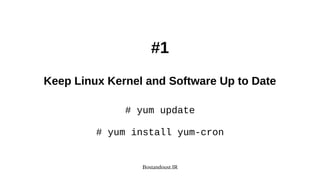
The document is a comprehensive guide on Linux server security and hardening techniques, authored by Saeid Bostandoust, an experienced software engineer and member of various tech associations. It outlines 40 essential security practices including keeping software updated, minimizing vulnerabilities, using centralized authentication services, and implementing strict user account policies. Additionally, it provides instructions on utilizing security tools and configuring systems to ensure better overall security against potential threats.
















![Bostandoust.IR
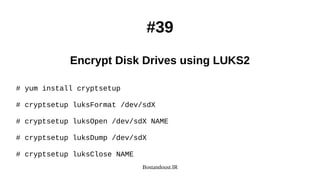
#15
Locking User Accounts After Login Failures
# vi /etc/pam.d/system-auth
# vi /etc/pam.d/password-auth
auth required pam_tally2.so audit deny=3 unlock_time=60 even_deny_root
account required pam_tally2.so
auth requisite pam_faillock.so preauth audit deny=3 unlock_time=60 even_deny_root
auth [default=die] pam_faillock.so authfail audit deny=3 unlock_time=60 even_deny_root
auth sufficient pam_faillock.so authsucc audit deny=3 unlock_time=60 even_deny_root
account required pam_faillock.so
# pam_tally2 --user USER --reset
# faillock --user USER --reset](https://image.slidesharecdn.com/hardening-191115152249/85/Linux-Security-and-Hardening-40-Tips-2019-19-320.jpg)