The February 2025 Patch Tuesday webinar covered important updates from Adobe, Microsoft, and Google, focusing on newly addressed vulnerabilities and security recommendations. Key updates include critical patches for Adobe applications and Microsoft’s release addressing 56 new CVEs, including several zero-day exploits. The session also discussed ongoing issues with older Exchange servers and the necessity to update to supported versions to maintain security.


















![Copyright © 2025 Ivanti. All rights reserved. 24
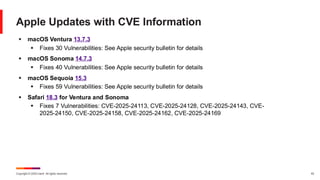
February Known Issues for Windows 11
▪ KB 5051989 – Windows 11 Enterprise and Education version 22H2, Windows 11 version 23H2,
all editions
▪ [OpenSSH] Following the installation of the October 2024 security update, some customers
report that the OpenSSH (Open Secure Shell) service fails to start, preventing SSH
connections.
▪ Workaround: Customers can temporarily resolve the issue by updating permissions (ACLs)
on the affected directories. See KB for details.
▪ [Citrix_SRA] Devices that have certain Citrix components installed might be unable to
complete installation of the January 2025 Windows security update. This has been noted
with the Citrix Session Recording Agent installed.
▪ Workaround: Citrix has provided several workaround options until they resolve the issue
with Microsoft. See KB for details.](https://image.slidesharecdn.com/february2025patchtuesday-250212191510-0ccceeb5/85/February-Patch-Tuesday-24-320.jpg)
![Copyright © 2025 Ivanti. All rights reserved. 25
February Known Issues for Windows 11 (cont)
▪ KB 5051987 – Windows 11 version 24H2, all editions
▪ [Roblox] We’re aware of an issue where players on Arm devices are unable to download
and play Roblox via the Microsoft Store on Windows.
▪ Workaround: Download Roblox directly from vendor.
▪ [OpenSSH]
▪ [Citrix_SRA]](https://image.slidesharecdn.com/february2025patchtuesday-250212191510-0ccceeb5/85/February-Patch-Tuesday-25-320.jpg)

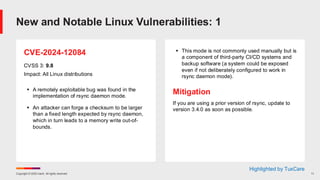
![Copyright © 2025 Ivanti. All rights reserved. 27
February Known Issues for Windows 10
▪ KB 5052000 – Win 10 Ent LTSC 2019, Win 10 IoT Ent LTSC 2019, Windows 10 IoT Core LTSC,
Windows Server 2019
▪ [OpenSSH]
▪ [Citrix_SRA]
▪ KB 5051974 – Windows 10 Enterprise LTSC 2021, Windows 10 IoT Enterprise LTSC 2021,
Windows 10, version 22H2, all editions
▪ [OpenSSH]
▪ [Citrix_SRA]
▪ [Broker] The Windows Event Viewer might display an error related to SgrmBroker.exe, on
devices that have installed Windows updates released January 14, 2025 or later. This error
can be found under Windows Logs > System as Event 7023, with text similar to ‘The
System Guard Runtime Monitor Broker service terminated with the following error:
%%3489660935’.
▪ Workaround: This is an error due to a Windows Defender service being disabled. Ignore it
and it will be corrected in a future release. See KB for more details.](https://image.slidesharecdn.com/february2025patchtuesday-250212191510-0ccceeb5/85/February-Patch-Tuesday-27-320.jpg)
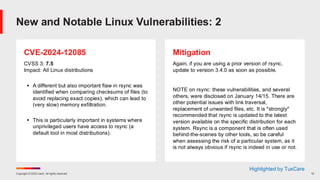
![Copyright © 2025 Ivanti. All rights reserved. 28
February Known Issues for Windows 10 (cont)
▪ KB 5051979 – Windows Server 2022
▪ [OpenSSH]
▪ [Citrix_SRA]
▪ [Broker]
▪ KB 5051980 – Windows Server, version 23H2
▪ [OpenSSH]](https://image.slidesharecdn.com/february2025patchtuesday-250212191510-0ccceeb5/85/February-Patch-Tuesday-28-320.jpg)