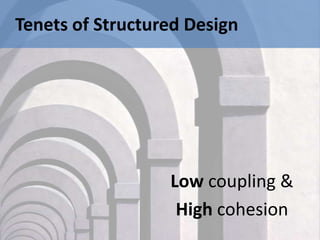
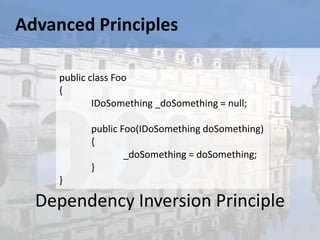
This document summarizes key aspects of .NET architecture for enterprises. It describes the roles and responsibilities of software architects, principles of architecture like separation of concerns and low coupling/high cohesion, and common architectural patterns. It also outlines common layers in applications like the business layer, services layer, data access layer, and presentation layer, describing what they are, responsibilities, and design patterns associated with each layer. The document provides guidance on how to design maintainable and testable systems with a focus on separation of concerns, low coupling between components, and following architectural best practices.