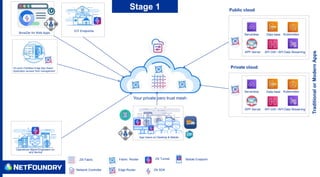
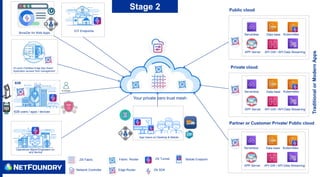
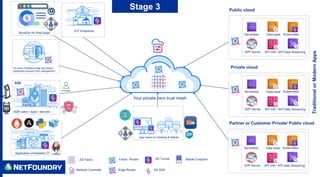
The document outlines a zero trust adoption journey for organizations, focusing on secure access to applications and data in both public and private cloud environments. It emphasizes the implementation of zero trust networks with features like micro-segmentation, mutual TLS, and end-to-end encryption to enhance security against cyber threats. The stages of adoption include securing internal applications, enabling secure B2B communications, and incorporating zero trust application access methods such as SDKs and connectors.