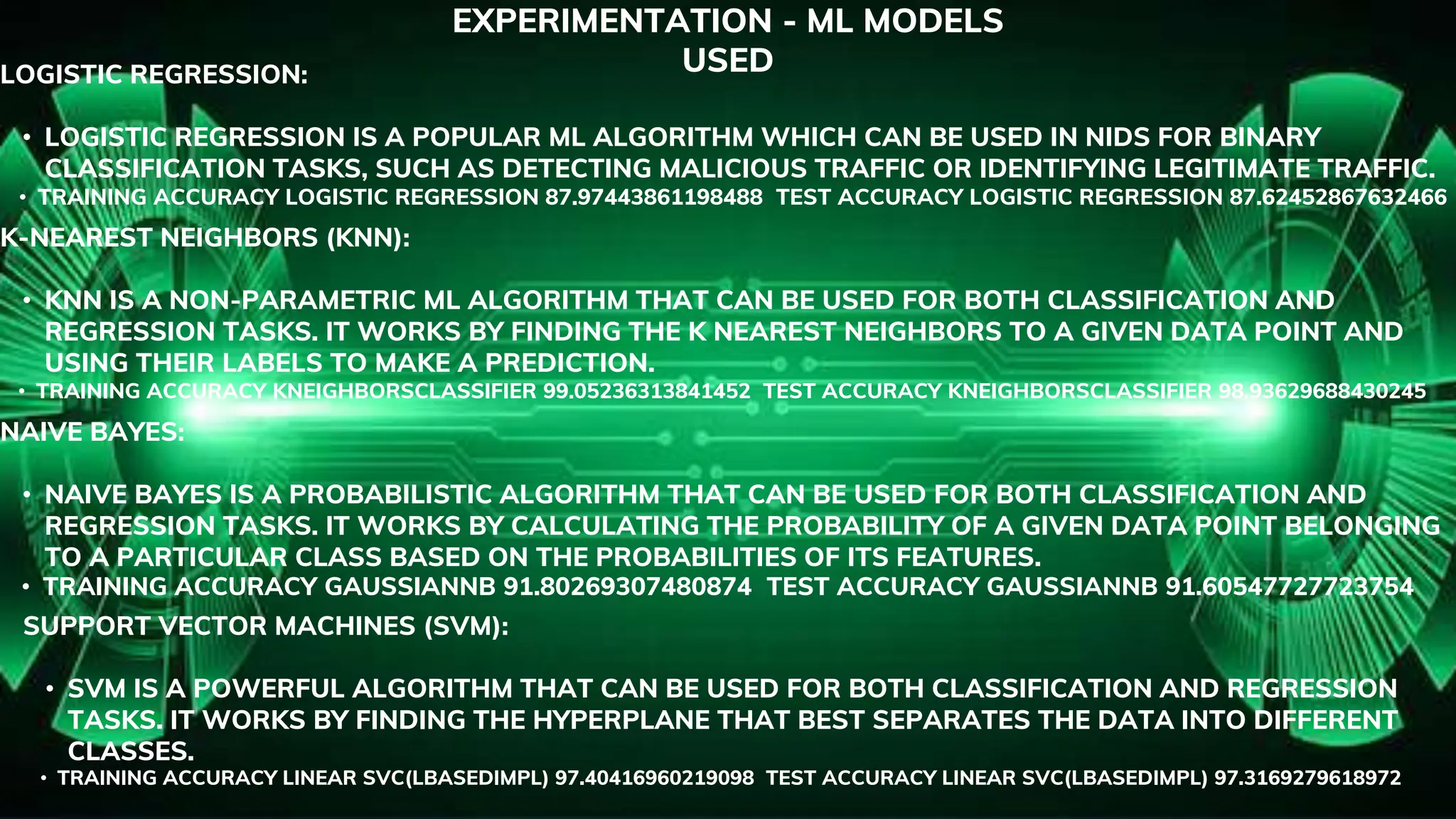
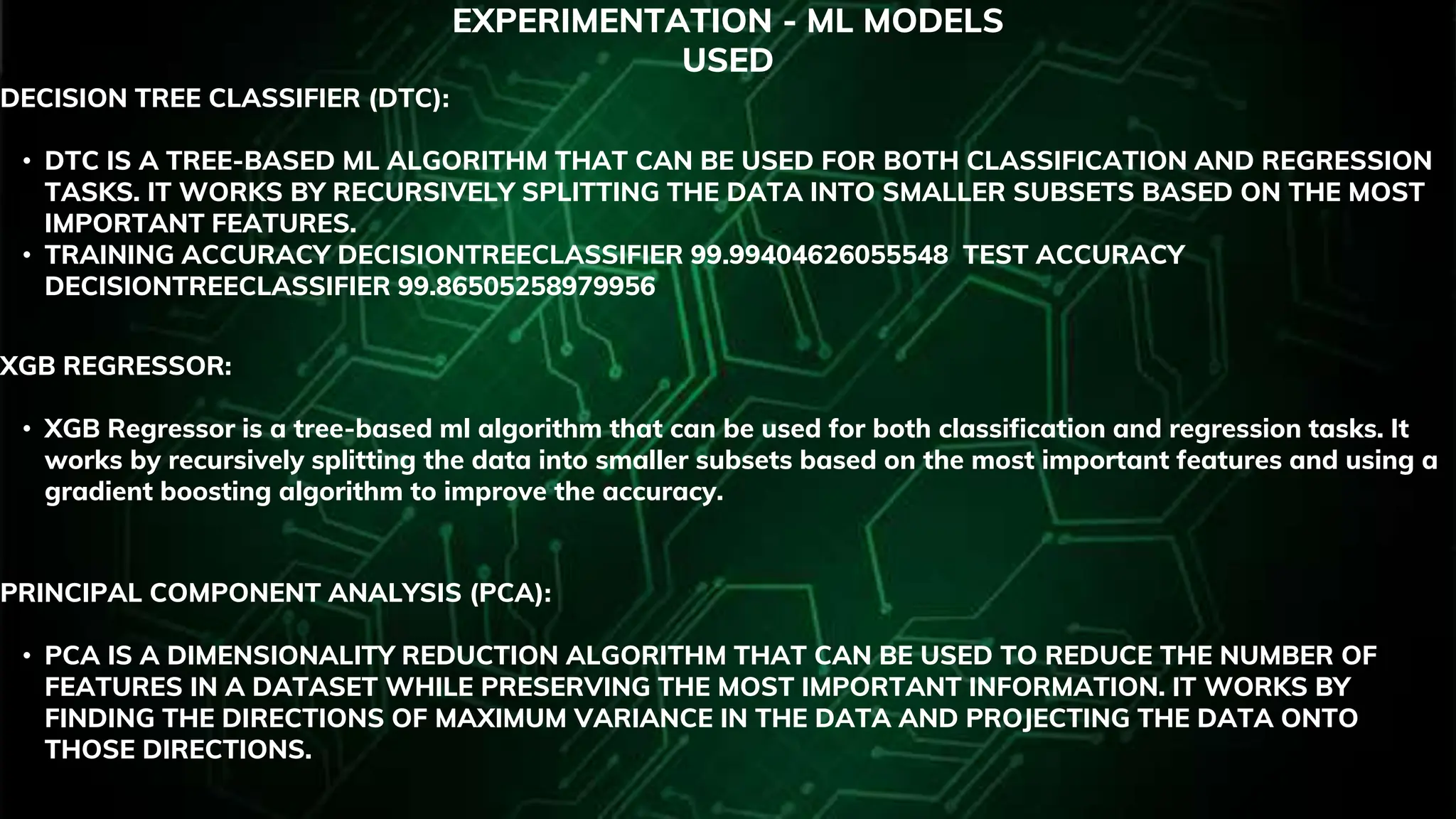
This document discusses the development of a network intrusion detection system (NIDS) utilizing machine learning and deep learning to enhance detection capabilities of network traffic for suspicious activities. It explores various machine learning models, such as logistic regression and decision trees, as well as deep learning approaches like convolutional and recurrent neural networks, highlighting their accuracies and effectiveness in intrusion detection. The project aims to advance NIDS integration into a comprehensive website security platform with features like DDoS mitigation and a web application firewall.