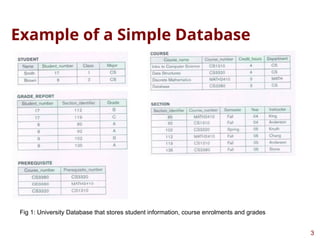
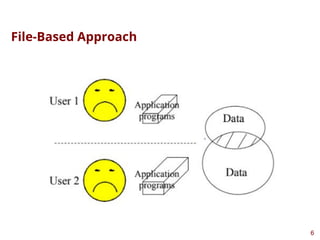
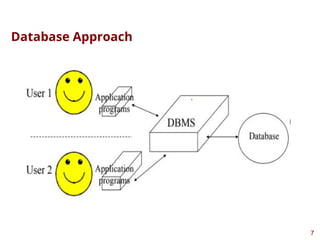
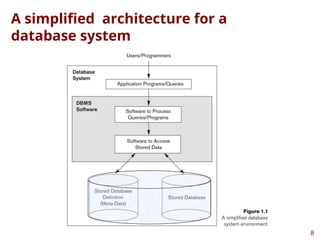
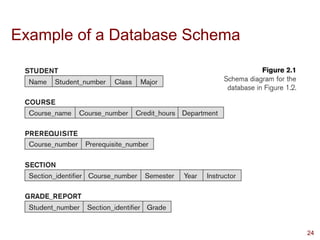
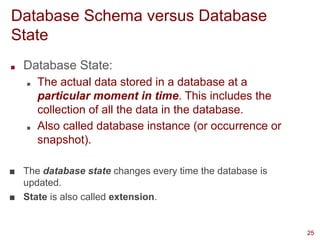
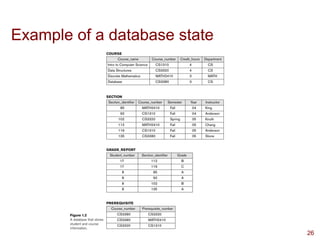
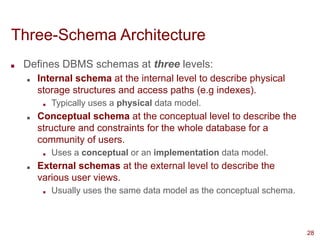
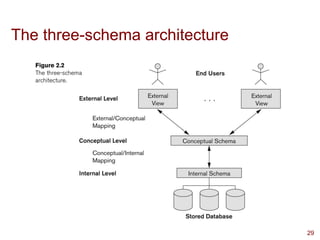
This presentation highlights on introductions and basics of Database and Database Management Systems (DBMS). Topics covered are Basic Definitions of Databases, Types of Databases and Database Applications, What a DBMS Facilitates and Other Functionalities, Main Characteristics of the Database Approach, Advantages of Using the Database Approach, Database Users, Database Users – Actors on the Scene, Database End Users, When not to use a DBMS, Data Models, Categories of Data Models, Database Schema versus Database State, Three-Schema Architecture, Data Independence, DBMS Languages, and DBMS Interfaces.