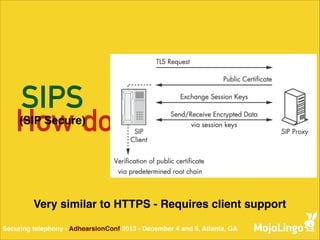
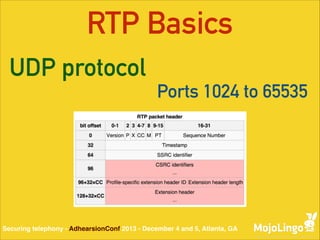
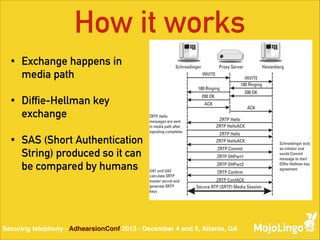
The document discusses the vulnerabilities of Voice over IP (VoIP) and Session Initiation Protocol (SIP), highlighting issues such as weak authentication and susceptibility to man-in-the-middle attacks. It introduces various methods to secure telephony communications, including Secure RTP (SRTP) and ZRTP, which enhance security by utilizing cryptographic techniques. Additionally, the document emphasizes the importance of secure key negotiation and lists software support for implementing these technologies.