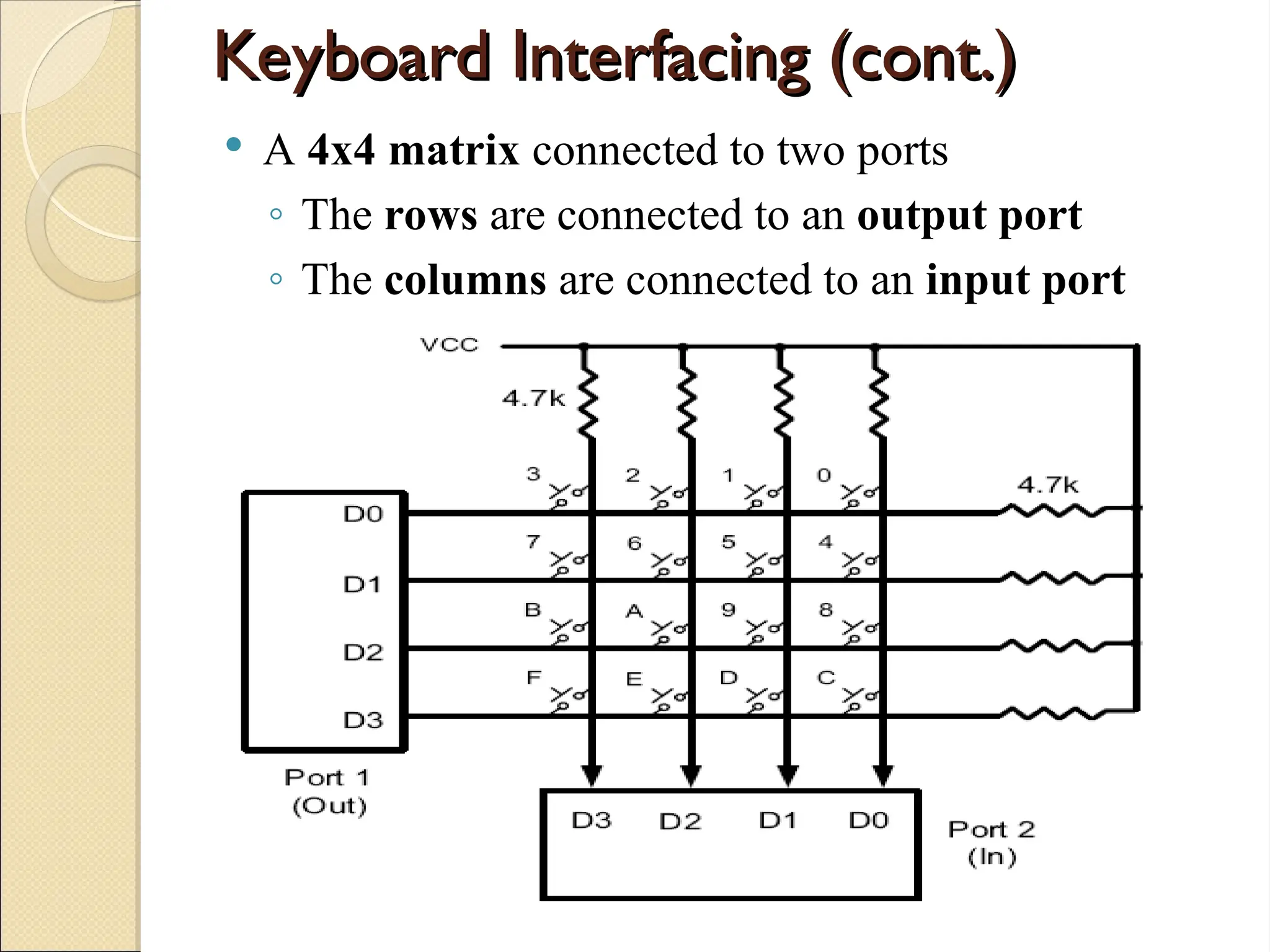
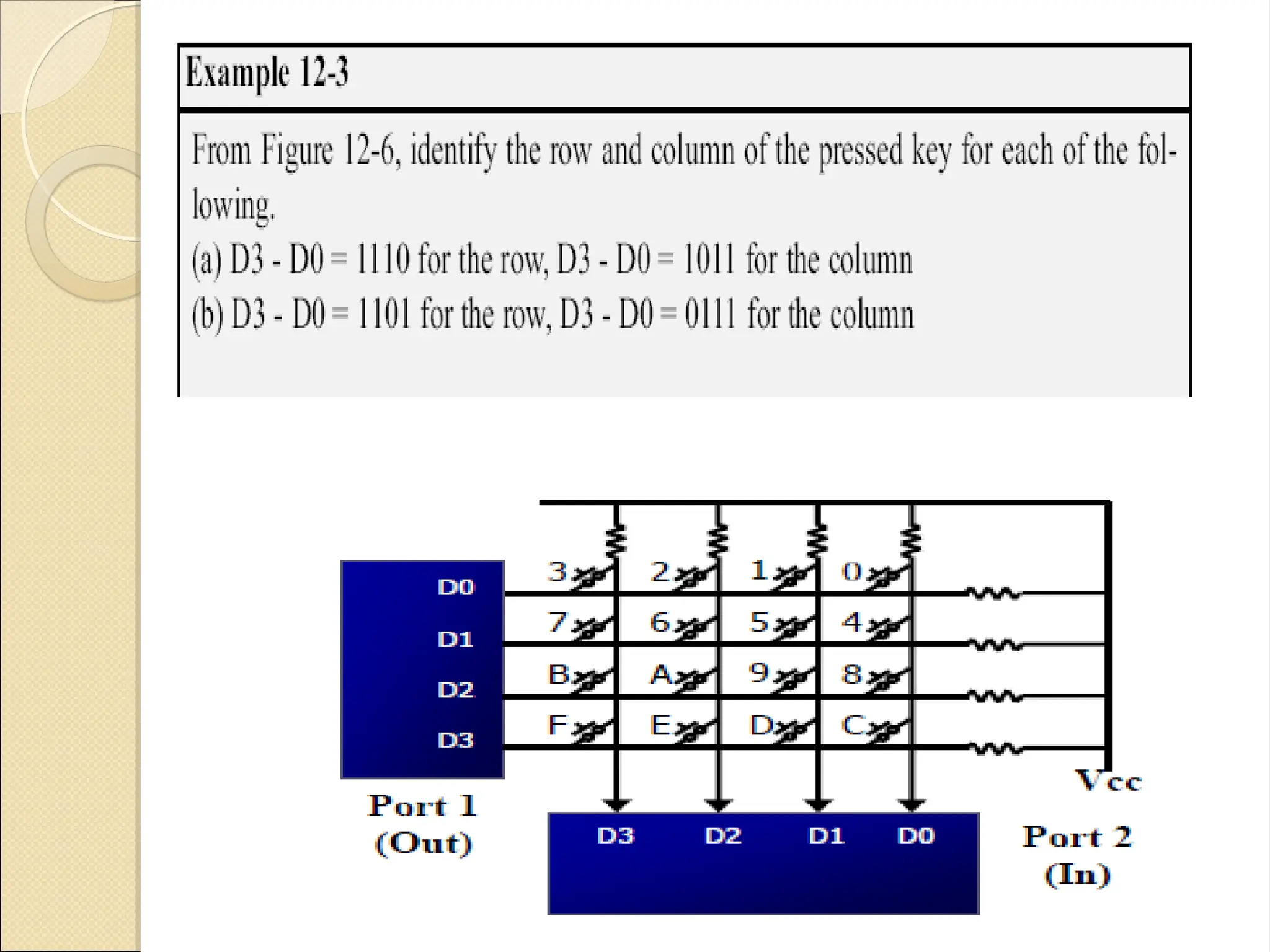
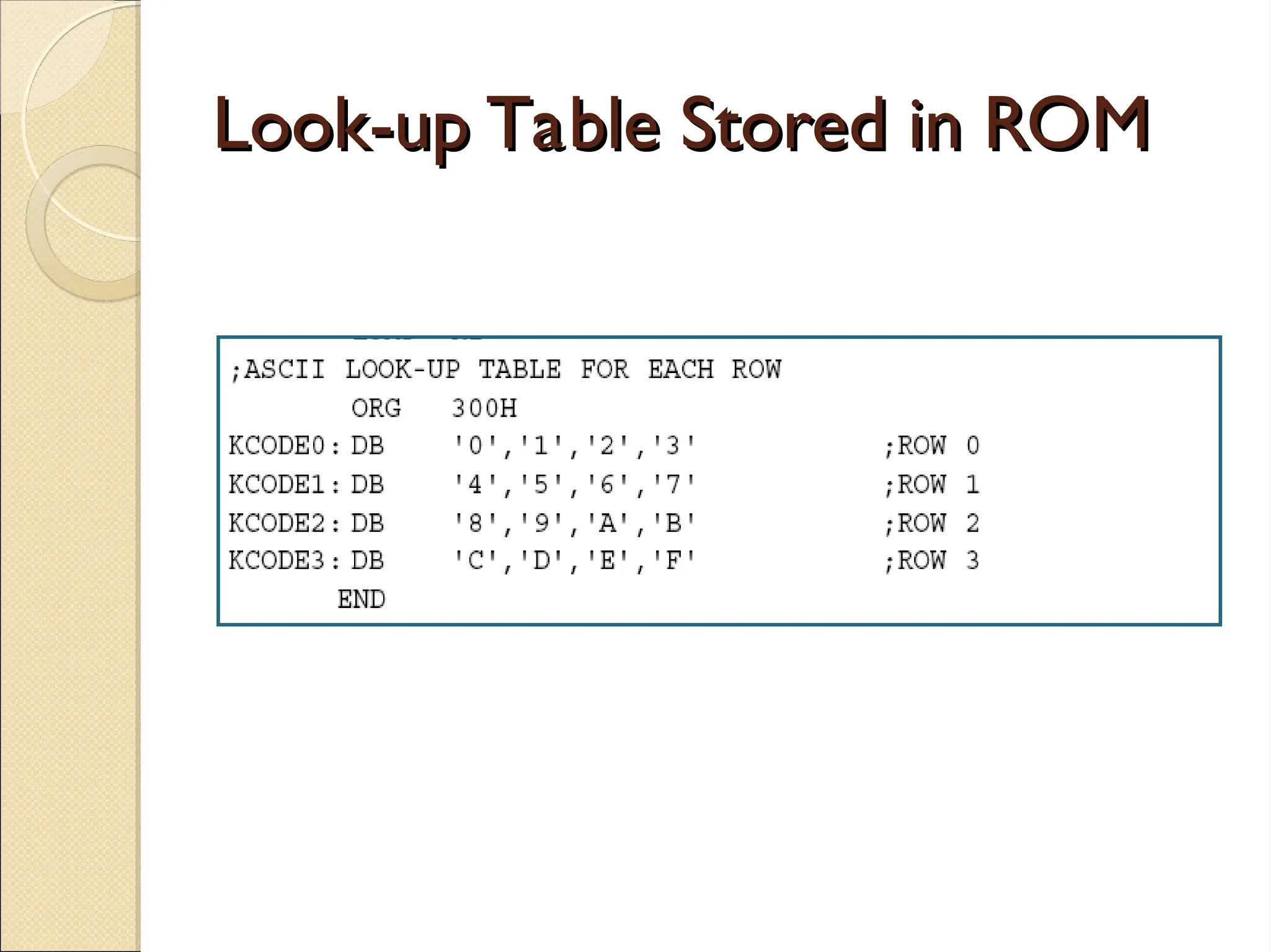
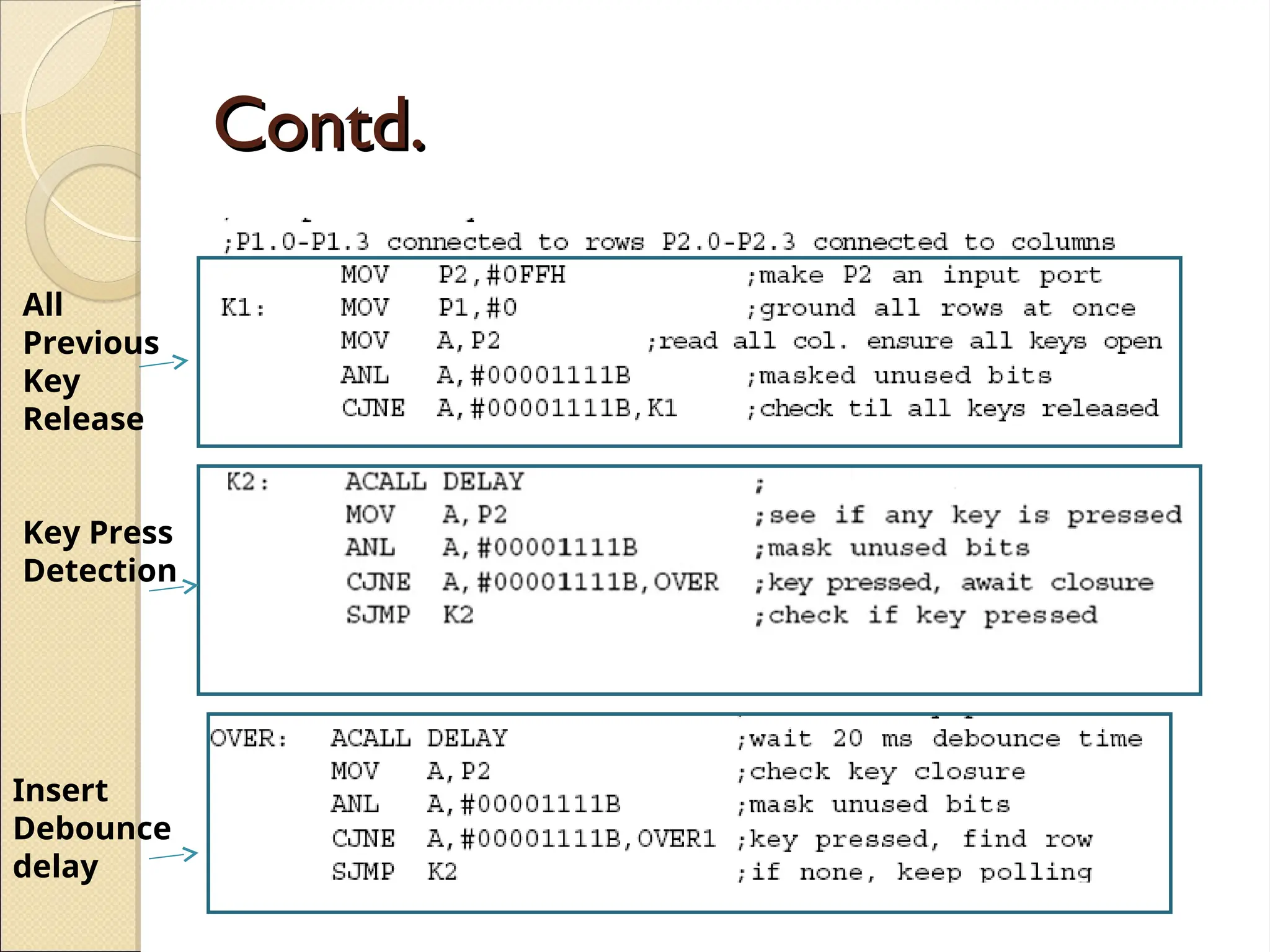
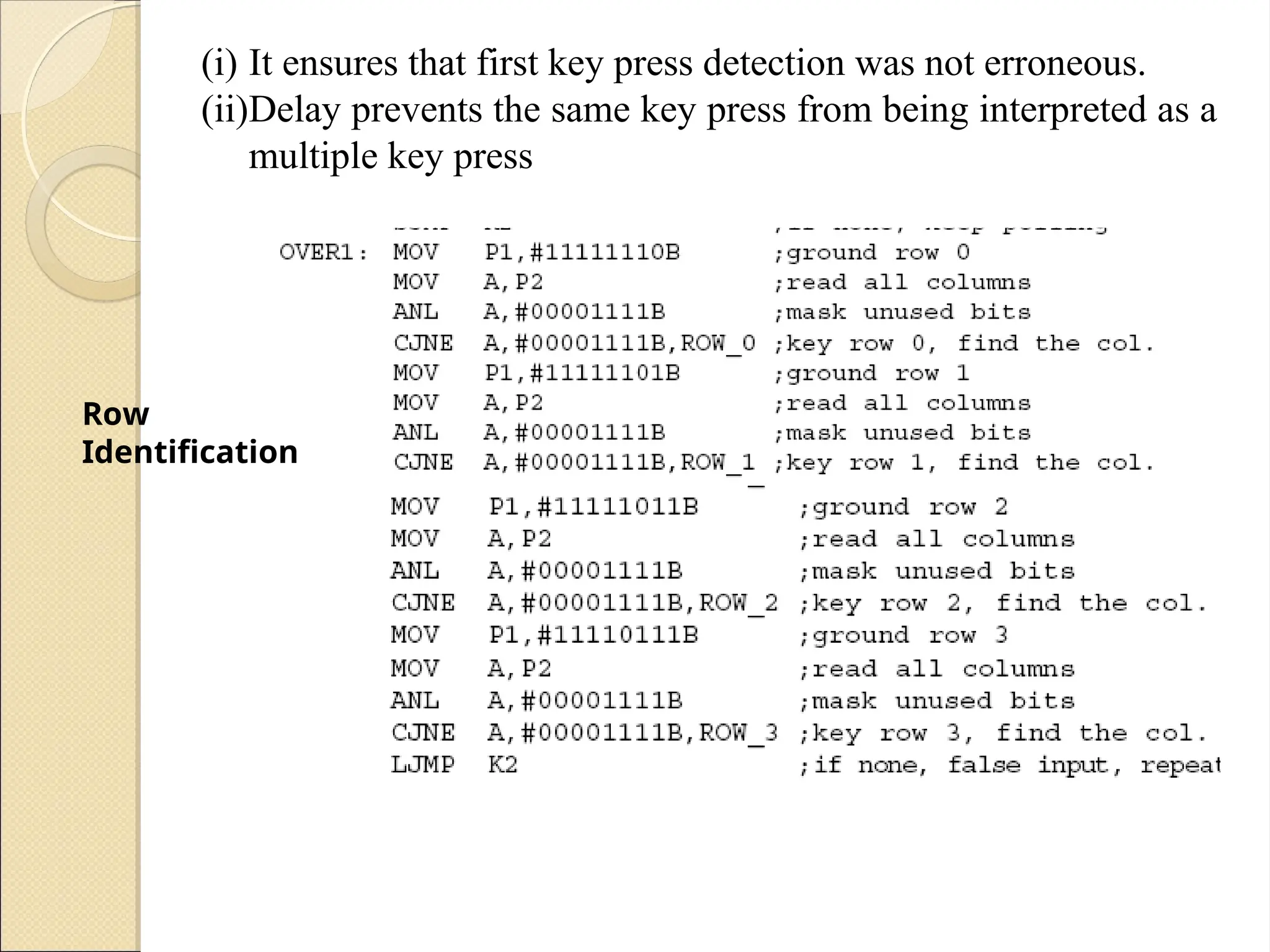
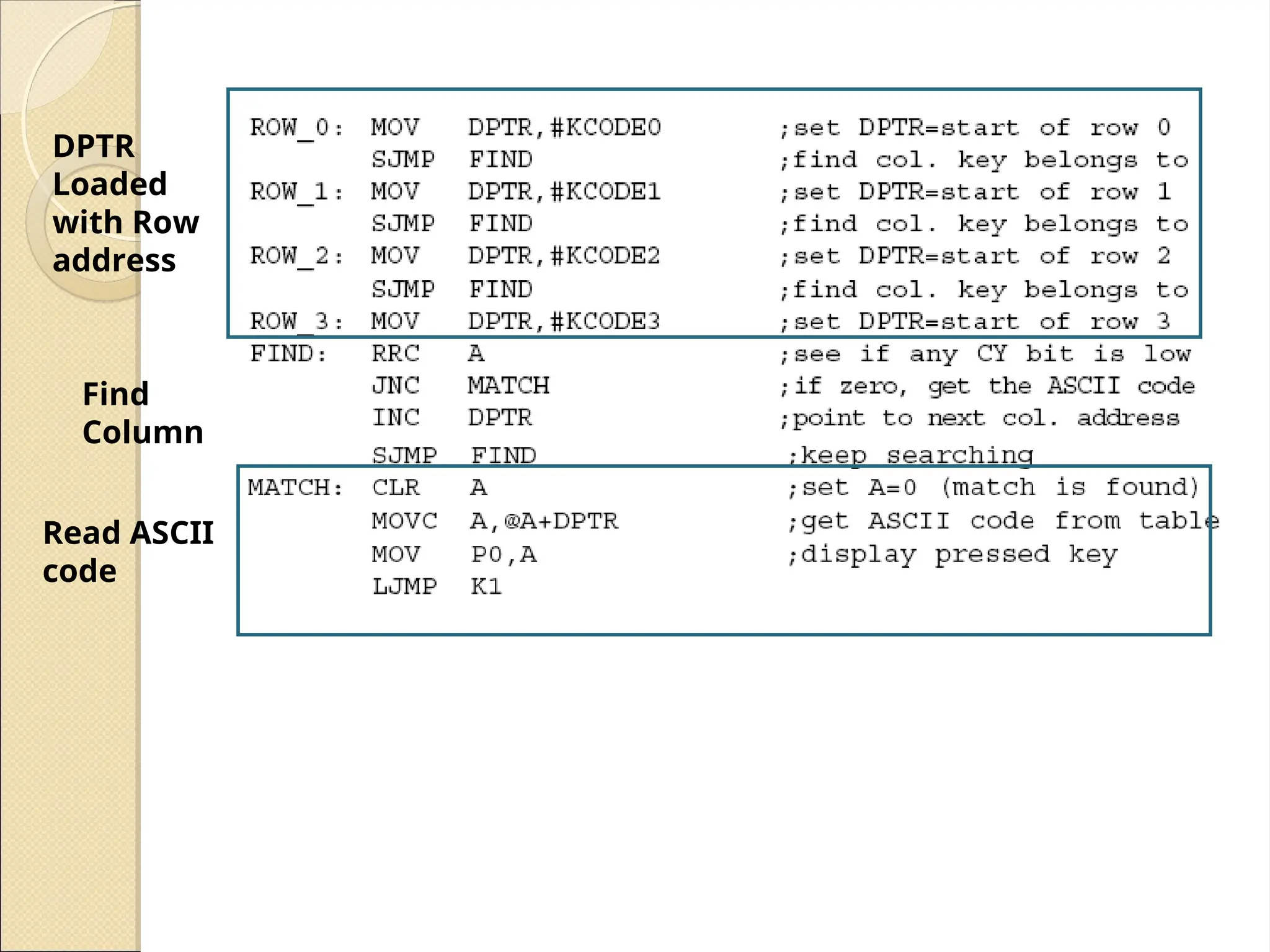
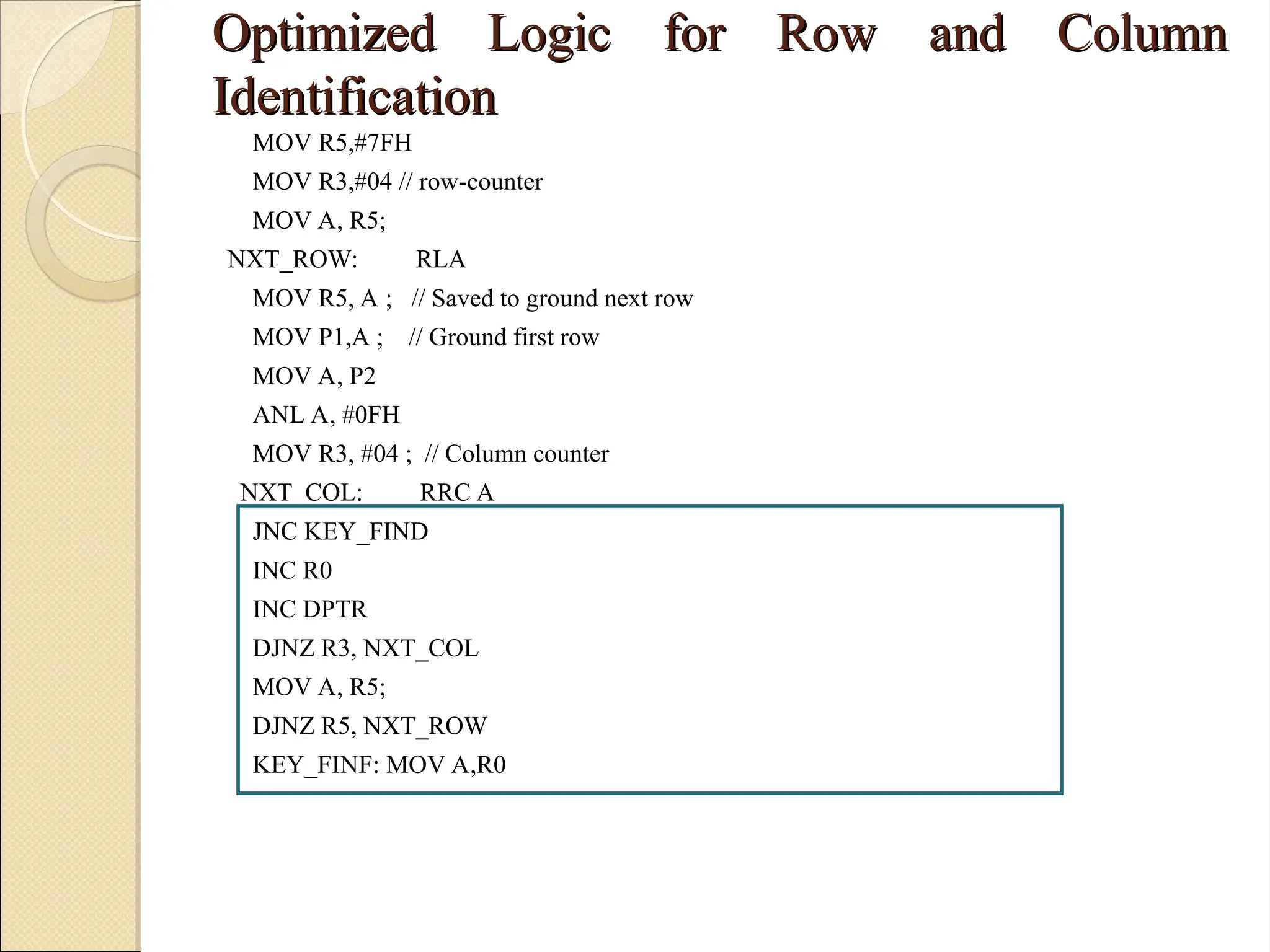
The document outlines the considerations in keyboard design, particularly focusing on key debouncing and the matrix organization of keys. It describes how a microcontroller detects and identifies key presses through a continuous scanning process and the importance of ensuring that each key press is valid. Furthermore, it details the logic for processing key inputs and managing key states, including debouncing techniques to prevent erroneous multiple key presses.