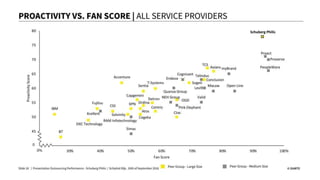
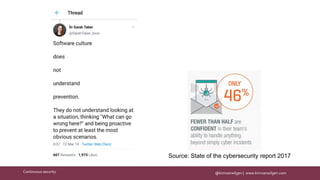
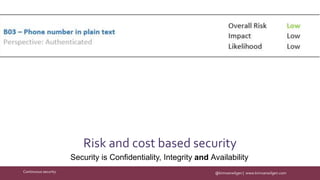
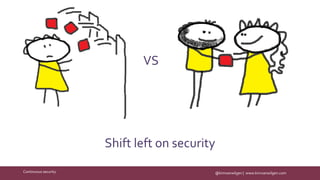
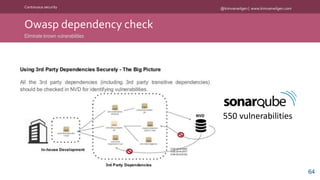
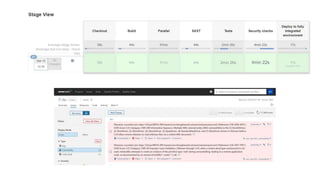
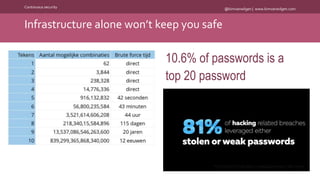
The document discusses the importance of continuous security in software development, emphasizing its integration with continuous delivery practices to enhance application integrity, availability, and confidentiality. It outlines strategies such as having security champions, risk assessment, and adopting immutable infrastructures to foster a secure DevOps environment. The need for automated security testing and a shift left approach is highlighted to ensure security becomes an integral part of the development process.