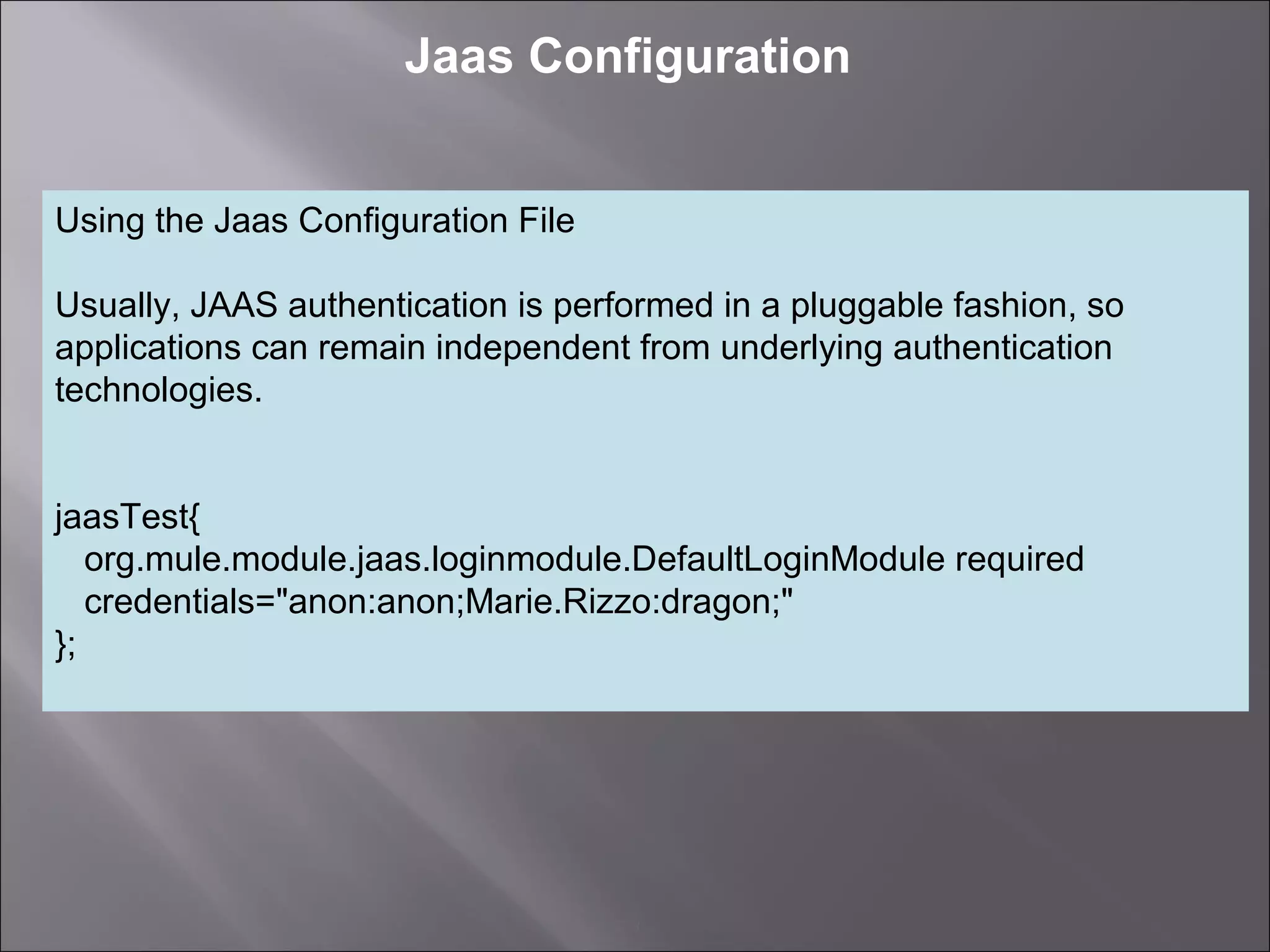
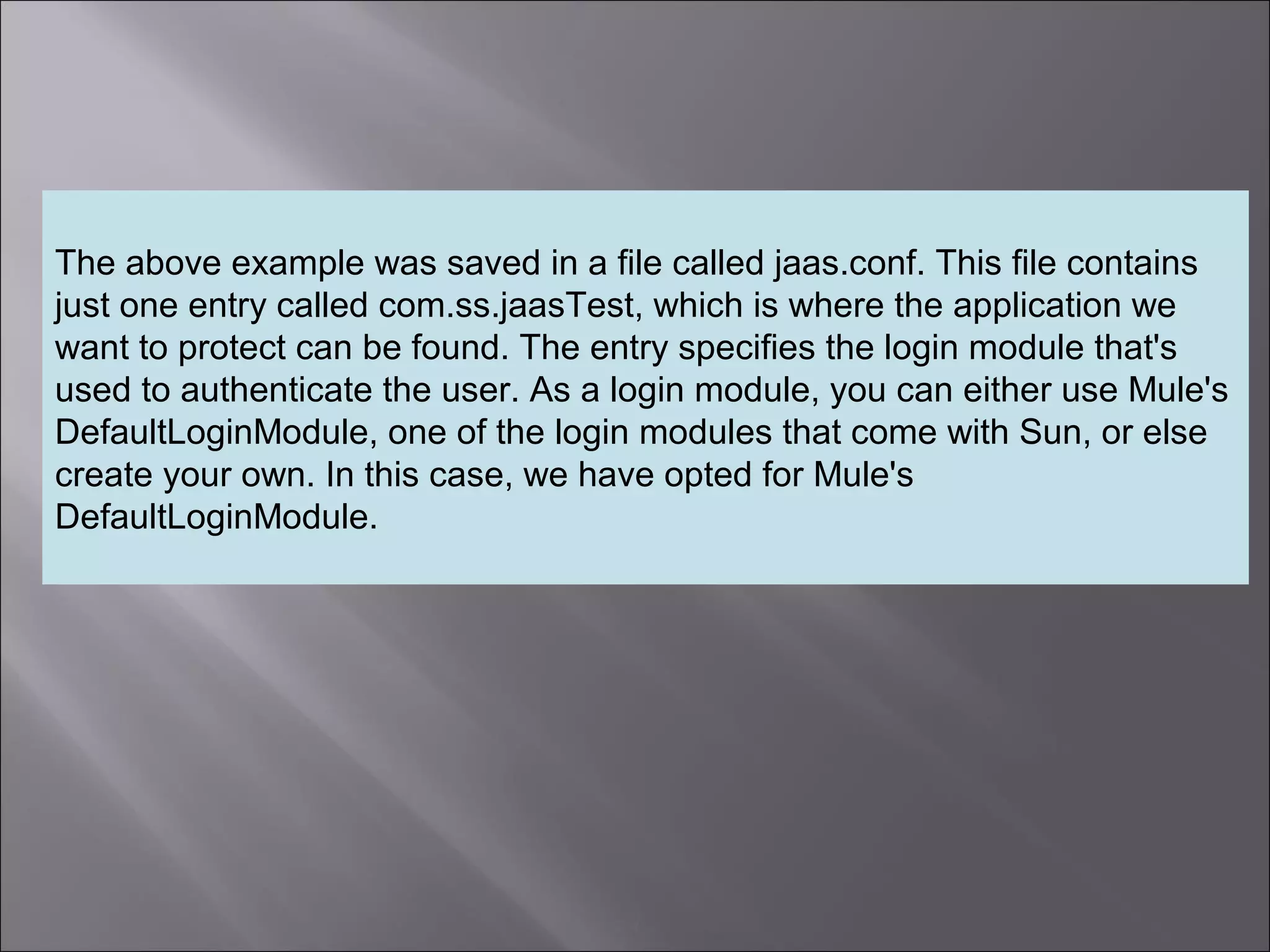
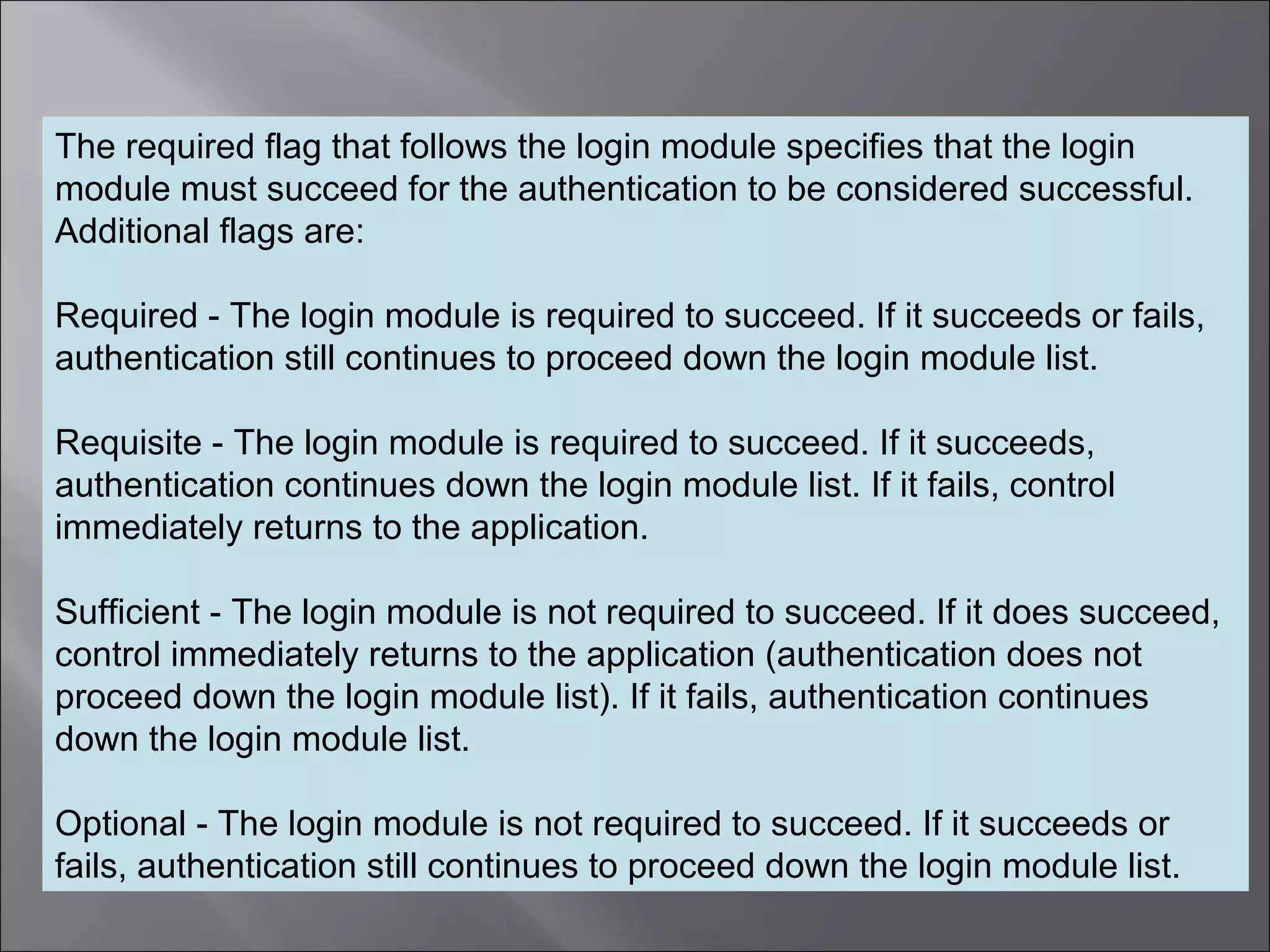
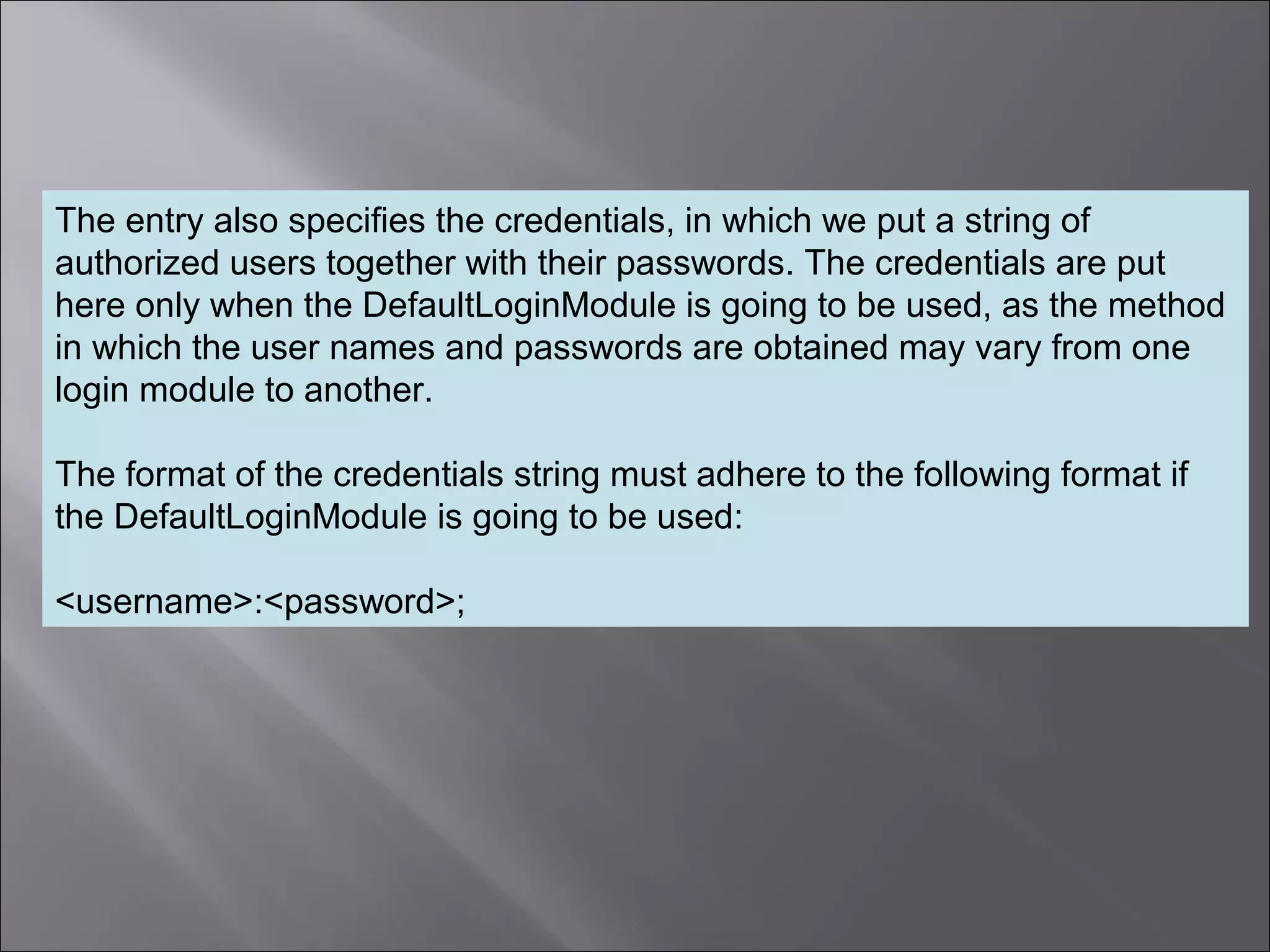
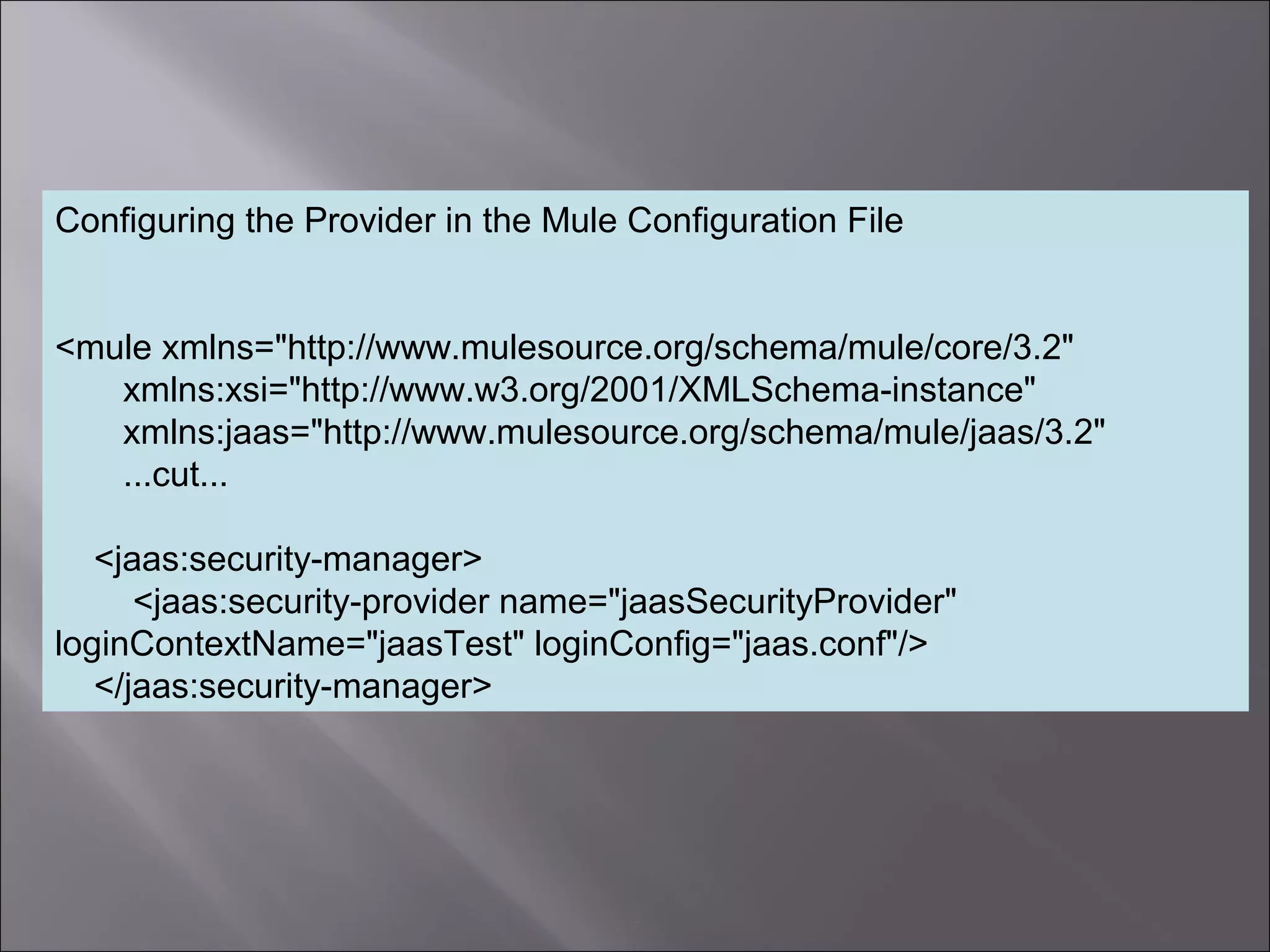
The document discusses how to configure the JaasSimpleAuthenticationProvider security provider in Mule to use the Jaas Authentication Service. It describes two configuration methods - passing a Jaas configuration file that defines login modules and credentials, or configuring attributes directly on the provider. The Jaas configuration file example shows a file defining a login module, required flag, and authorized users mapped to passwords.