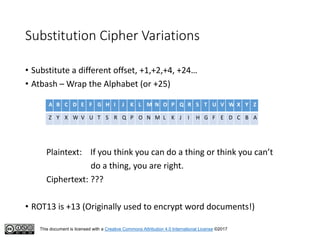
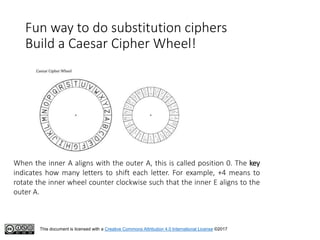
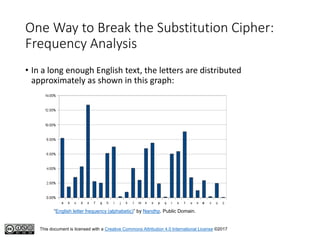
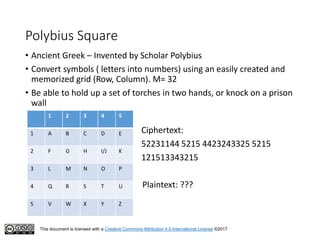
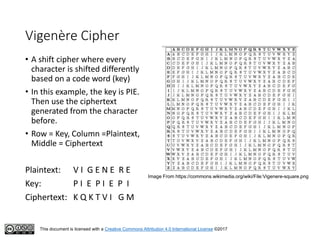
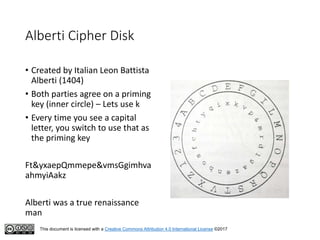
This document serves as an introduction to classical cryptography, covering various historical ciphers such as the Caesar cipher, Vigenère cipher, and Enigma machine. Students will learn about key concepts, encryption and decryption processes, and the vulnerabilities of these methods against modern analysis techniques. While these ciphers were effective in their time, they are now easily cracked using frequency analysis and pattern recognition.