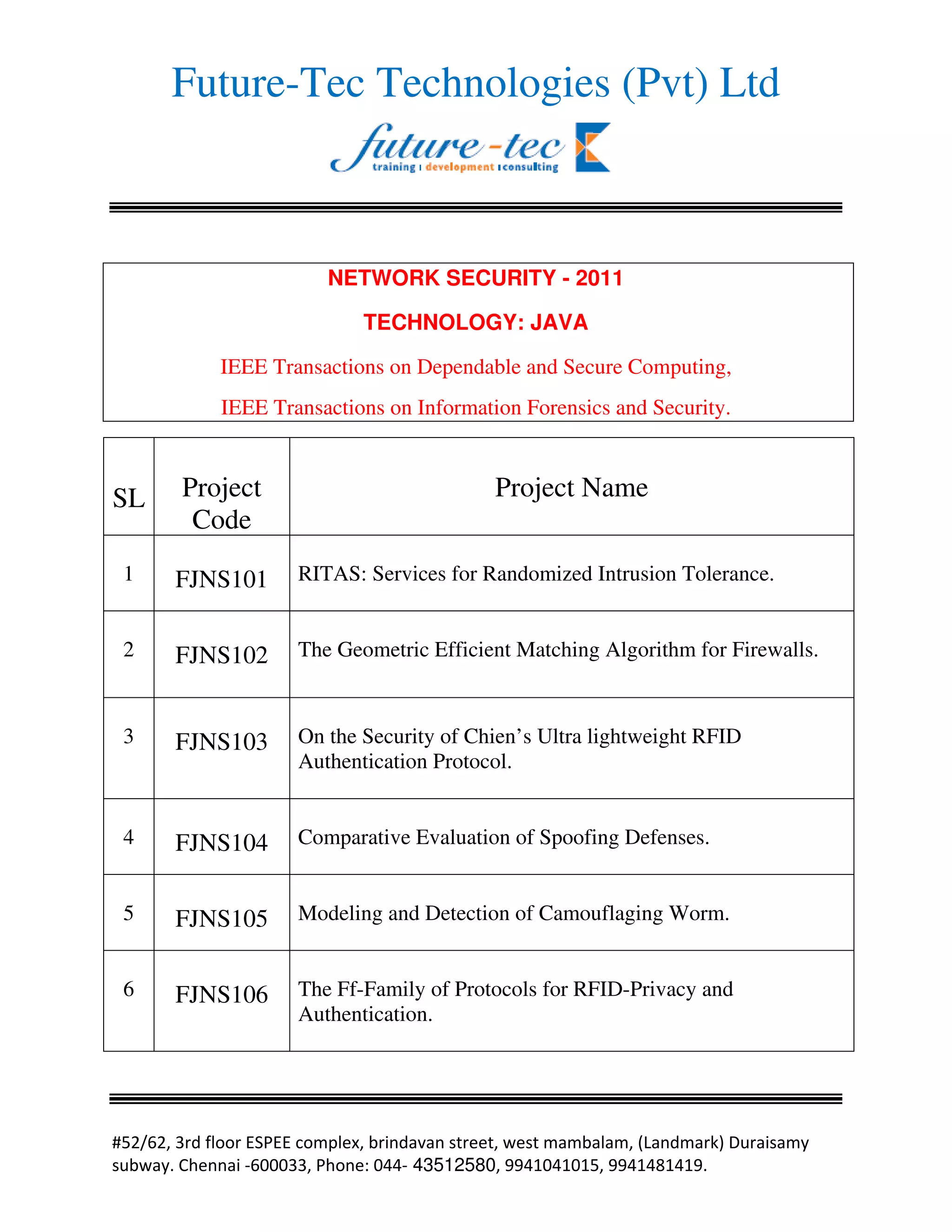
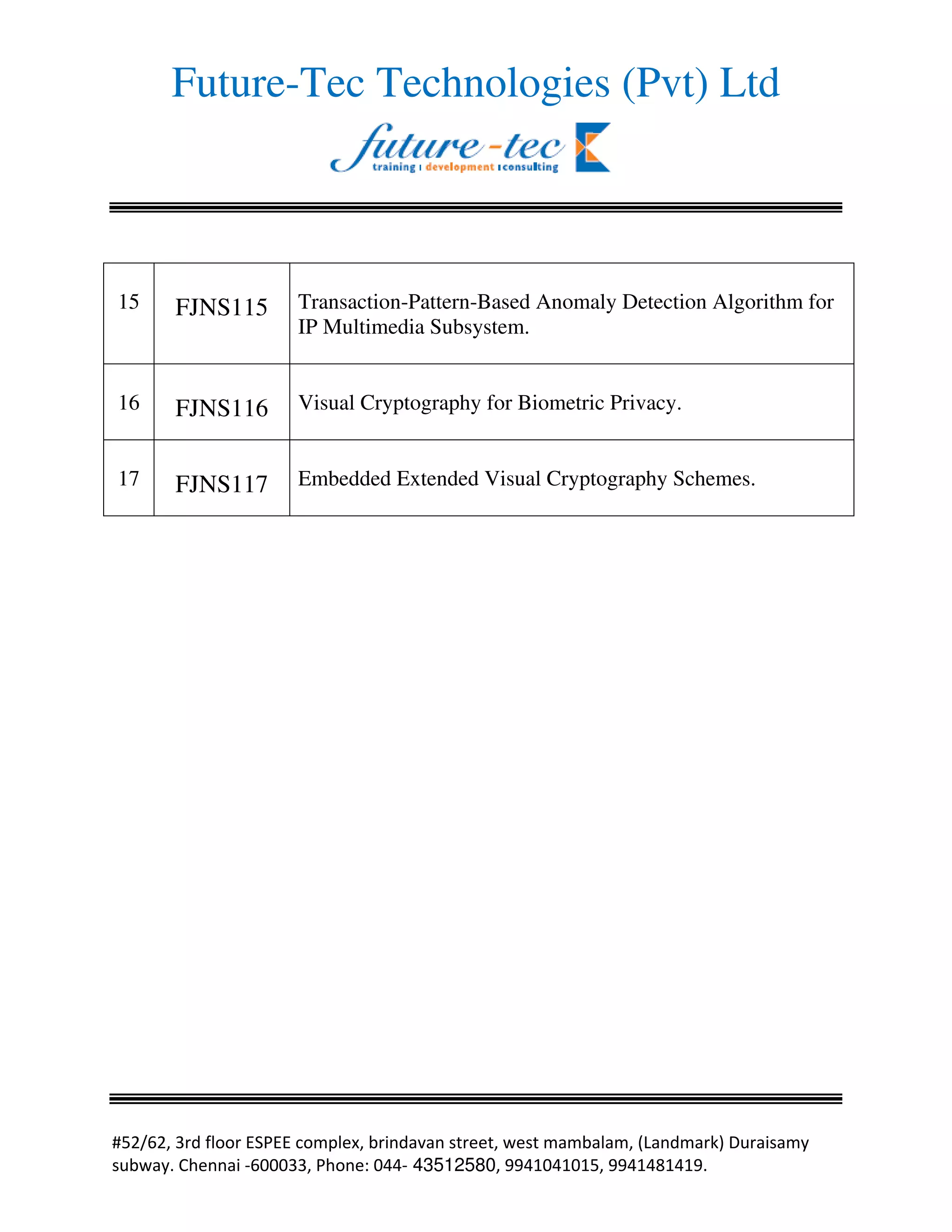
This document lists 17 projects related to network security conducted in 2011 using Java technology. The projects addressed topics such as intrusion tolerance, firewall algorithms, RFID authentication protocols, spoofing defenses, worm detection, sensor network monitoring, and malware analysis. The results of the projects were published in IEEE journals on dependable and secure computing and information forensics and security.