Juniper vSRX - Fast Performance, Low TCO
•
12 likes•8,925 views
A quick look at how the industry's fastest virtual firewall also sports the lowest Total Cost of Ownership (TCO) to better support today's businesses.
Report
Share
Report
Share
Download to read offline
Recommended
More Related Content
What's hot
What's hot (20)
VMworld 2014: Virtualize your Network with VMware NSX

VMworld 2014: Virtualize your Network with VMware NSX
VMworld 2013: VMware NSX Extensibility: Network and Security Services from 3r...

VMworld 2013: VMware NSX Extensibility: Network and Security Services from 3r...
Security Practitioners guide to Micro Segmentation with VMware NSX and Log In...

Security Practitioners guide to Micro Segmentation with VMware NSX and Log In...
The Vision for the Future of Network Virtualization with VMware NSX (Q2 2016)

The Vision for the Future of Network Virtualization with VMware NSX (Q2 2016)
Deploying HPC Cluster with Mellanox InfiniBand Interconnect Solutions 

Deploying HPC Cluster with Mellanox InfiniBand Interconnect Solutions
Close your security gaps and get 100% of your traffic protected with Cloudflare

Close your security gaps and get 100% of your traffic protected with Cloudflare
Introducing Ensemble Simulator – ADVA’s virtual networking environment

Introducing Ensemble Simulator – ADVA’s virtual networking environment
[Cisco Connect 2018 - Vietnam] Rajinder singh cisco sd-wan-next generation ...![[Cisco Connect 2018 - Vietnam] Rajinder singh cisco sd-wan-next generation ...](data:image/gif;base64,R0lGODlhAQABAIAAAAAAAP///yH5BAEAAAAALAAAAAABAAEAAAIBRAA7)
![[Cisco Connect 2018 - Vietnam] Rajinder singh cisco sd-wan-next generation ...](data:image/gif;base64,R0lGODlhAQABAIAAAAAAAP///yH5BAEAAAAALAAAAAABAAEAAAIBRAA7)
[Cisco Connect 2018 - Vietnam] Rajinder singh cisco sd-wan-next generation ...
SYN 208: Power HDX 3D Applications with Intel and NVIDIA GPUs. 

SYN 208: Power HDX 3D Applications with Intel and NVIDIA GPUs.
Viewers also liked
PHP on Windows Training Program - New Horizons Computer Learning Center Singa...

PHP on Windows Training Program - New Horizons Computer Learning Center Singa...Enterprise PHP Center
Viewers also liked (20)
NYC* 2013 — "Using Cassandra for DVR Scheduling at Comcast"

NYC* 2013 — "Using Cassandra for DVR Scheduling at Comcast"
Arrow are No.1 Juniper Networks Authorised Education Partner

Arrow are No.1 Juniper Networks Authorised Education Partner
10 characteristics of a successful competitive Citrix Service Provider

10 characteristics of a successful competitive Citrix Service Provider
How to Deliver Maximum Citrix Performance and User Satisfaction

How to Deliver Maximum Citrix Performance and User Satisfaction
PHP on Windows Training Program - New Horizons Computer Learning Center Singa...

PHP on Windows Training Program - New Horizons Computer Learning Center Singa...
Similar to Juniper vSRX - Fast Performance, Low TCO
Similar to Juniper vSRX - Fast Performance, Low TCO (20)
Cisco Firepower Next-Generation Firewall (NGFW).pdf

Cisco Firepower Next-Generation Firewall (NGFW).pdf
WBA (Wireless Broadband Access) Ruckus Wireless - FORENSE

WBA (Wireless Broadband Access) Ruckus Wireless - FORENSE
35 9142 it s-execution evaluation of end-to-end edit septian

35 9142 it s-execution evaluation of end-to-end edit septian
Best Data Center Service Provider in India - Best Hybrid Cloud Hosting Servi...

Best Data Center Service Provider in India - Best Hybrid Cloud Hosting Servi...
Supermicro AI Pod that’s Super Simple, Super Scalable, and Super Affordable

Supermicro AI Pod that’s Super Simple, Super Scalable, and Super Affordable
Virtual security gateways at network edge are key to protecting ultra broadba...

Virtual security gateways at network edge are key to protecting ultra broadba...
More from Juniper Networks
More from Juniper Networks (20)
Real AI. Real Results. Mist AI Customer Testimonials.

Real AI. Real Results. Mist AI Customer Testimonials.
Are you able to deliver reliable experiences for connected devices

Are you able to deliver reliable experiences for connected devices
Securing IoT at Scale Requires a Holistic Approach

Securing IoT at Scale Requires a Holistic Approach
Smart Solutions for Smart Communities: What's Next & Who's Responsible?

Smart Solutions for Smart Communities: What's Next & Who's Responsible?
SDN and NFV: Transforming the Service Provider Organization

SDN and NFV: Transforming the Service Provider Organization
Navigating the Uncertain World Facing Service Providers - Juniper's Perspective

Navigating the Uncertain World Facing Service Providers - Juniper's Perspective
High performance data center computing using manageable distributed computing

High performance data center computing using manageable distributed computing
What Are Virtual Chassis and Virtual Chassis Fabric?

What Are Virtual Chassis and Virtual Chassis Fabric?
MetaFabric Architectures 1.0 - Virtualized IT Data Center

MetaFabric Architectures 1.0 - Virtualized IT Data Center
Recently uploaded
Making_way_through_DLL_hollowing_inspite_of_CFG_by_Debjeet Banerjee.pptx

Making_way_through_DLL_hollowing_inspite_of_CFG_by_Debjeet Banerjee.pptxnull - The Open Security Community
Recently uploaded (20)
Hyderabad Call Girls Khairatabad ✨ 7001305949 ✨ Cheap Price Your Budget

Hyderabad Call Girls Khairatabad ✨ 7001305949 ✨ Cheap Price Your Budget
IAC 2024 - IA Fast Track to Search Focused AI Solutions

IAC 2024 - IA Fast Track to Search Focused AI Solutions
Beyond Boundaries: Leveraging No-Code Solutions for Industry Innovation

Beyond Boundaries: Leveraging No-Code Solutions for Industry Innovation
Next-generation AAM aircraft unveiled by Supernal, S-A2

Next-generation AAM aircraft unveiled by Supernal, S-A2
Making_way_through_DLL_hollowing_inspite_of_CFG_by_Debjeet Banerjee.pptx

Making_way_through_DLL_hollowing_inspite_of_CFG_by_Debjeet Banerjee.pptx
SQL Database Design For Developers at php[tek] 2024![SQL Database Design For Developers at php[tek] 2024](data:image/gif;base64,R0lGODlhAQABAIAAAAAAAP///yH5BAEAAAAALAAAAAABAAEAAAIBRAA7)
![SQL Database Design For Developers at php[tek] 2024](data:image/gif;base64,R0lGODlhAQABAIAAAAAAAP///yH5BAEAAAAALAAAAAABAAEAAAIBRAA7)
SQL Database Design For Developers at php[tek] 2024
08448380779 Call Girls In Friends Colony Women Seeking Men

08448380779 Call Girls In Friends Colony Women Seeking Men
08448380779 Call Girls In Civil Lines Women Seeking Men

08448380779 Call Girls In Civil Lines Women Seeking Men
Azure Monitor & Application Insight to monitor Infrastructure & Application

Azure Monitor & Application Insight to monitor Infrastructure & Application
08448380779 Call Girls In Diplomatic Enclave Women Seeking Men

08448380779 Call Girls In Diplomatic Enclave Women Seeking Men
Presentation on how to chat with PDF using ChatGPT code interpreter

Presentation on how to chat with PDF using ChatGPT code interpreter
The Codex of Business Writing Software for Real-World Solutions 2.pptx

The Codex of Business Writing Software for Real-World Solutions 2.pptx
Tech-Forward - Achieving Business Readiness For Copilot in Microsoft 365

Tech-Forward - Achieving Business Readiness For Copilot in Microsoft 365
Transforming Data Streams with Kafka Connect: An Introduction to Single Messa...

Transforming Data Streams with Kafka Connect: An Introduction to Single Messa...
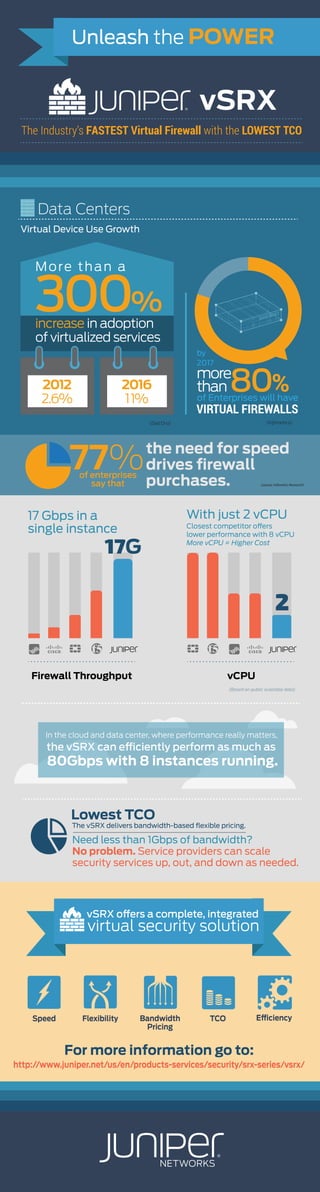
Juniper vSRX - Fast Performance, Low TCO
- 1. (source: Infonetics Research) the need for speed drives firewall purchases. of enterprises say that 77% Unleash the POWER vSRX The Industry’s FASTEST Virtual Firewall with the LOWEST TCO Data Centers more than 80%of Enterprises will have by 2017 VIRTUAL FIREWALLS (Dell’Oro) (Infonetics) Flexibility TCO In the cloud and data center, where performance really matters, the vSRX can efficiently perform as much as 80Gbps with 8 instances running. Firewall Throughput vCPU 17G 2 vSRX offers a complete, integrated virtual security solution Lowest TCO The vSRX delivers bandwidth-based flexible pricing. Bandwidth Pricing (Based on public available data) Need less than 1Gbps of bandwidth? No problem. Service providers can scale security services up, out, and down as needed. Virtual Device Use Growth For more information go to: http://www.juniper.net/us/en/products-services/security/srx-series/vsrx/ Speed 17 Gbps in a single instance With just 2 vCPU Closest competitor offers lower performance with 8 vCPU More vCPU = Higher Cost More than a 300% increase in adoption of virtualized services 2012 2.6% 2016 11%
