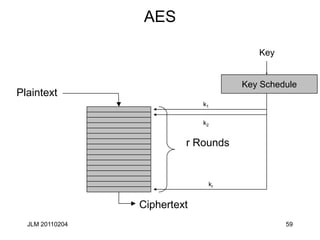
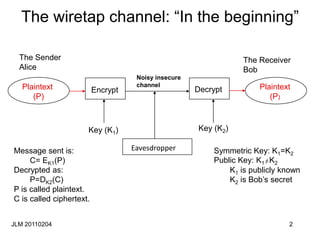
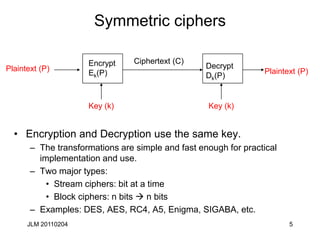
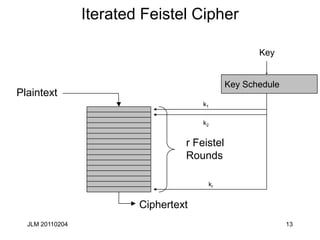
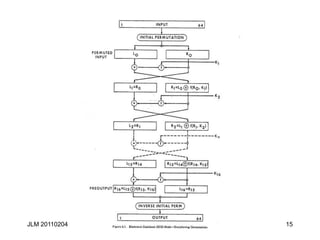
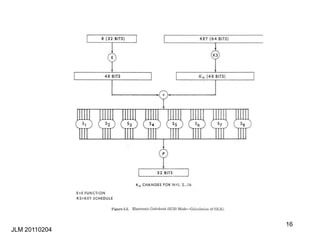
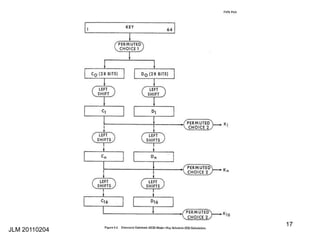
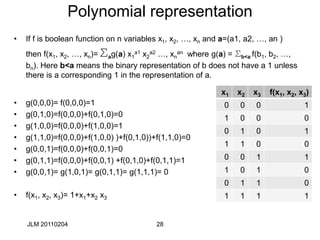
This document discusses block ciphers and their mathematical foundation, highlighting symmetric key cryptography where the same key is used for encryption and decryption. It covers various types of ciphers, practical attacks, and historical implementations, focusing on the Data Encryption Standard (DES) and its vulnerabilities. Key concepts include adversarial threats, cipher characteristics, and techniques to enhance security against cryptanalysis.
















![JLM 20110204 40
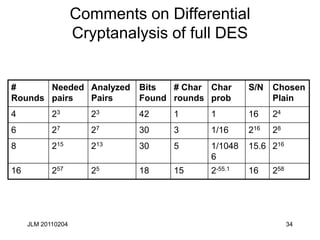
Linear and near linear dependence
• Here is a linear relationship over GF(2) in S5 that holds with
probability 52/64 (from NS5(010000,1111)= 12:
• X[2] Y[1] Y[2] Y[3] Y[4]=K[2] 1.
• Sometimes written: X[2] Y[1,2,3,4]=K[2] 1.
• You can find relations like this using the “Boolean Function”
techniques we describe a little later
• After applying P, this becomes
X[17] F(X,K)[3,8,14,25]= K[26] 1
S5
K[1..6]
Y[1..4]
X[1..6]](https://image.slidesharecdn.com/class5jf-240428053117-a04fbf59/85/class5jf-pptx-Block-cipher-in-information-security-40-320.jpg)
![JLM 20110204 41
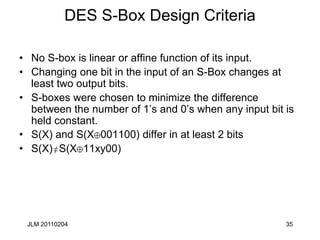
Linear Cryptanalysis of 3 round DES
X[17] Y[3,8,14,25]= K[26] 1, p= 52/64
• Round 1
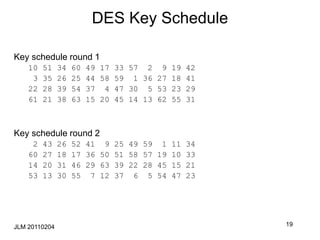
X1[17] Y1[3,8,14,25]= K1[26] 1
PR[17] PL[3,8,14,25] R1[3,8,14,25]=
K1[26] 1
• Round 3
X3[17] Y3[3,8,14,25]= K3[26] 1
R1[3,8,14,25] CL[3,8,14,25] CR[17]=
K3[26] 1
• Adding the two get:
PR[17] PL[3,8,14,25] CL[3,8,14,25] CR[17]=
K1[26] K3[26]
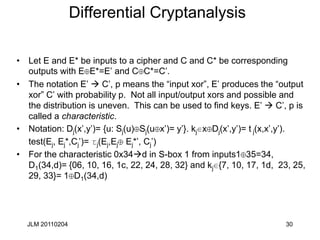
Thus holds with p= (52/64)2+(12/64)2=.66
PL PR
CL CR
F
X1, 17
F
X2
F
X3
k1
k2
k3
Y1,
3,8,14,25
Y2
Y3
L1
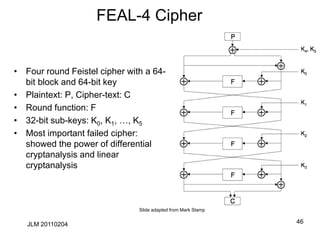
L2
L0 R0
R1
R2](https://image.slidesharecdn.com/class5jf-240428053117-a04fbf59/85/class5jf-pptx-Block-cipher-in-information-security-41-320.jpg)
![JLM 20110204 42
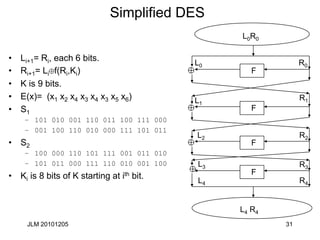
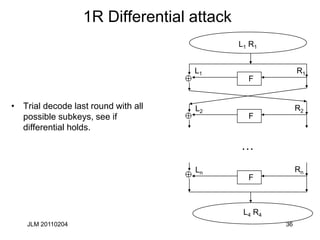
Piling up Lemma
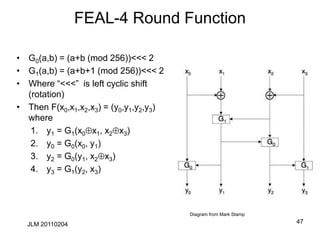
• Let Xi (1cicn) be independent random variables whose
values are 0 with probability pi. Then the probability that
X1 X2 ... Xn= 0 is
½+2n-1 P[1,n] (pi-1/2)
Proof:
By induction on n. It’s tautological for n=1.
Suppose Pr[X1 X2 ... Xn-1= 0]= q= ½+2n-2 P[1,n-1] (pi-1/2).
Then Pr[X1 X2 ... Xn= 0]= qpn +(1-q)(1-pn)= ½+2n-1 P[1,n]
(pi-1/2) as claimed.](https://image.slidesharecdn.com/class5jf-240428053117-a04fbf59/85/class5jf-pptx-Block-cipher-in-information-security-42-320.jpg)
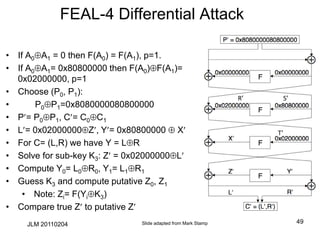
![JLM 20110204 43
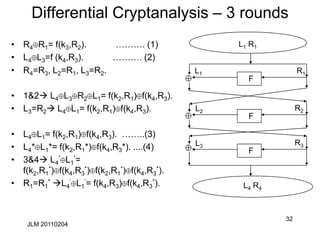
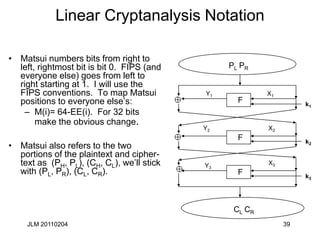
Linear Cryptanalysis of full DES
• Can be accomplished with ~243 known plaintexts, using a14 round
approximation
– For each 48 bit last round sub-key, decrypt cipher-text
backwards across last round for all sample cipher-texts
– Increment count for all sub-keys whose linear expression holds
true to the penultimate round
– This is done for the first and last round yielding 13 key bits each
(total: 26)
• Here they are:
PR[8,14,25] CL[3,8,14,25] CR[17]= K1[26] K3[4] K4[26] K6[26]
K7[4] K8[26] K10[26] K11[4] K12[26] K14[26]
with probability ½ -1.19x2-21
CR[8,14,25] PL[3,8,14,25] PR[17]= K13[26] K12[24] K11[26]
K9[26] K8[24] K7[26] K5[26] K4[4] K3[26] K1 [26]
with probability ½ -1.19x2-21](https://image.slidesharecdn.com/class5jf-240428053117-a04fbf59/85/class5jf-pptx-Block-cipher-in-information-security-43-320.jpg)

![45
Full Linear Attack on DES
• Linear cryptanalysis can be accomplished with ~243 known
plaintexts, using a more sophisticated estimation 14 round
approximation
– For each 48 bit last round sub-key, decrypt cipher-text
backwards across last round for all sample cipher-texts
– Increment count for all sub-keys whose linear expression holds
true to the penultimate round
– This is done for the first and last round yielding 13 key bits each
(total: 26)
• Here they are:
PR[8,14,25] CL[3,8,14,25] CR[17]=
K1[26] K3[4] K4[26] K6[26] K7[4] K8[26]
K10[26] K11[4] K12[26] K14[26]
with probability ½ -1.19x2-21
CR[8,14,25] PL[3,8,14,25] PR[17]= K13[26] K12[24] K11[26] K9[26] K8[24]
K7[26] K5[26] K4[4] K3[26] K1 [26]
with probability ½ -1.19x2-21
JLM 20110204](https://image.slidesharecdn.com/class5jf-240428053117-a04fbf59/85/class5jf-pptx-Block-cipher-in-information-security-45-320.jpg)



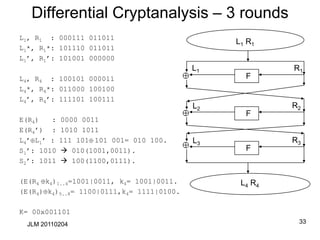
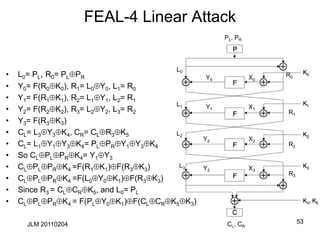
![FEAL-4 Linear Attack
• X = X[0], …, X[31]), Y=F(X). Notation: X[i,j]= X[i]X[j]
• (ab)[7] = (a+b(mod 256))[7], so
• G0(a,b)[5] = (ab)[7]
• (ab1)[7] = (a+b+1(mod 256))[7], so
• G1(a,b)[5] = (ab1)[7]
• Since y1= G1(x0x1, x2x3),
• Y[13]=y1[5]=x0[7]x1[7]x2[7]x3[7]1=X[7,15,23,31]1
• Since y0=G0(x0, y1), Y[5]=y0[5]=y1[7]x0[7] =Y[15]X[7]
• Since y2=G0(y1, x2x3),
Y[21]=y2[5]=y1[7]x2[7]x3[7] = Y[15]X[23,31]
• Since y3=G1(y2,x3),
Y[29]=y3[5]=y2[7]x3[7]1= Y[23]X[31]1
52
JLM 20110204
Y X
Y=F(X)
• Y=(y0, y1, y2, y3)
• X=(x0, x1, x2, x3)
F](https://image.slidesharecdn.com/class5jf-240428053117-a04fbf59/85/class5jf-pptx-Block-cipher-in-information-security-52-320.jpg)
![FEAL-4 Linear Attack
• We’ve show
1. CLPLPRK4 = F(PLY0K1)F(CLCRK5K3),
2. Y0= F(R0K0)=F(PLPRK0)
3. Y[13]=X[7,15,23,31]1
4. Y[5] =Y[15]X[7]
5. Y[21]=Y[15]X[23,31]
6. Y[29]Y[23] = X[31]1
• From 1,
7. (CLPLPRK4)[23,29]= F(PLY0K1)[23,29]F(CLCRK5K3)[23,29]
• From 6,
8. F(PLY0K1)[23,29]= (PLY0K1)[31]1
9. F(CLCRK5K3)[23,29]= (CLCRK5K3)[31]1
• Adding 8 and 9,
10.(CLPLPRK4)[23,29]= (PLY0K1)[31](CLCRK5K3)[31]
Slide adapted from Mark Stamp 54
JLM 20110204](https://image.slidesharecdn.com/class5jf-240428053117-a04fbf59/85/class5jf-pptx-Block-cipher-in-information-security-54-320.jpg)
![FEAL-4 Linear Attack
• From the last slide,
• (CLPLPRK4)[23,29]= (PLY0K1)[31](CLCRK5K3)[31], so
• K4[23,29](K1K5K3)[31]=
(CLPLPR)[23,29]PL[31]Y0[31](CLCR)[31]=
(CLPLPR)[23,29]PL[31](CLCR)[31] F(PLPRK0)[31]
• The left hand side is a constant for fixed key.
• The attack consists of guessing K0 and computing
h(P,C)= (CLPLPR)[23,29]PL[31](CLCR)[31]F(PLPRK0)[31]
for a number of corresponding (PL, PR), (CL, CR)
• If the guessed K0 is right, h(P,C) will have the same value for each
corresponding pair of plain-text and cipher-text.
55
JLM 20110204](https://image.slidesharecdn.com/class5jf-240428053117-a04fbf59/85/class5jf-pptx-Block-cipher-in-information-security-55-320.jpg)
![FEAL-4 Linear Attack - Improvement
• Possible to improve on linear attack
– Put K0’= ((K0)0,…,7(K0)8,…,15, (K0)16,…,23(K0)24,…,31)
– Consider reduced cipher to get a new relation
– h’(P,C)=
(CLPLPR)[5,13,21]PL[15](CLCR)[15]F(PLPRK0)[15]
– h’(P,C) depends only on bits 0,9,…,15,17,…,23 of K0
– Find these 12 bits of K0 first, then the remaining 20 can be found
using similar approximations and exhaustive search.
56
JLM 20110204](https://image.slidesharecdn.com/class5jf-240428053117-a04fbf59/85/class5jf-pptx-Block-cipher-in-information-security-56-320.jpg)