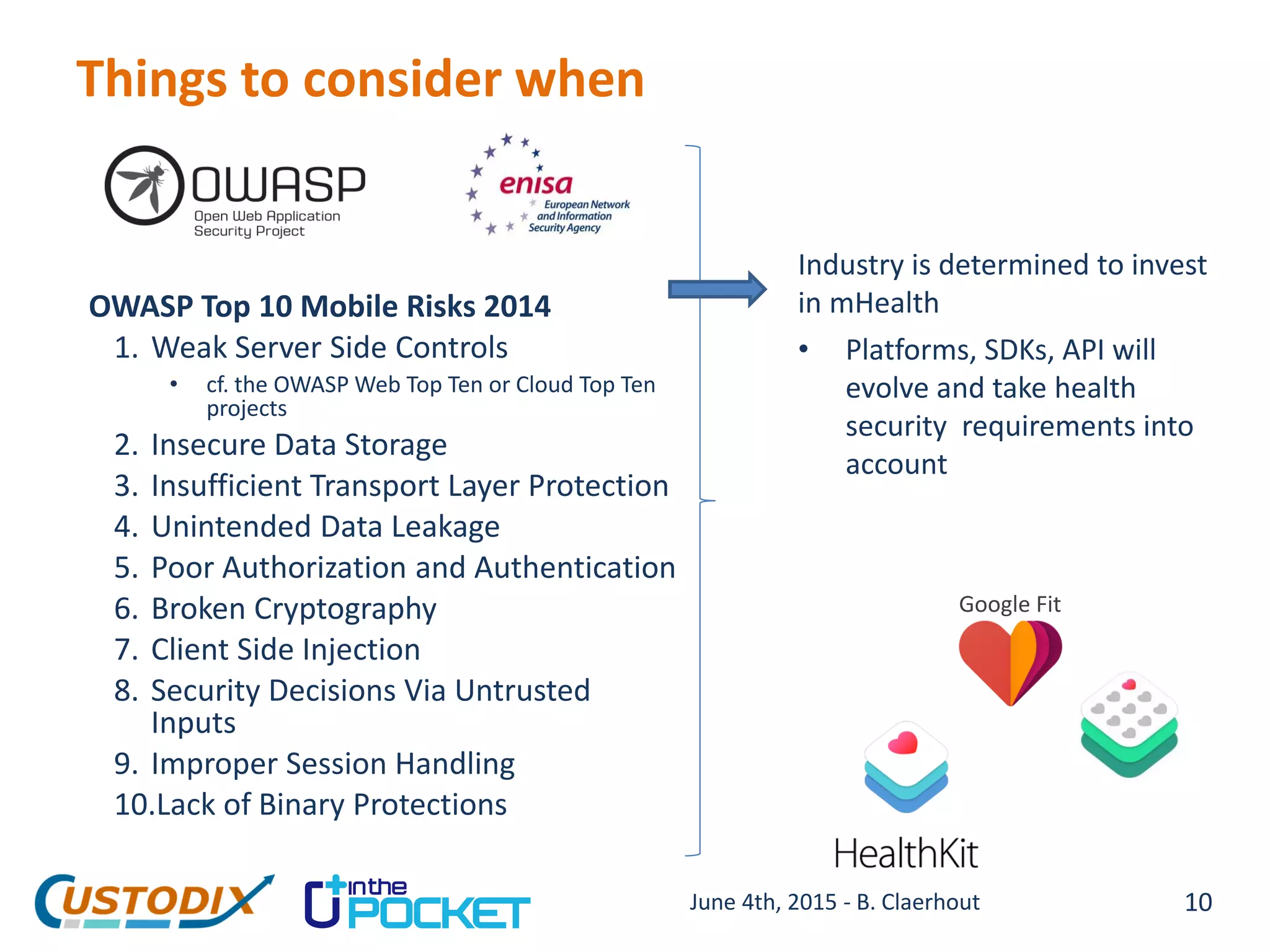
The document discusses the importance of security and privacy in managing sensitive health data, particularly in the context of mobile health (mHealth). It emphasizes the necessity of incorporating data protection strategies from the design stage and highlights various security challenges, including device security, unauthorized access, and legal compliance. Custodix, as a trusted third party in health data management, aims to ensure compliant data collection and protection in a highly complex and evolving technological environment.