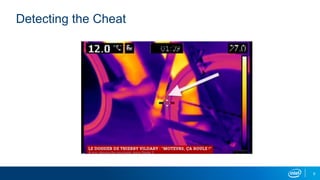
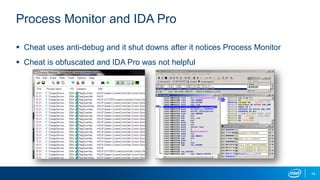
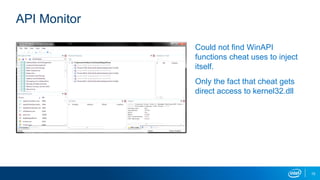
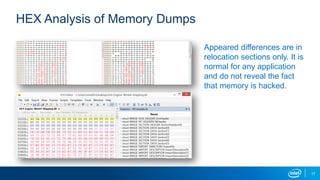
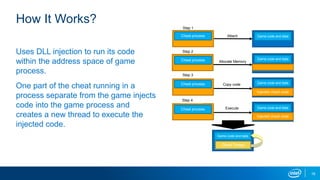
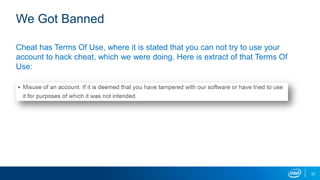
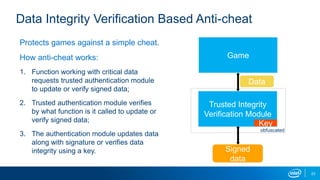
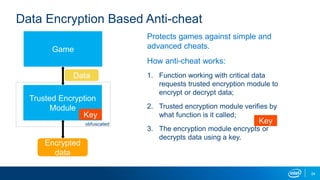
The document explores the motivations behind cheating in online games and its consequences on player experience and game integrity. It discusses various techniques used by cheaters, as well as approaches to anti-cheat systems including server-side and local solutions. Additionally, it highlights the pros and cons of different anti-cheat methods and emphasizes the importance of user privacy.