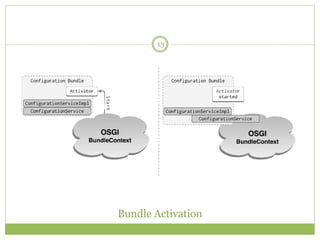
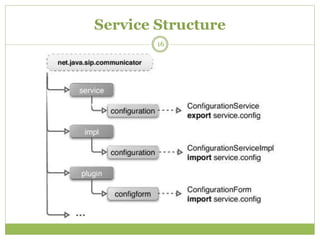
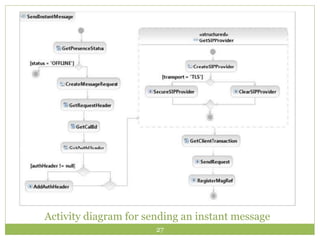
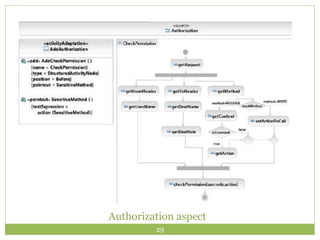
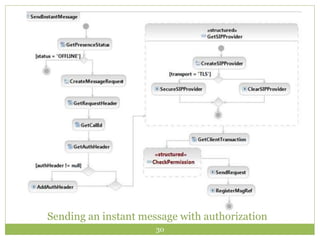
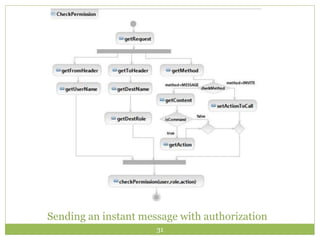
Jitsi is a free and open-source multiplatform application that provides voice, video calling, and instant messaging capabilities across Windows, Linux, Mac OS X and Android devices. It uses protocols like SIP, XMPP and OSCAR to support communications and supports features like direct media connections, file transfers, and both voice and video calls. Jitsi has a modular architecture that uses the OSGi framework and separates functionality into services and protocol implementations to provide flexibility and cross-platform compatibility. It implements various security measures like encrypted chat, call encryption with SRTP and ZRTP, and authorization controls to manage communication between authorized clients.