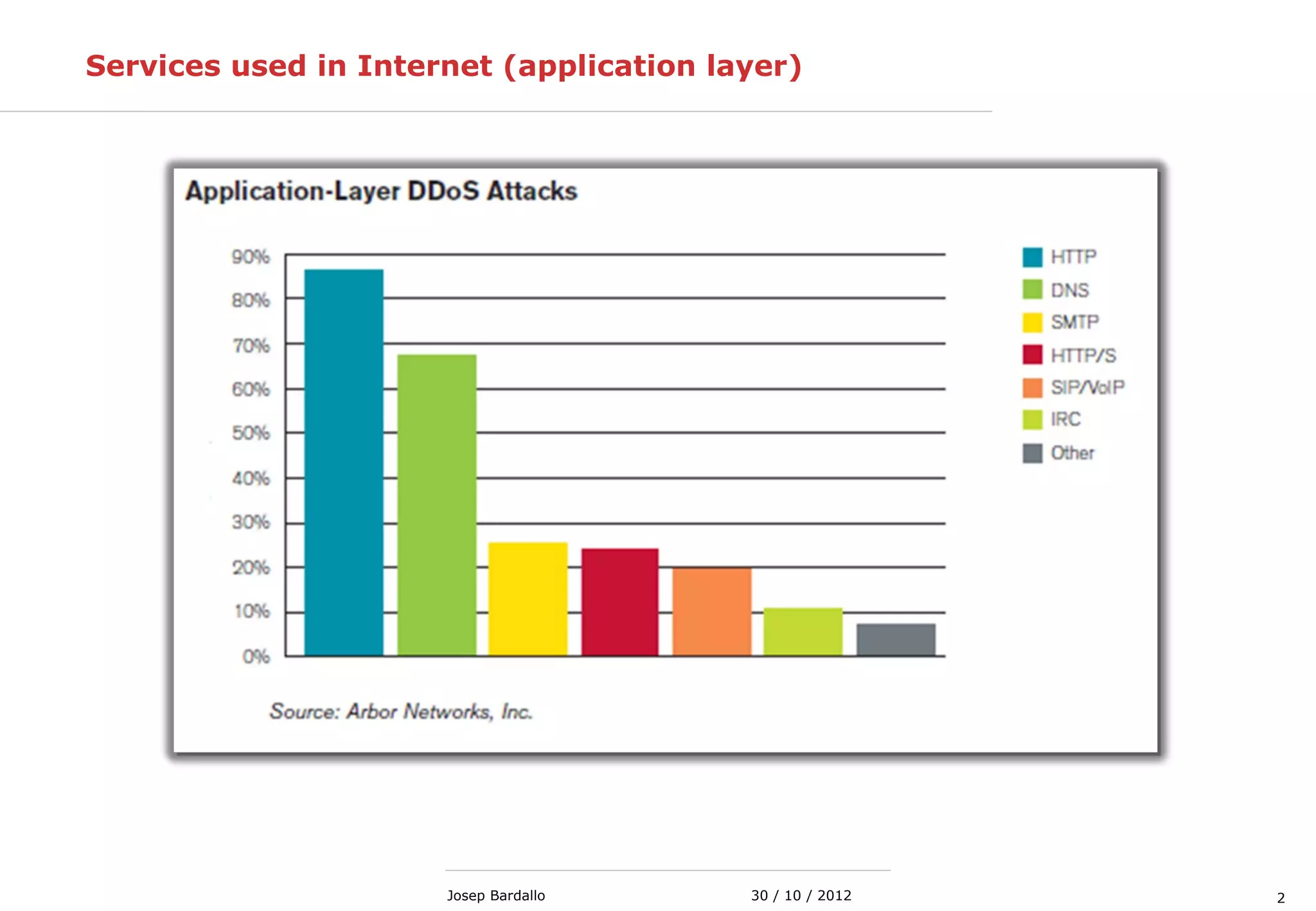
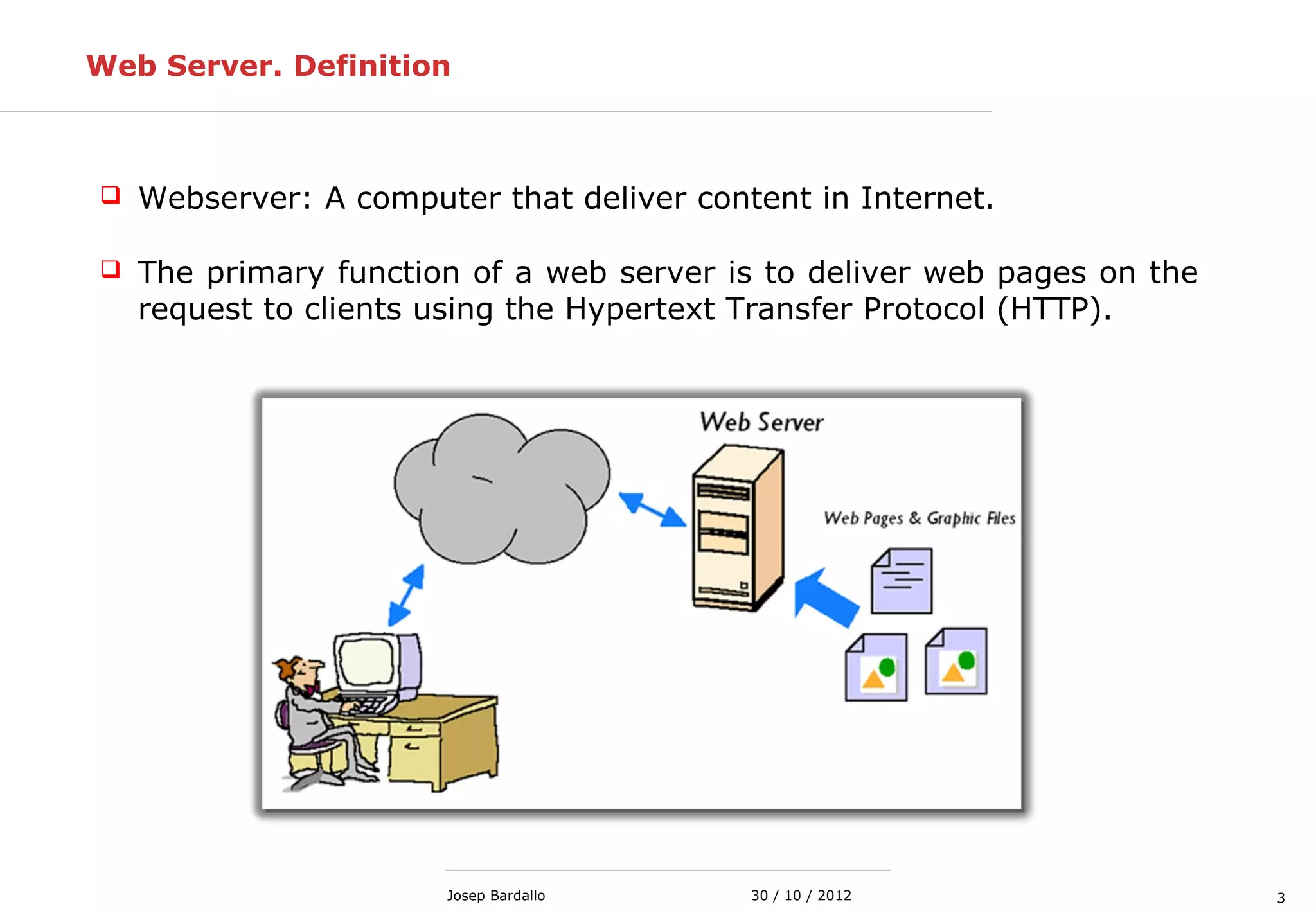
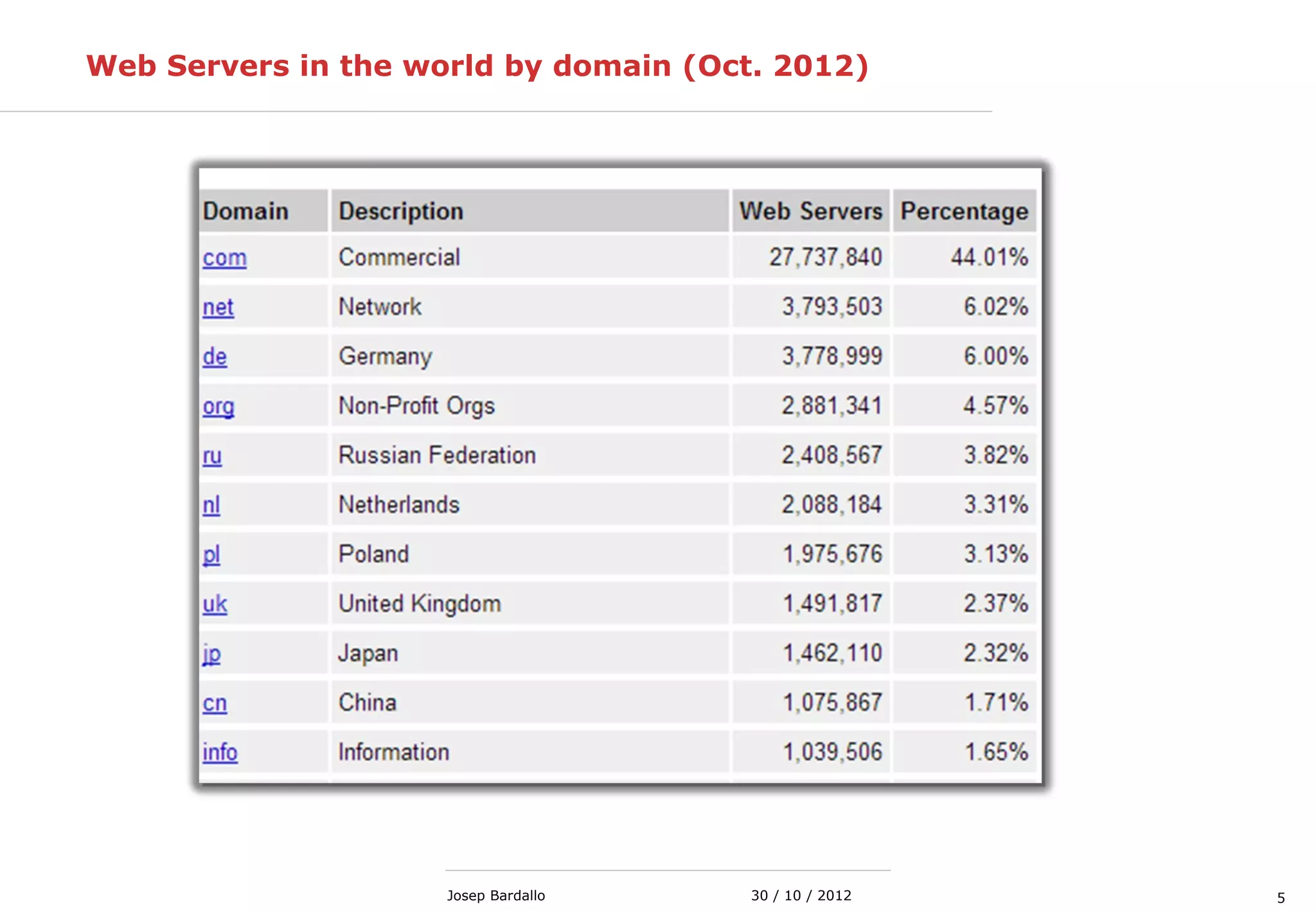
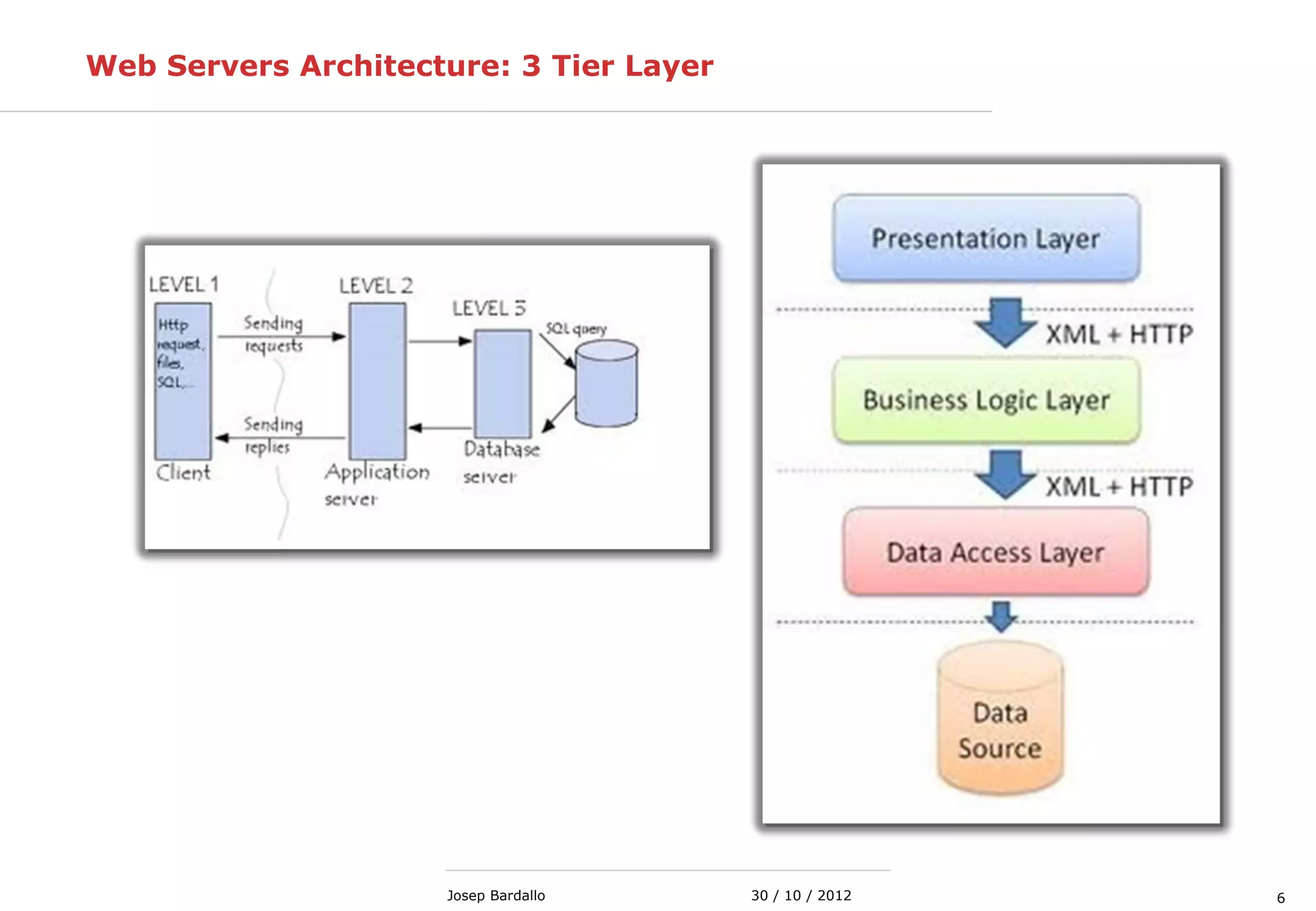
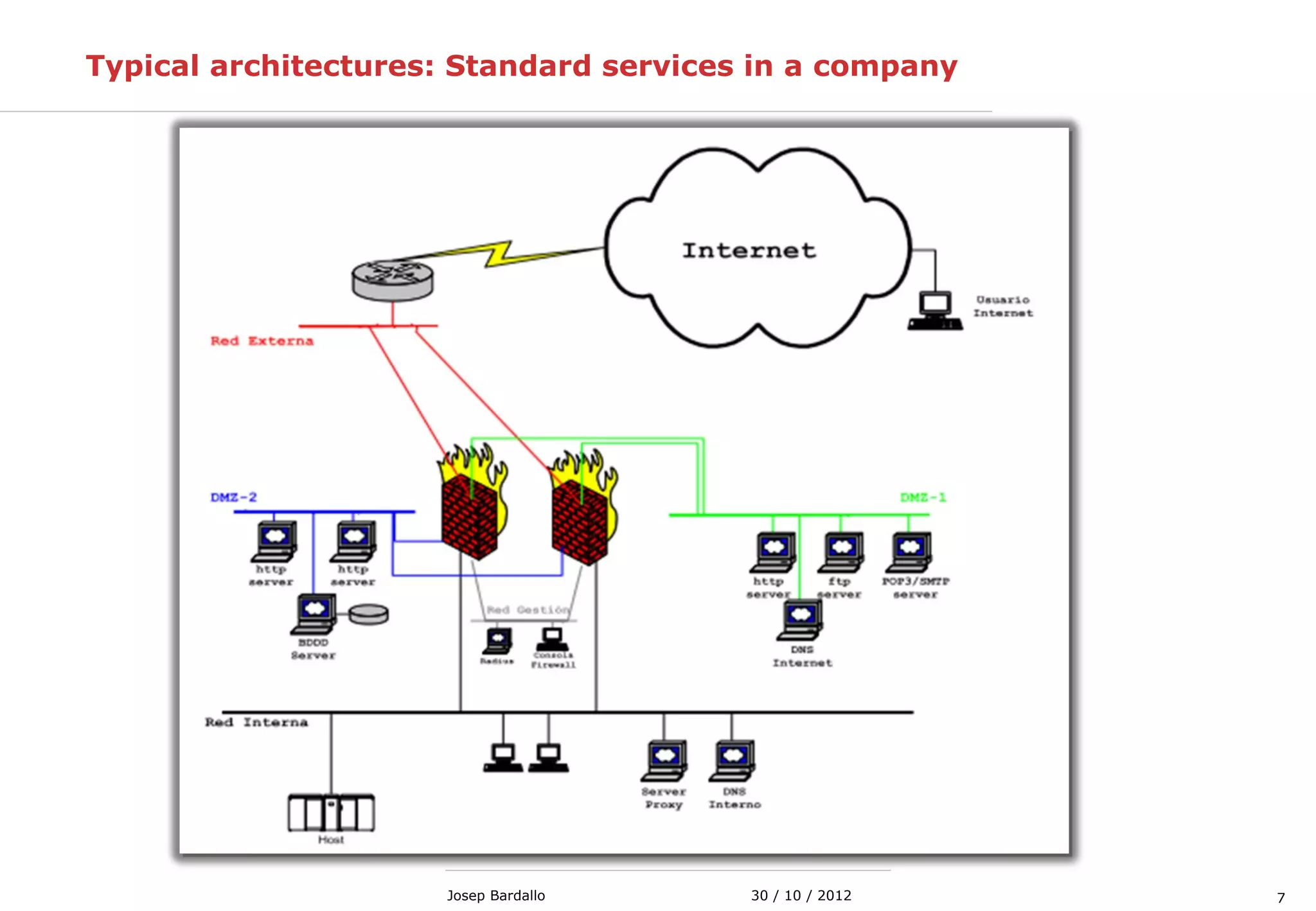
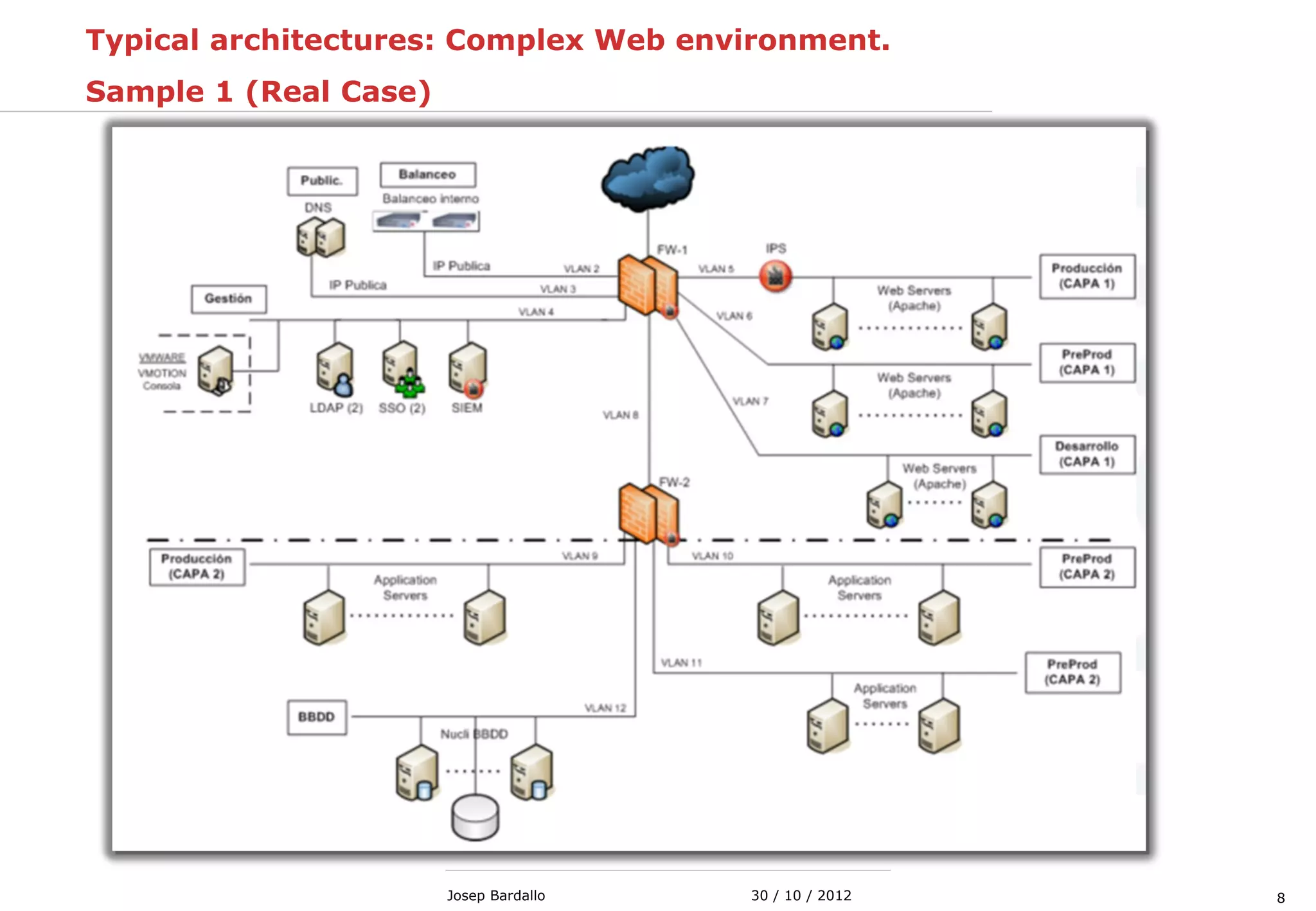
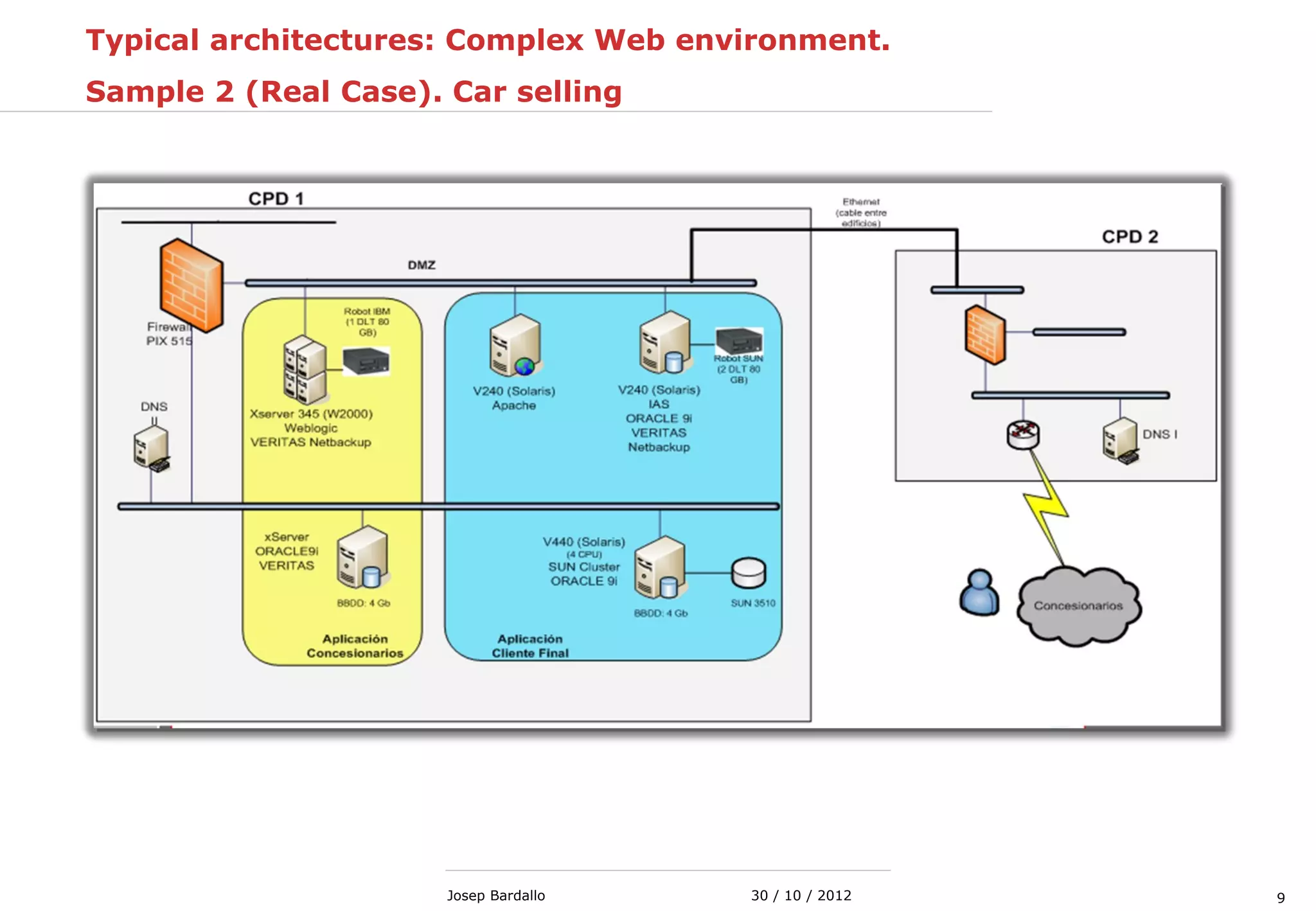
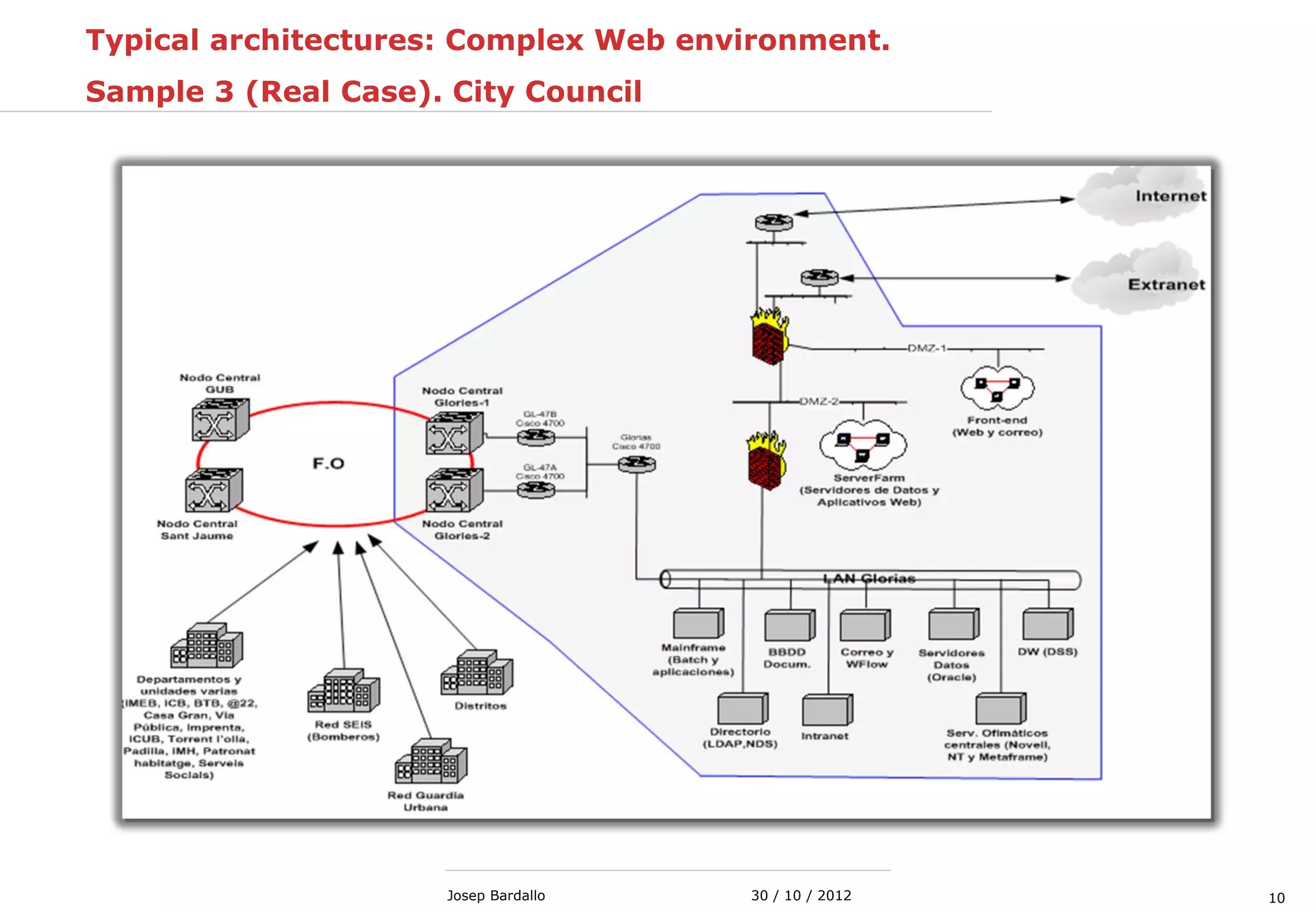
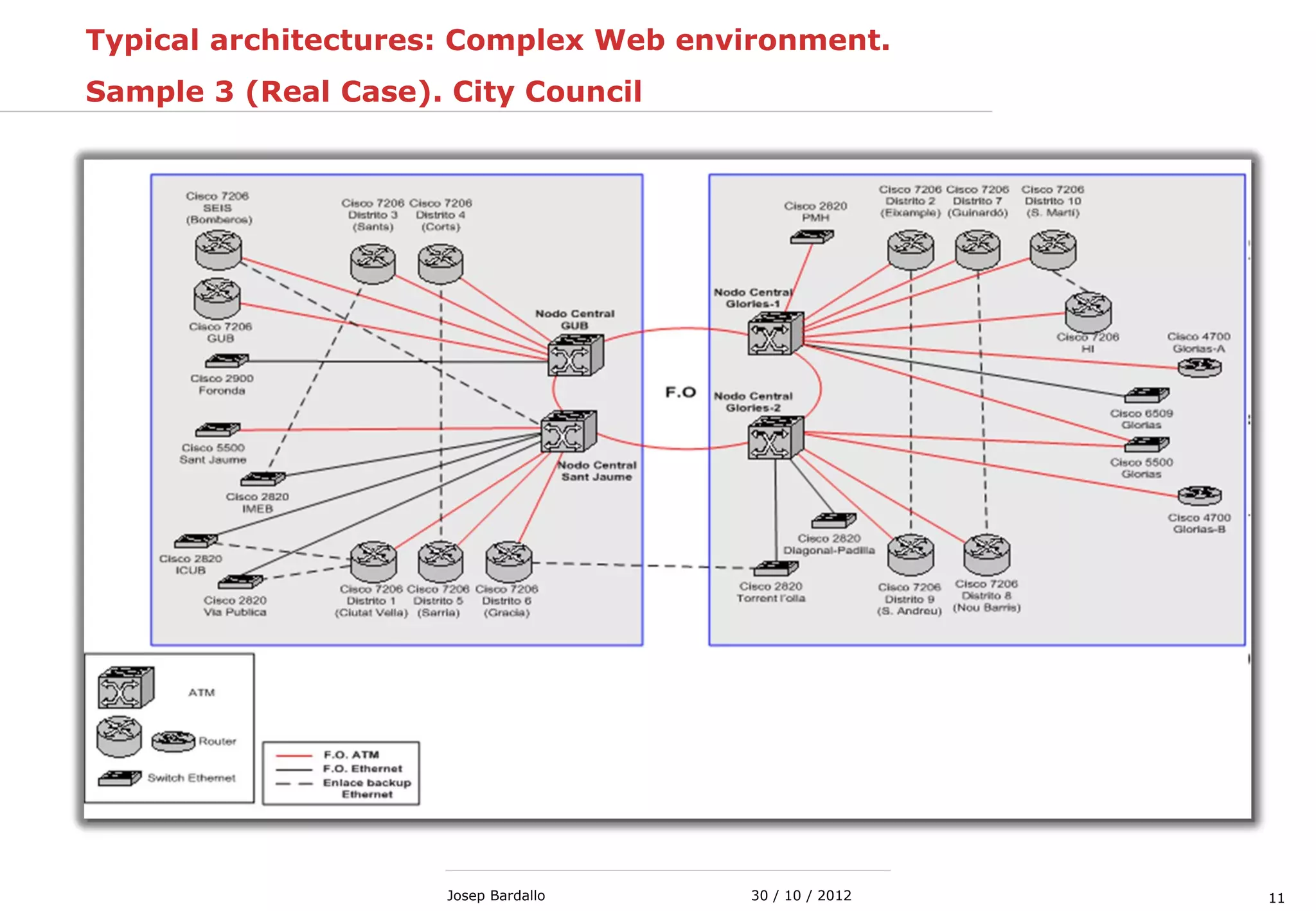
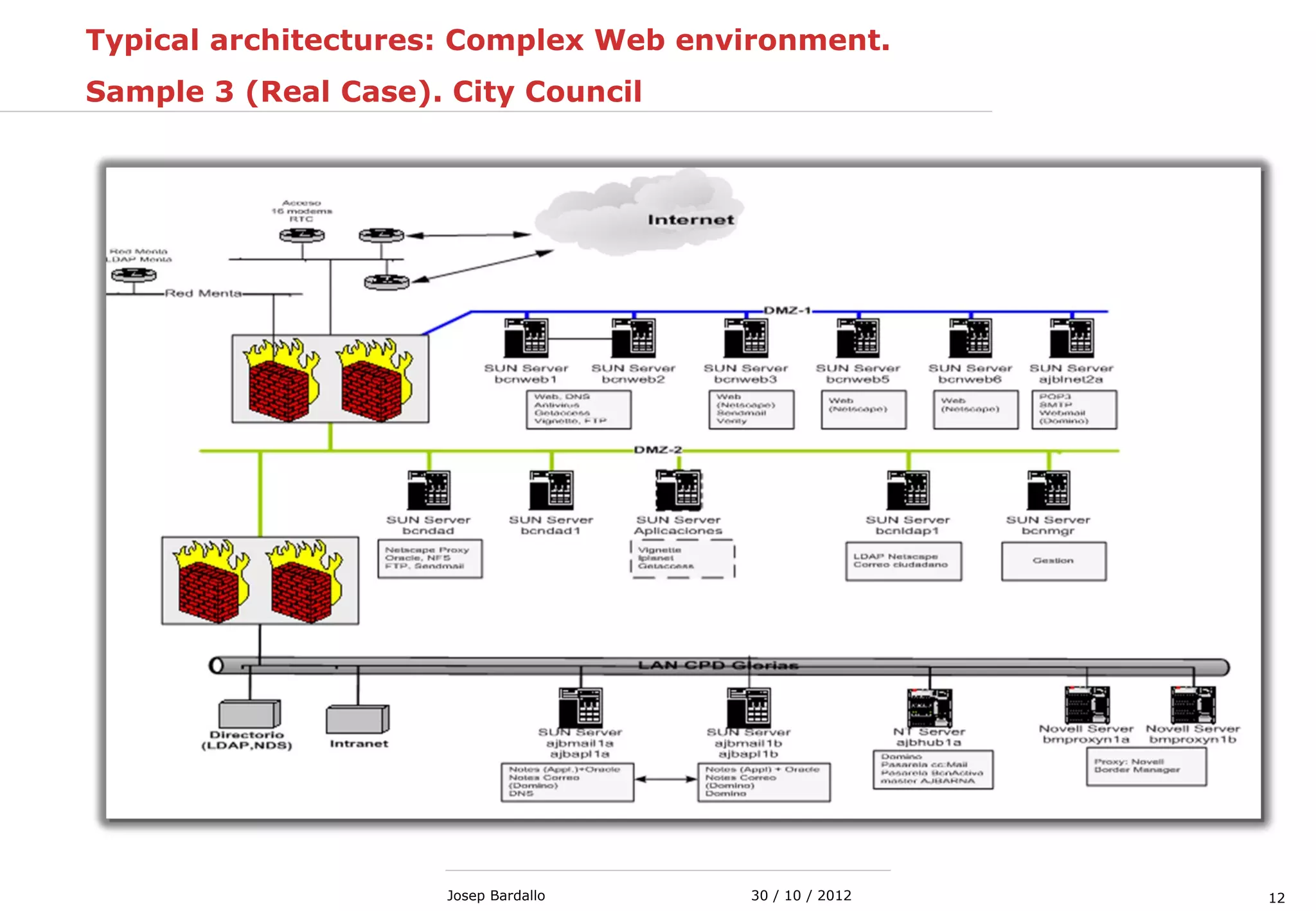
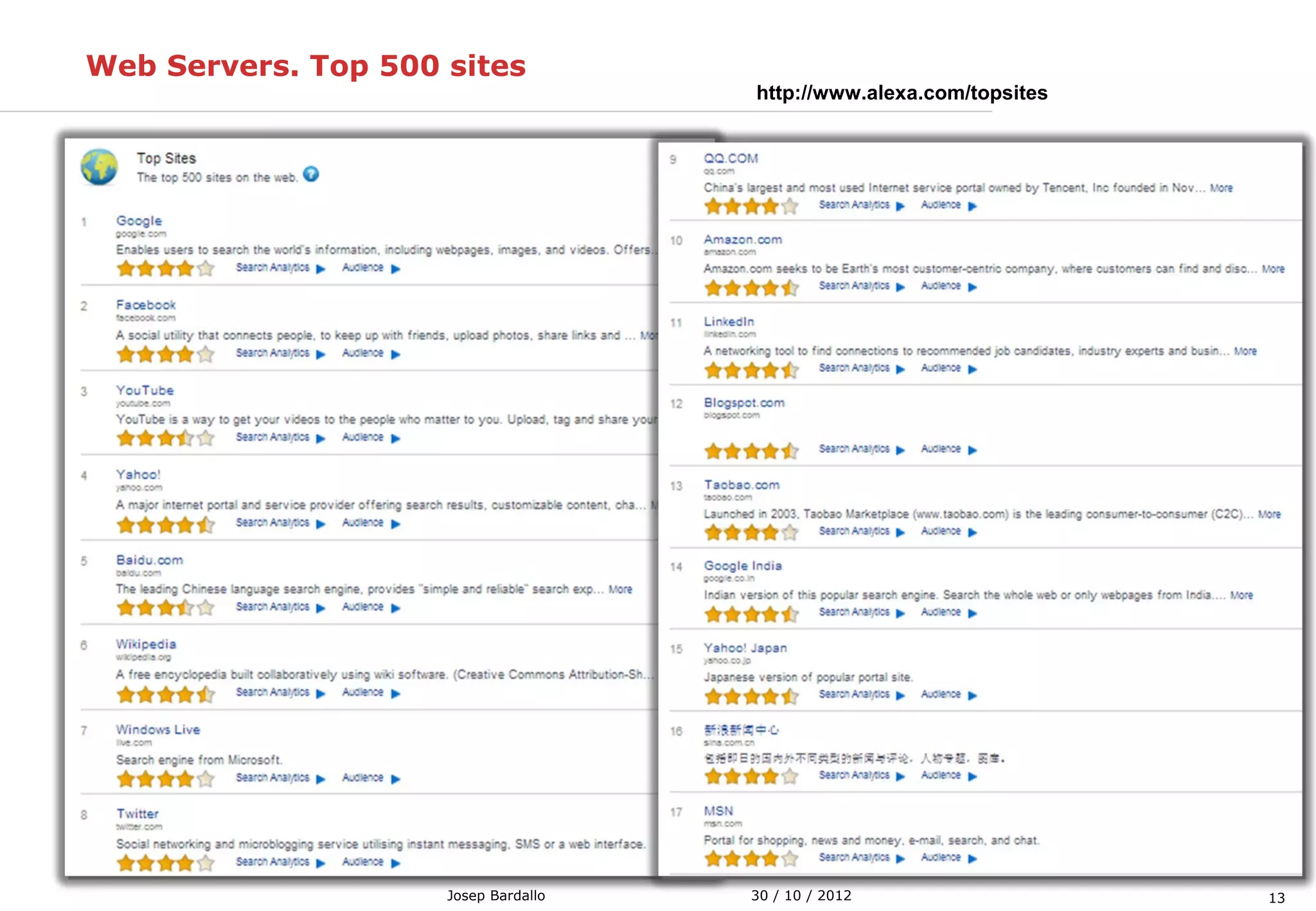
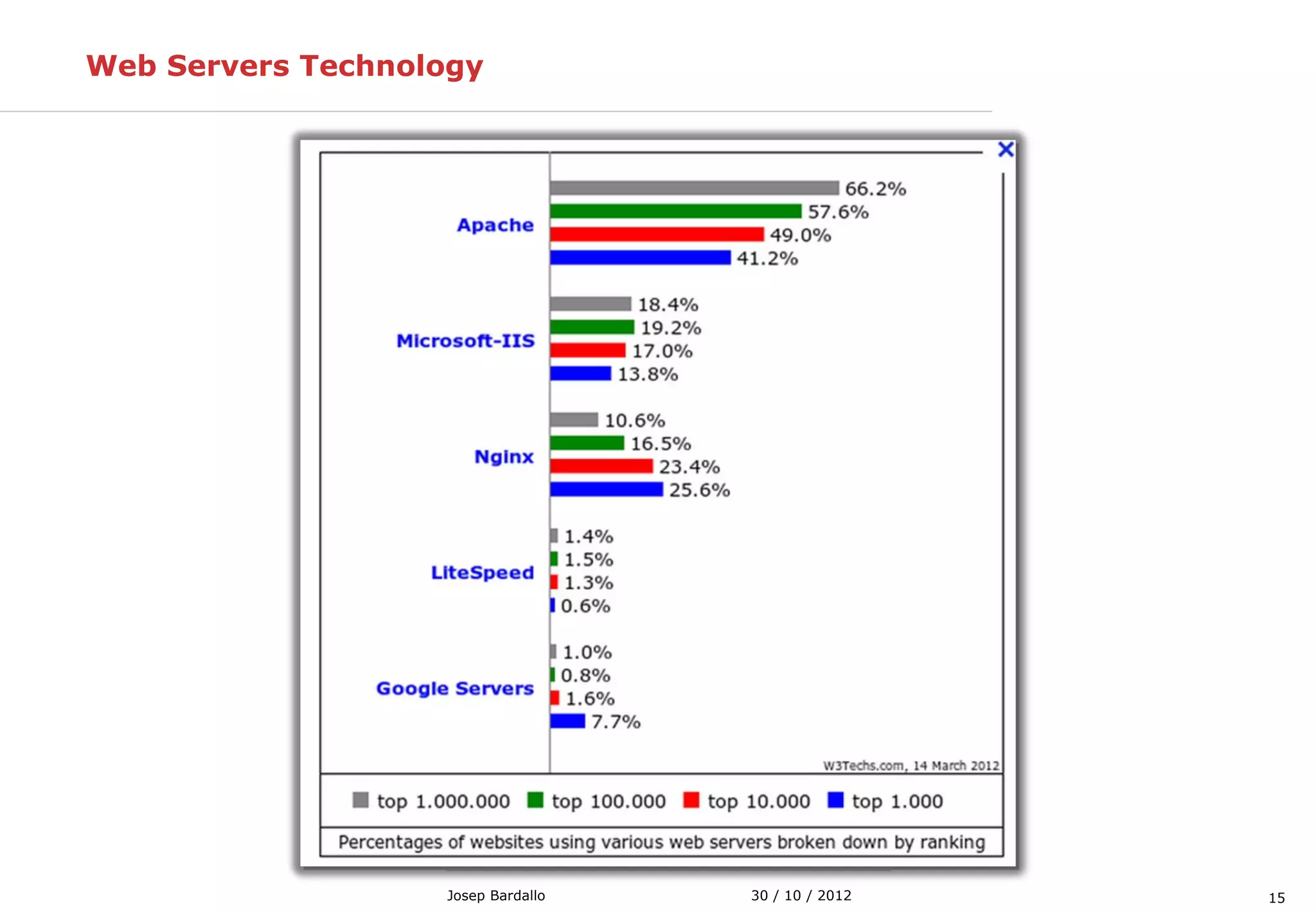
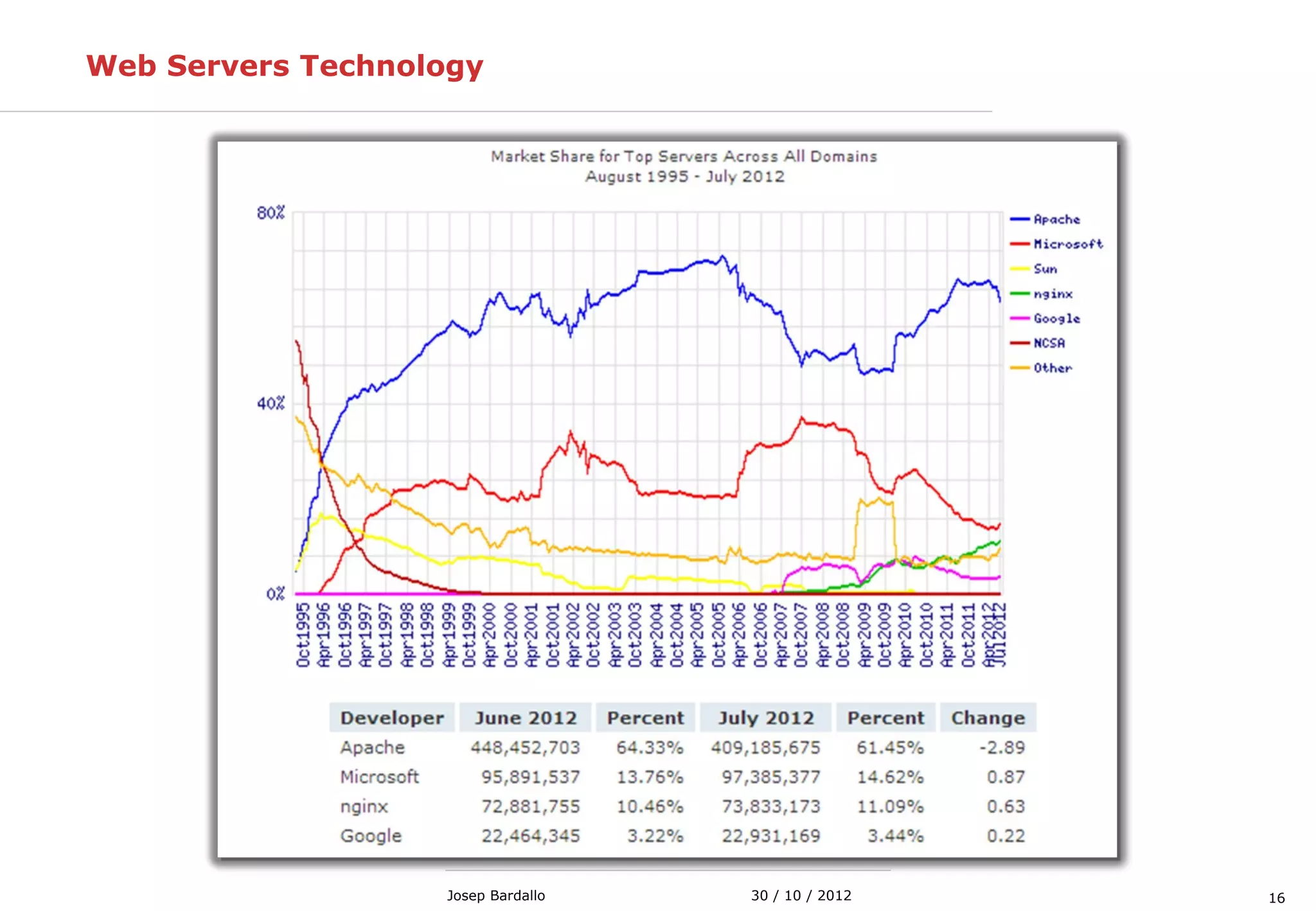
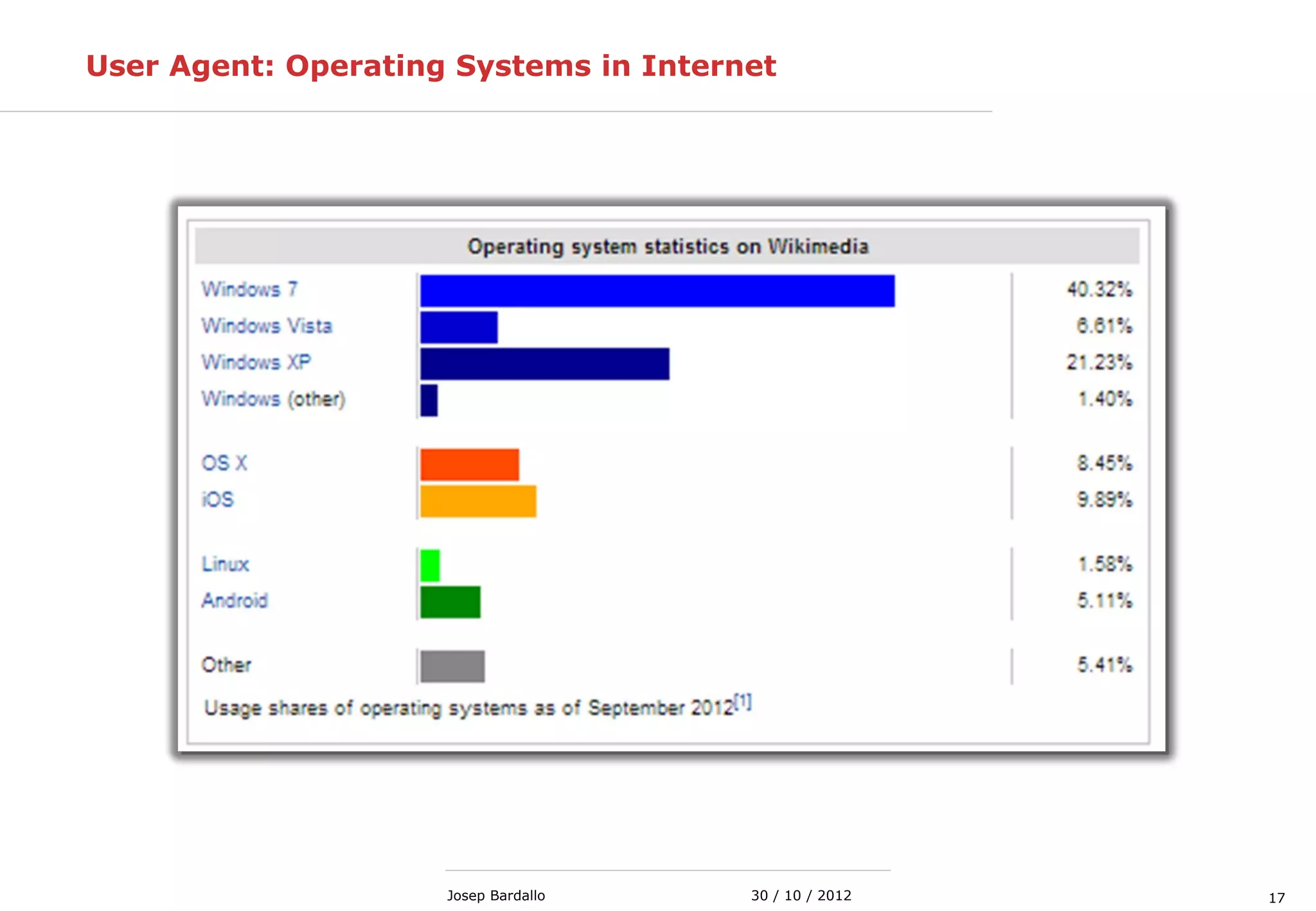
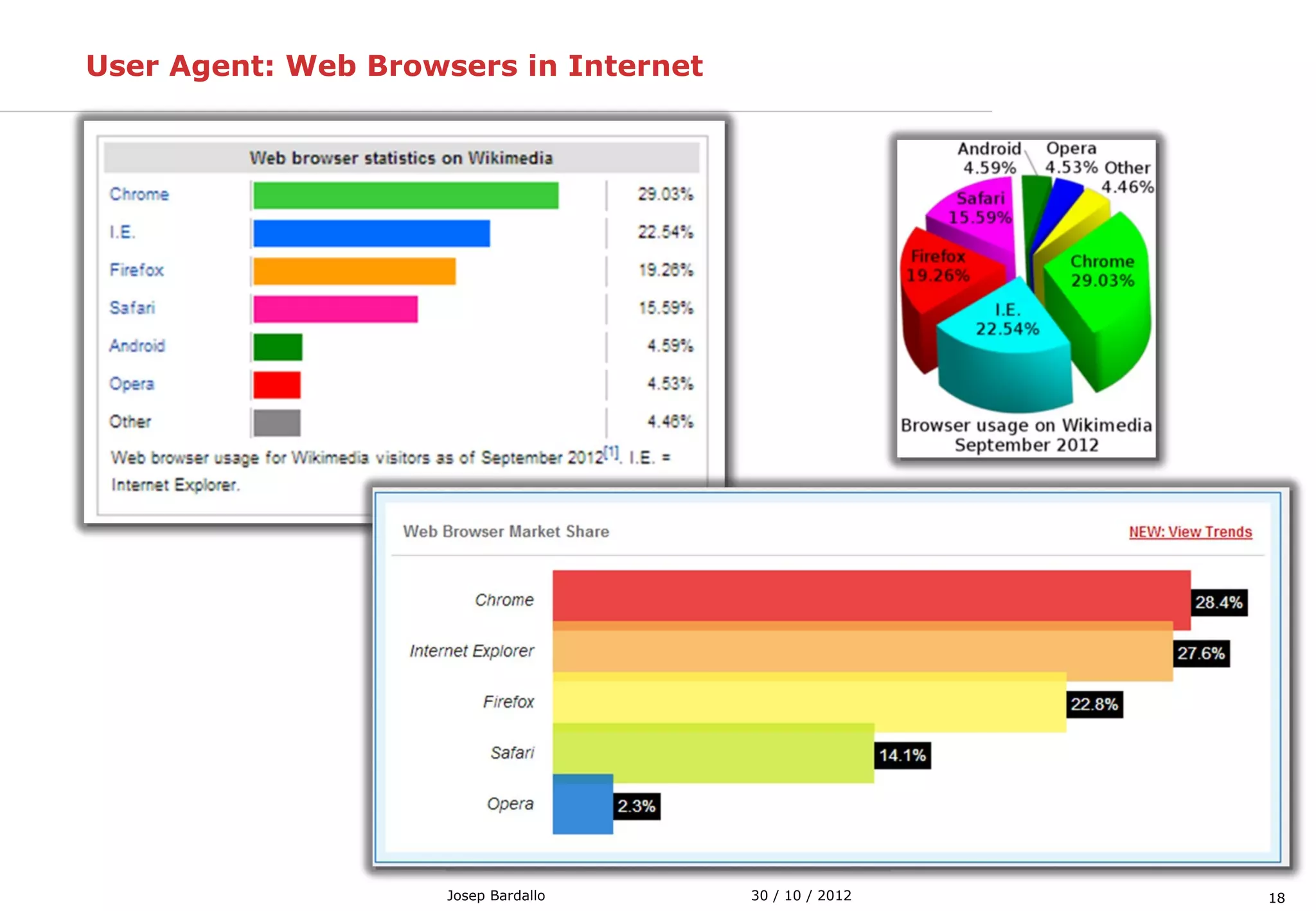
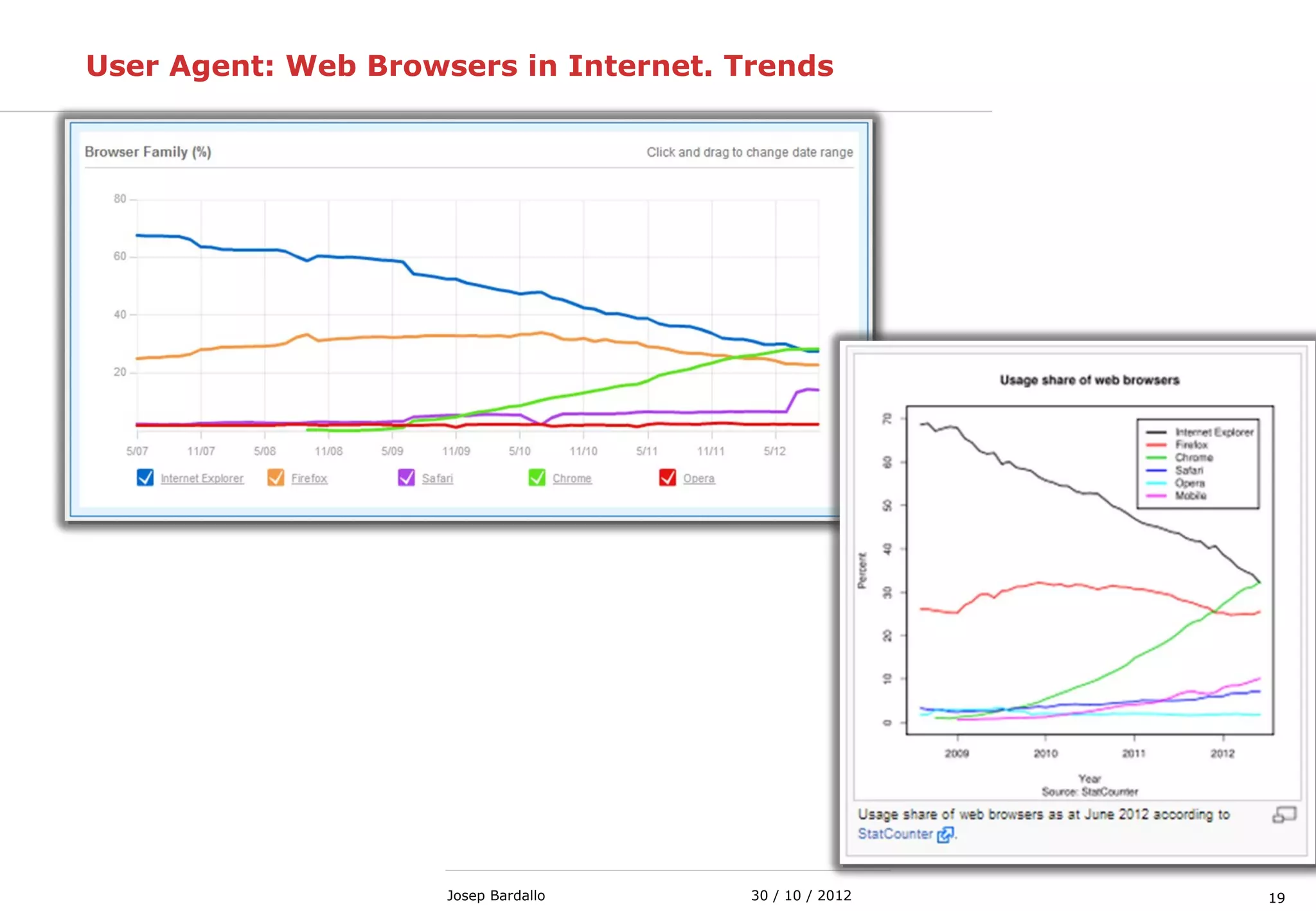
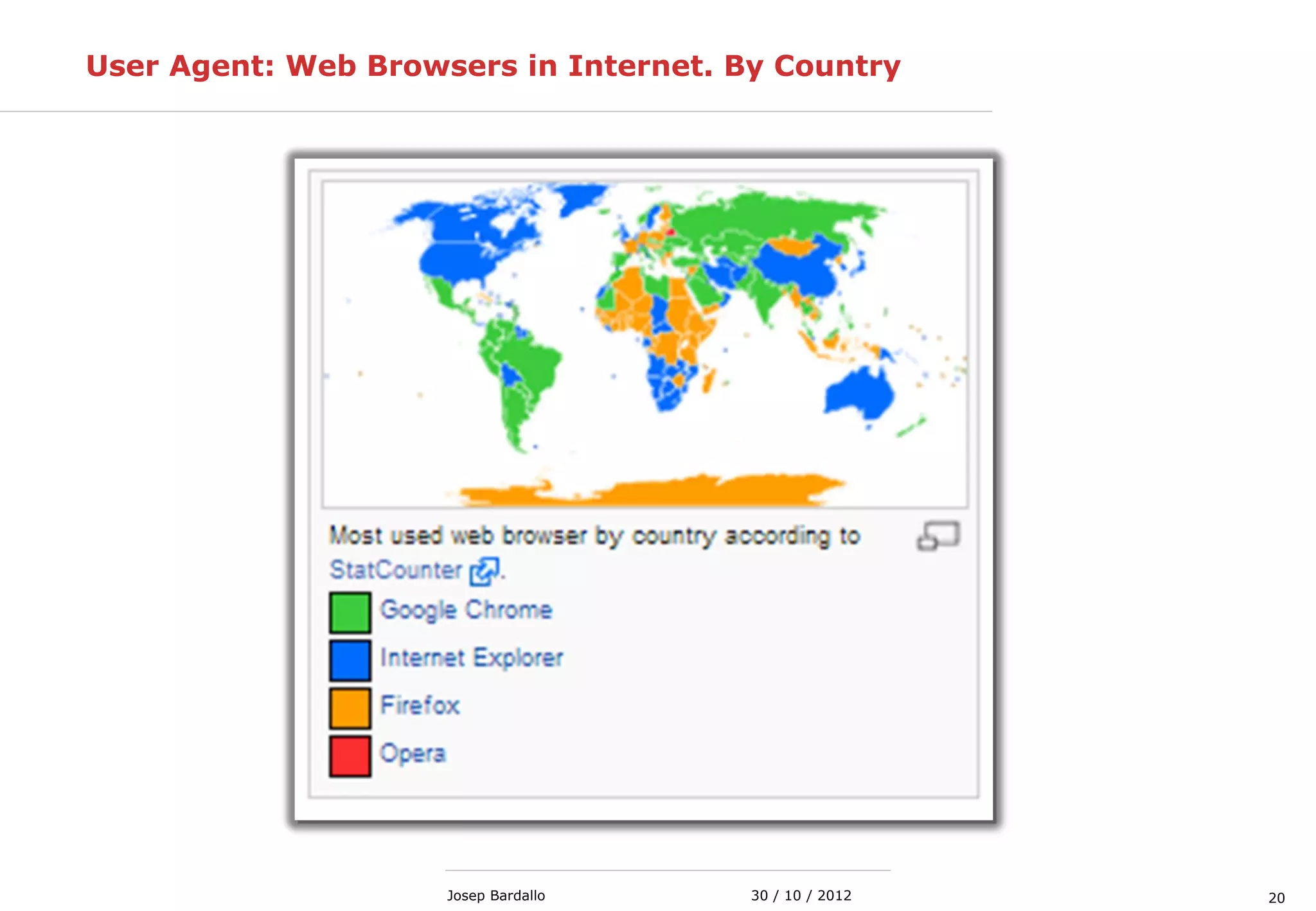
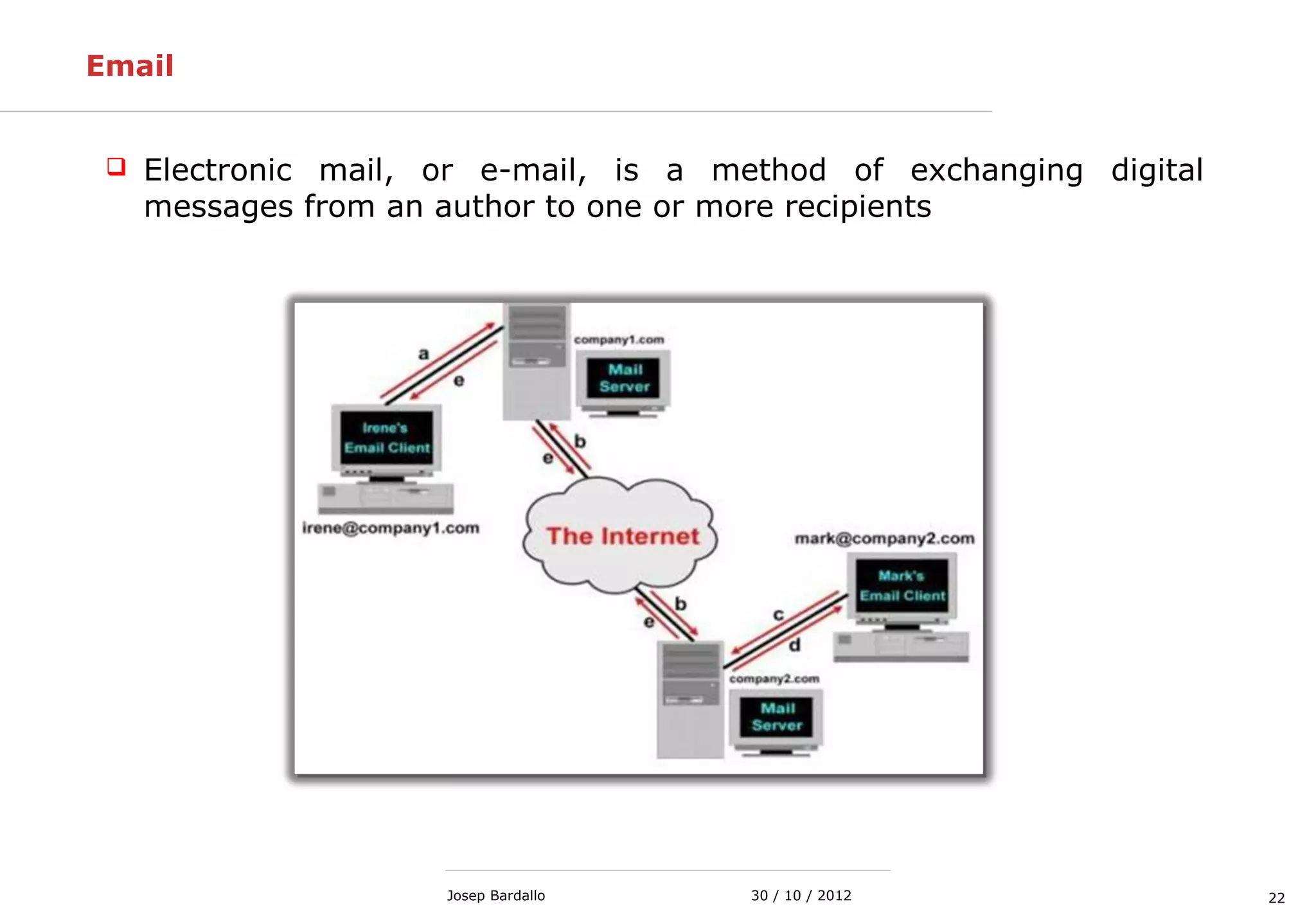
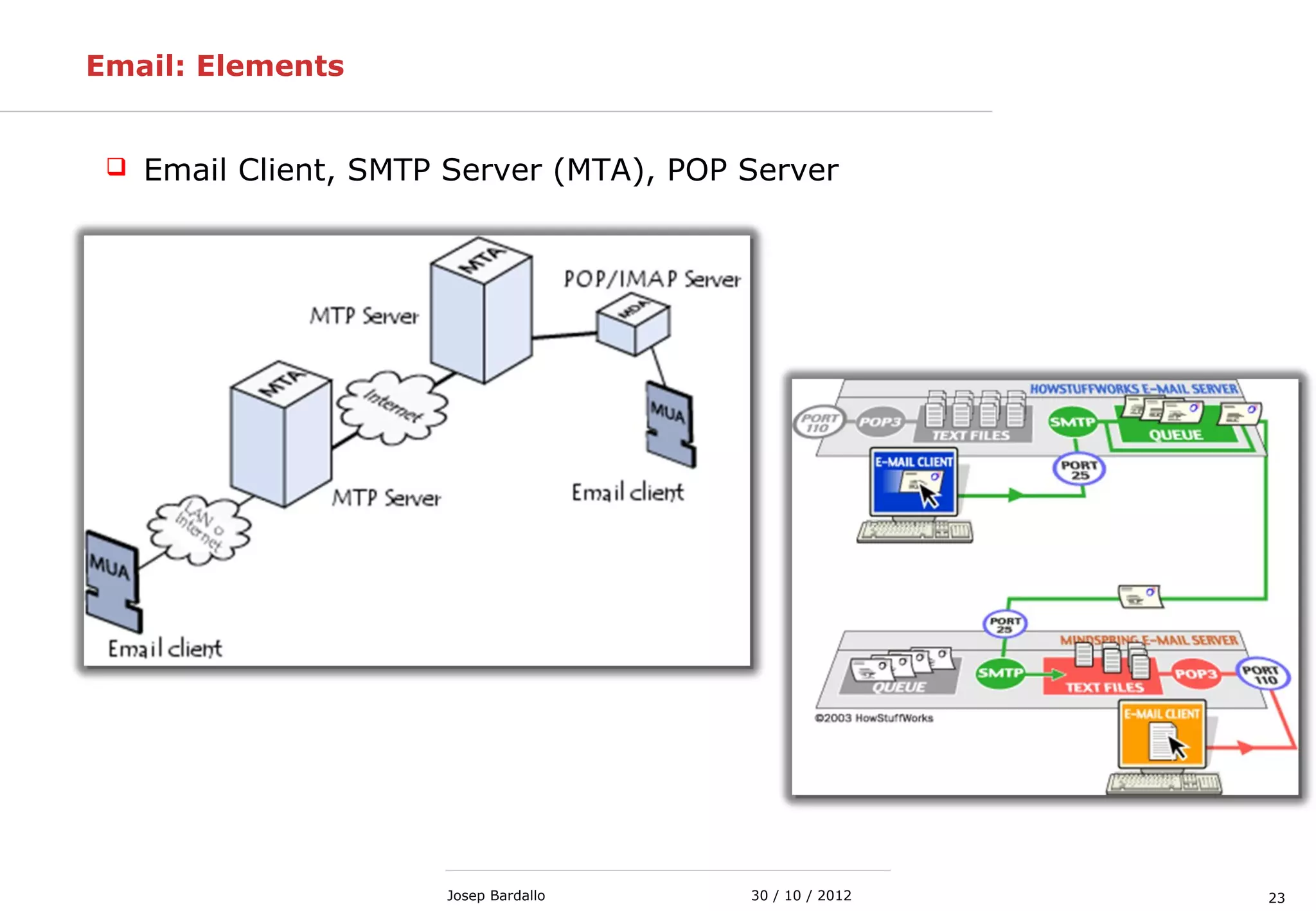
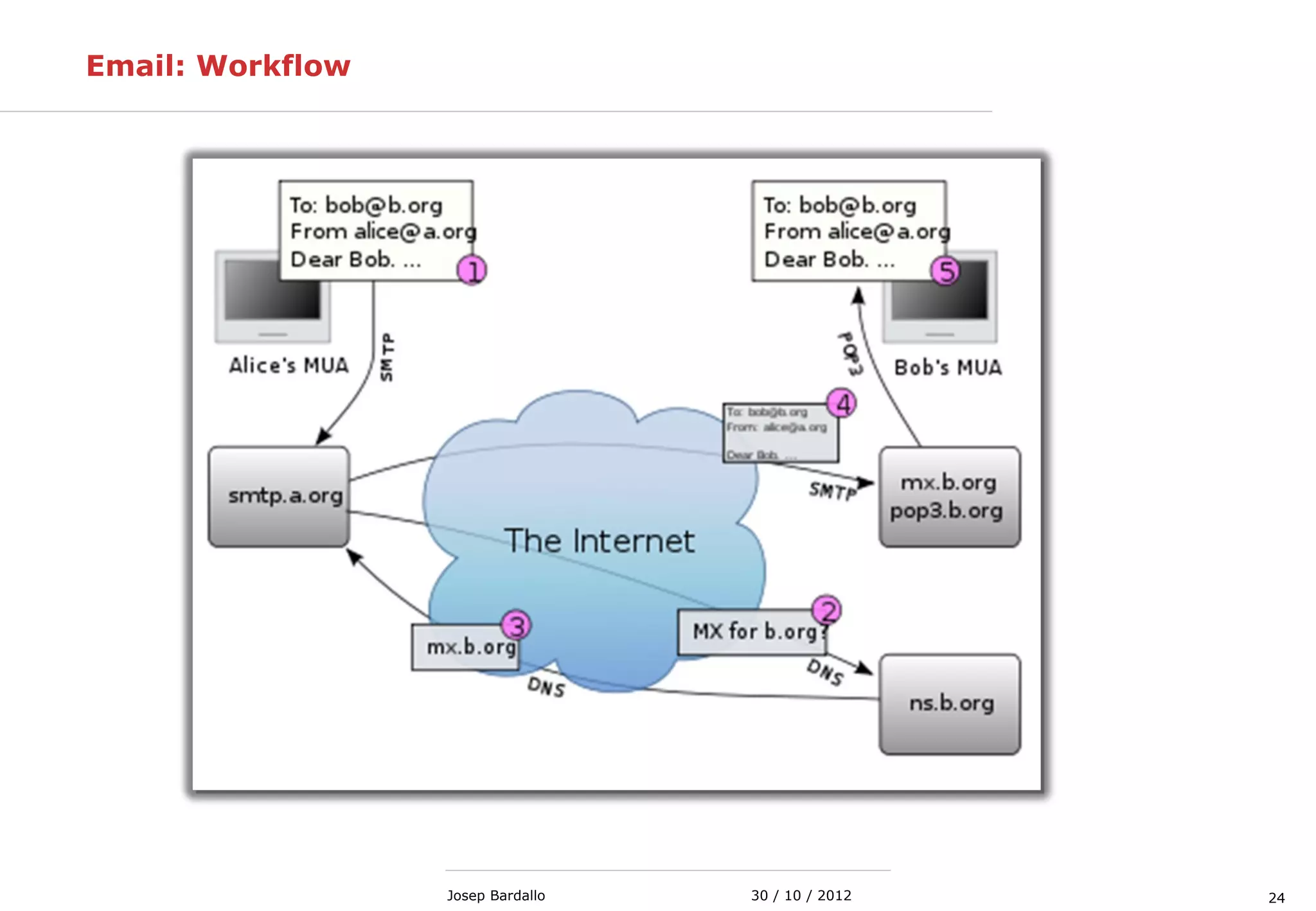
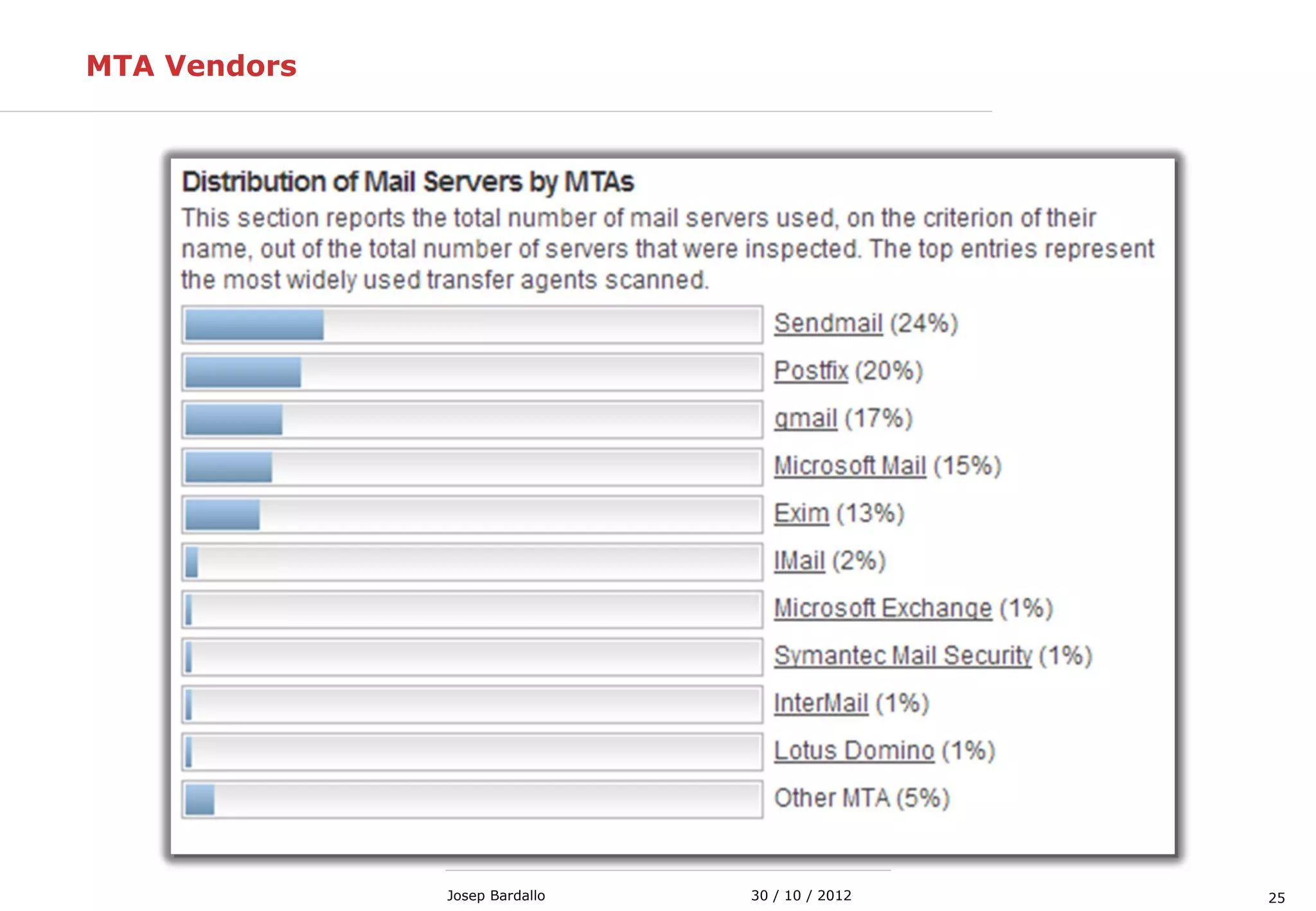
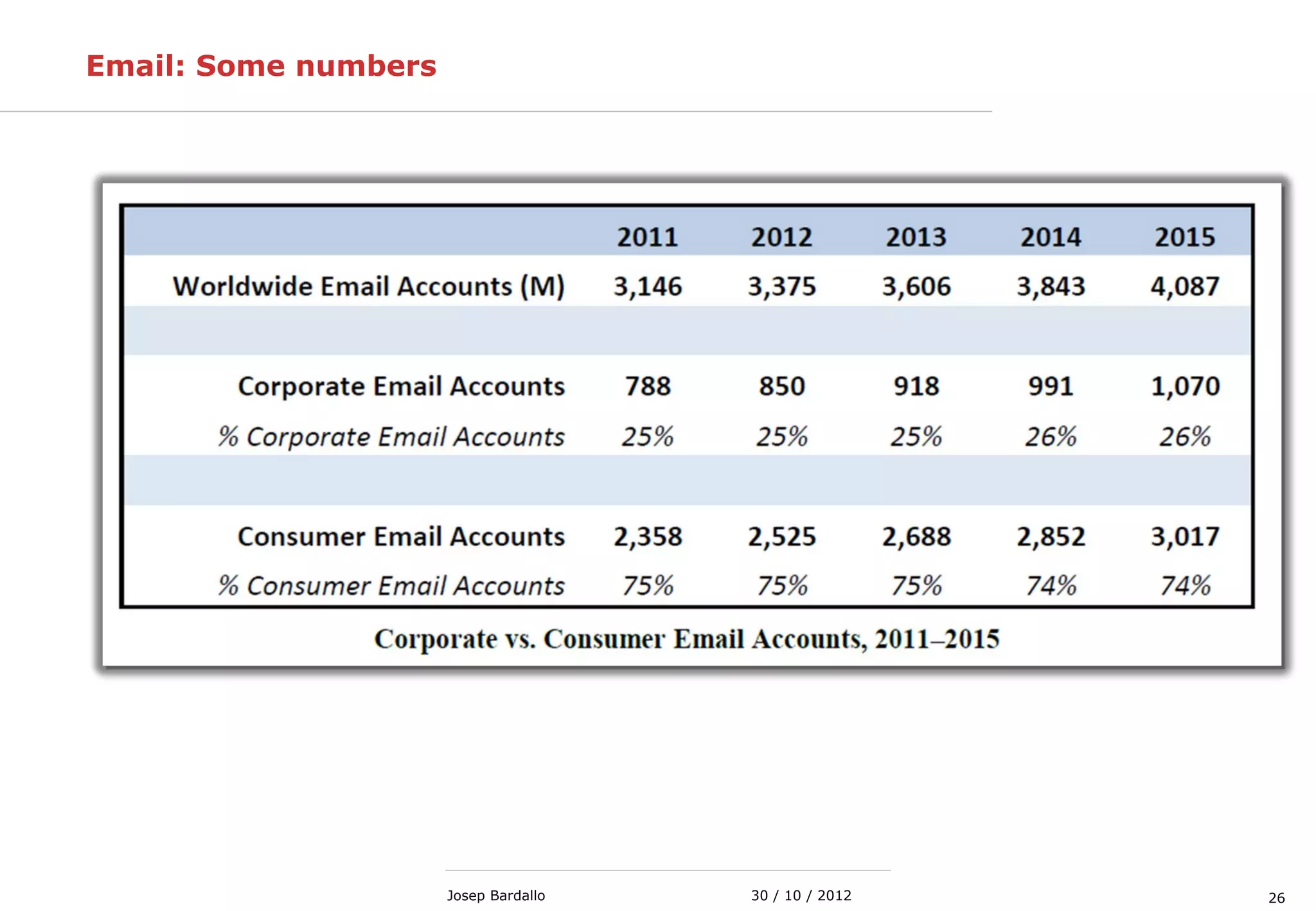
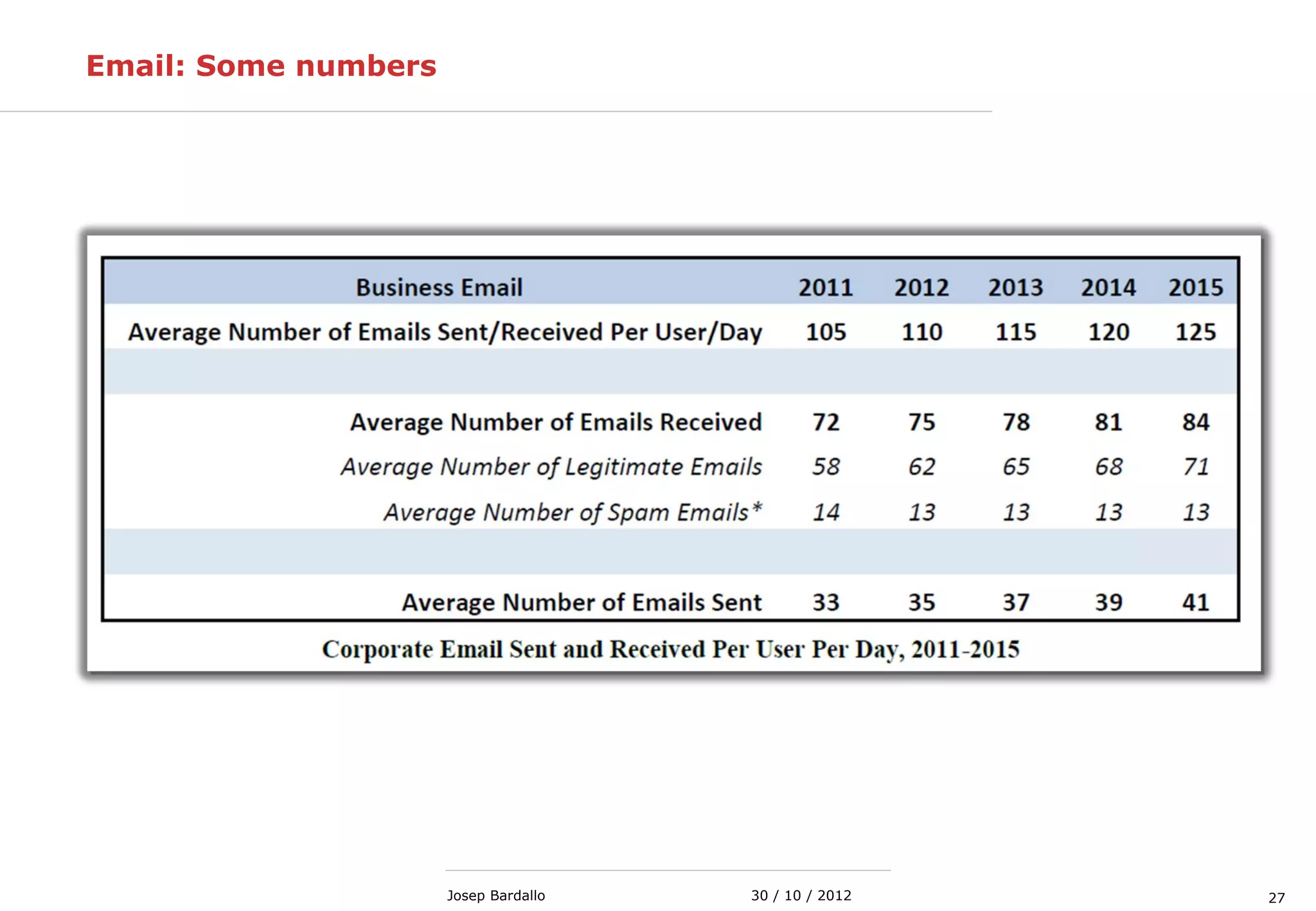
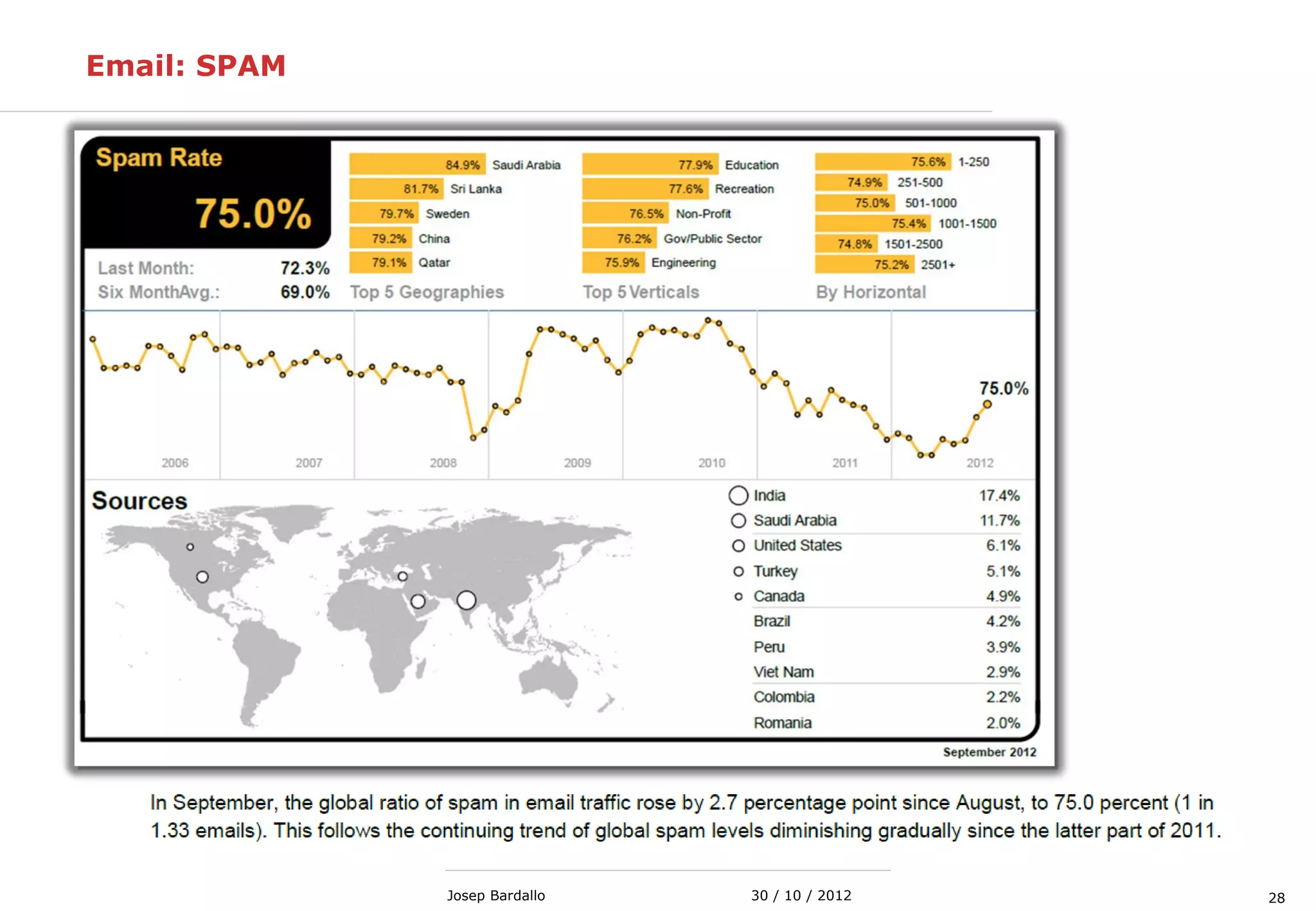
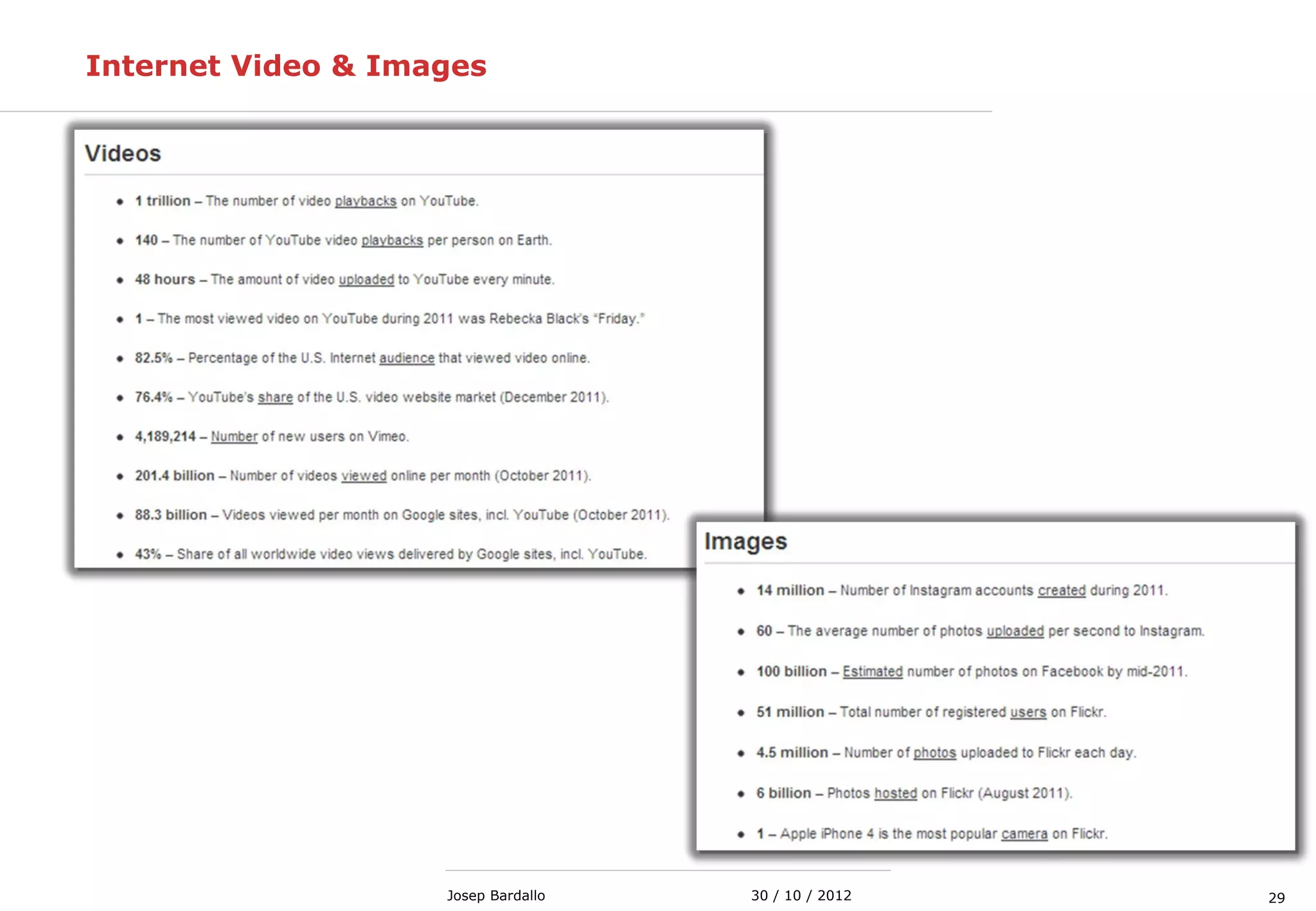
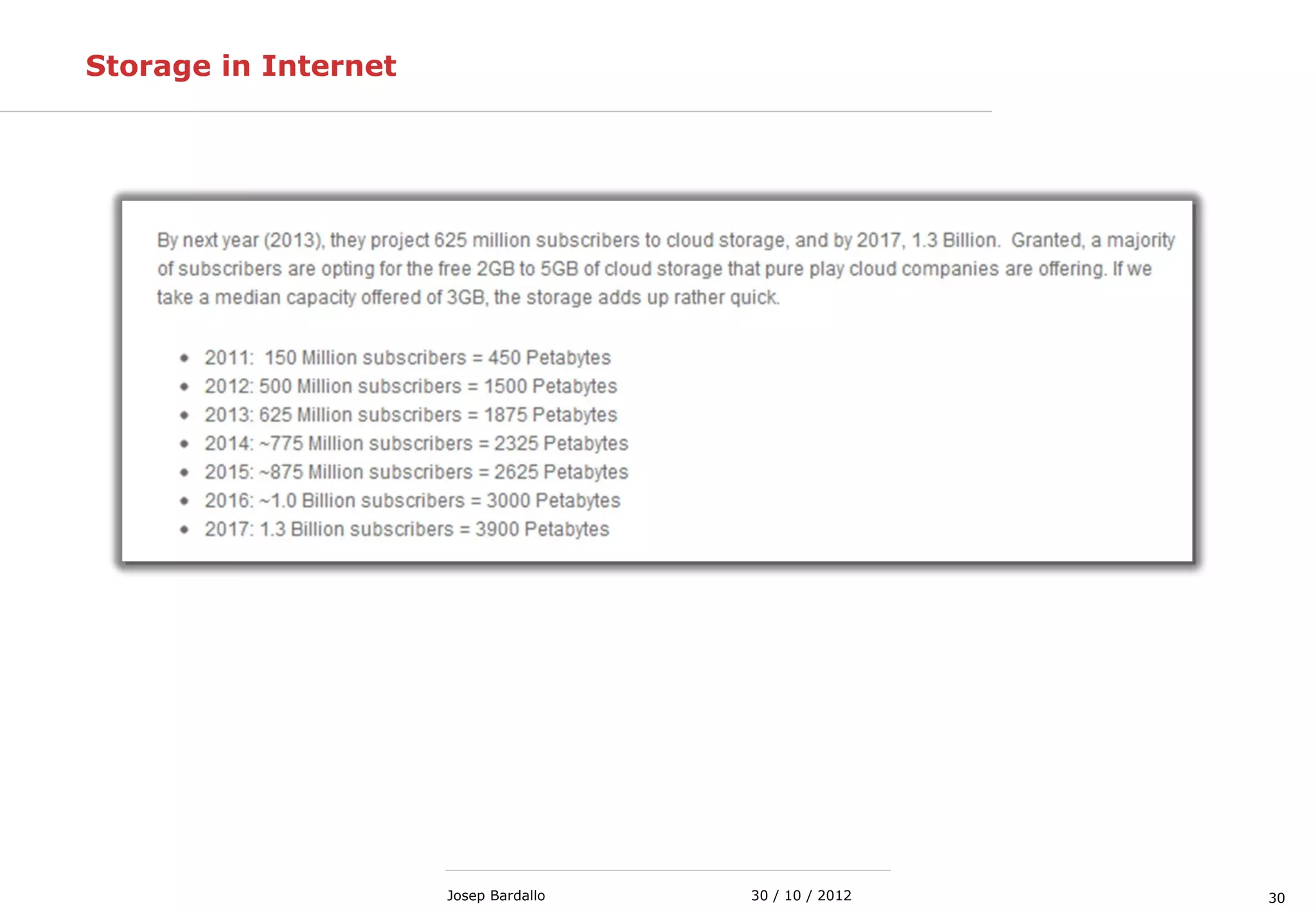
This document discusses web servers and their role in delivering web pages on the internet. It defines a web server as a computer that delivers content via the Hypertext Transfer Protocol (HTTP) and notes they include hardware, operating systems, server software, and TCP/IP protocols. The document also mentions some of the largest web servers in the world like Google, Amazon, and Facebook, with Google estimated to have over 900,000 servers. Finally, it reviews common web server technologies, secure servers using SSL, email services, and storage solutions on the internet.