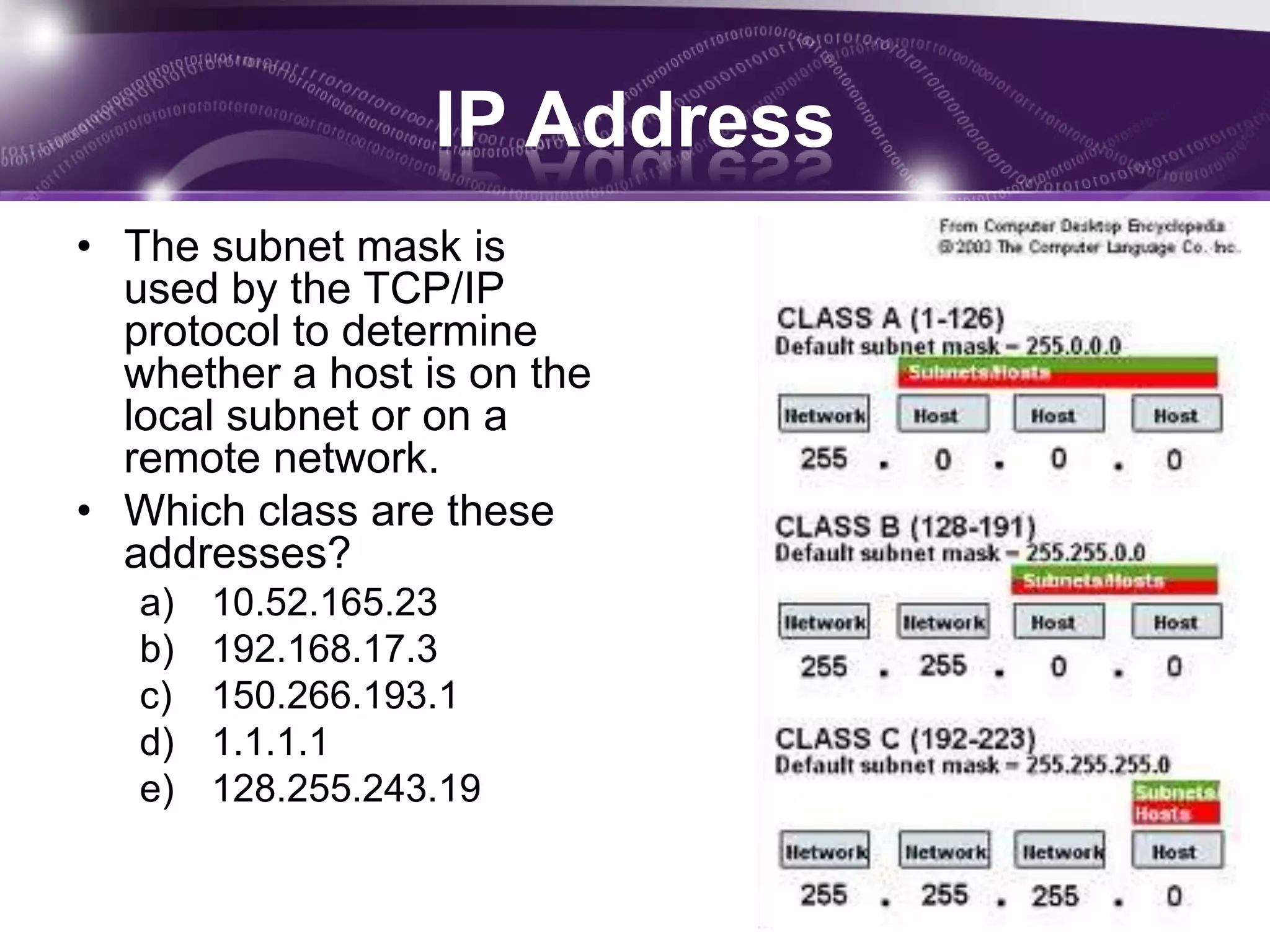
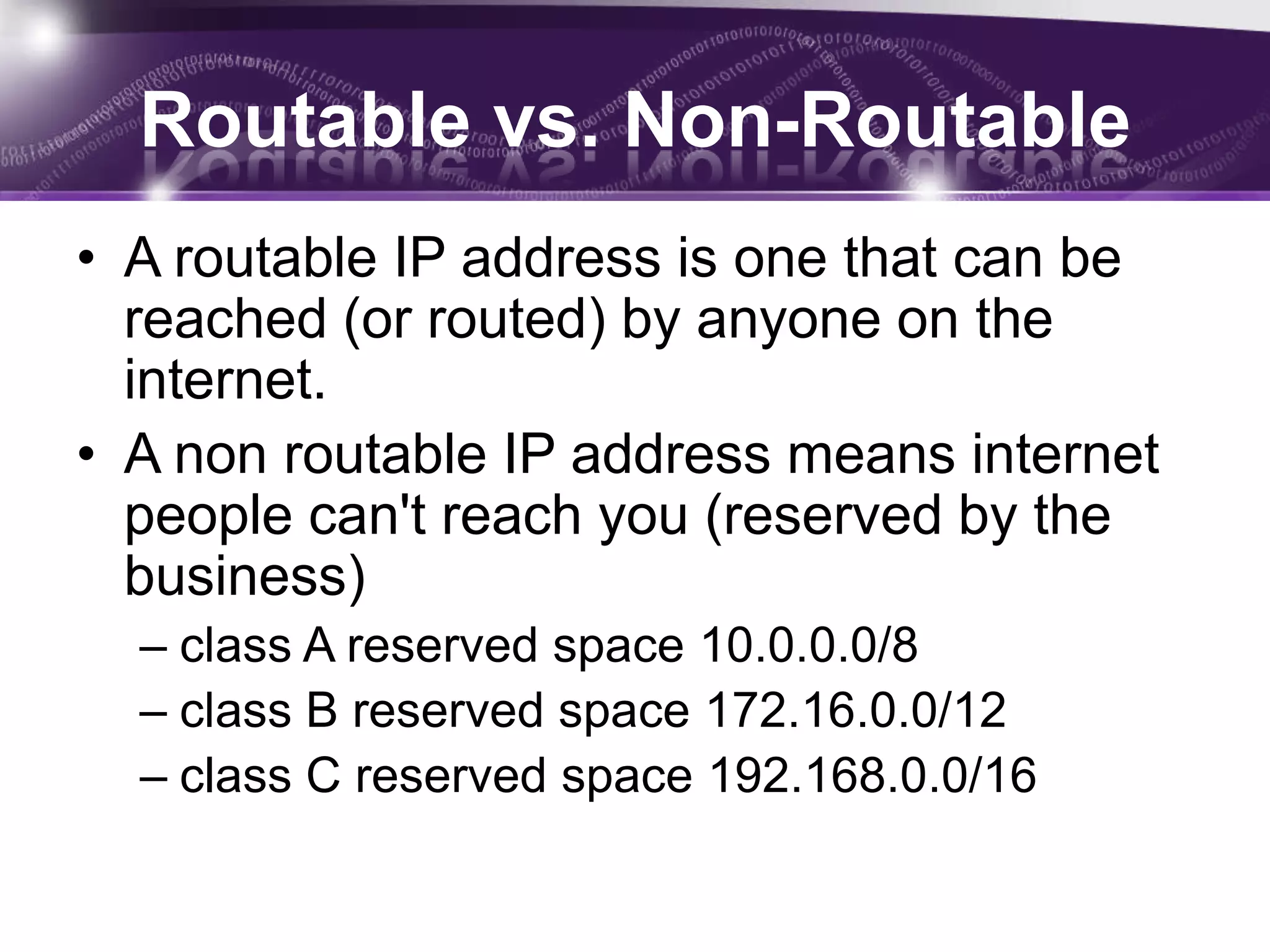
Inter-networking allows computers on different networks to communicate via gateways. Routers and bridges connect different network segments and allow communication between computers on different segments. Routers use destination IP addresses to pass data packets between networks, while bridges maintain a table of addresses to reduce traffic by only forwarding packets with valid destinations. A subnet mask is used to determine if an IP address is local or remote, and routable addresses can be reached by anyone on the internet while non-routable addresses are reserved for internal networks.