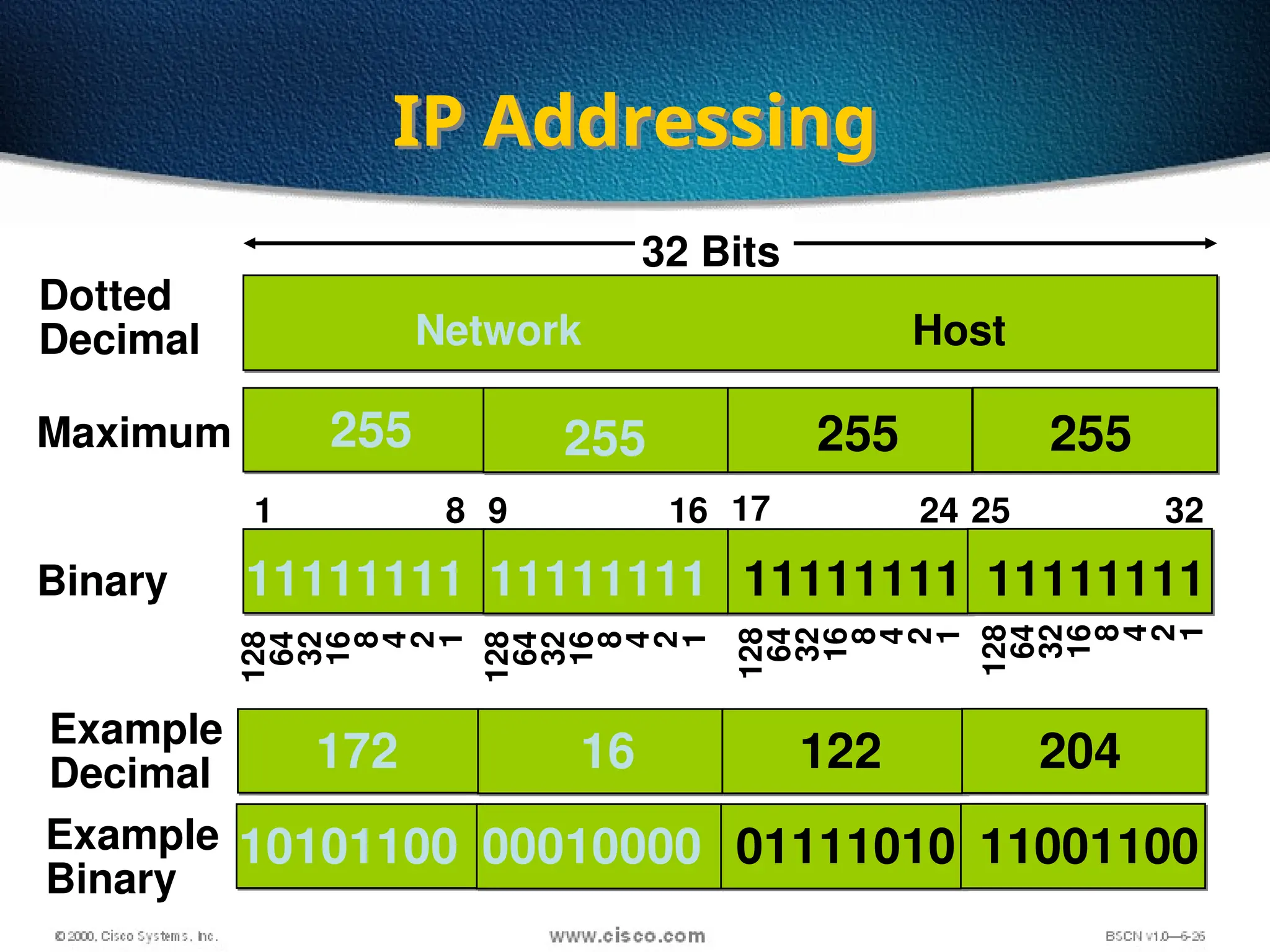
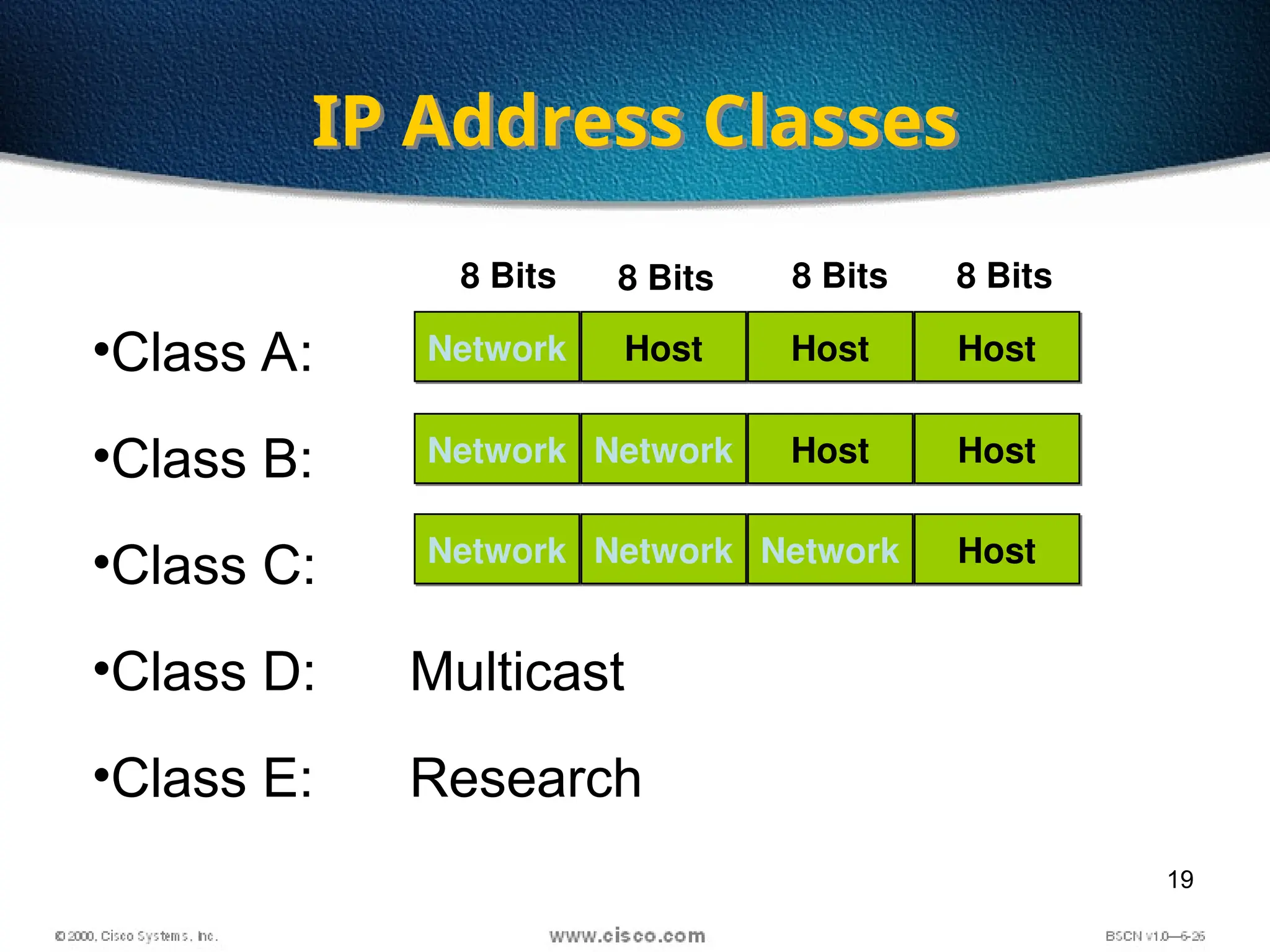
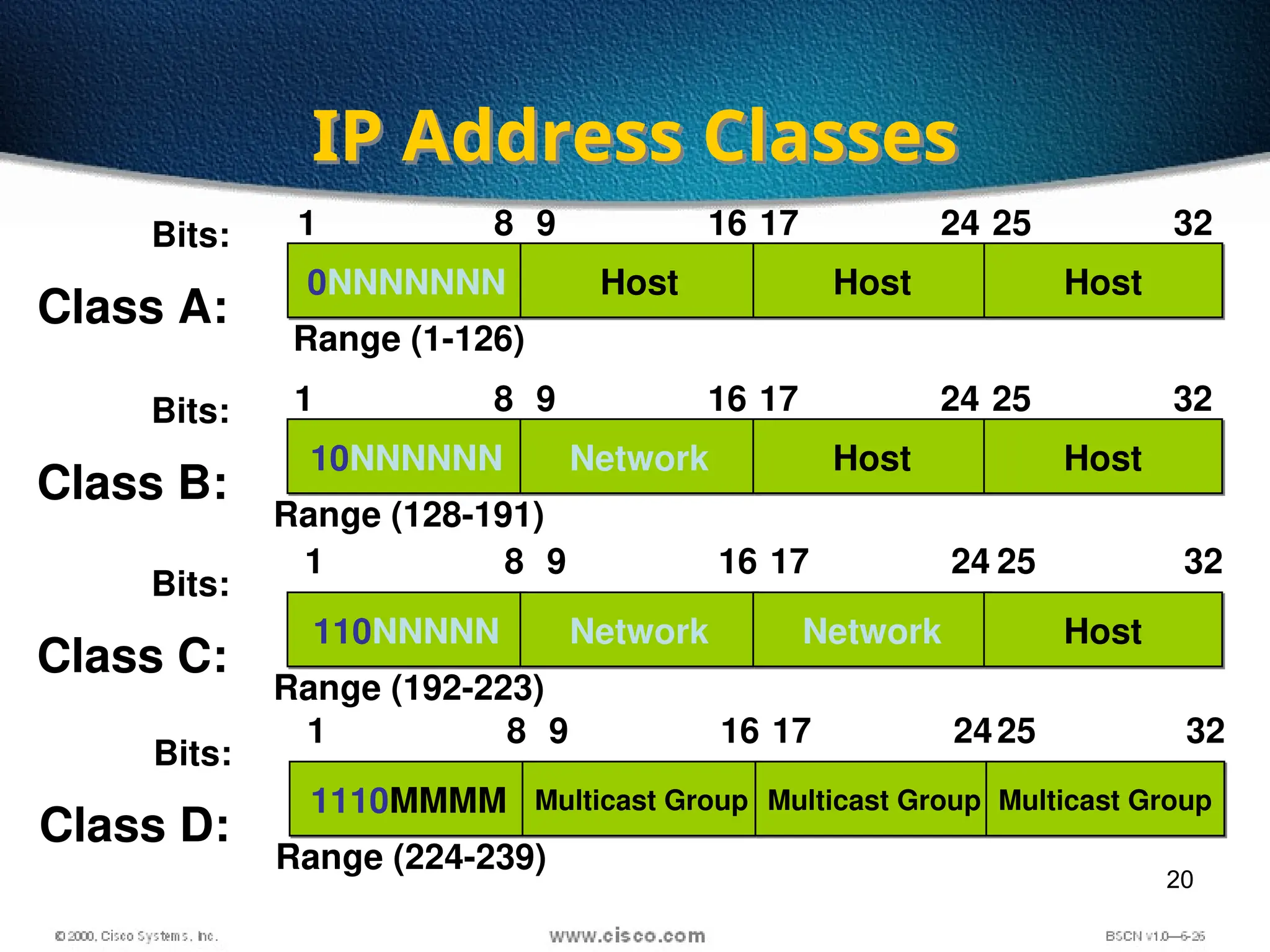
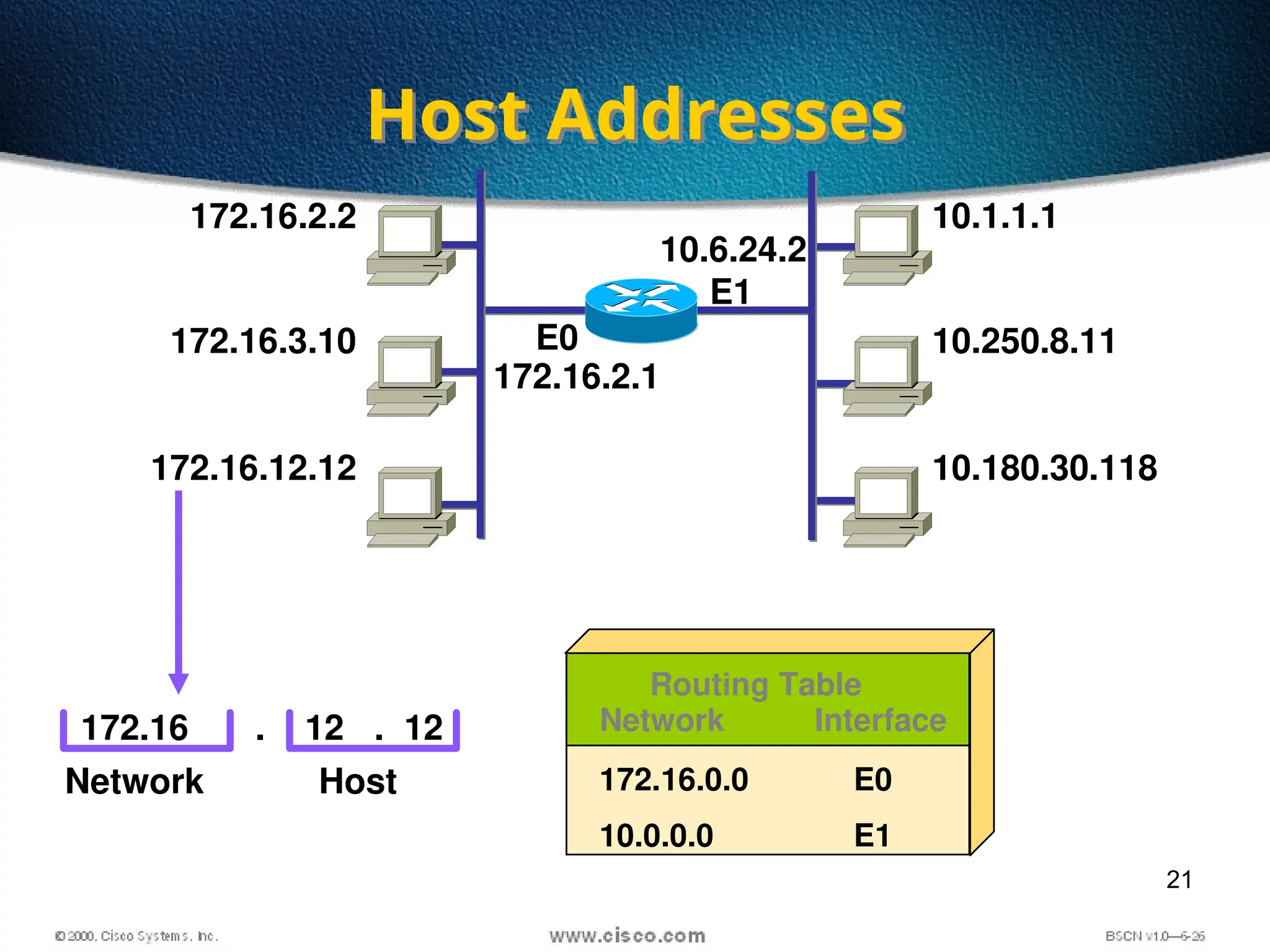
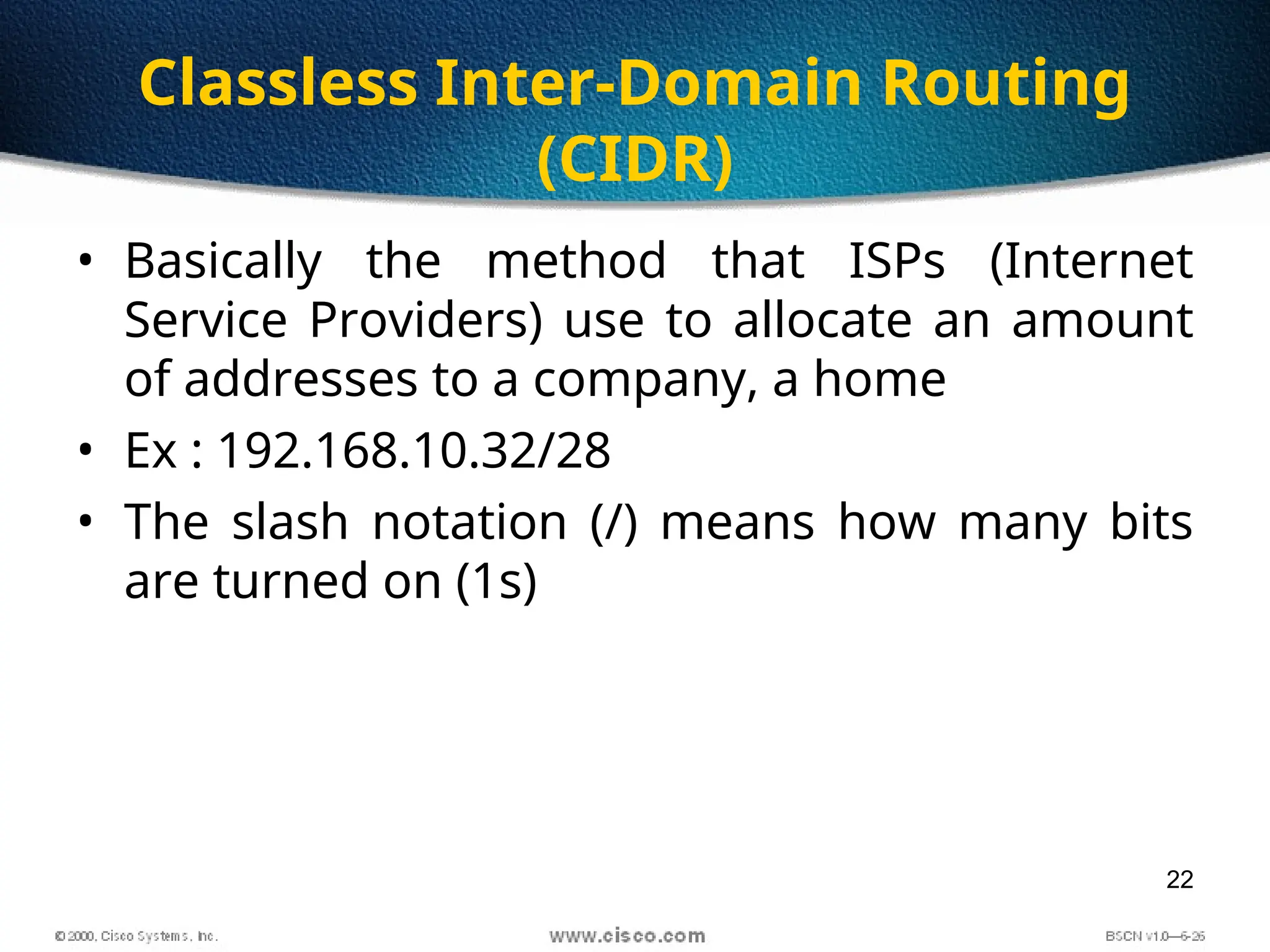
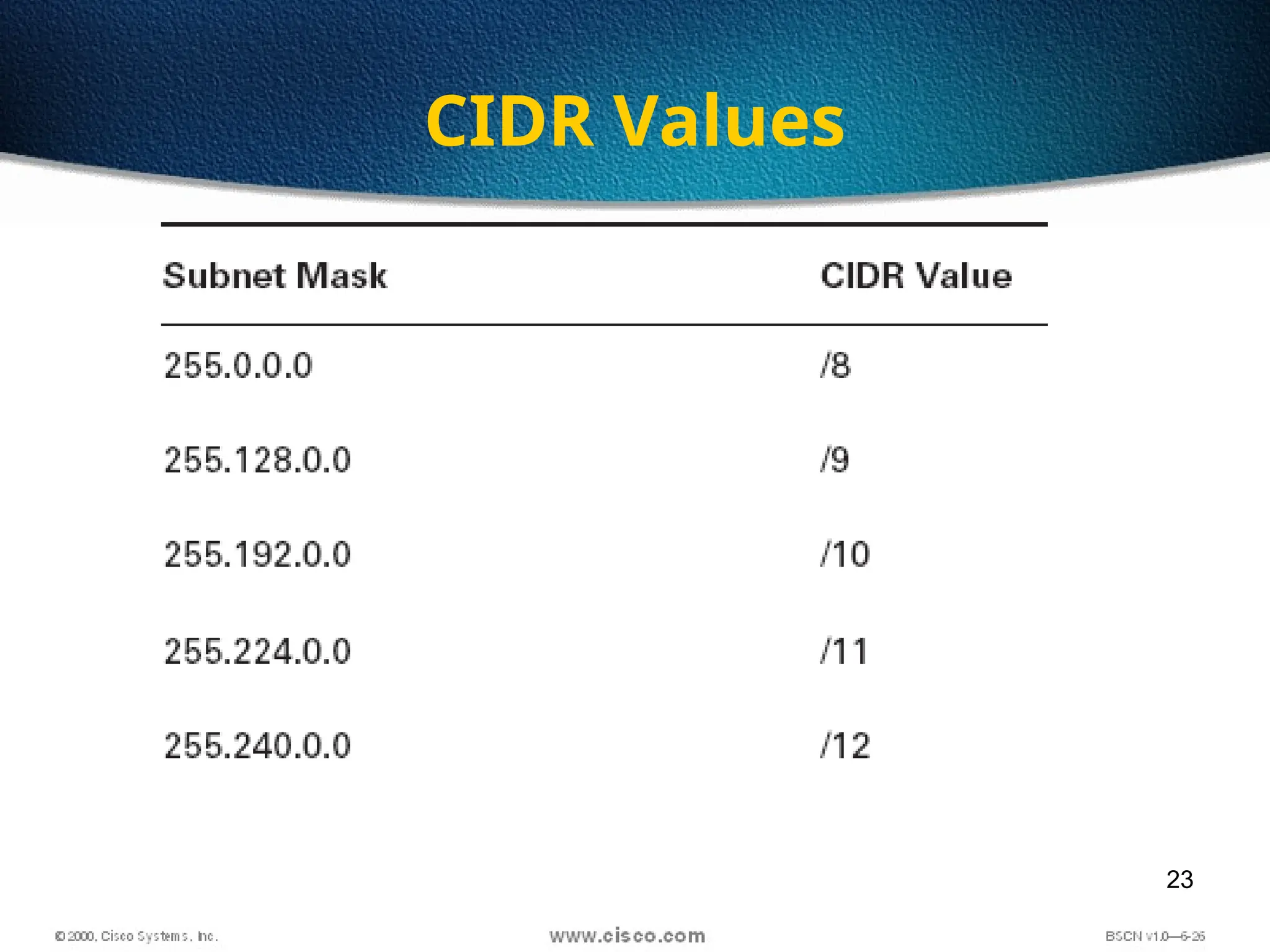
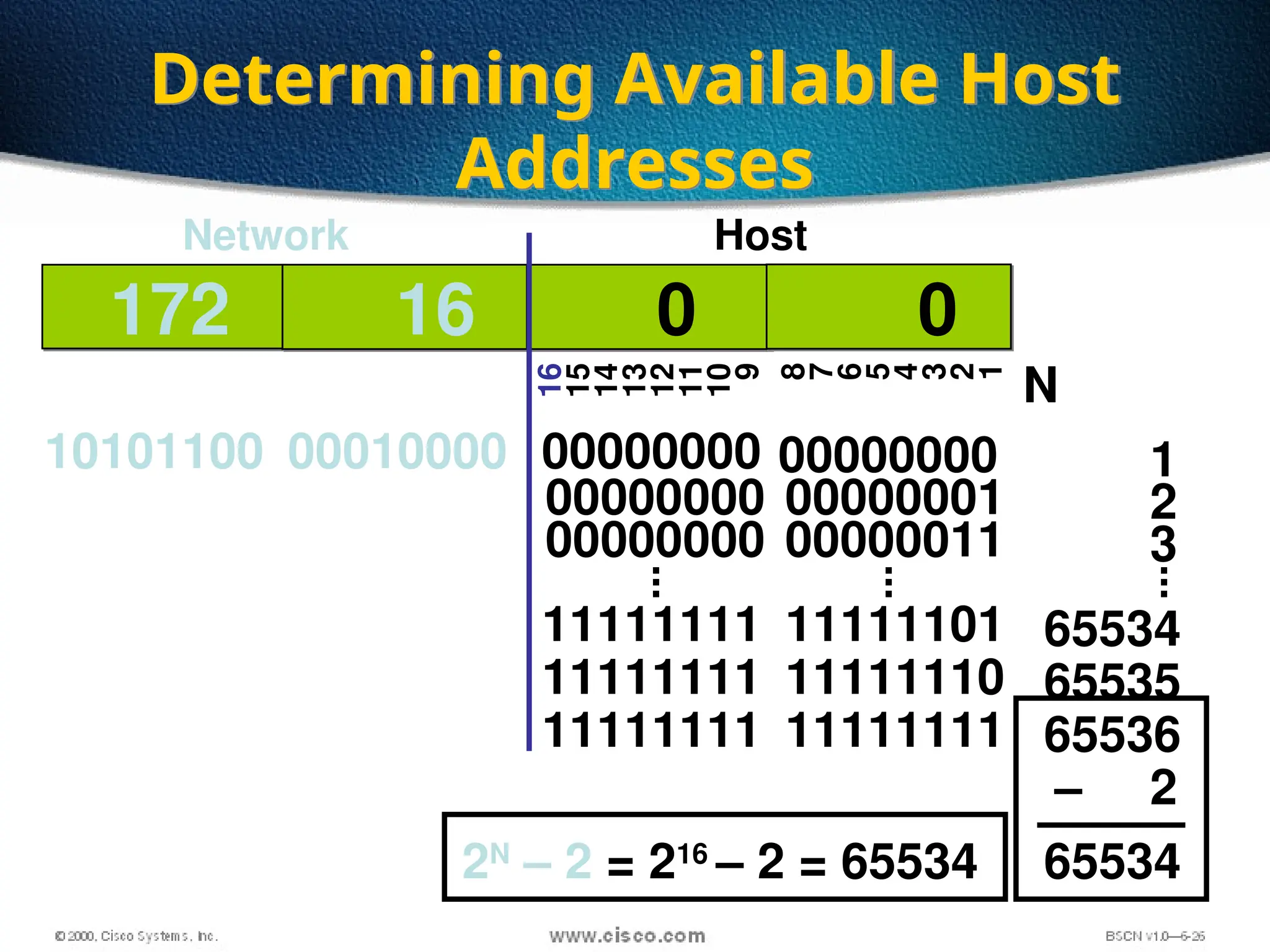
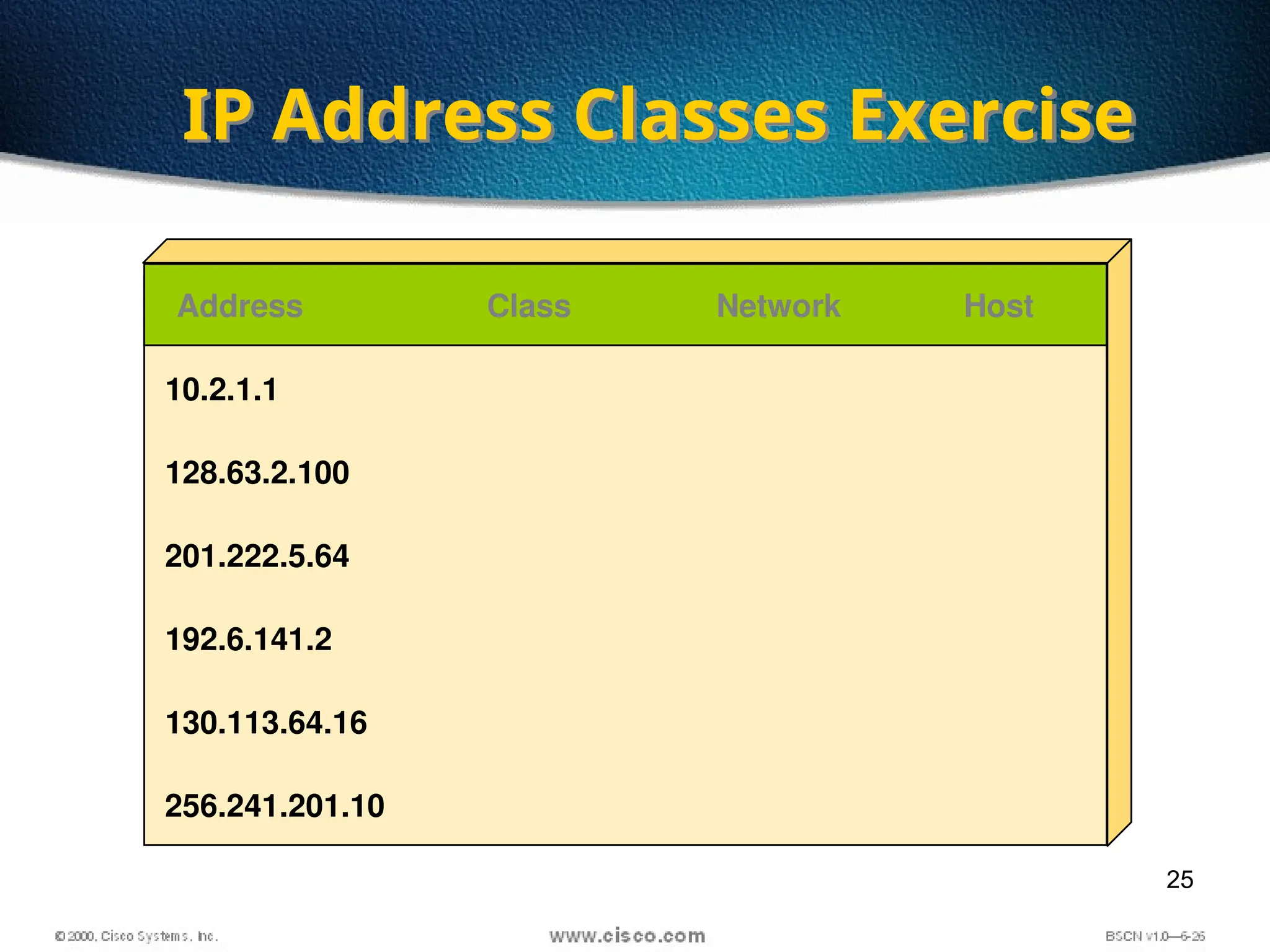
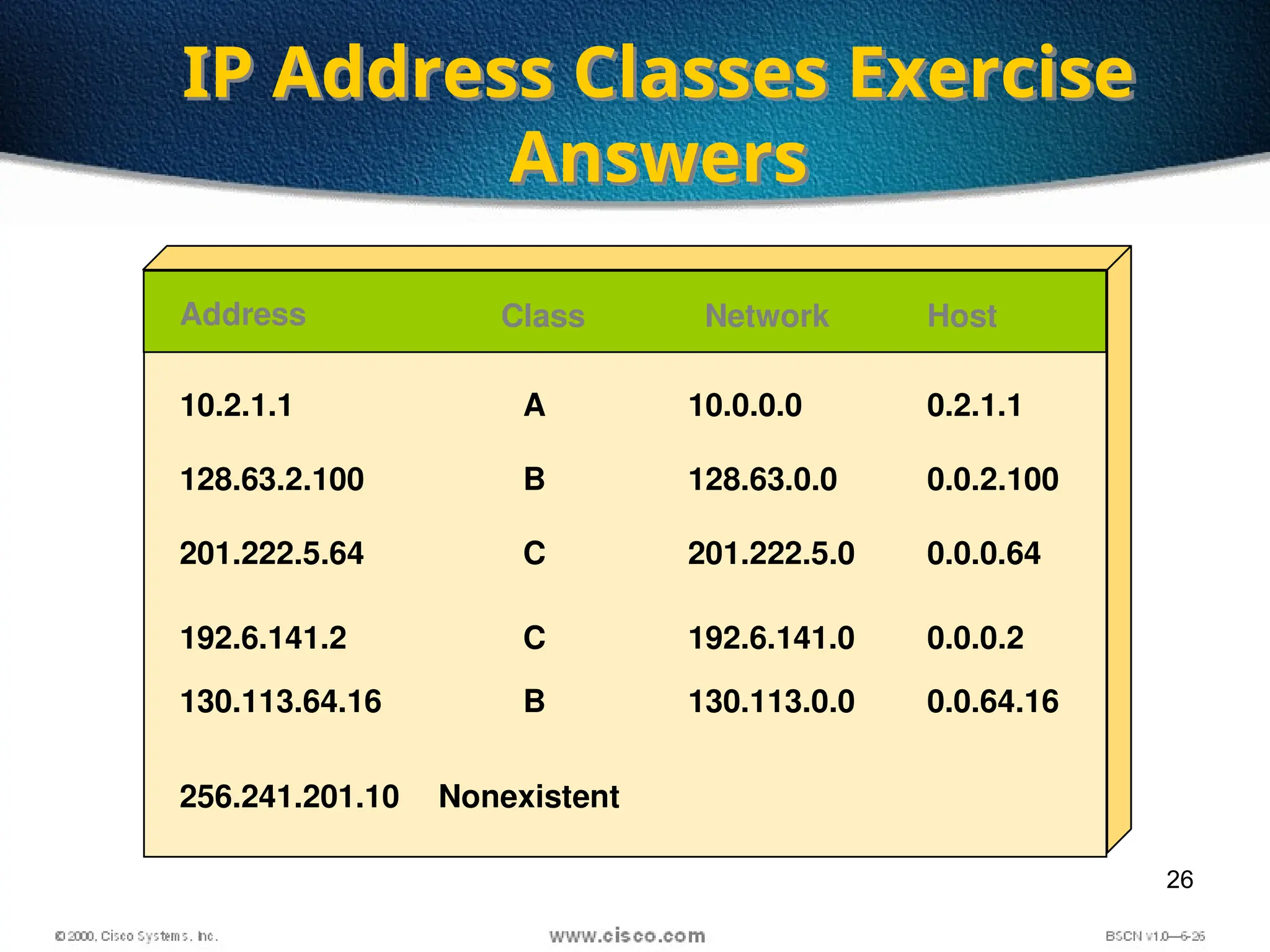
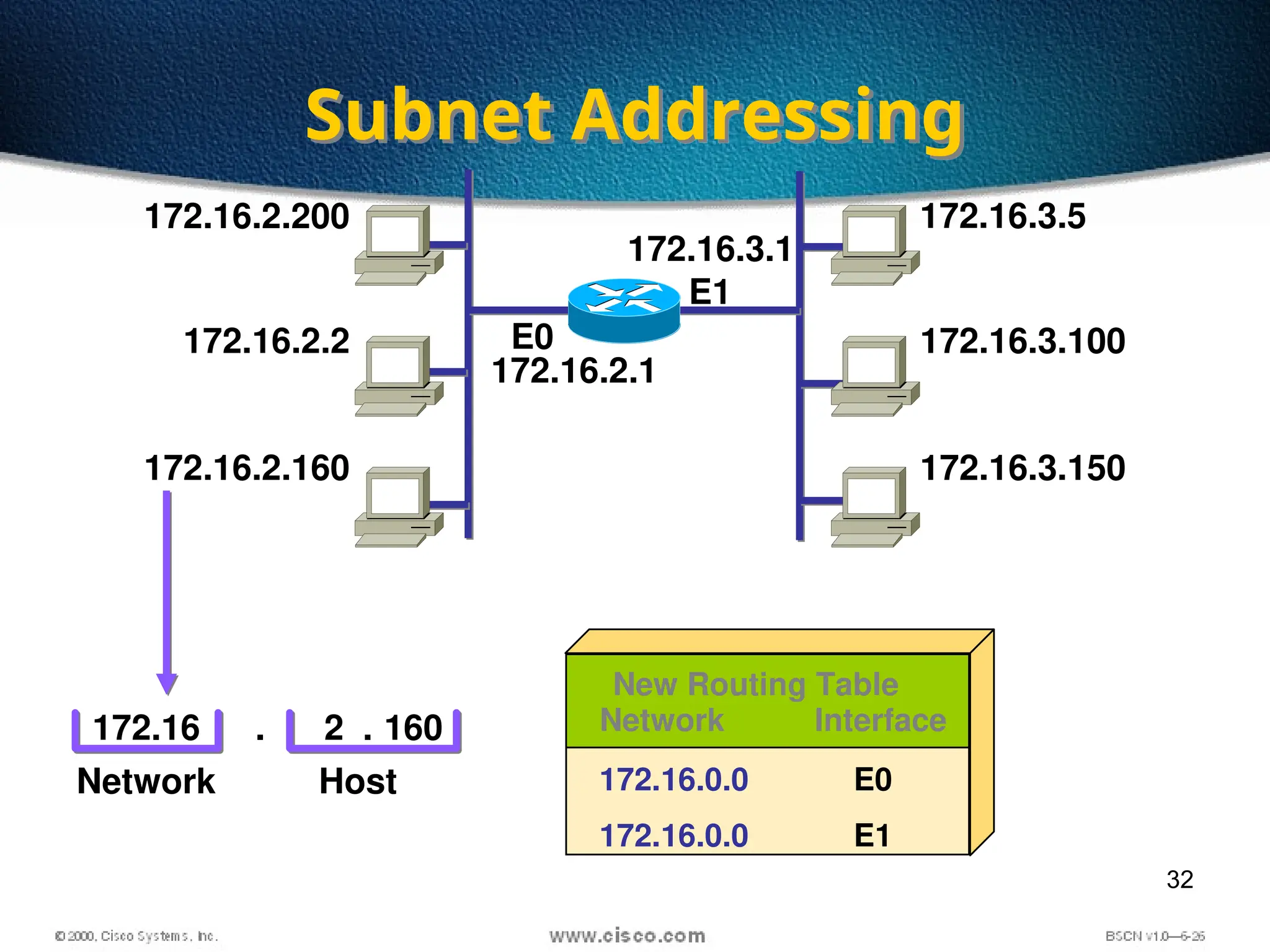
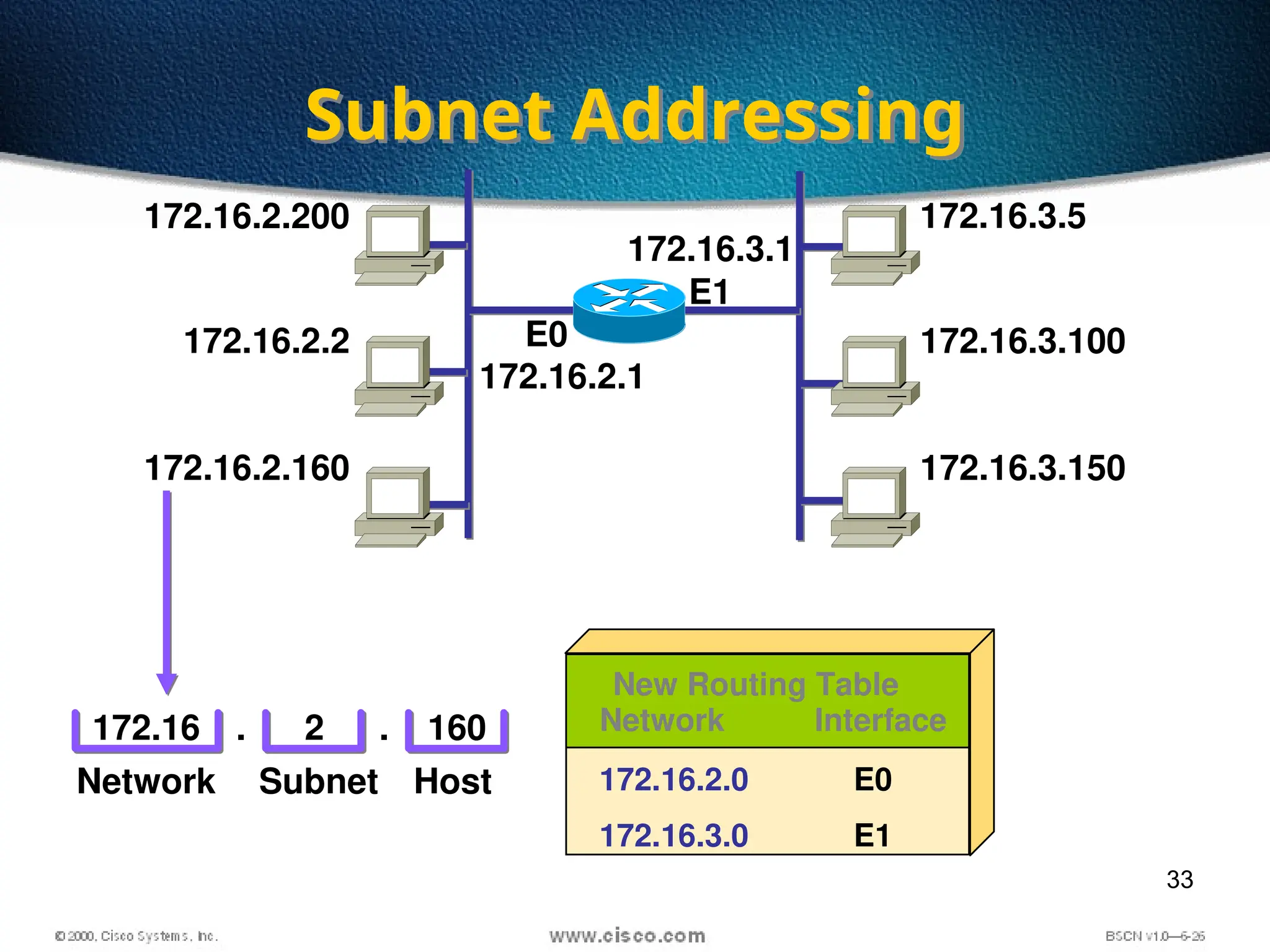
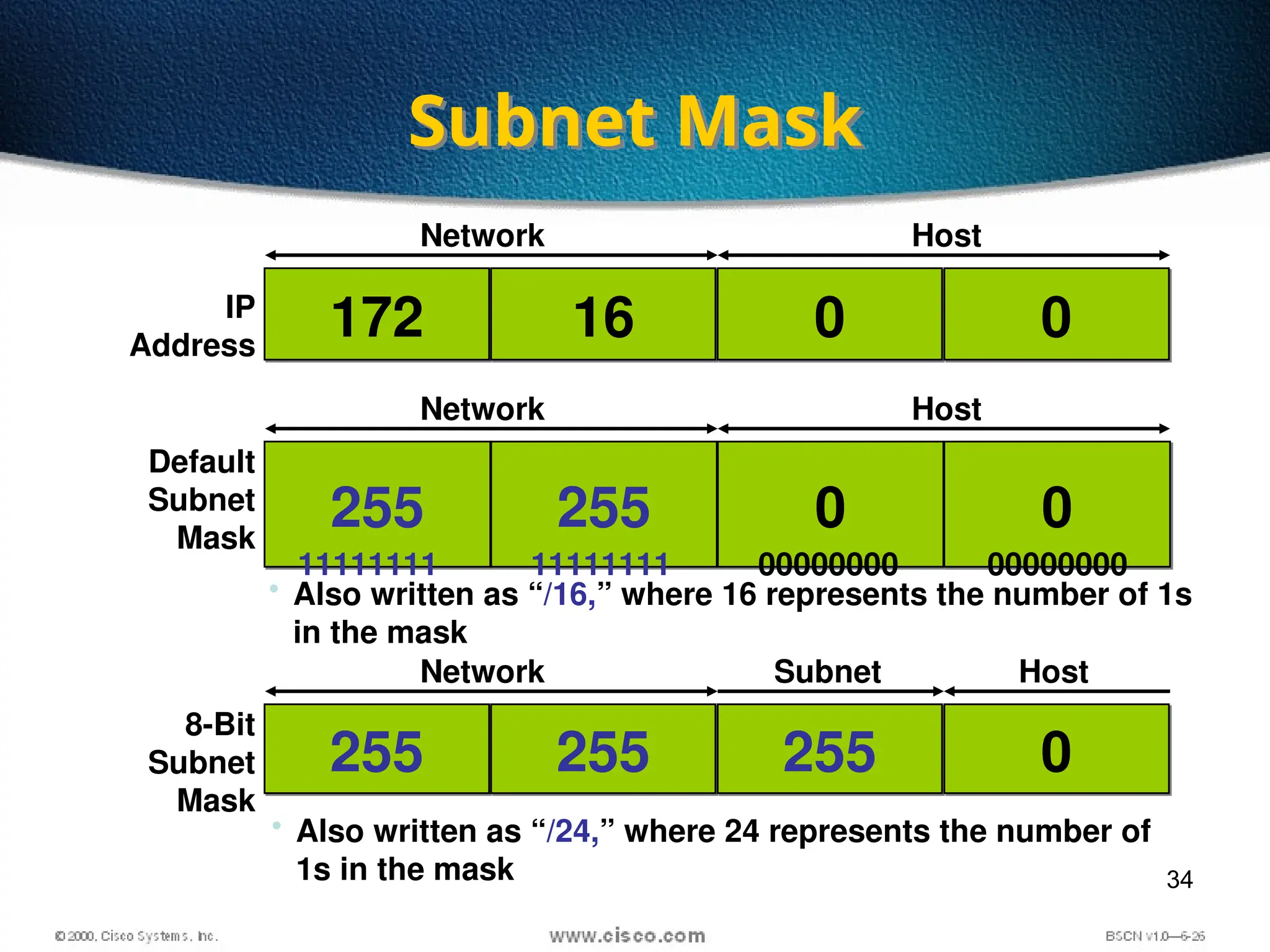
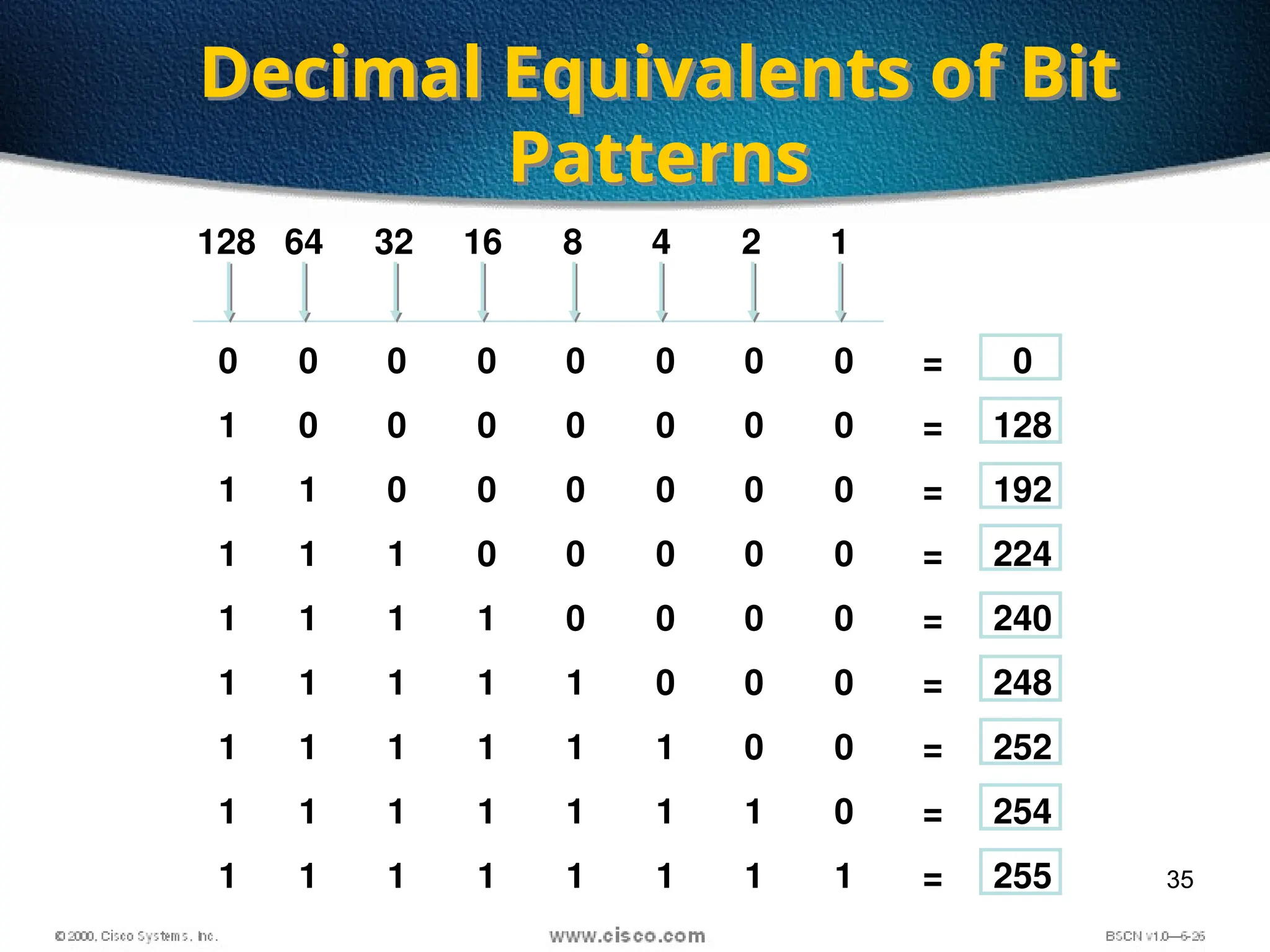
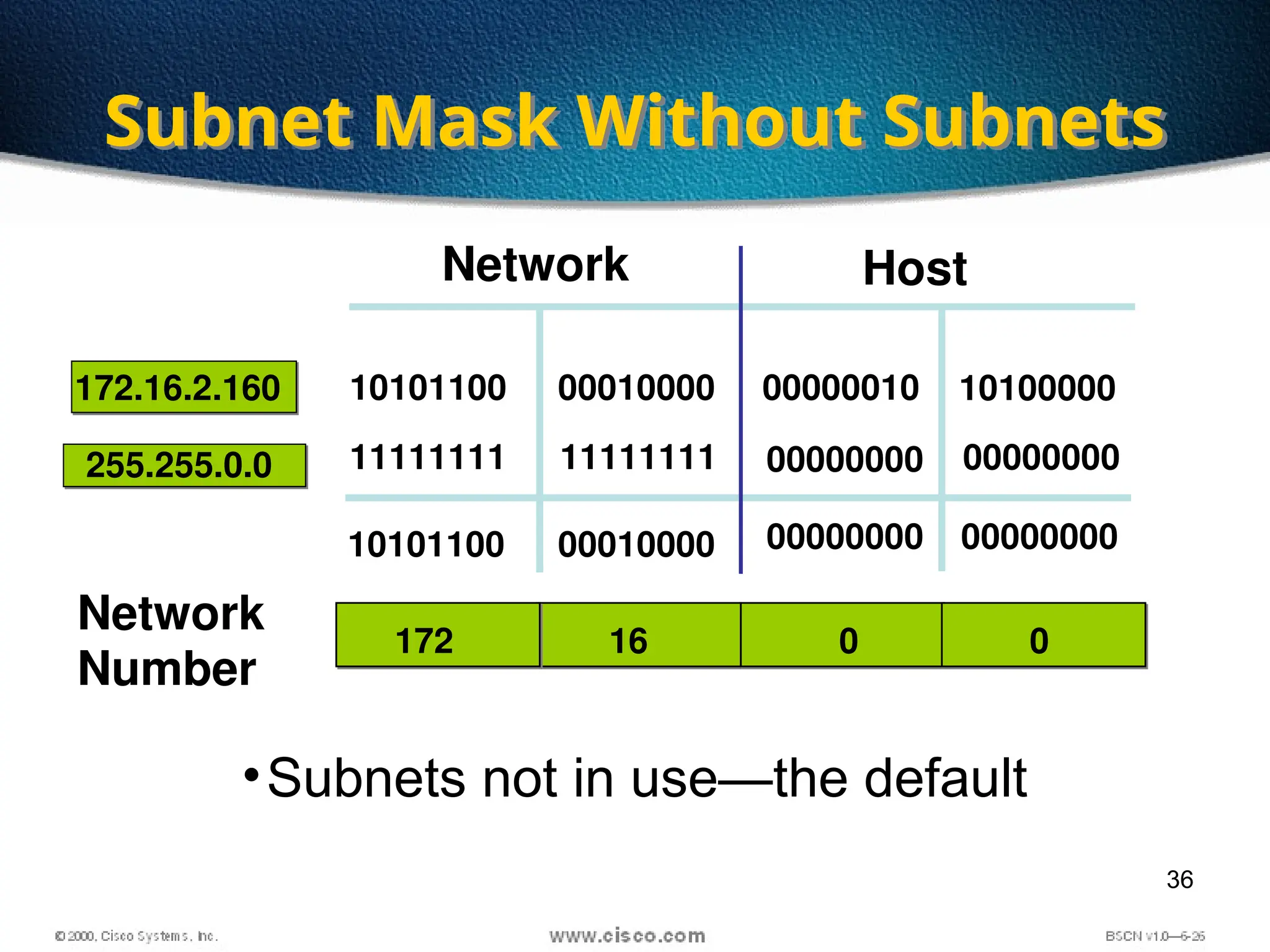
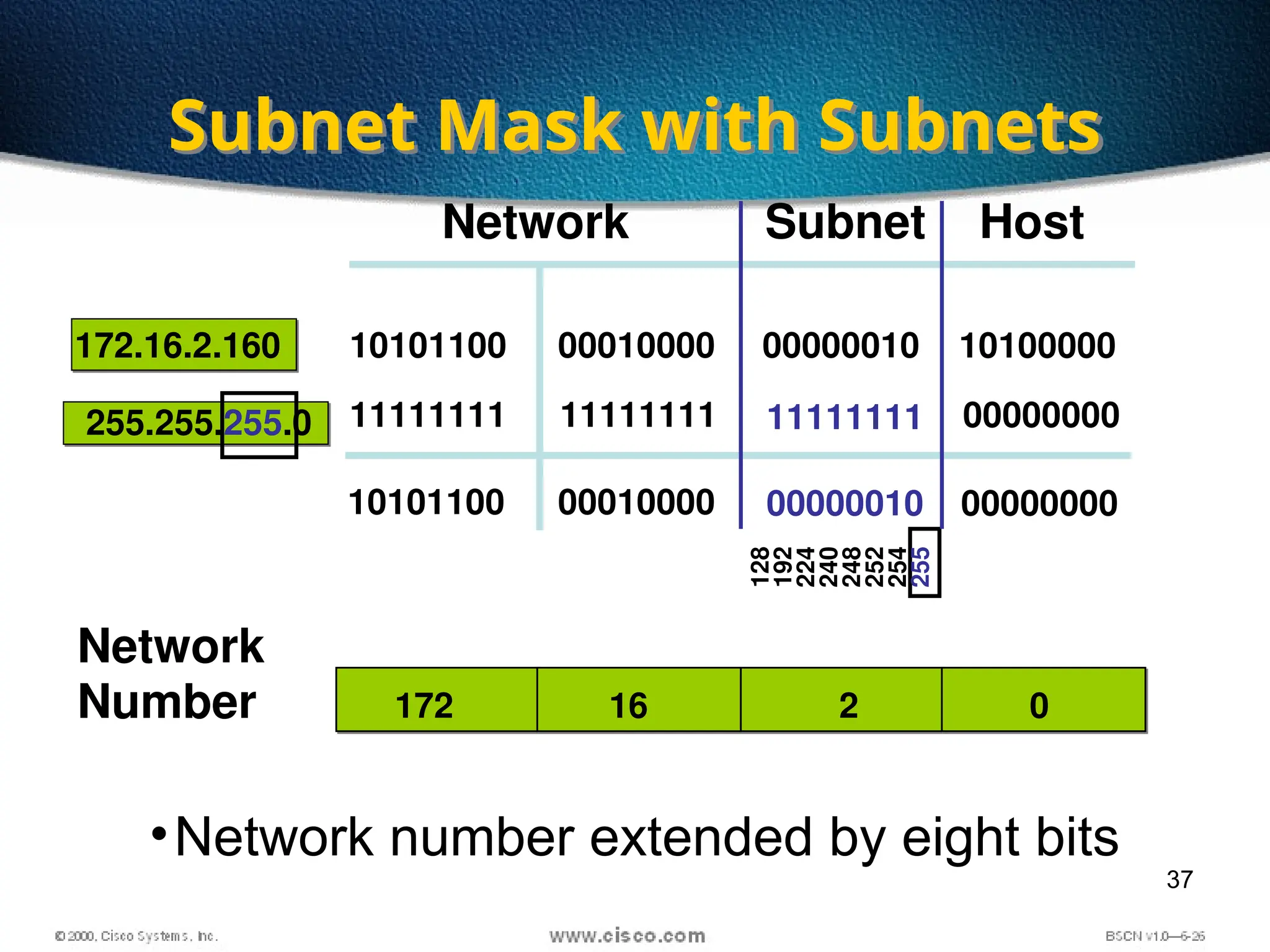
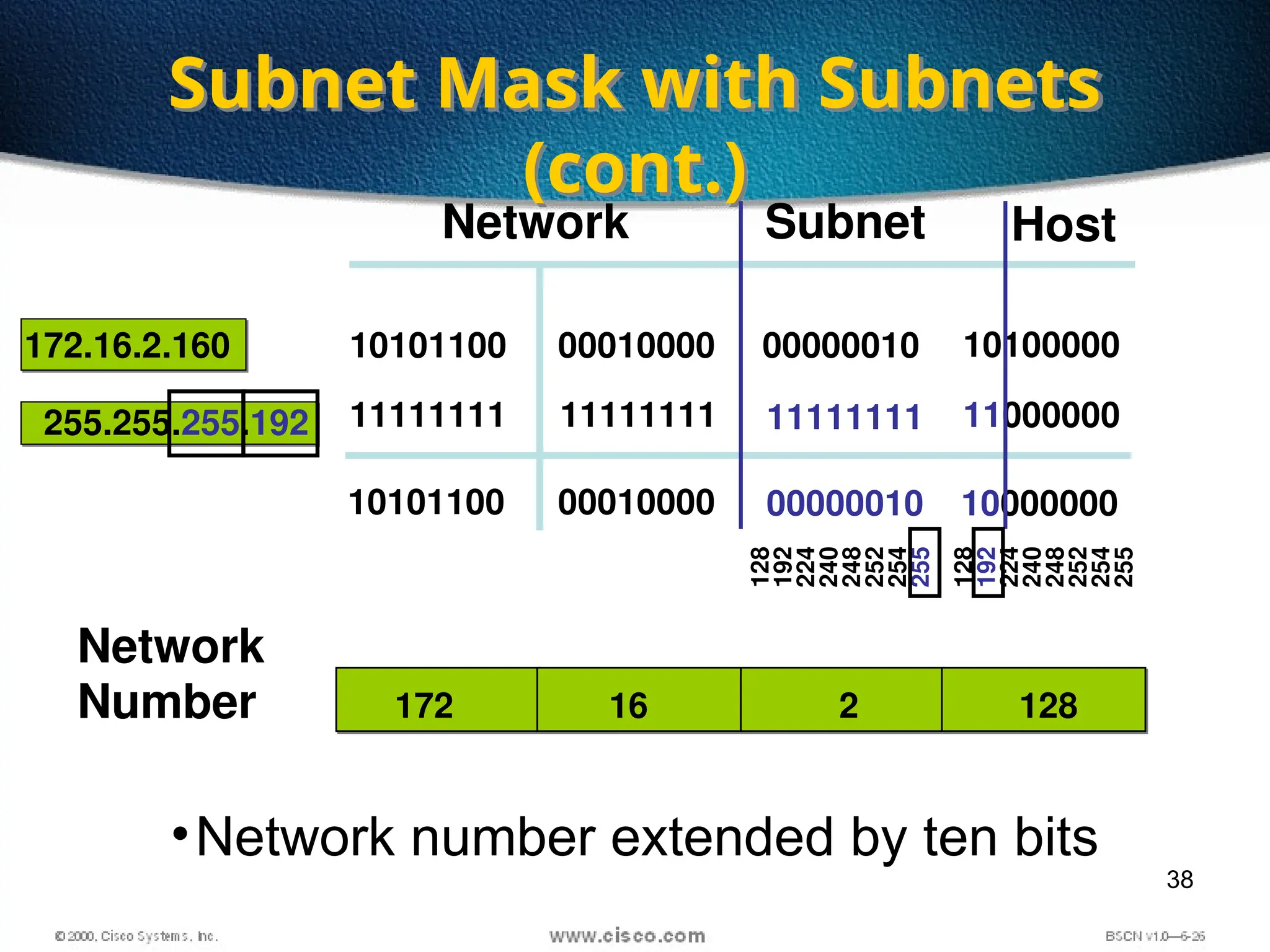
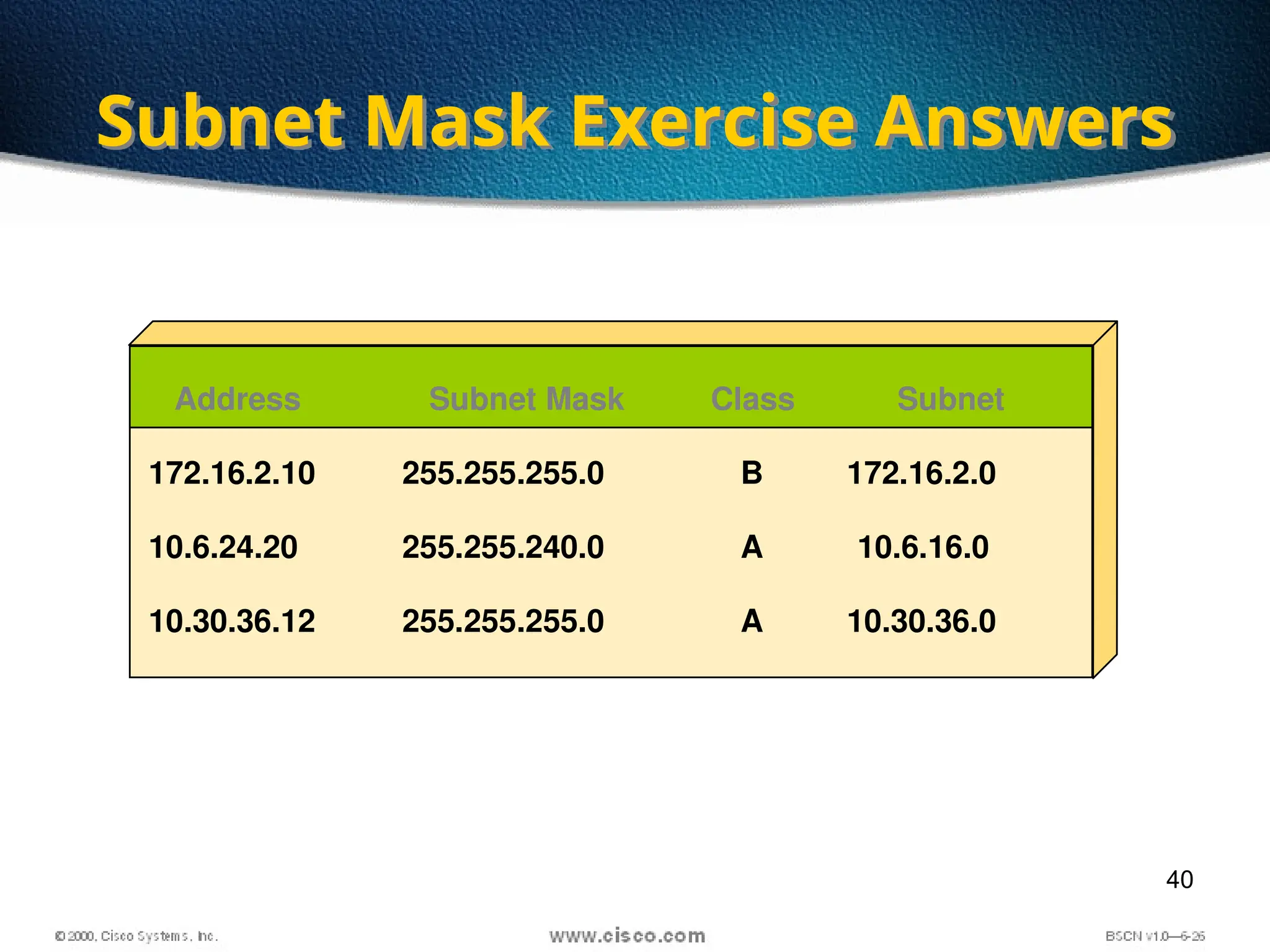
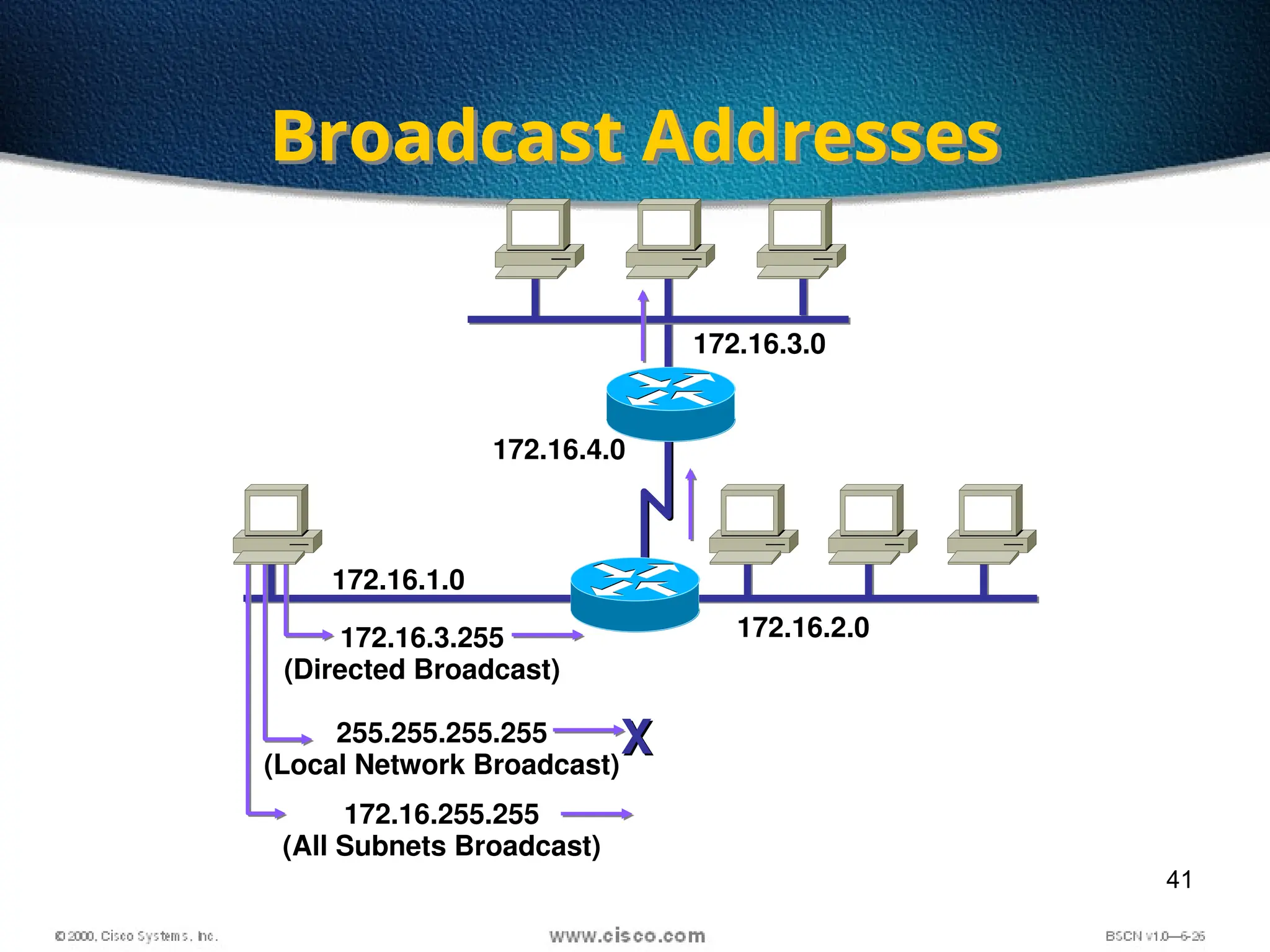
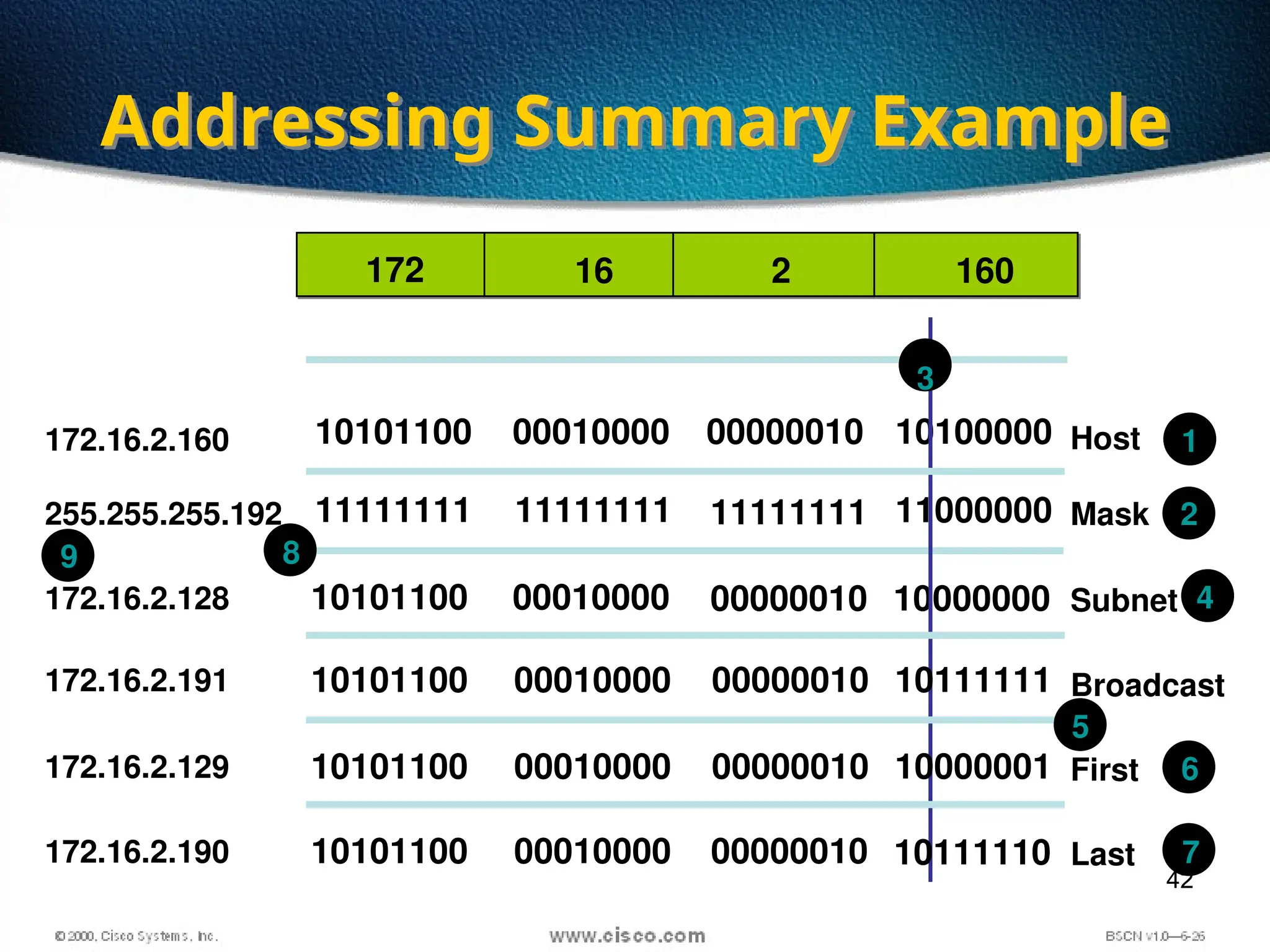
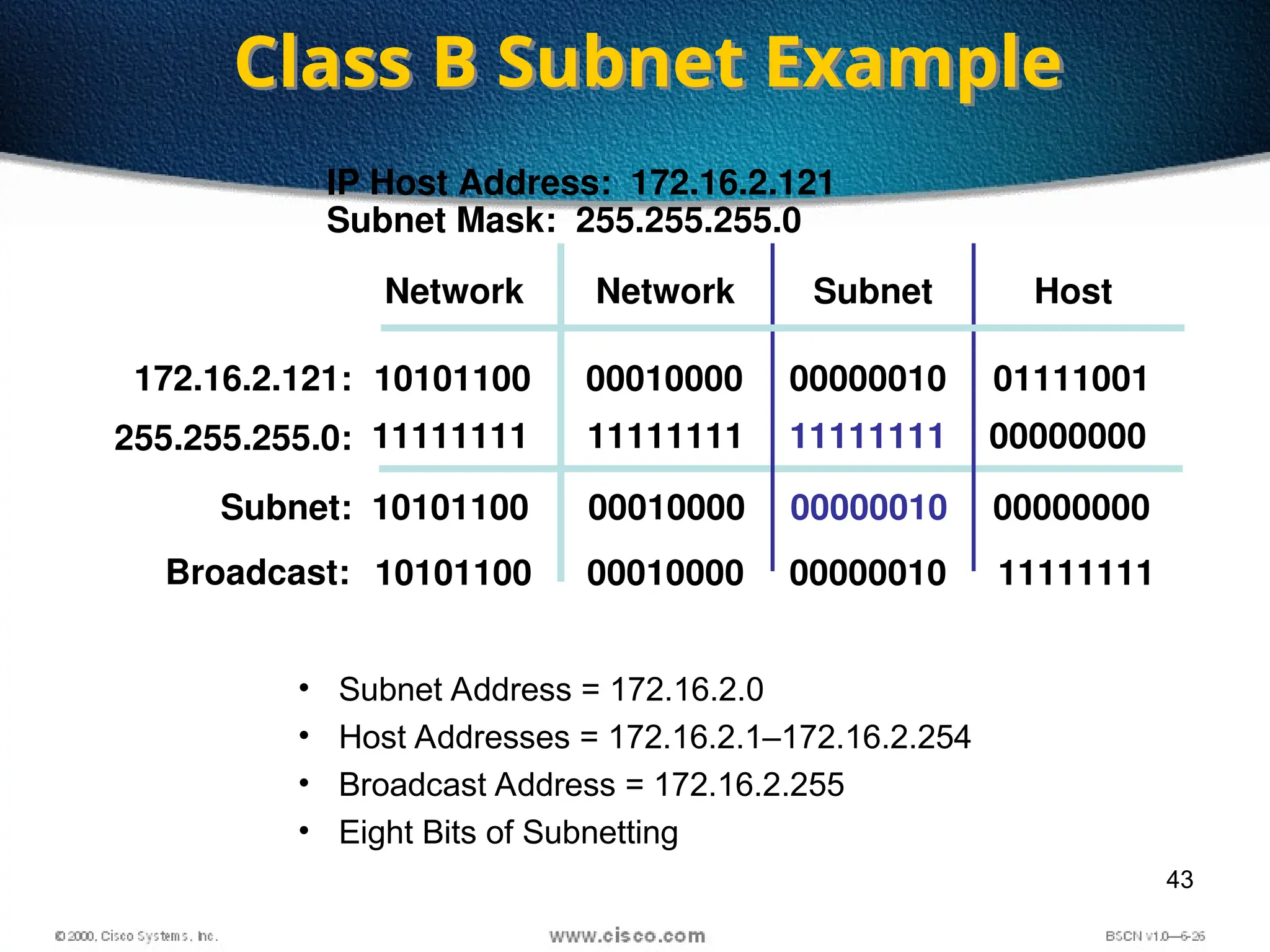
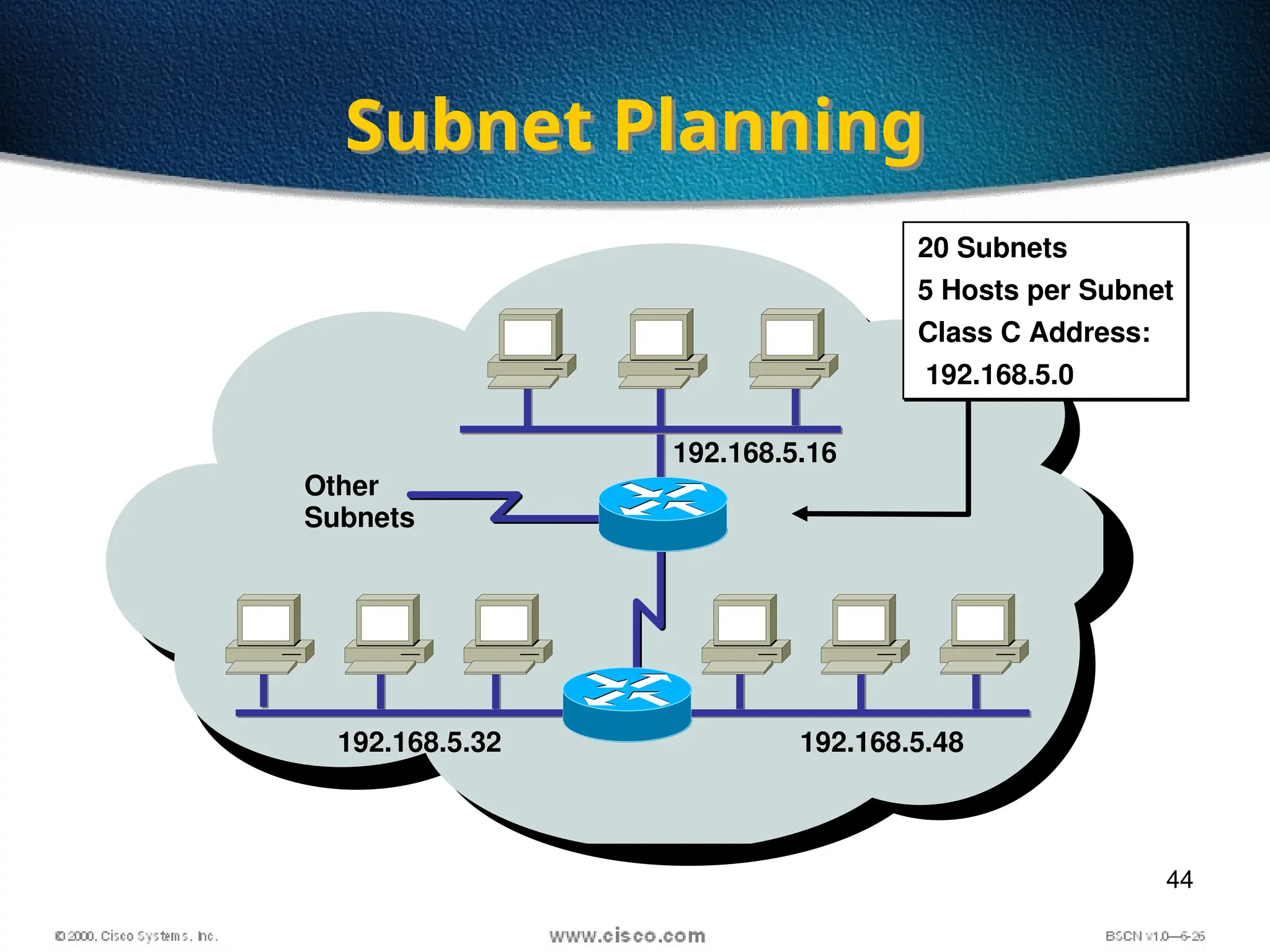
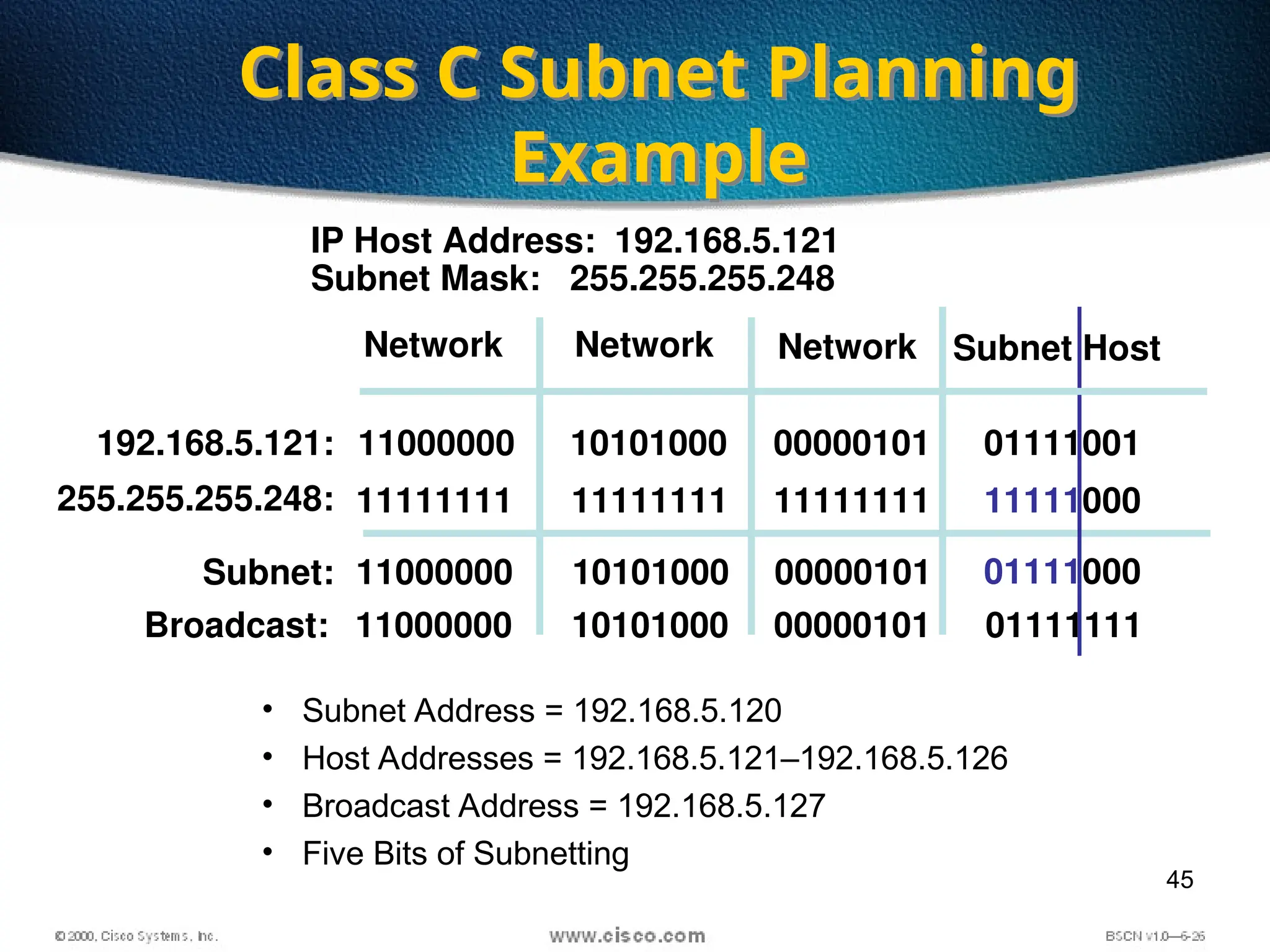
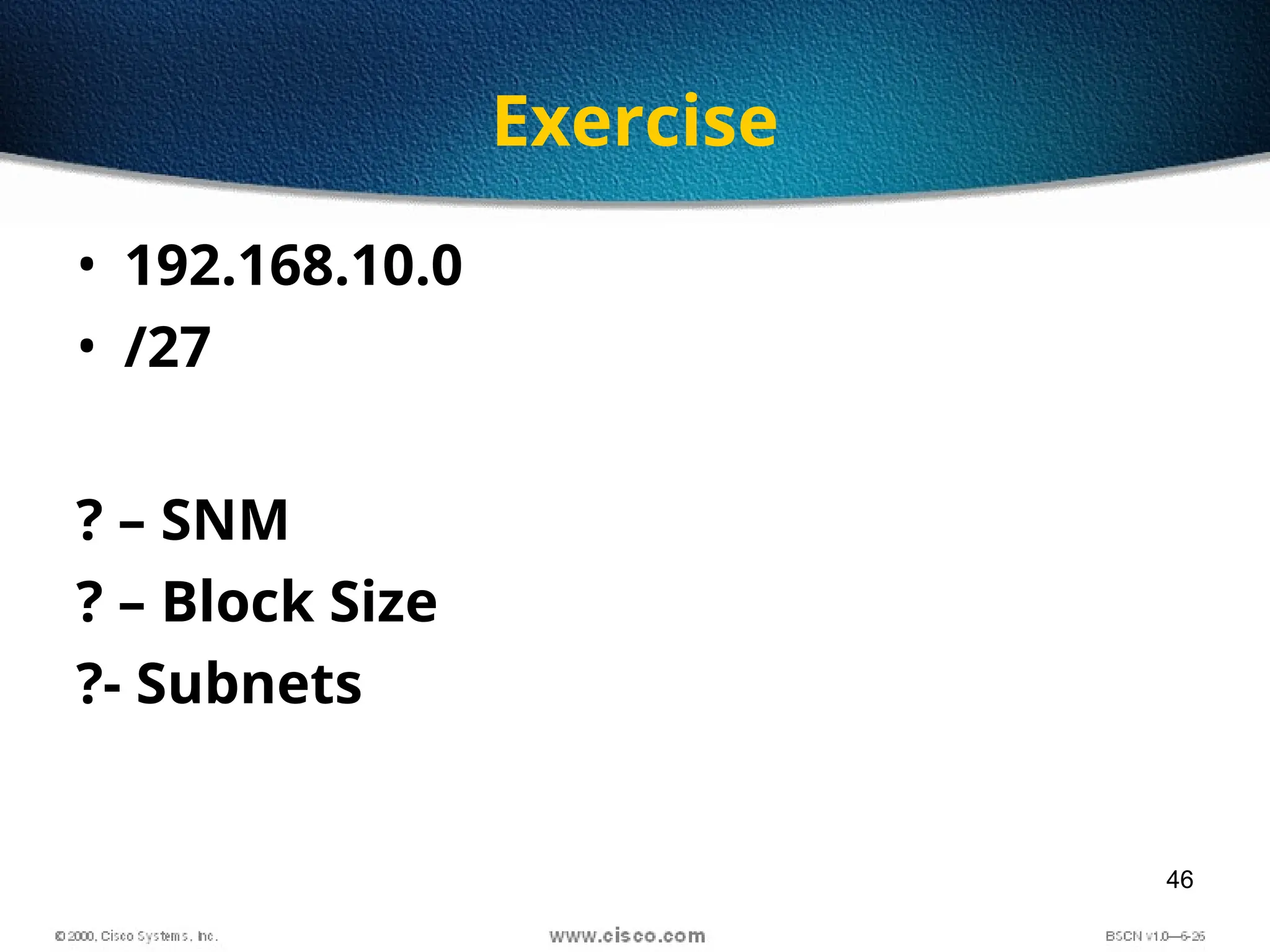
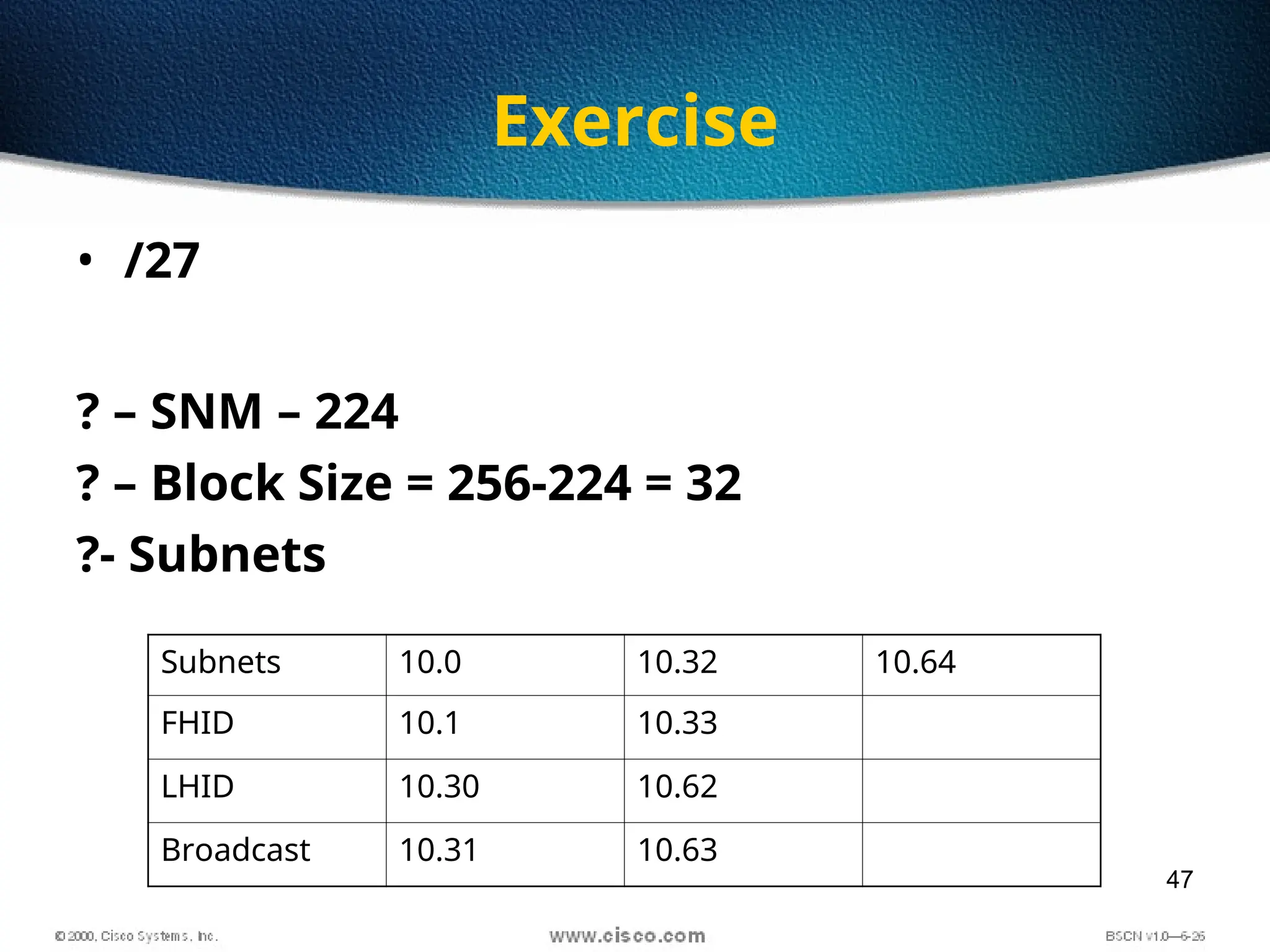
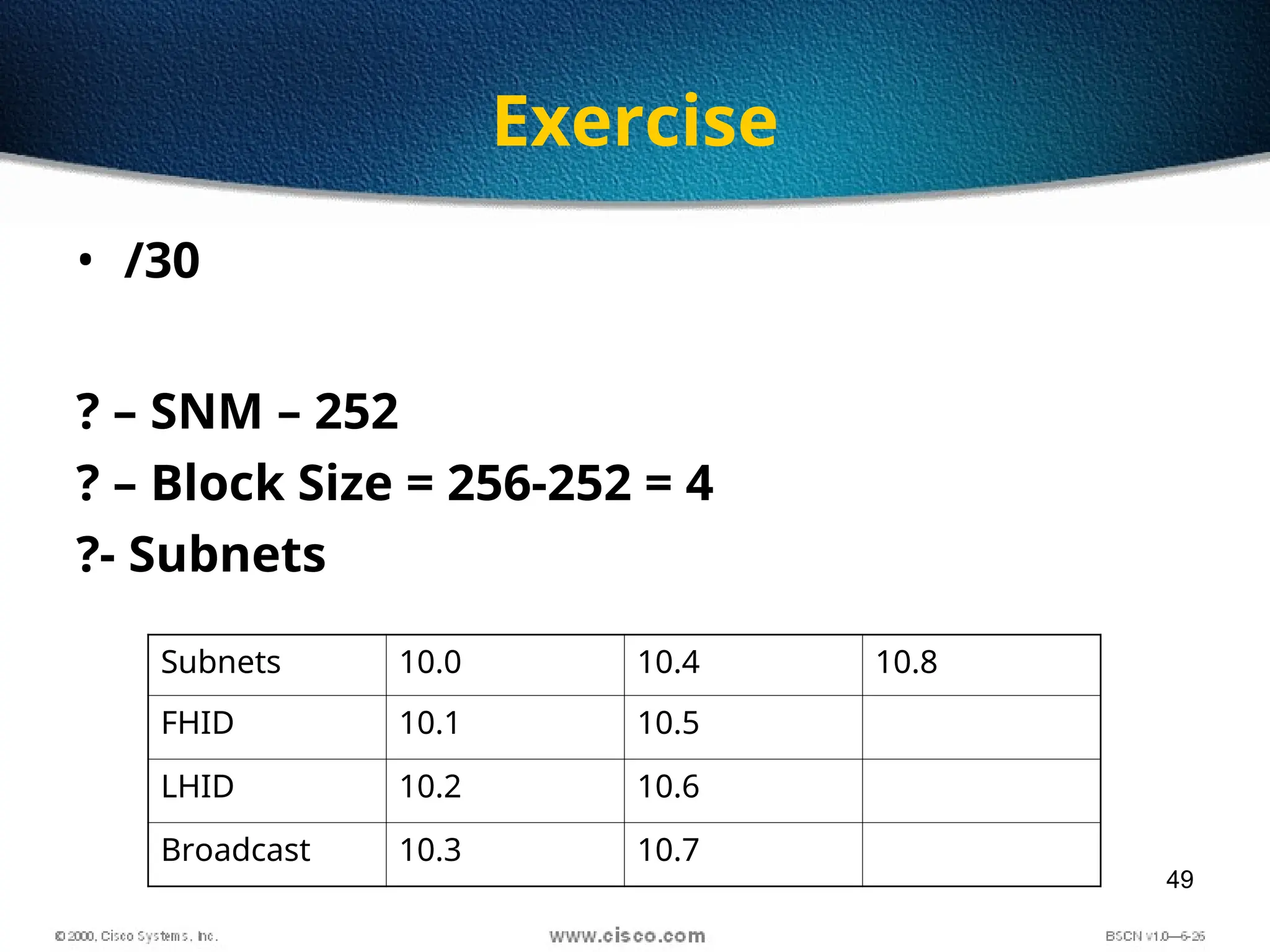
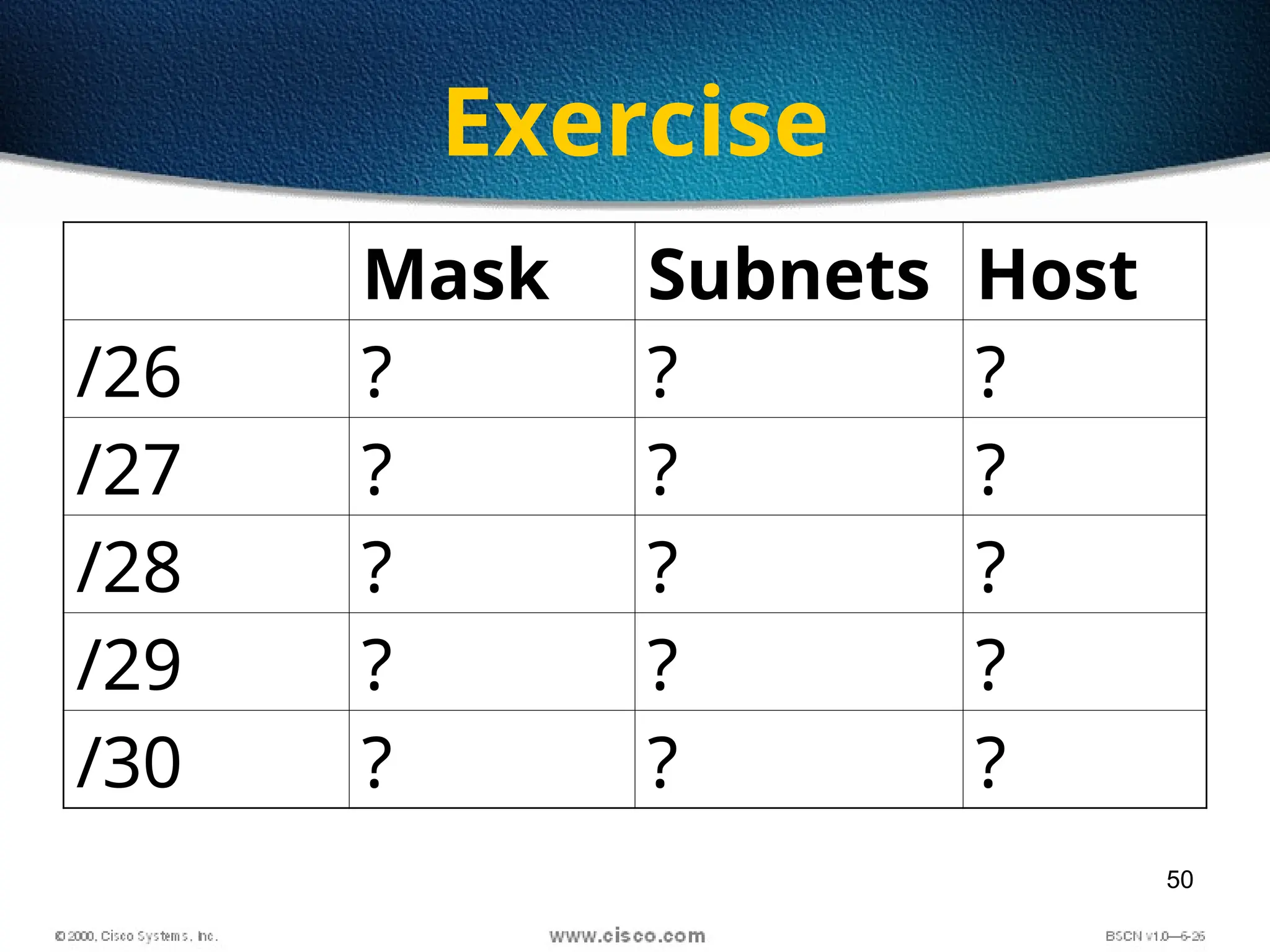
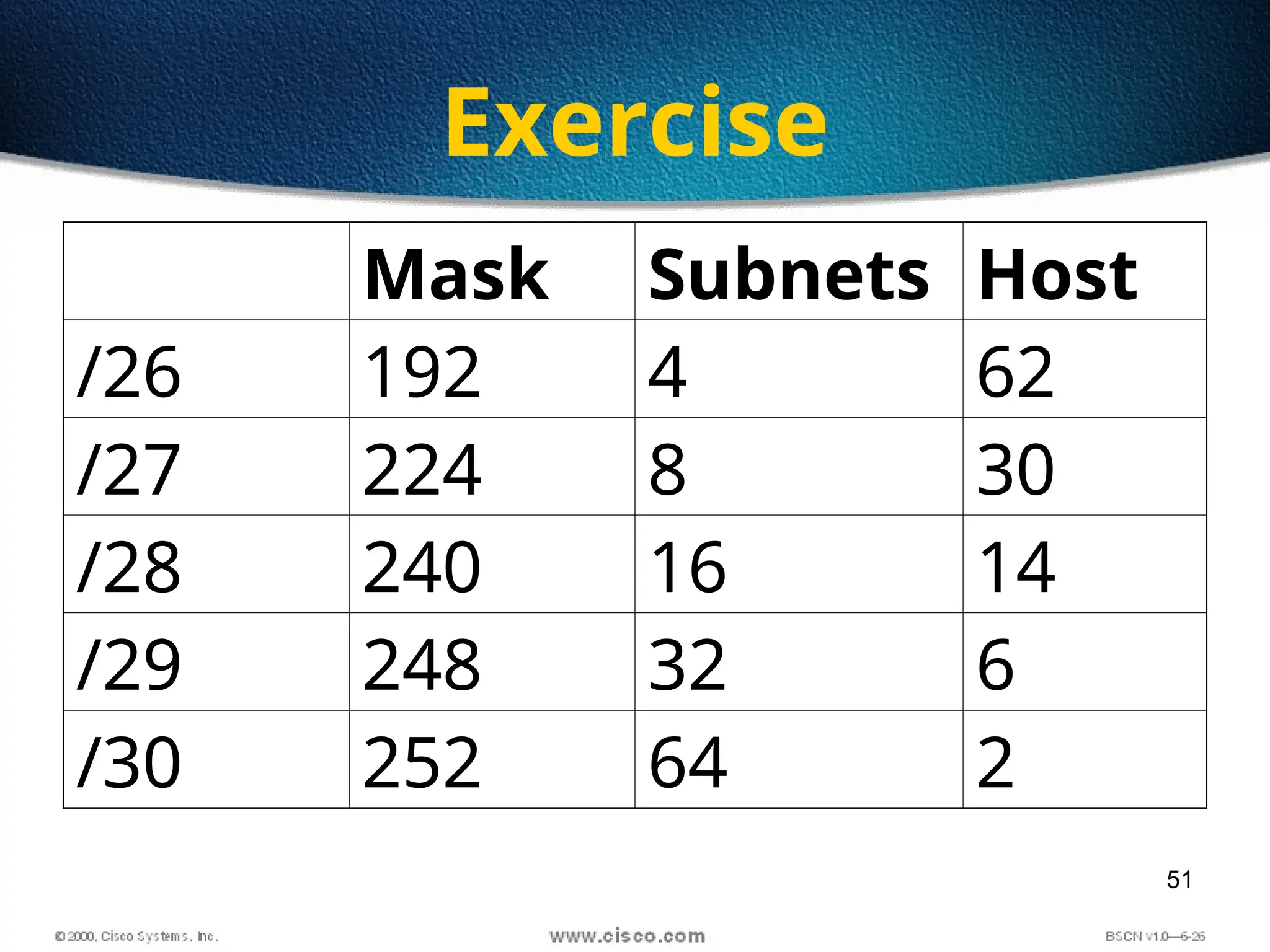
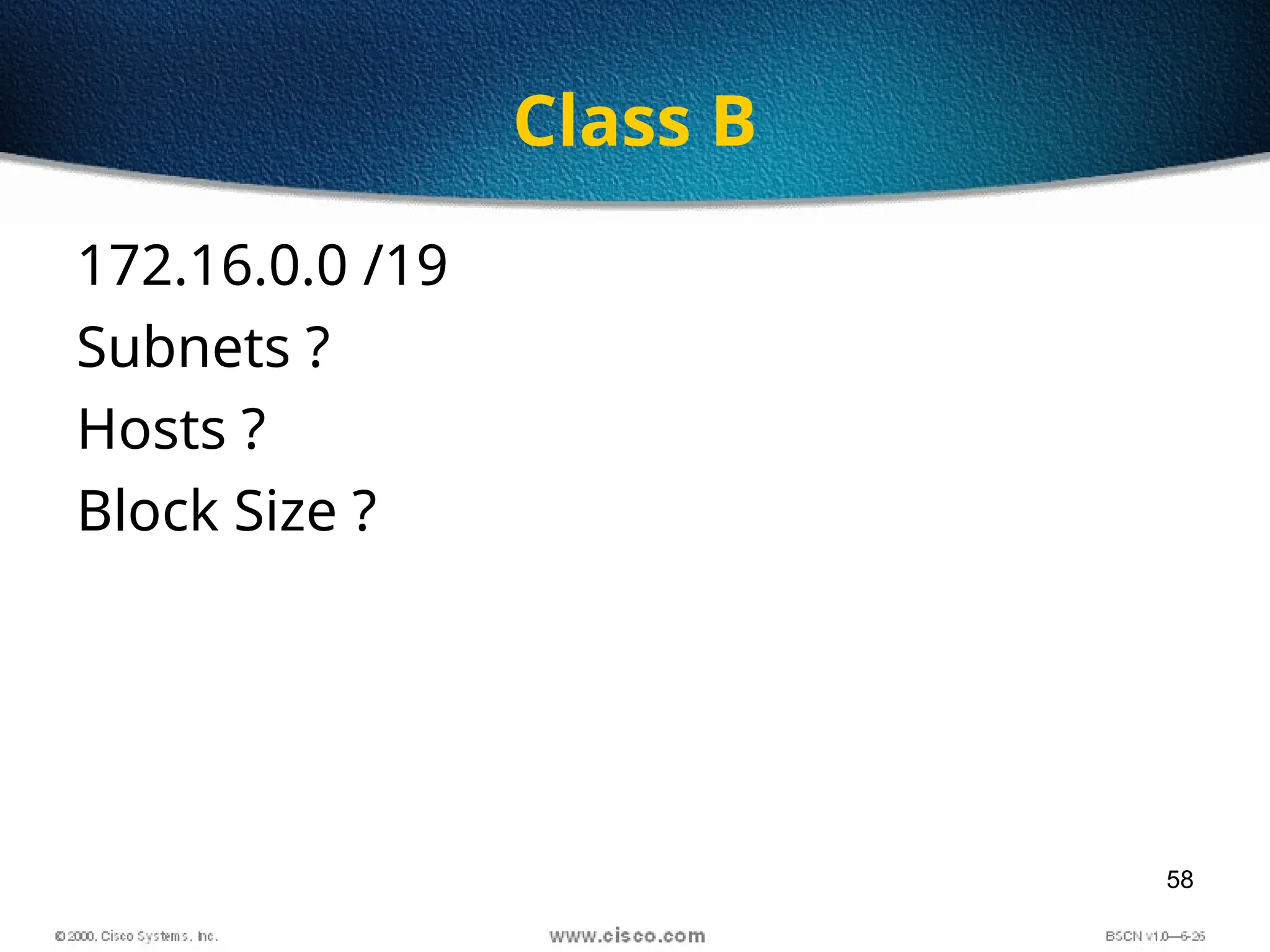
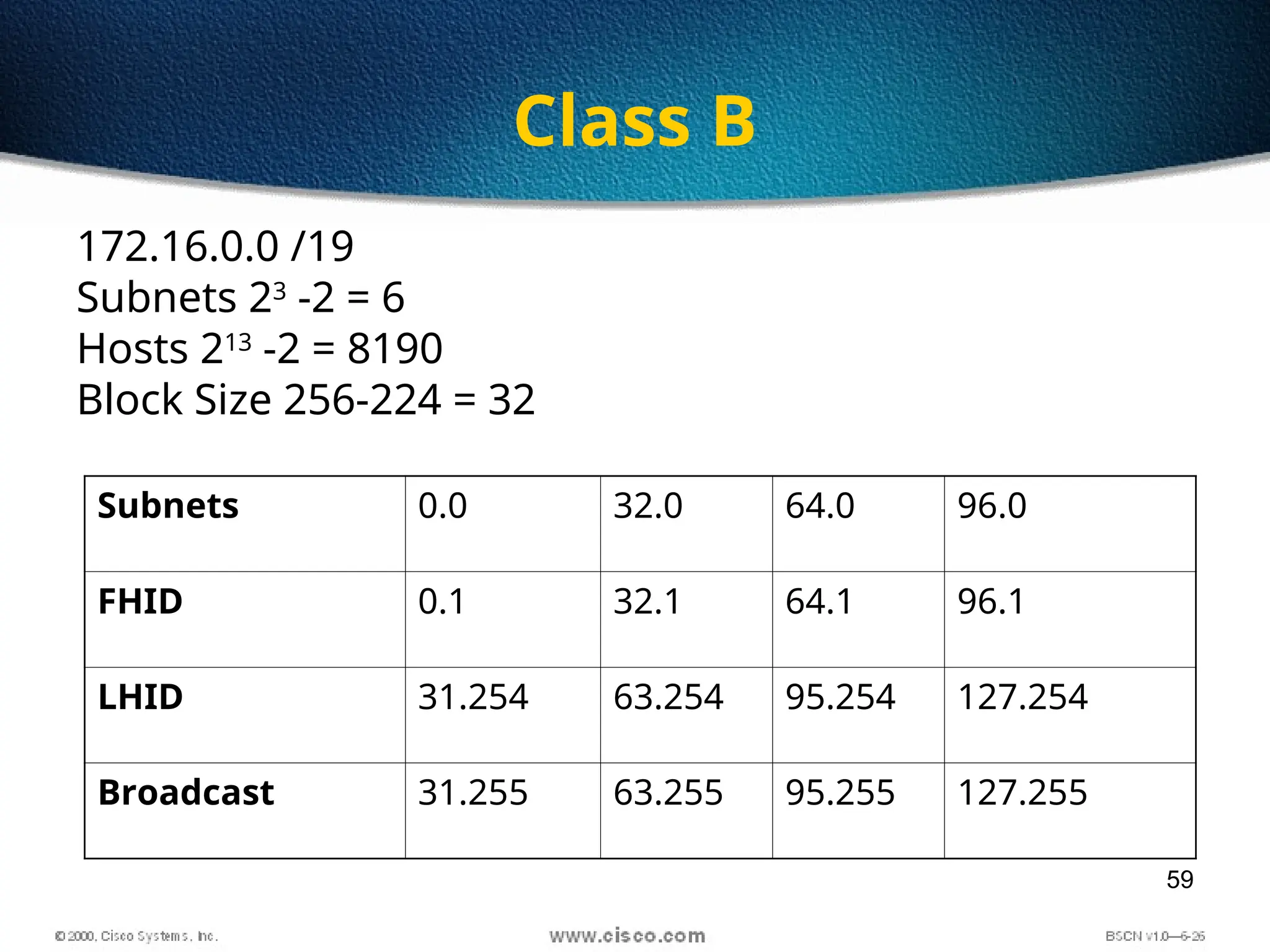
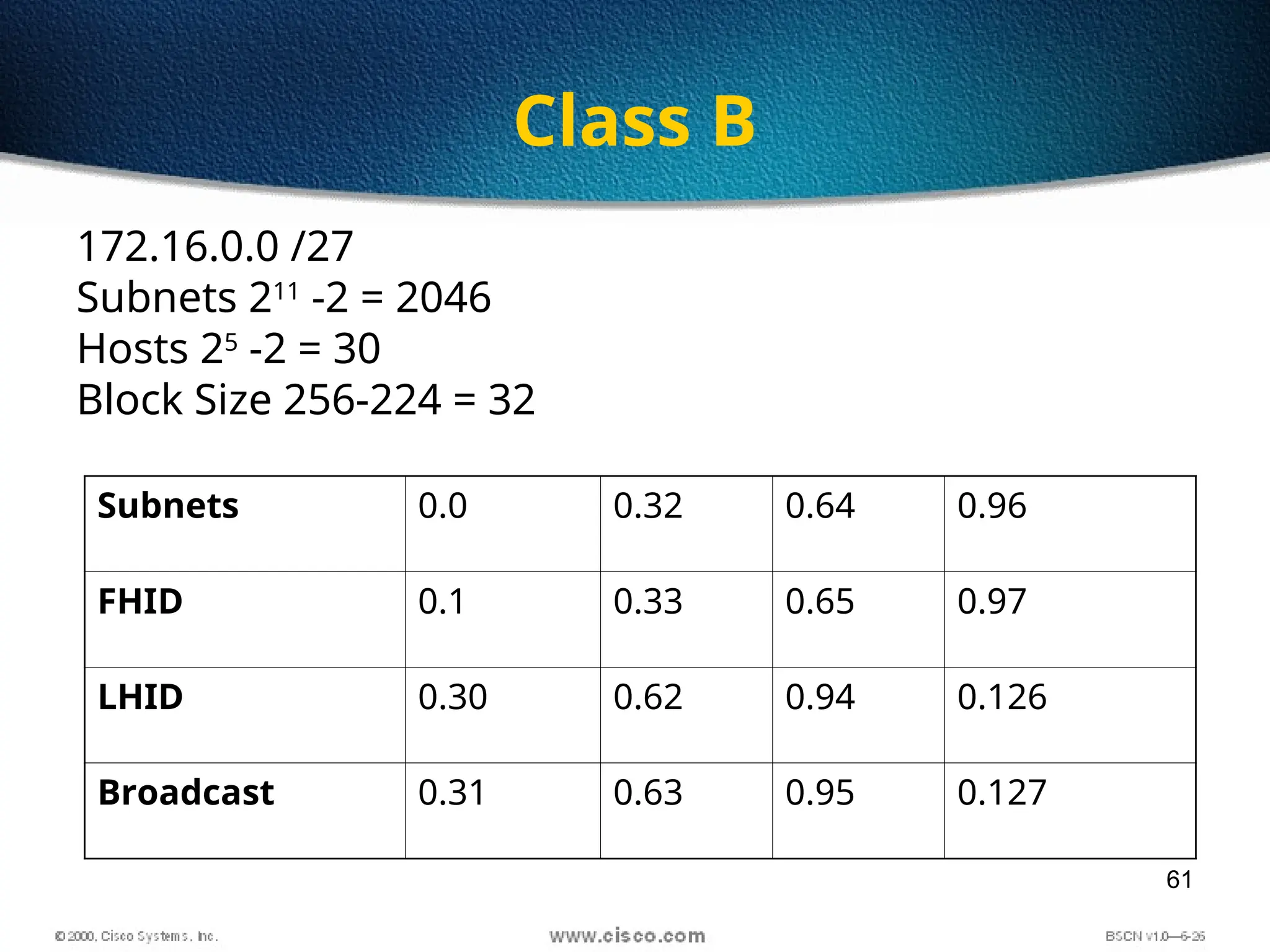
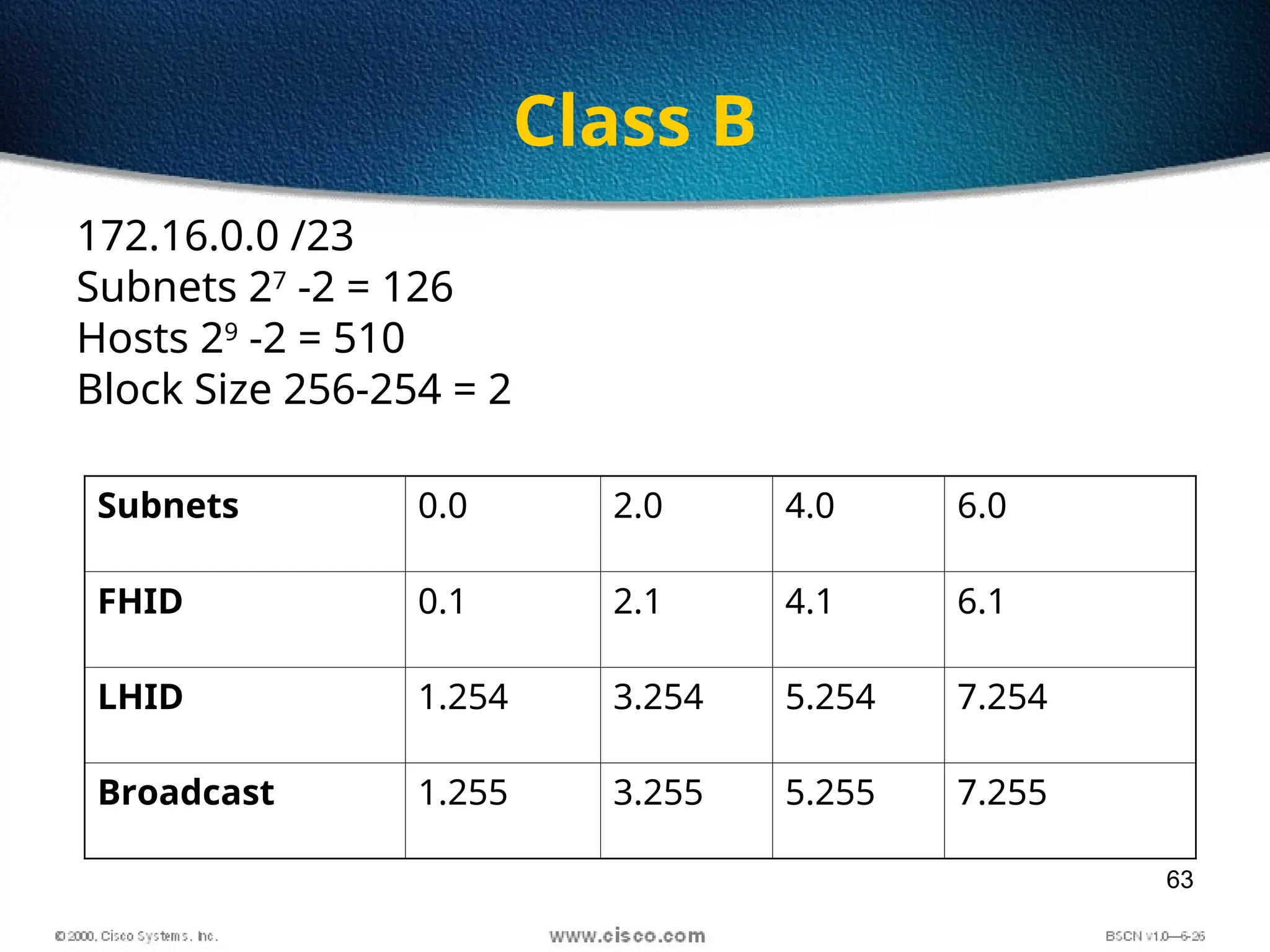
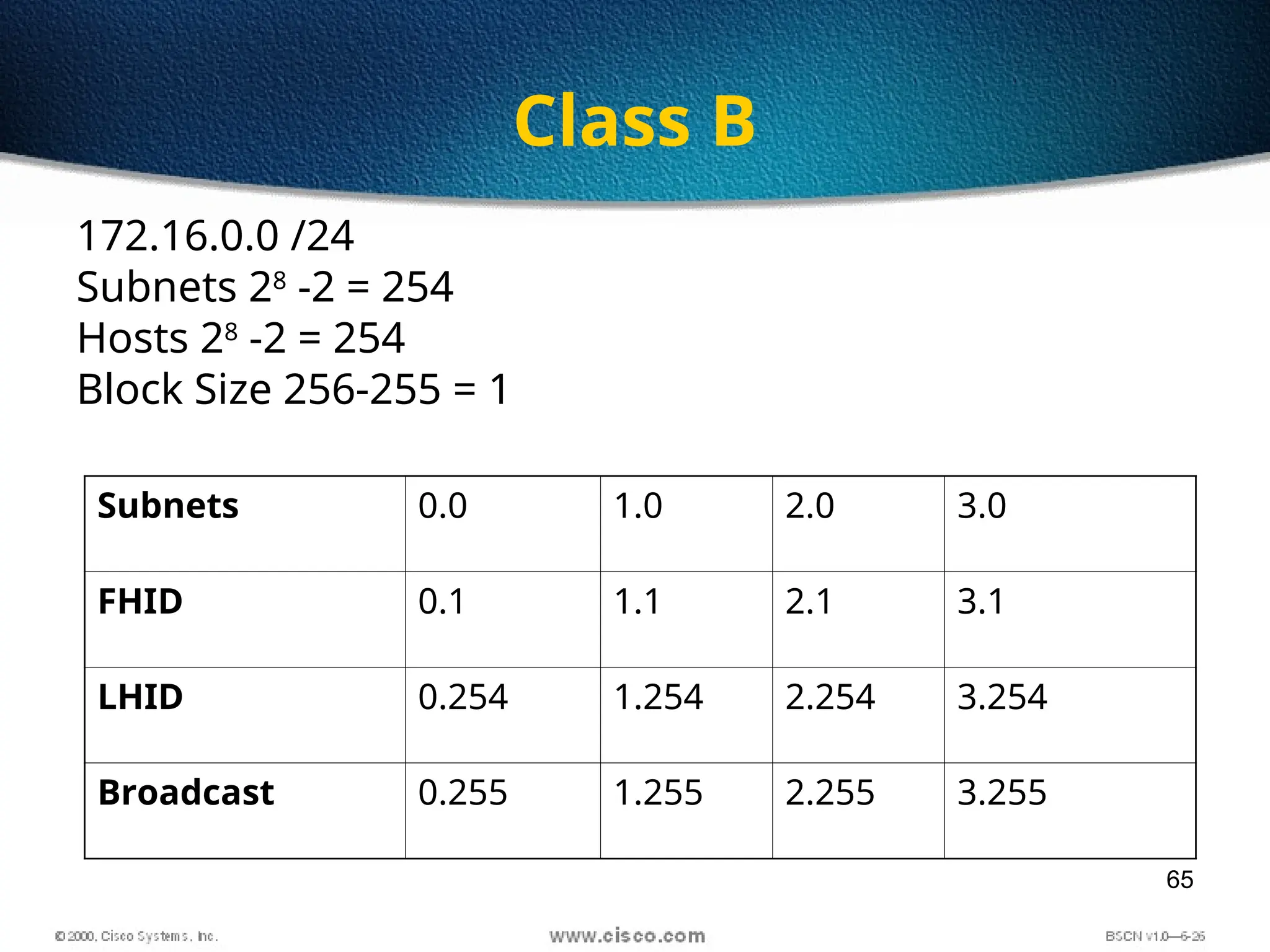
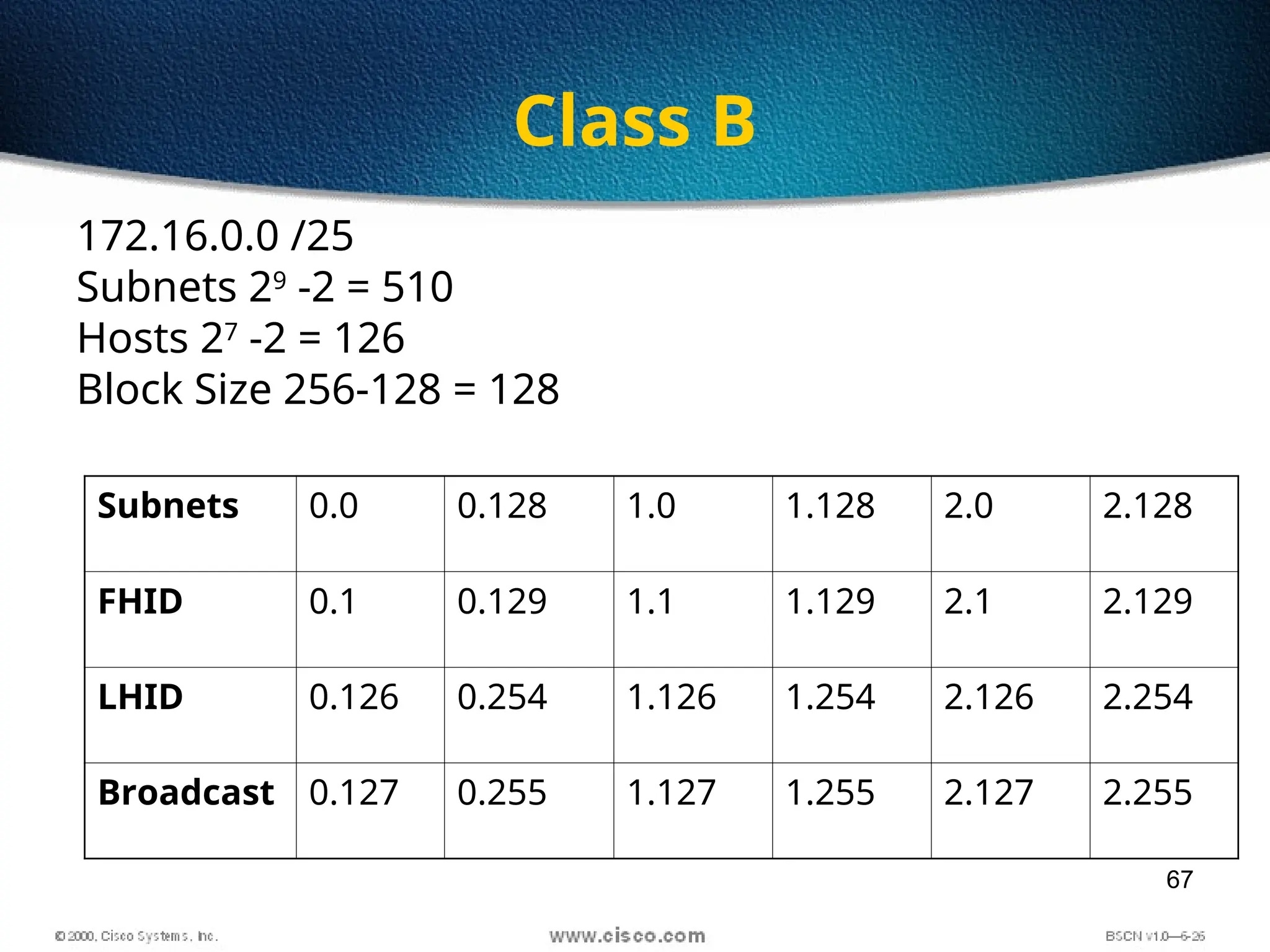
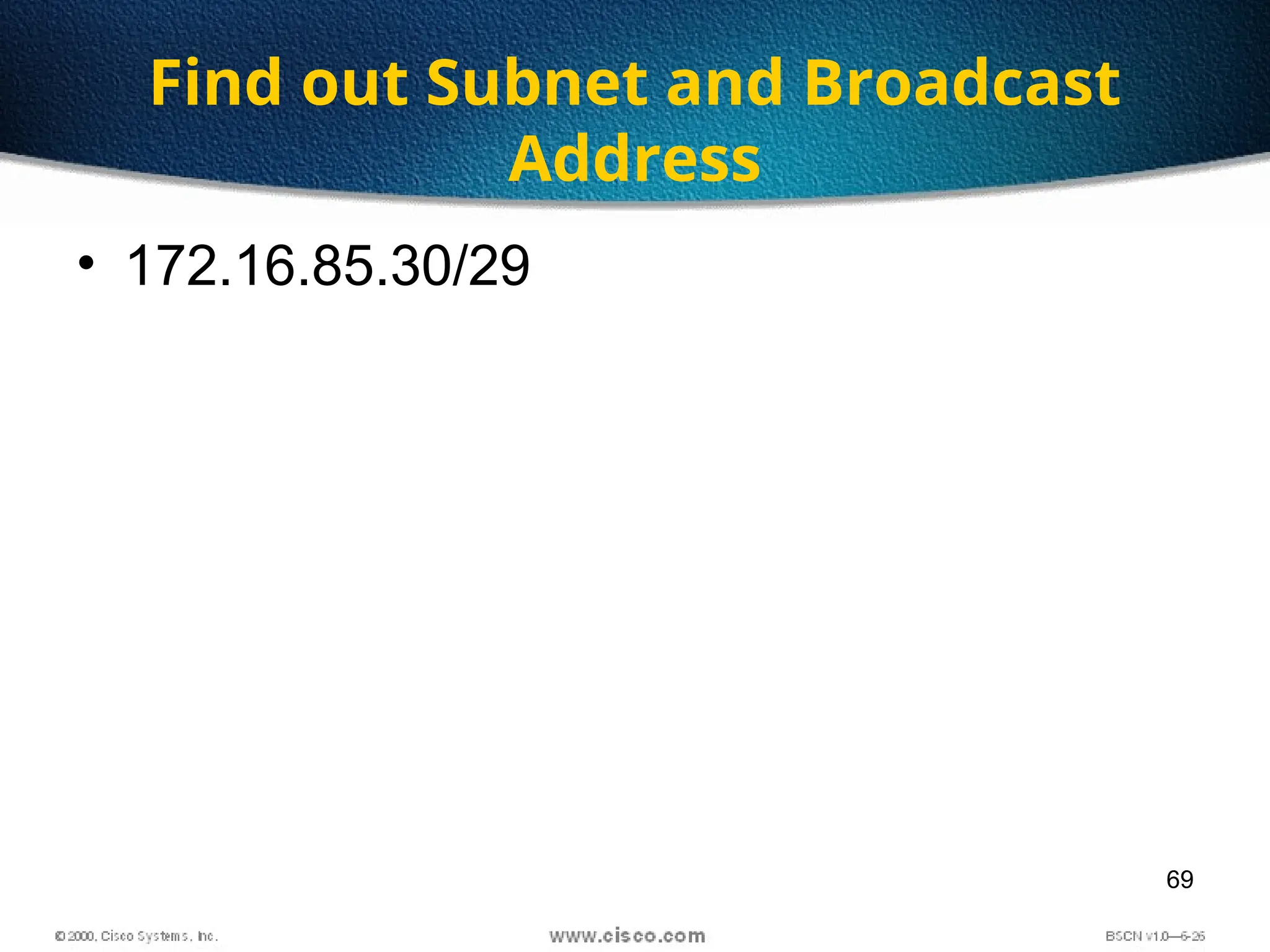
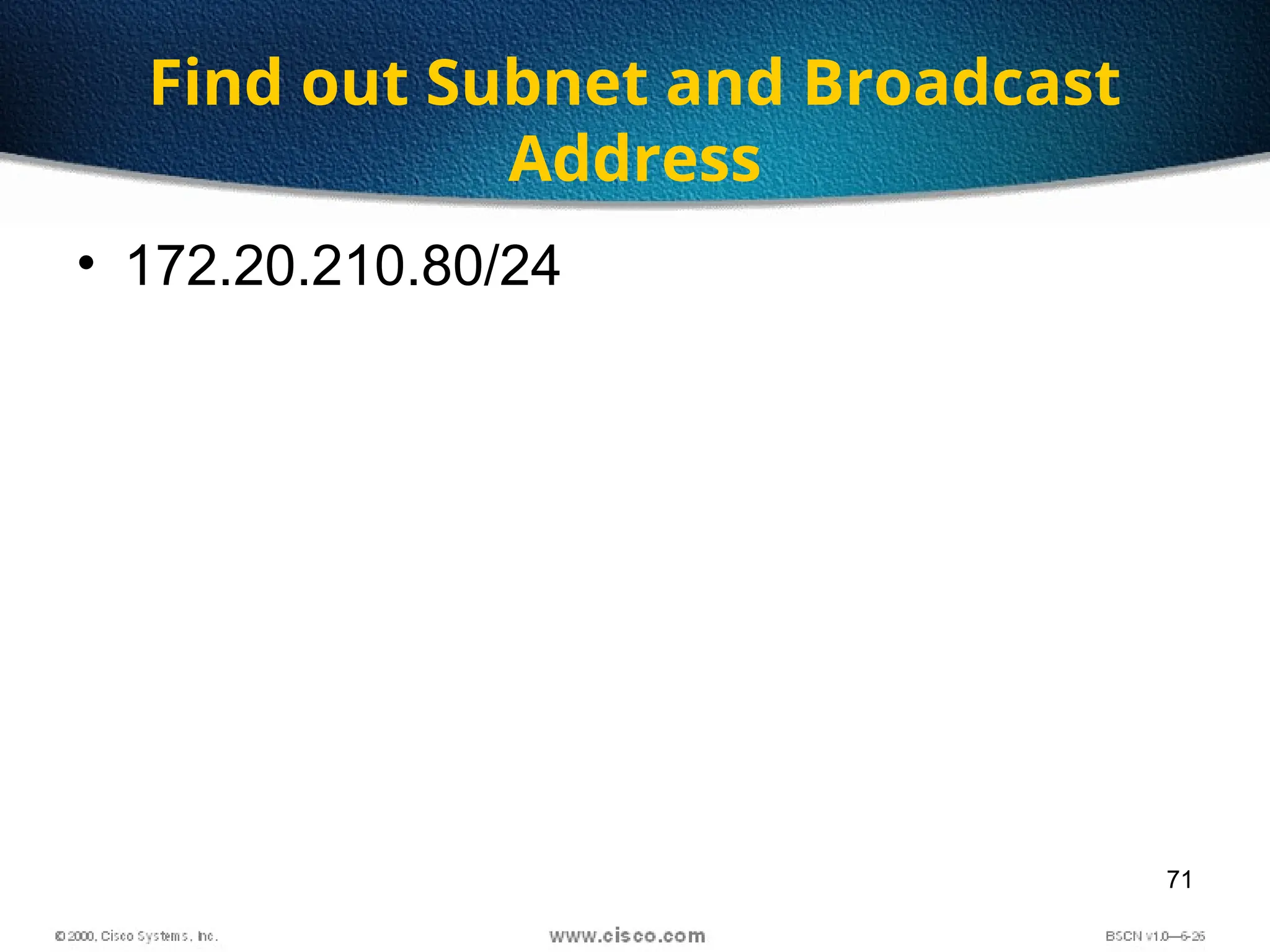
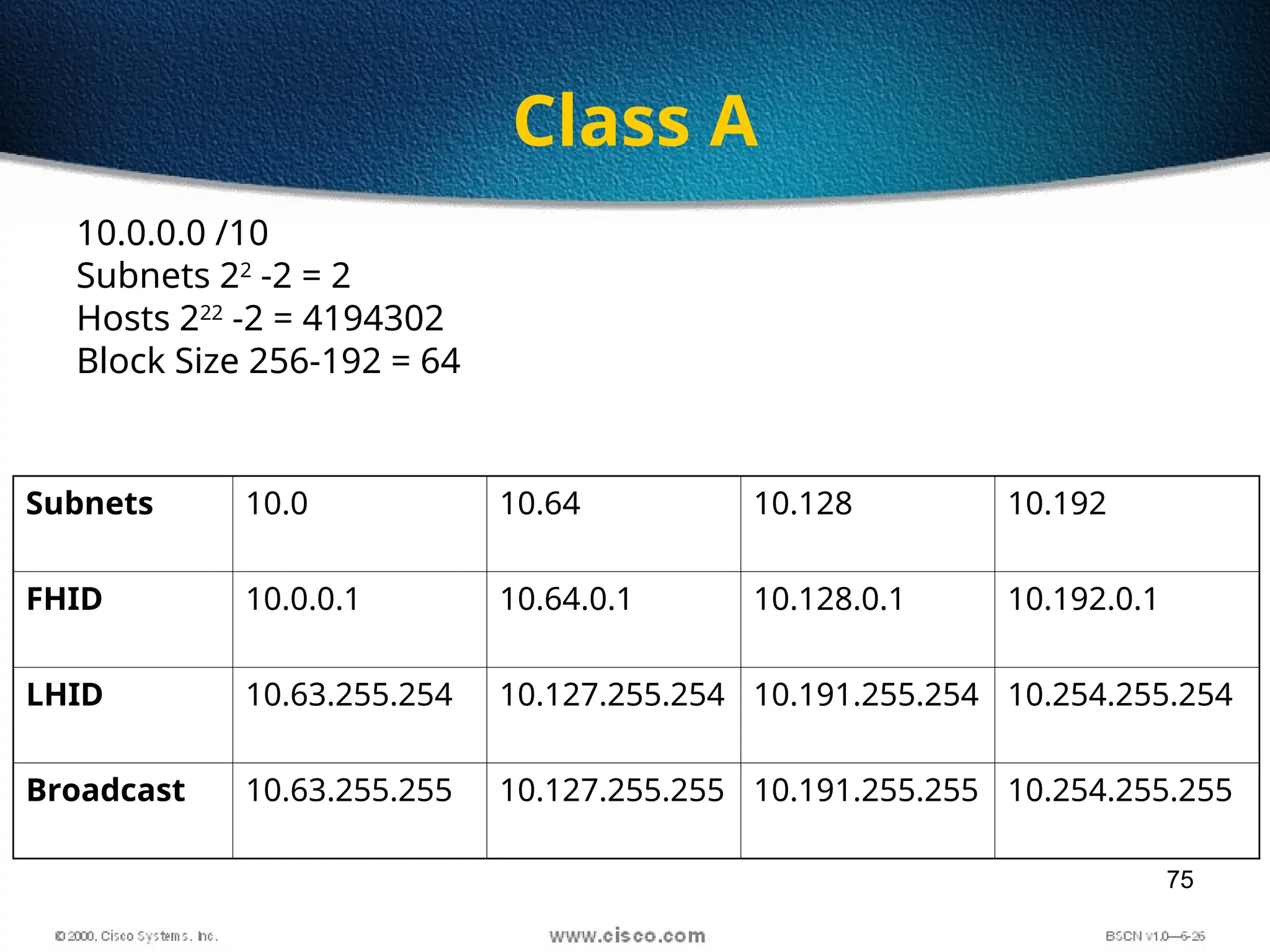
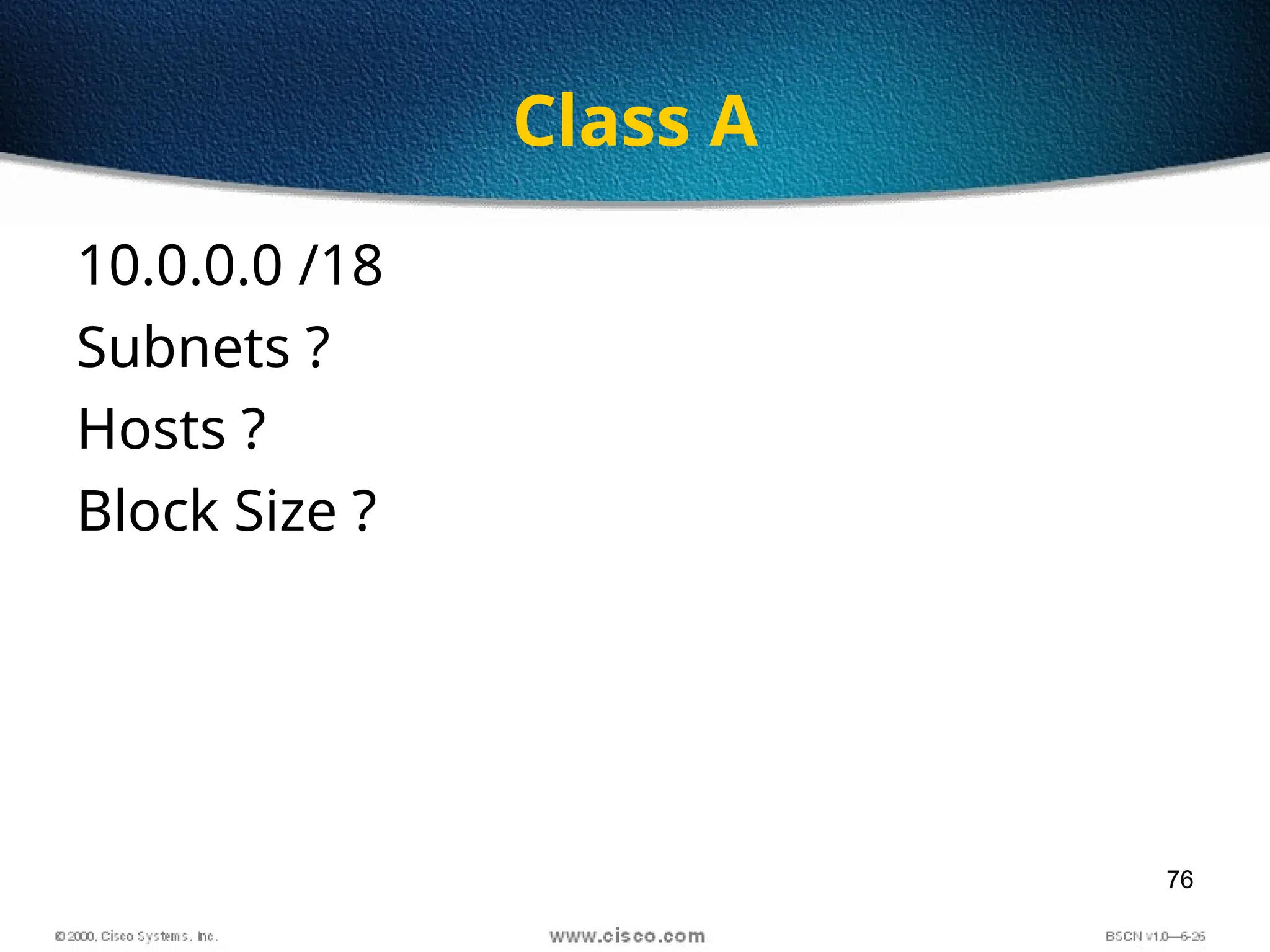
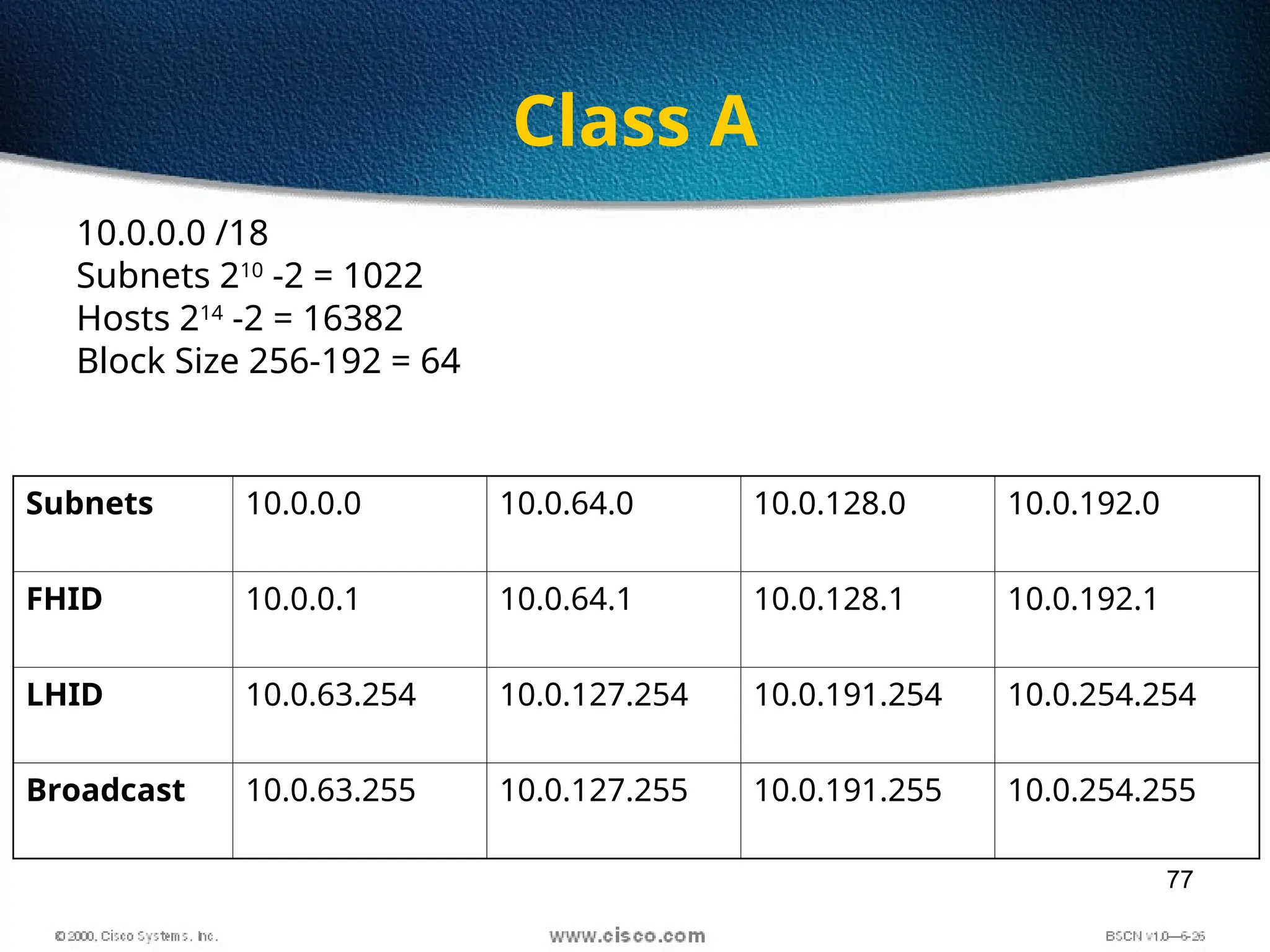
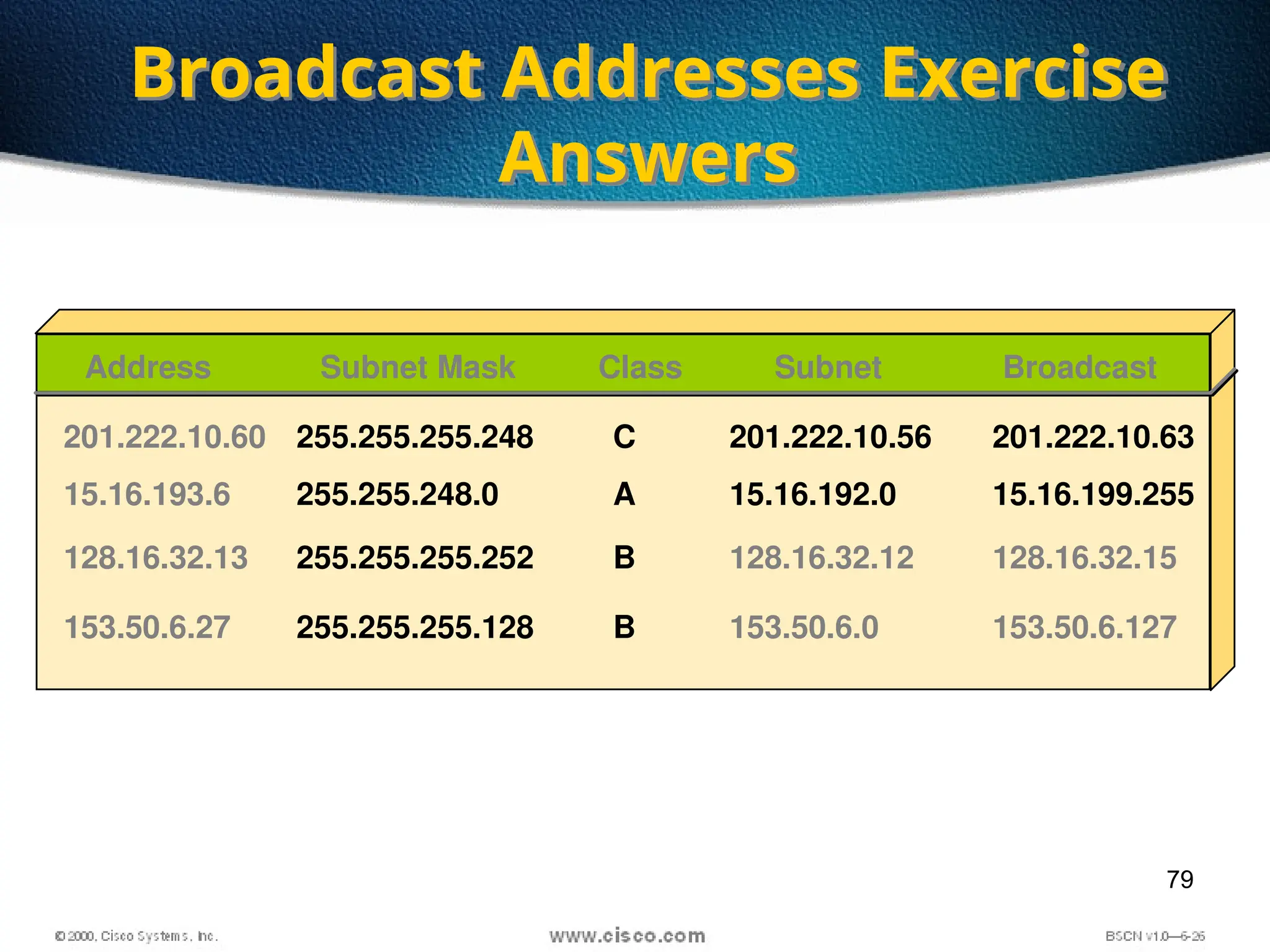
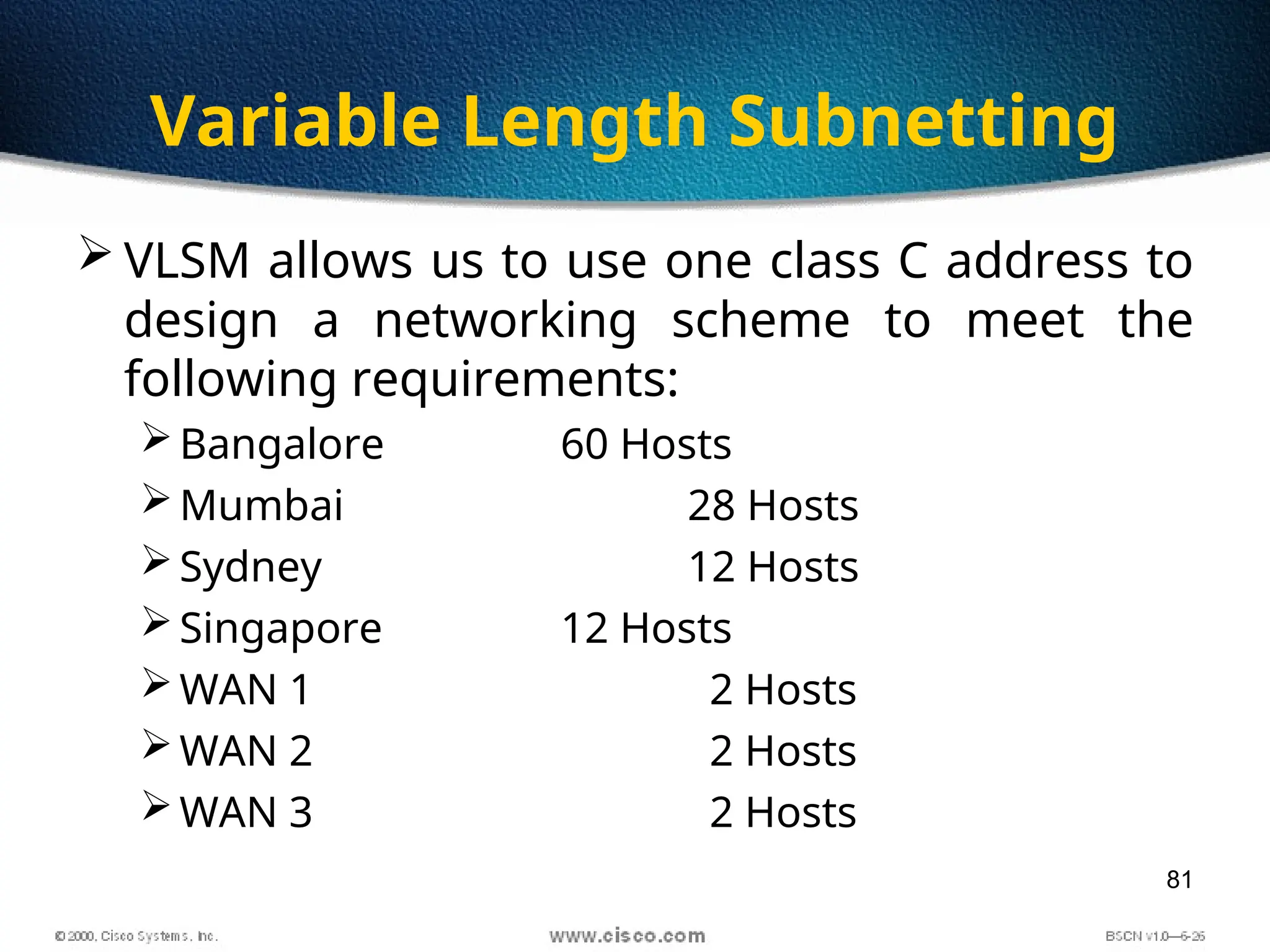
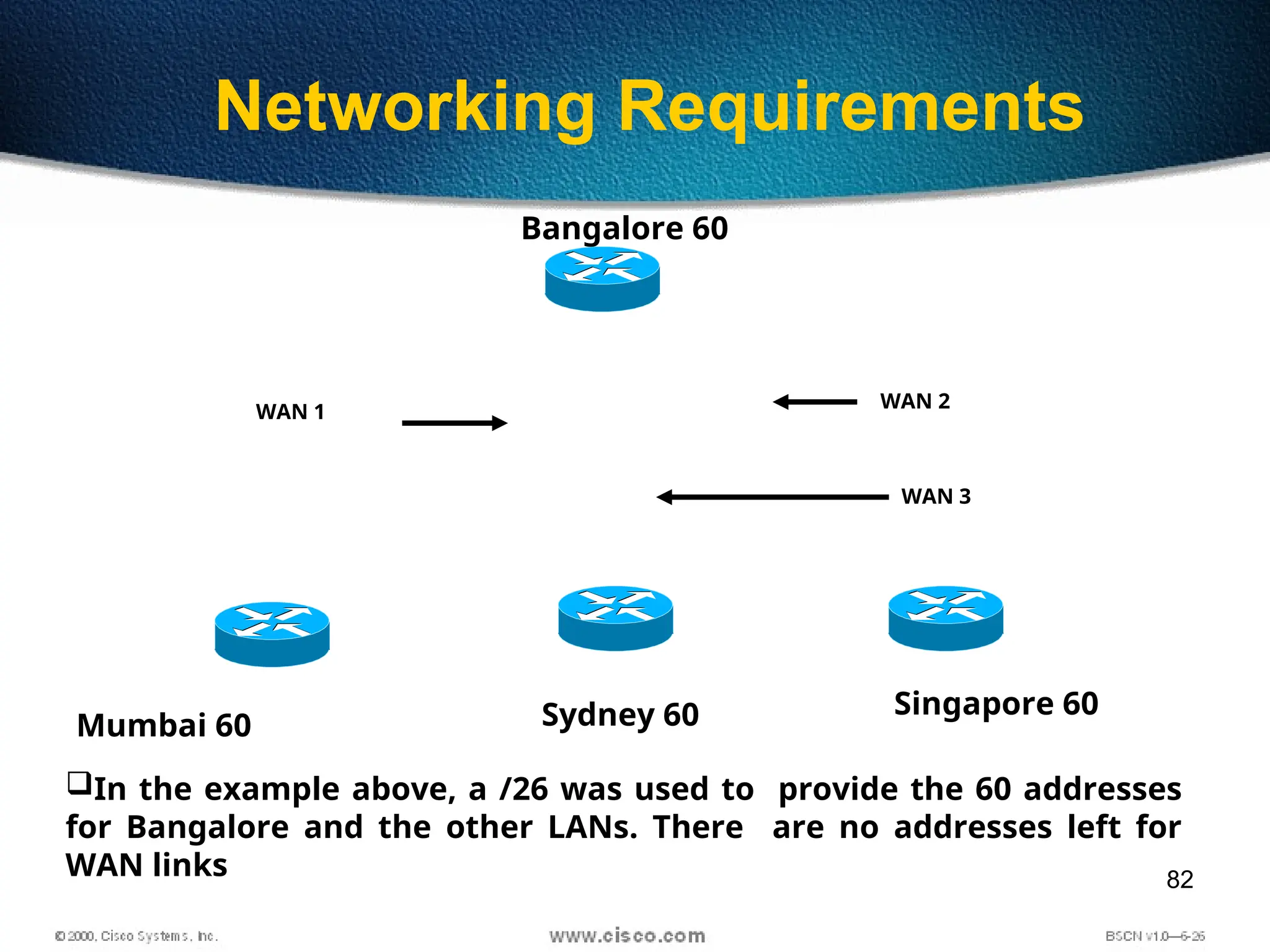
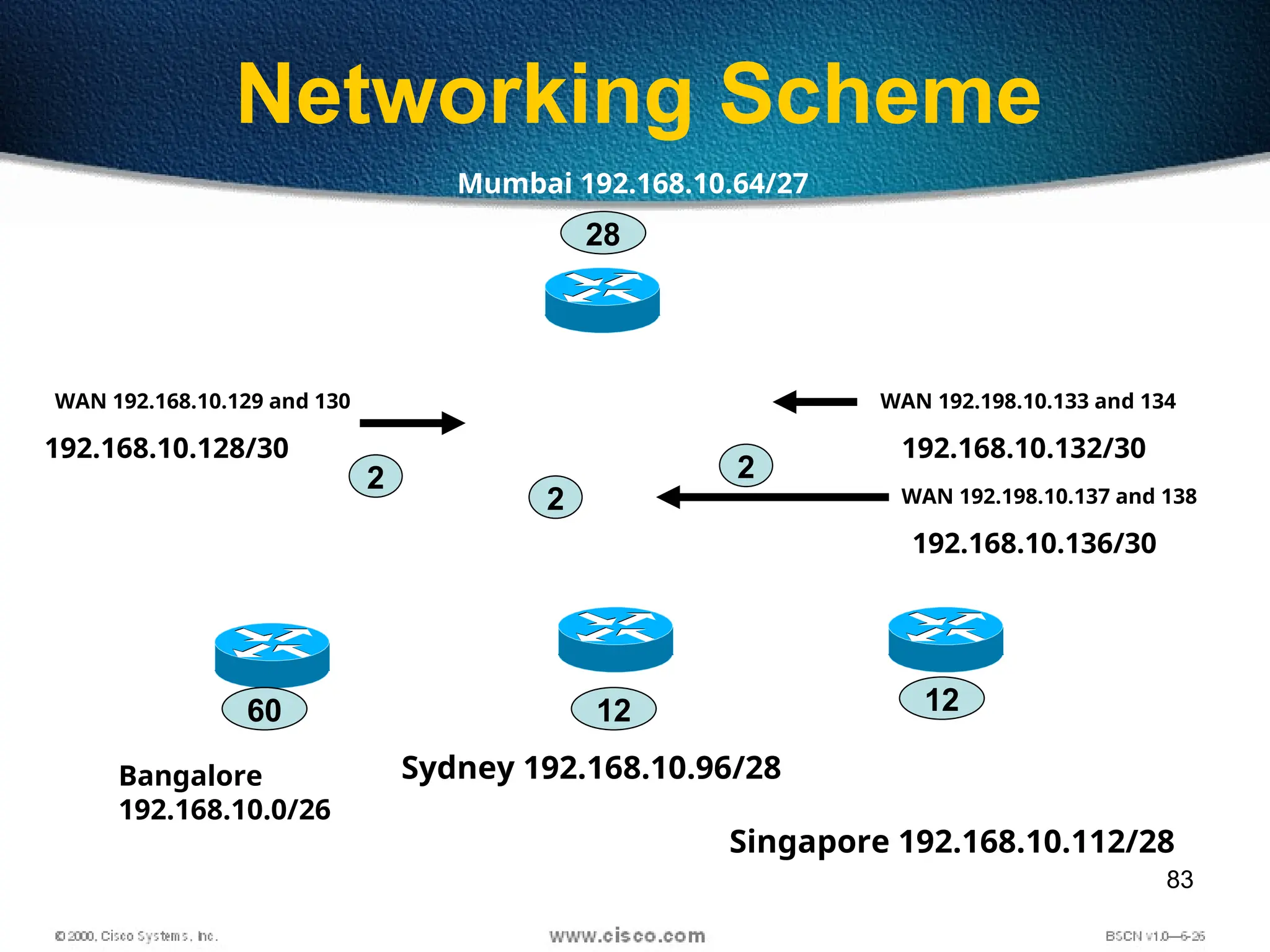
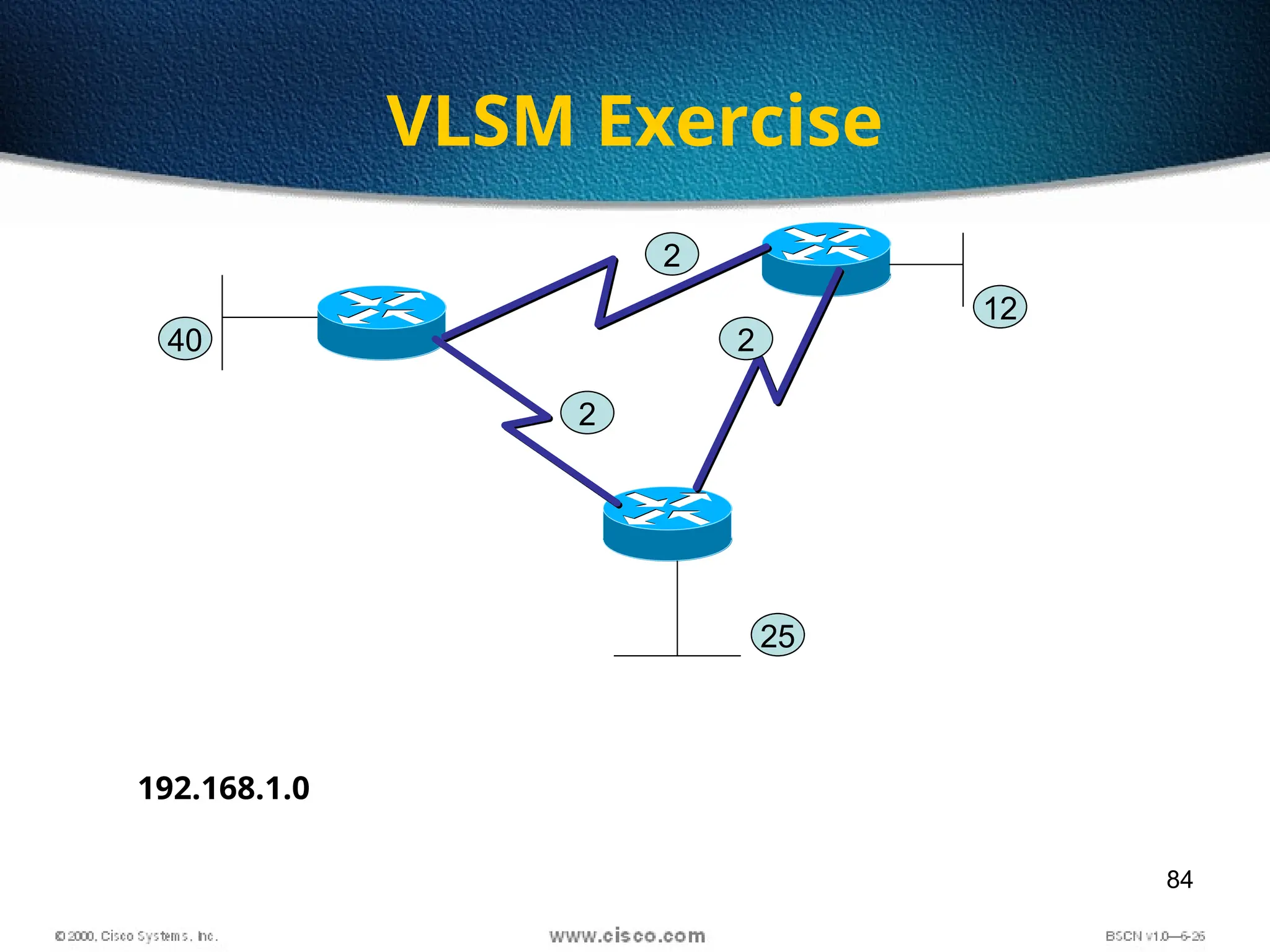
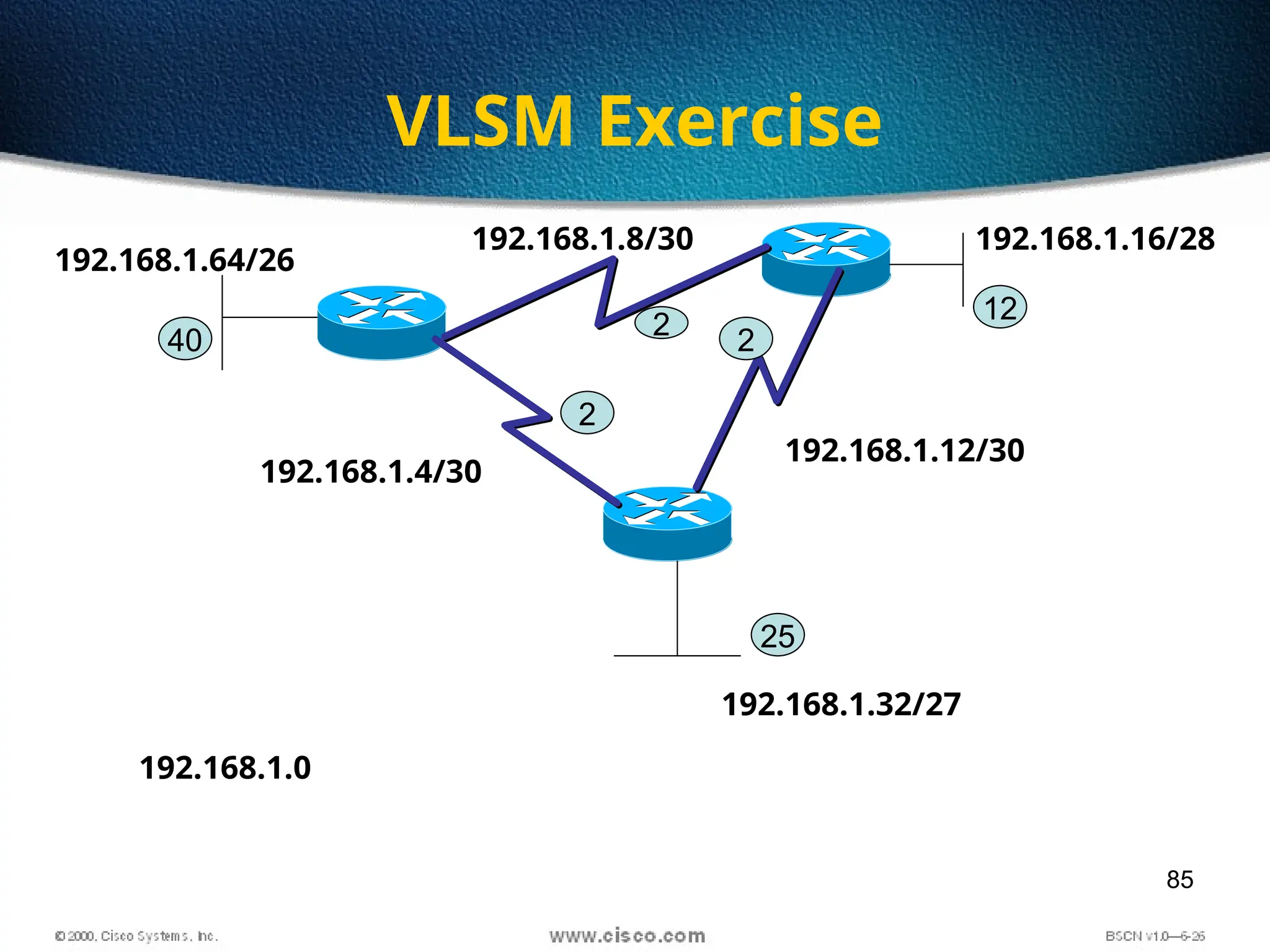
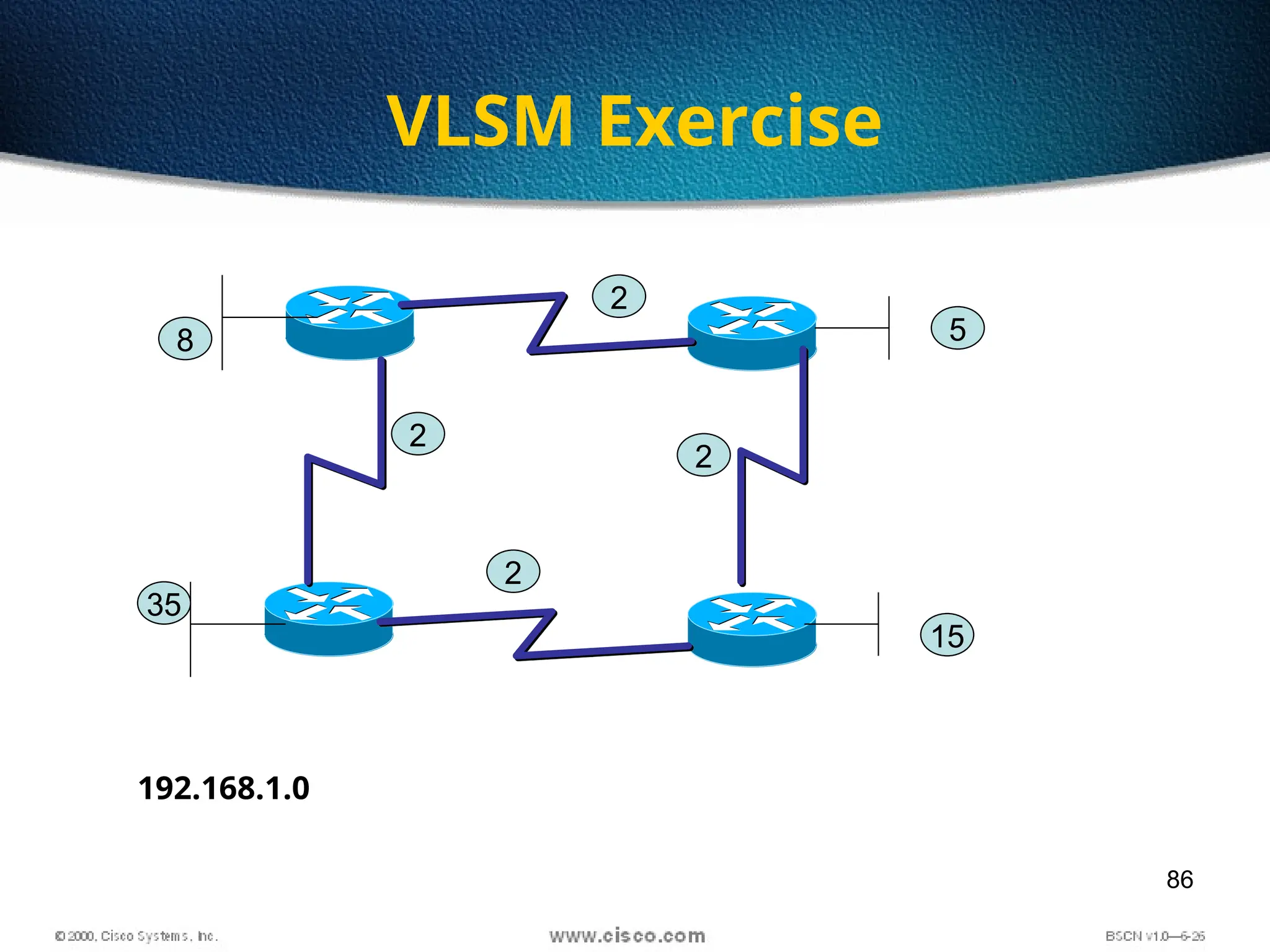
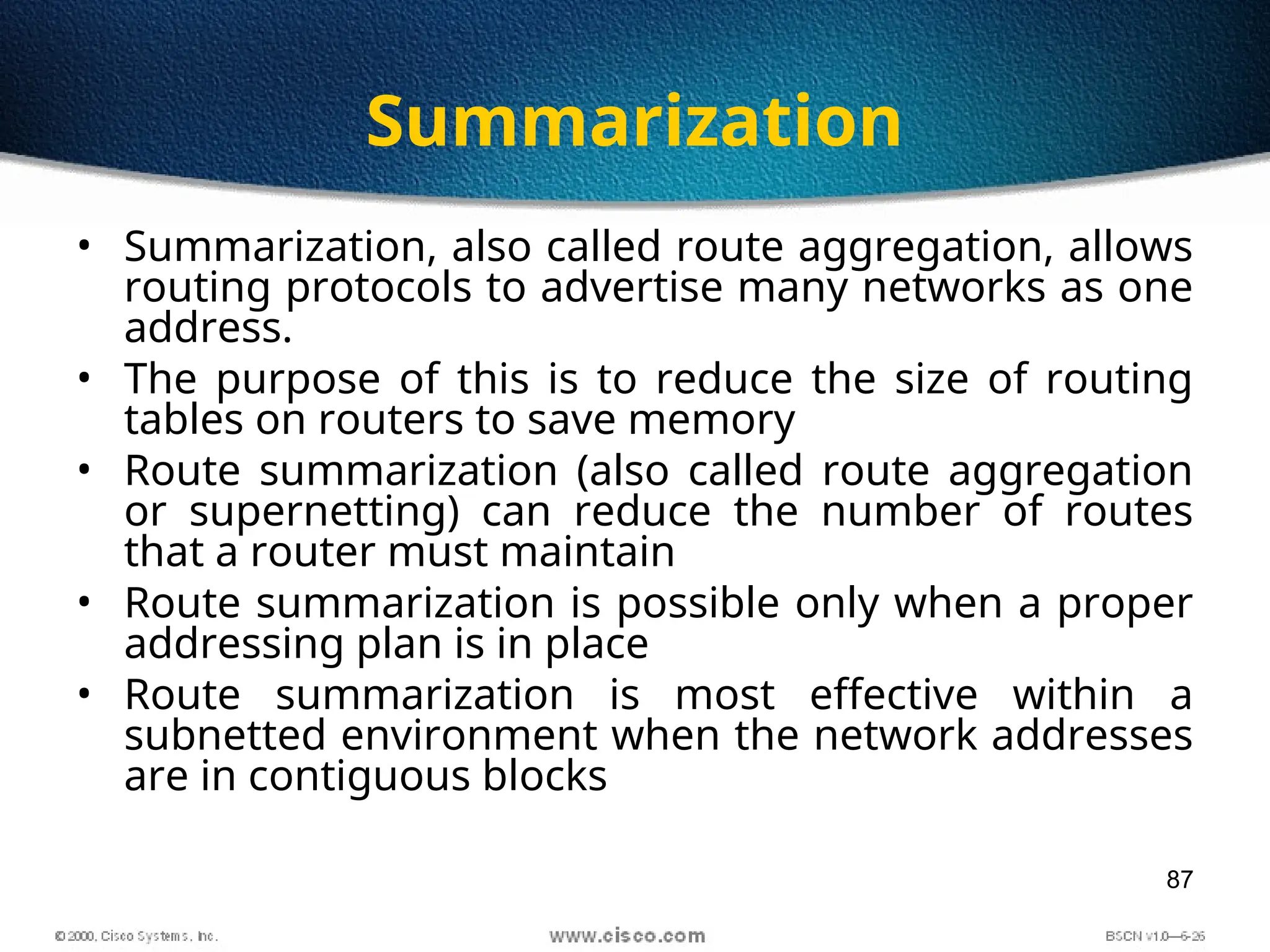
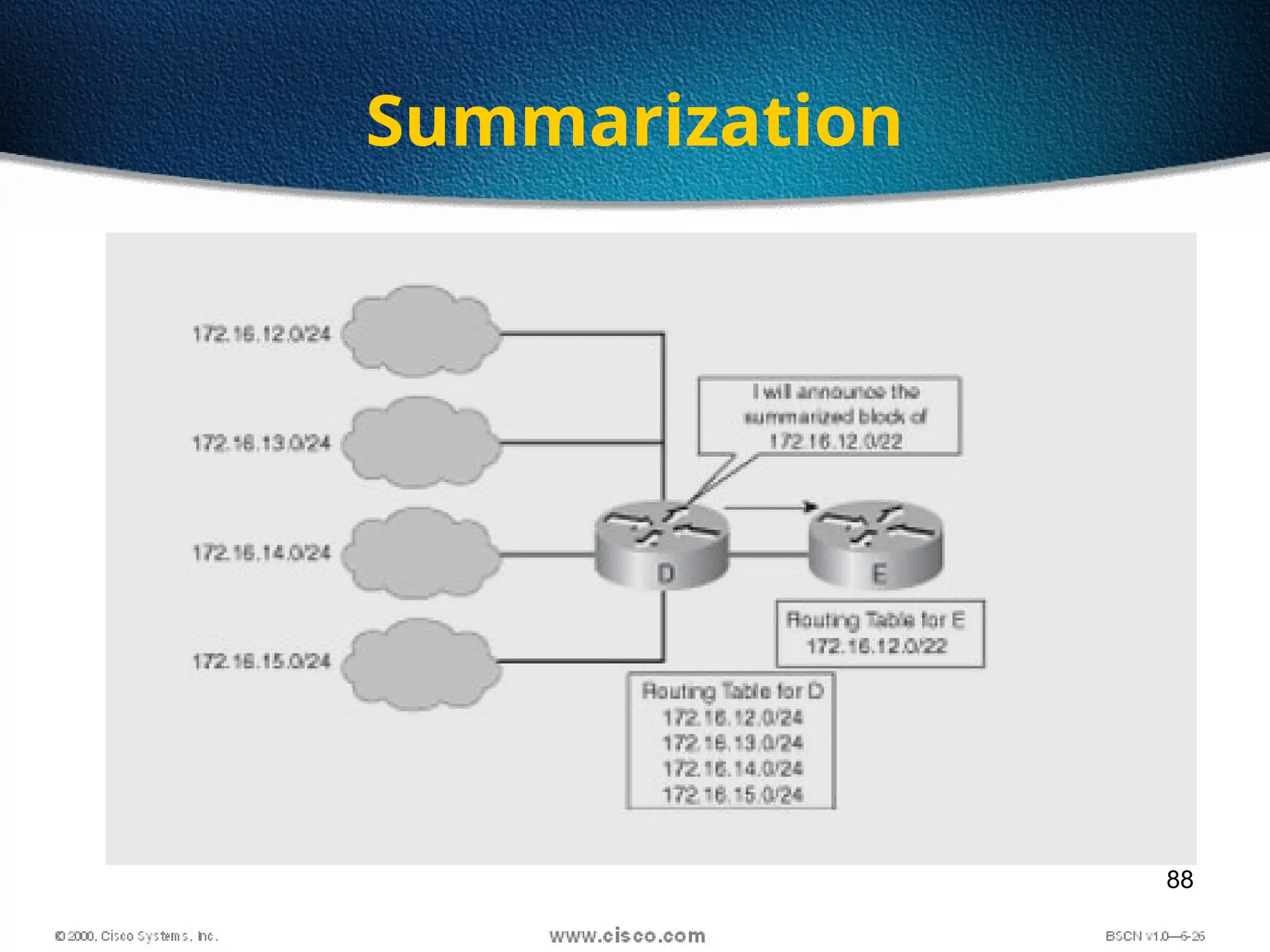
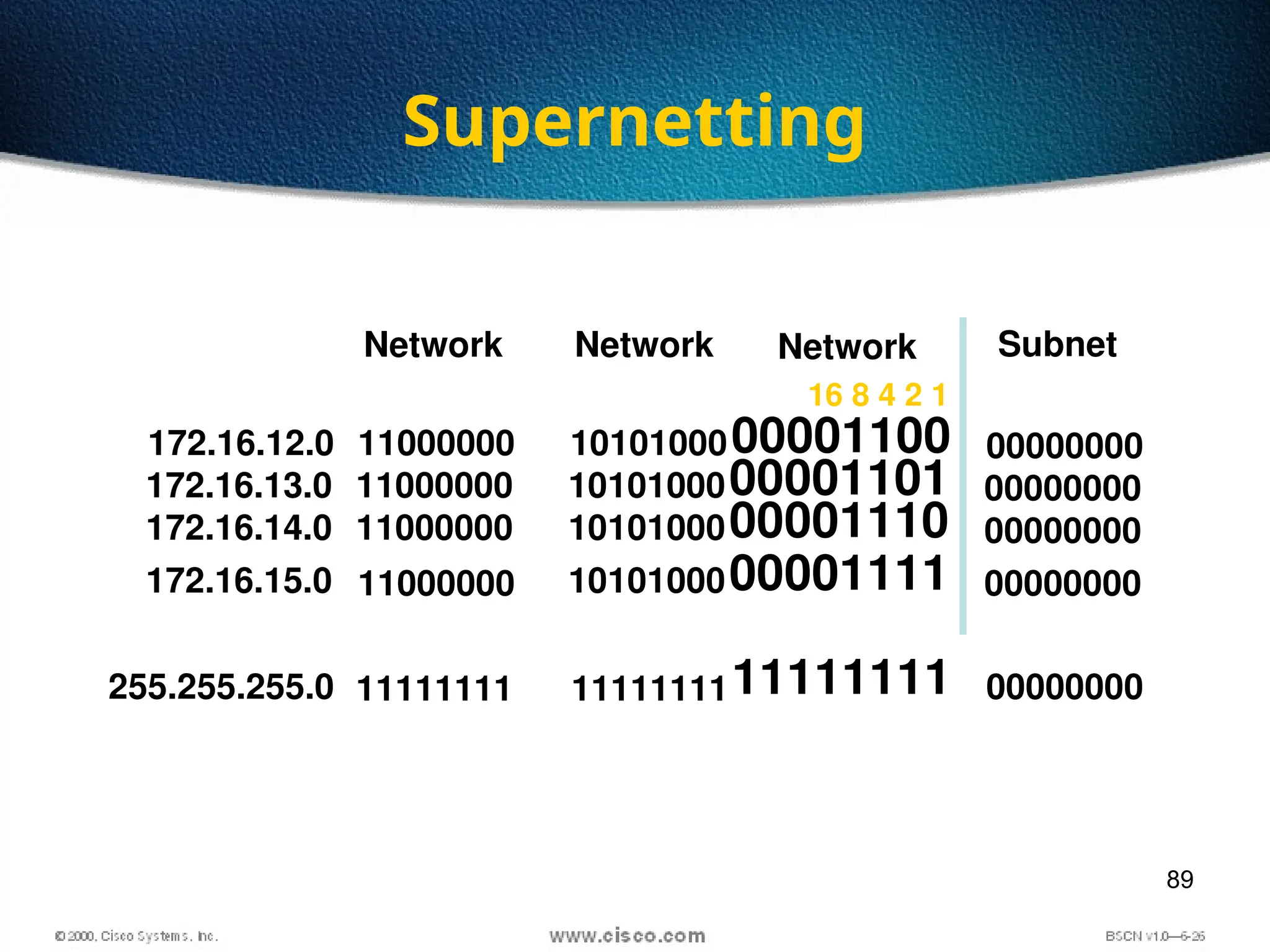
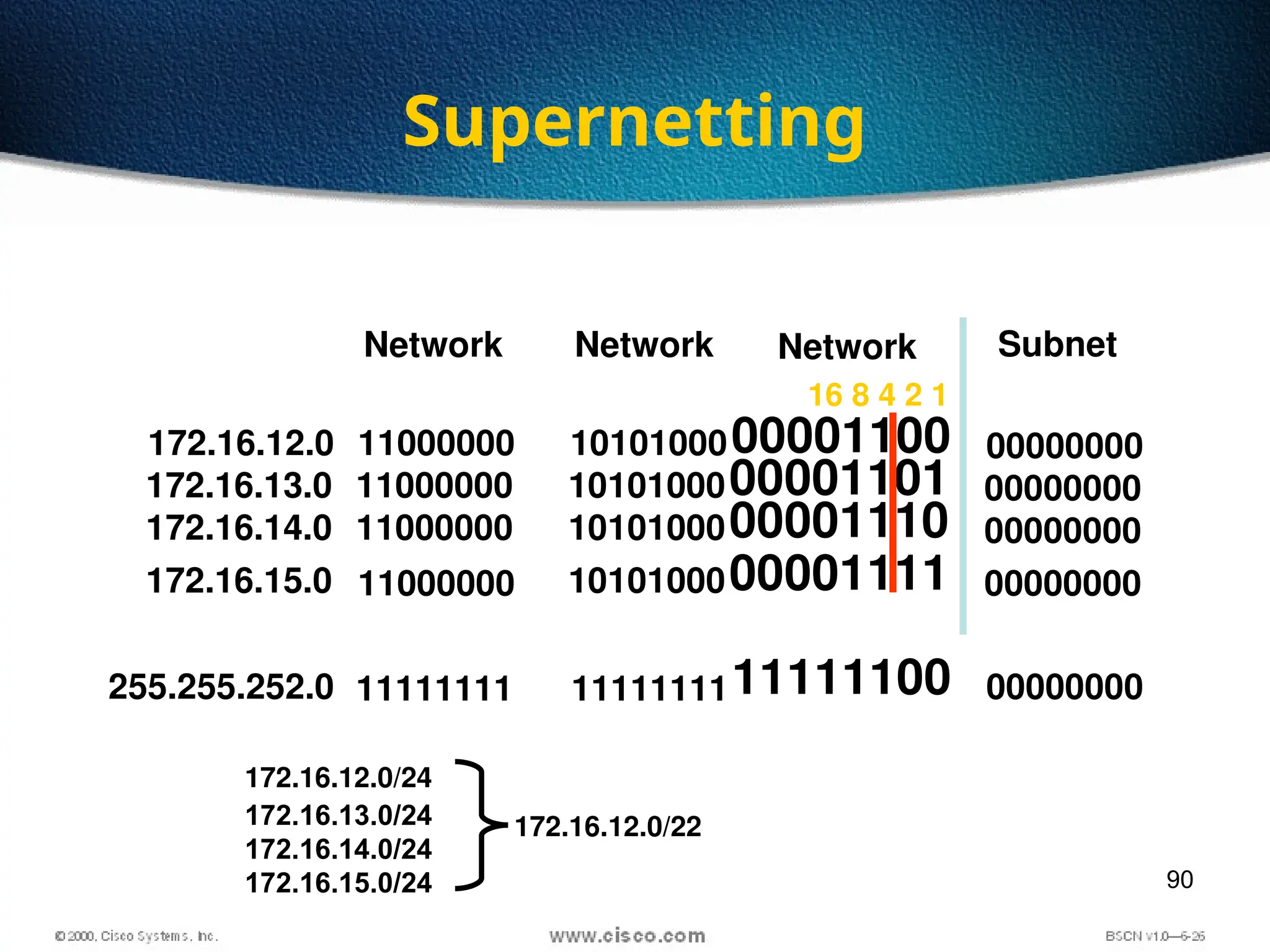
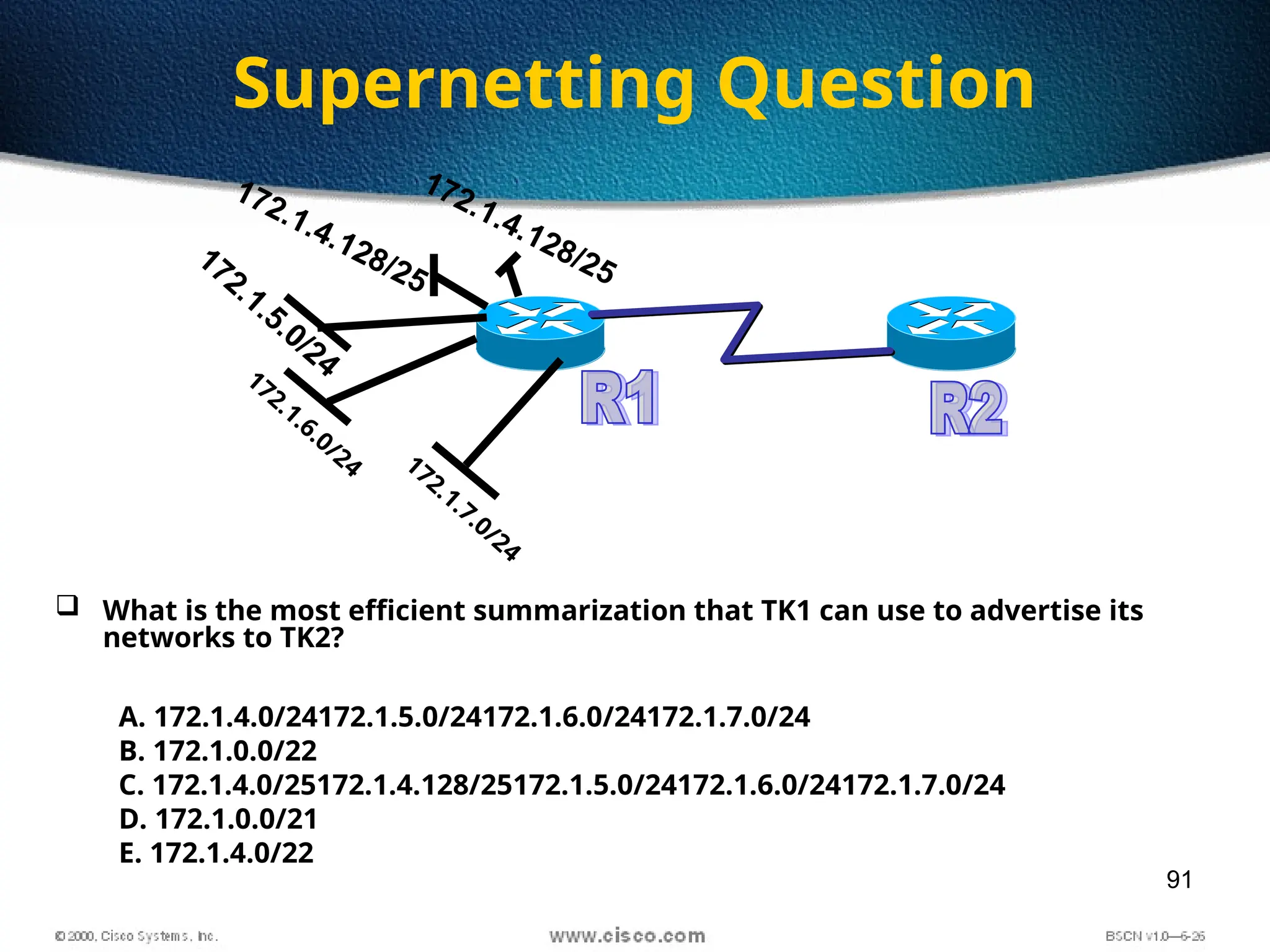
The document discusses the evolution and specifications of Ethernet technology, detailing its origins at Xerox PARC and subsequent development of standards such as IEEE 802.3. It covers various types of cabling, transmission methods (baseband vs broadband), IP addressing classes, and the process of subnetting in networks. Additionally, it includes examples of IP address allocation and subnetting calculations for network management.