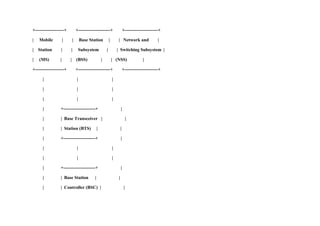
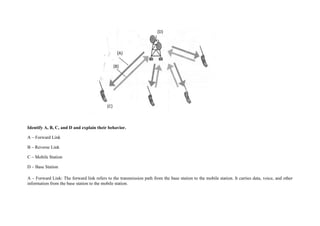
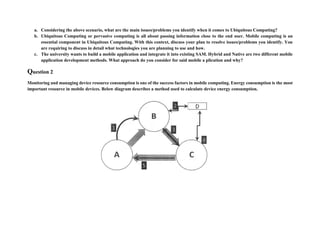
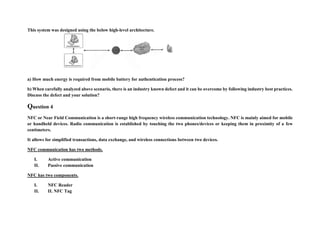
Mobile security is important due to widespread mobile device use. Mobile devices face threats like malware, phishing attacks, and device theft. A comprehensive mobile security strategy includes mobile device management, secure app distribution, encryption, authentication, and user education. Successful attacks can result in data loss, resource misuse, reputation damage, and identity theft. Implementing security best practices can help mitigate these risks.