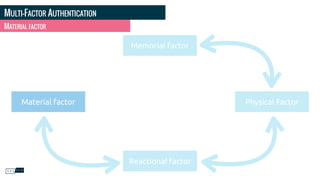
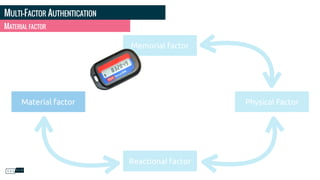
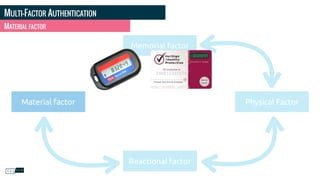
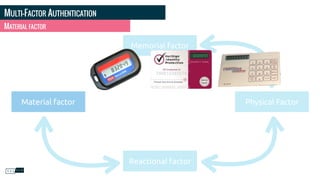
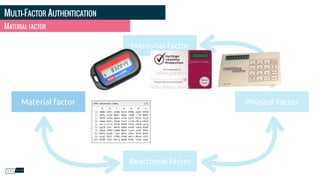
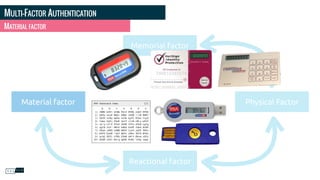
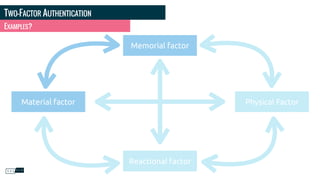
Philippe Gamache discusses the importance of multi-factor authentication and the differences between authentication and authorization in his presentation. He highlights common problems with password security and presents various solutions for strong authentication that cater to different budgets. The presentation emphasizes the necessity of using multiple pieces of evidence to verify user identity to enhance security against threats such as phishing and data theft.












![THE SOLUTIONS
SIGN THE FORM
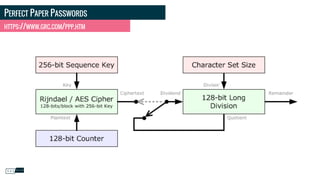
<?php
$code = hash_hmac(
'sha256',
json_encode([
$verifierNonce,
$userID,
$expiration->format('Y-m-dTH:i:s')
]),
$tokenSigningKey
]);](https://image.slidesharecdn.com/multi-factorauthetification2017-en-171023201554/85/Multi-Factor-Authetification-ZendCon-2017-14-320.jpg)









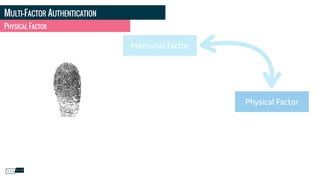
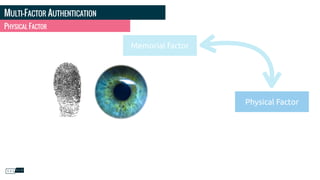
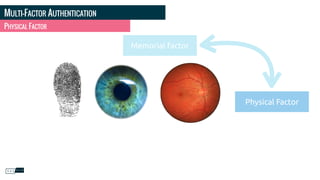

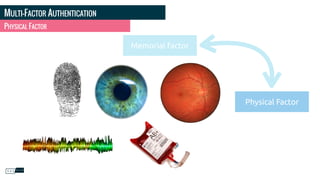
















![PHOTO CREDITS
• Page 3 to 5: By Simeon87 (Own work) [CC BY-SA 3.0 (http://
creativecommons.org/licenses/by-sa/3.0)], via Wikimedia Commons
• Page 11: http://failblog.cheezburger.com/](https://image.slidesharecdn.com/multi-factorauthetification2017-en-171023201554/85/Multi-Factor-Authetification-ZendCon-2017-65-320.jpg)