The August 2024 Patch Tuesday webinar, hosted by Chris Goettl and Todd Schell, covers significant security updates including critical vulnerabilities for Microsoft’s OS and Office products, as well as updates for Adobe Acrobat and Google Chrome. Notable issues include several exploited CVEs requiring urgent attention, with a focus on various Windows-related vulnerabilities impacting privilege escalation and remote code execution. The session also highlights lifecycle awareness for Windows 10 and 11, along with known issues associated with recent updates.















![Copyright © 2024 Ivanti. All rights reserved. 21
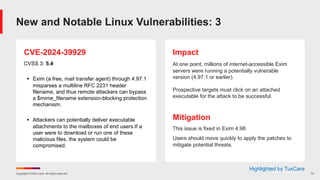
August Known Issues for Windows 11
§ KB 5041592 – Windows 11 version 21H2, all editions
§ [Prof_Pic] After installing this update, you might be unable to change your user account
profile picture. When attempting to change a profile picture by selecting the button Start>
Settings> Accounts > Your info, and then selecting Choose a file, you might receive an error
message with error code 0x80070520. Workaround: Microsoft is working on a resolution
§ KB 5041571 – Windows 11 version 24H2, all editions
§ [Roblox] We’re aware of an issue where players on Arm devices are unable to download
and play Roblox via the Microsoft Store on Windows.
§ Workaround: Download Roblox directly from vendor.](https://image.slidesharecdn.com/aug2024patchtuesday-240814202007-8a12f143/85/August-Patch-Tuesday-21-320.jpg)

![Copyright © 2024 Ivanti. All rights reserved. 23
August Known Issues for Windows 10
§ KB 5041773 – Windows 10 version 1607, all editions; Windows Server 2016, all editions
§ [Remote Desktop] After installing the Windows update released on or after July 9, 2024,
Windows Servers might affect Remote Desktop Connectivity across an organization. This
issue might occur if legacy protocol (Remote Procedure Call over HTTP) is used in Remote
Desktop Gateway. Resulting from this, remote desktop connections might be interrupted.
§ Workaround: See KB for multiple options. Microsoft is working on a resolution.
§ KB 5041578 – Win 10 Enterprise LTSC 2019, Win 10 IoT Enterprise LTSC 2019, Windows 10
IoT Core 2019 LTSC, Windows Server 2019
§ [Remote Desktop]
§ KB 5041580 – Windows 10 Enterprise LTSC 2021, Windows 10 IoT Enterprise LTSC 2021,
Windows 10, version 22H2, all editions
§ [Prof_Pic]
§ KB 5041160 – Windows Server 2022
§ [Prof_Pic]
§ [Remote Desktop]](https://image.slidesharecdn.com/aug2024patchtuesday-240814202007-8a12f143/85/August-Patch-Tuesday-23-320.jpg)