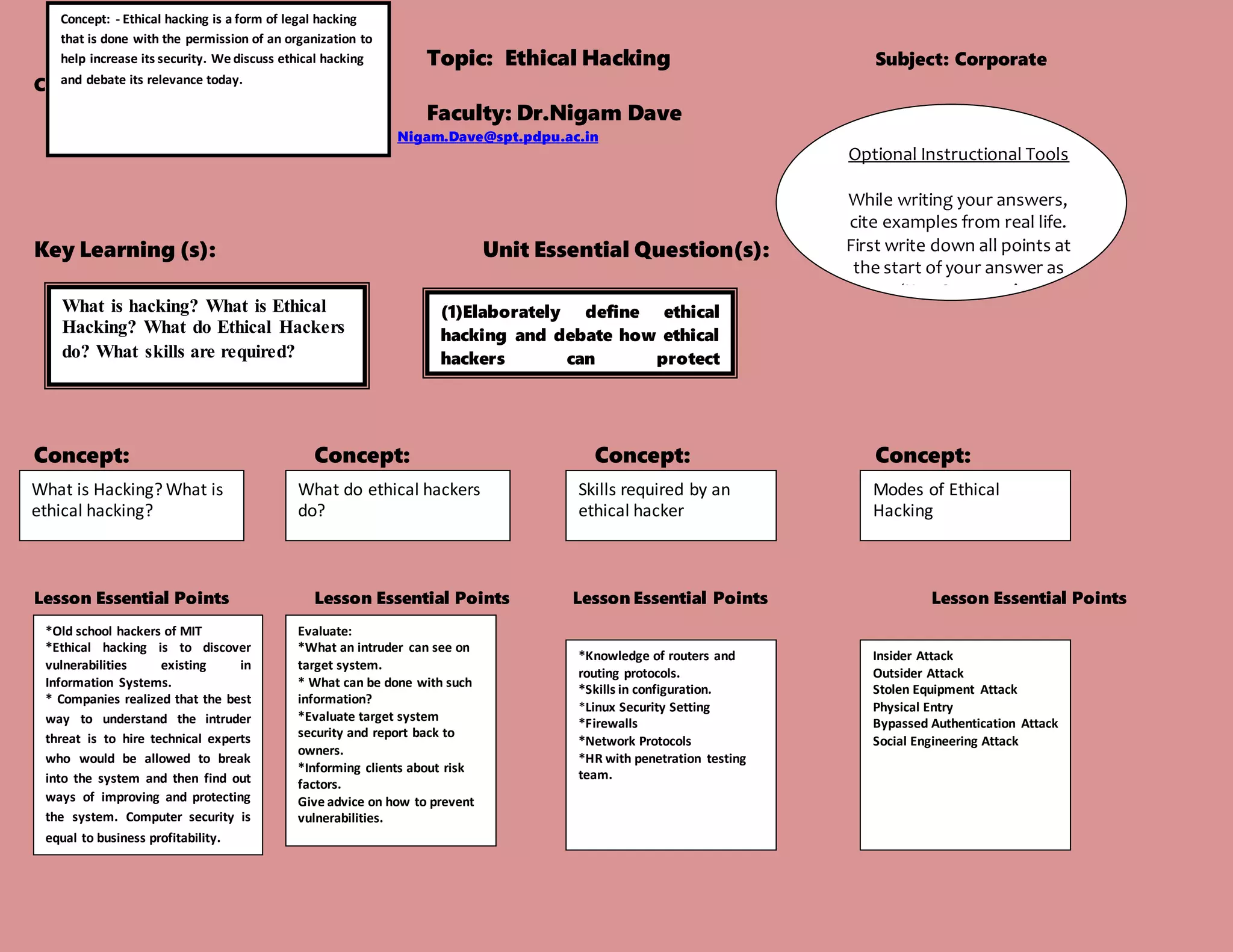
(1) Ethical hacking is a form of legal hacking done with an organization's permission to help increase security. Ethical hackers discover vulnerabilities in information systems and then work with companies to improve protection.
(2) Companies realized hiring ethical hackers allows them to understand intruder threats by allowing experts to penetrate their systems and find ways to strengthen security. Computer security directly impacts business profitability.
(3) Ethical hackers evaluate target systems, identify what intruders can access and what can be done with that information, then inform clients of risks and advise how to prevent vulnerabilities. This requires skills in networking, protocols, firewalls and system configurations.