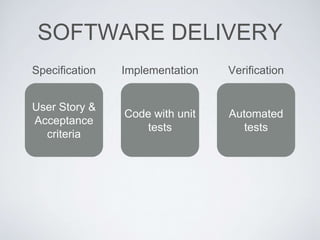
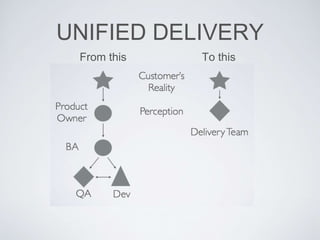
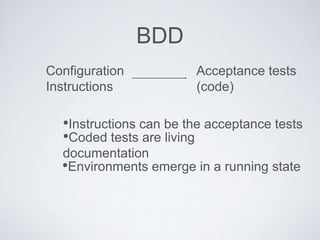
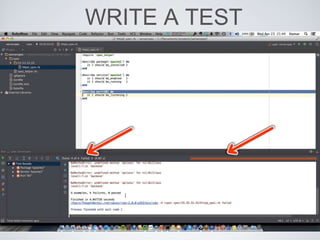
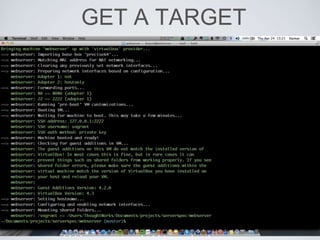
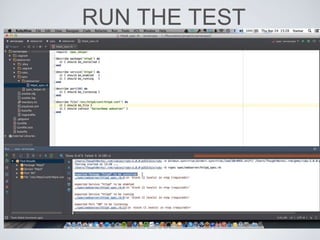
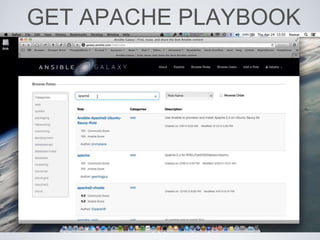
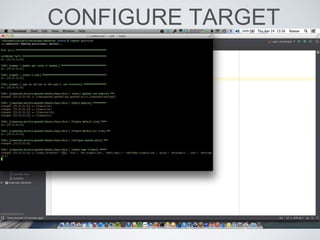
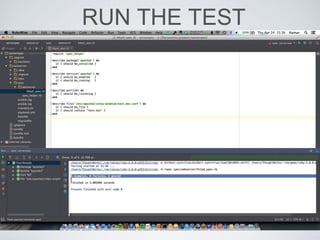
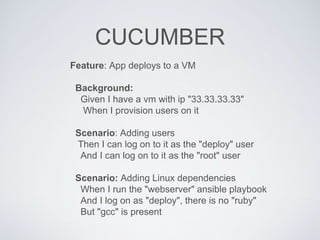
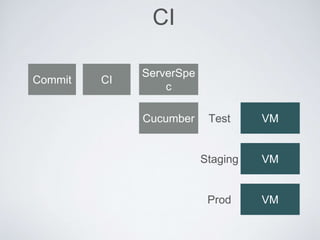
The document discusses best practices for using Ansible in infrastructure development, emphasizing the importance of treating Ansible scripts with the same rigor as application code, including automated testing and version control. It details the necessity of automation to ensure scalability and consistent environments while promoting collaboration between developers and sysadmins. Key practices include employing Test-Driven Development (TDD), using Serverspec for testing, and integrating continuous integration (CI) methodologies into the deployment process.