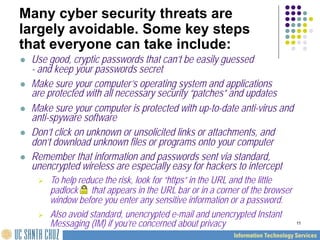
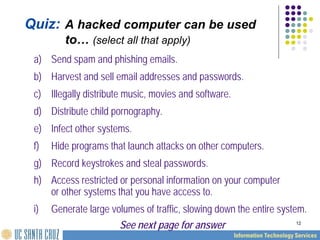
The UCSC computer security overview provides 11 self-paced training modules focused on essential security practices to protect computing systems and data. It emphasizes that 90% of security safeguards rely on user adherence to good computing practices, with training covering topics such as password security, internet privacy, and handling sensitive information. The course is aimed at equipping users with knowledge and practices to mitigate cybersecurity threats and emphasizes the shared responsibility of all community members in maintaining security.