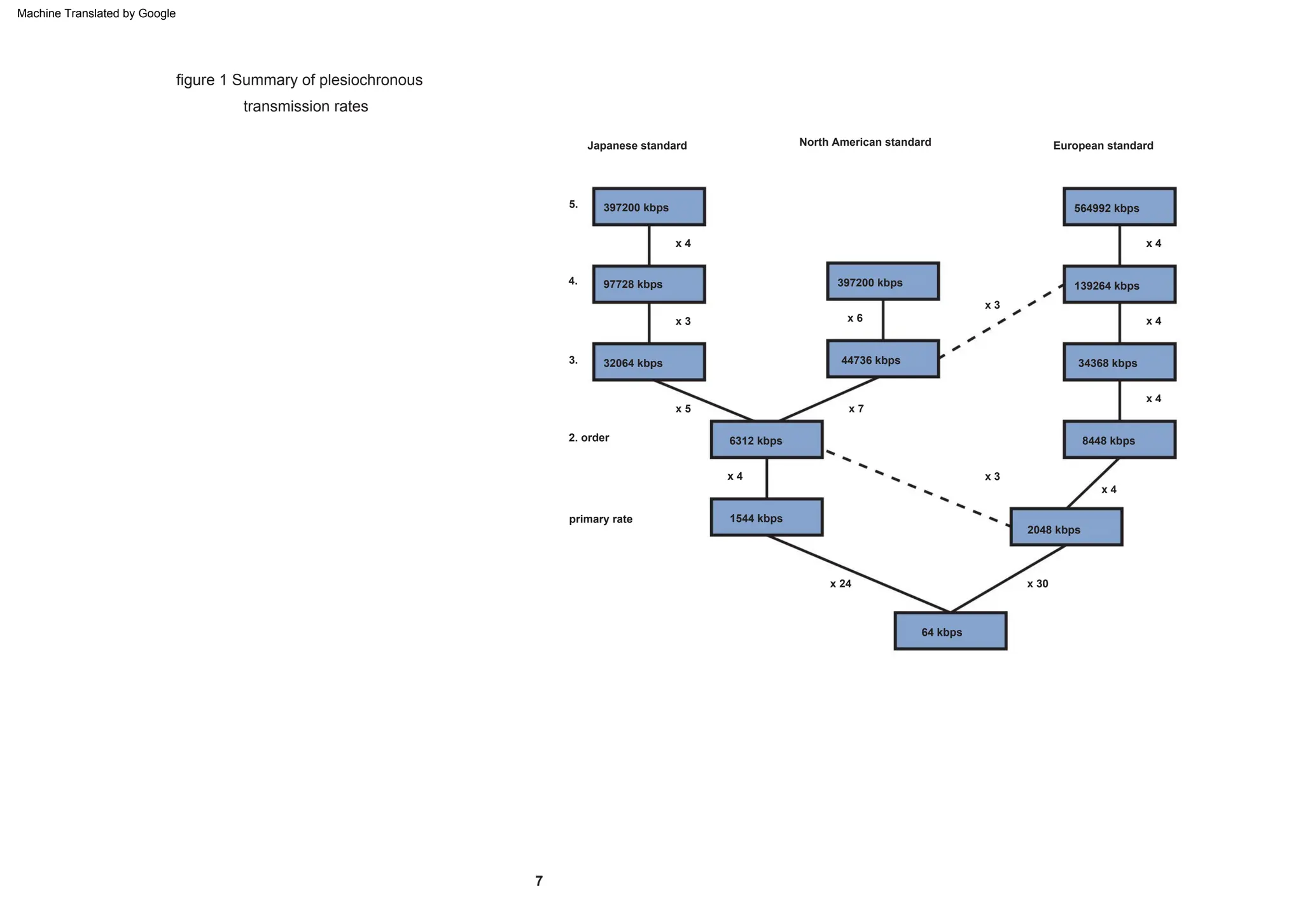
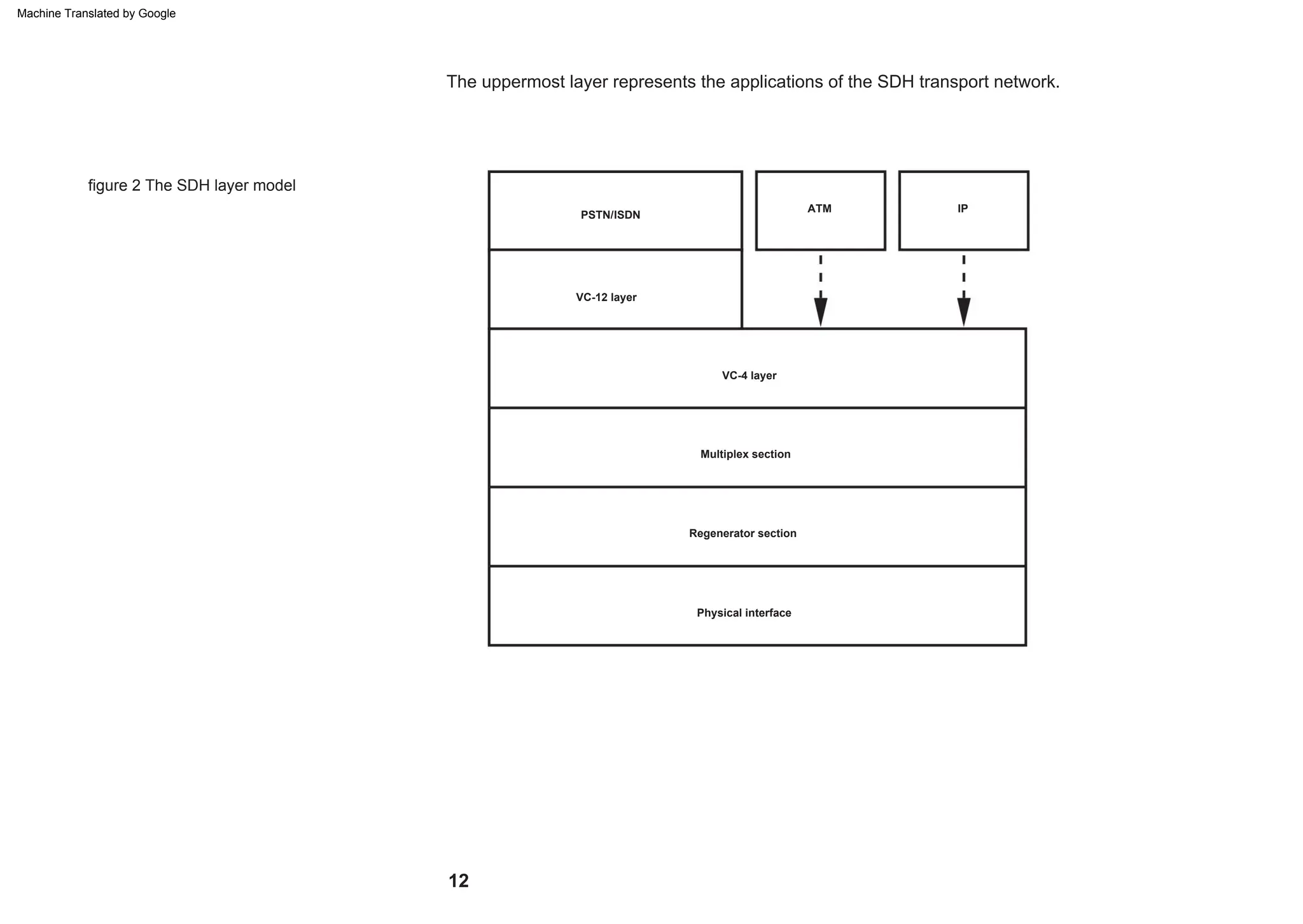
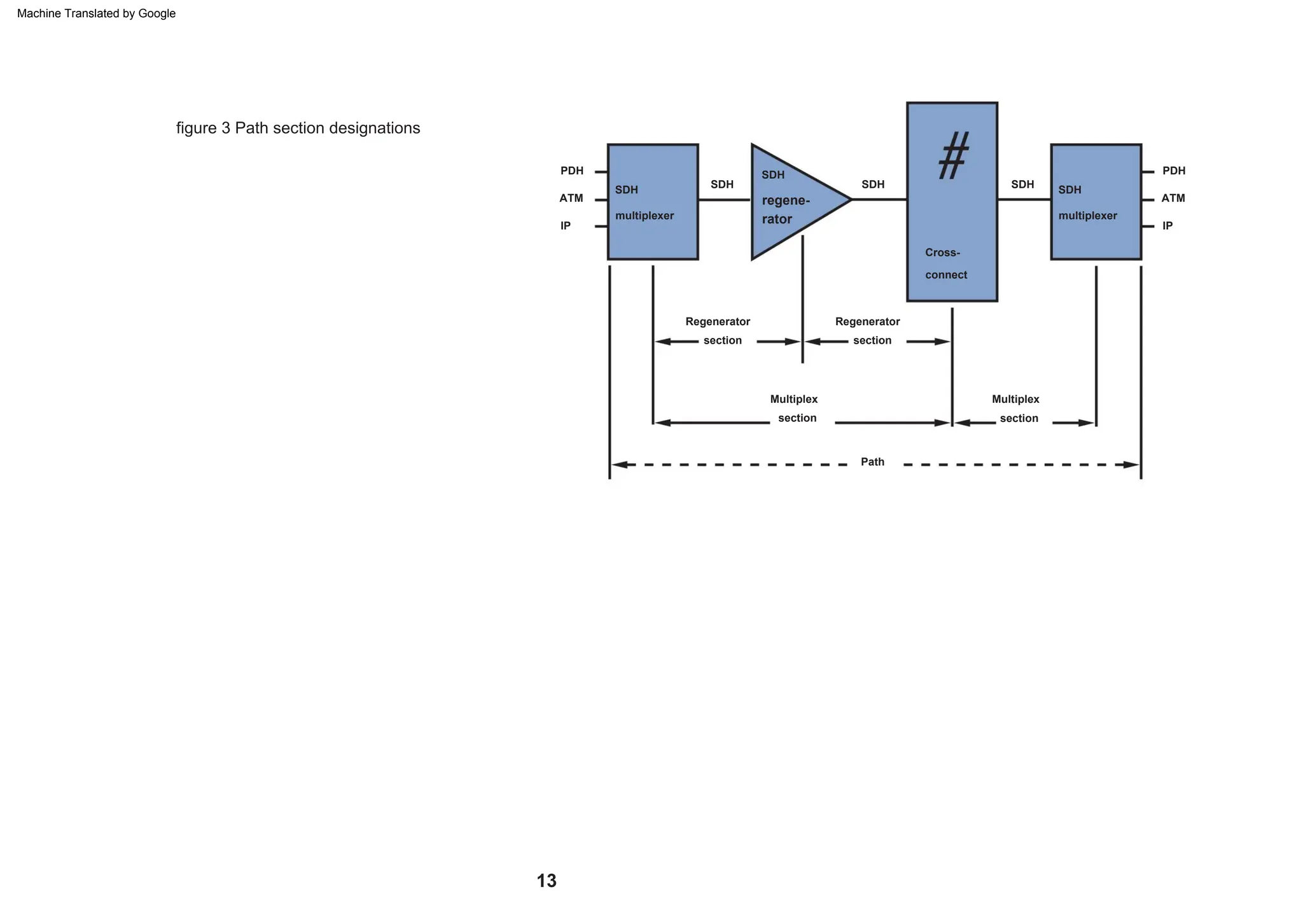
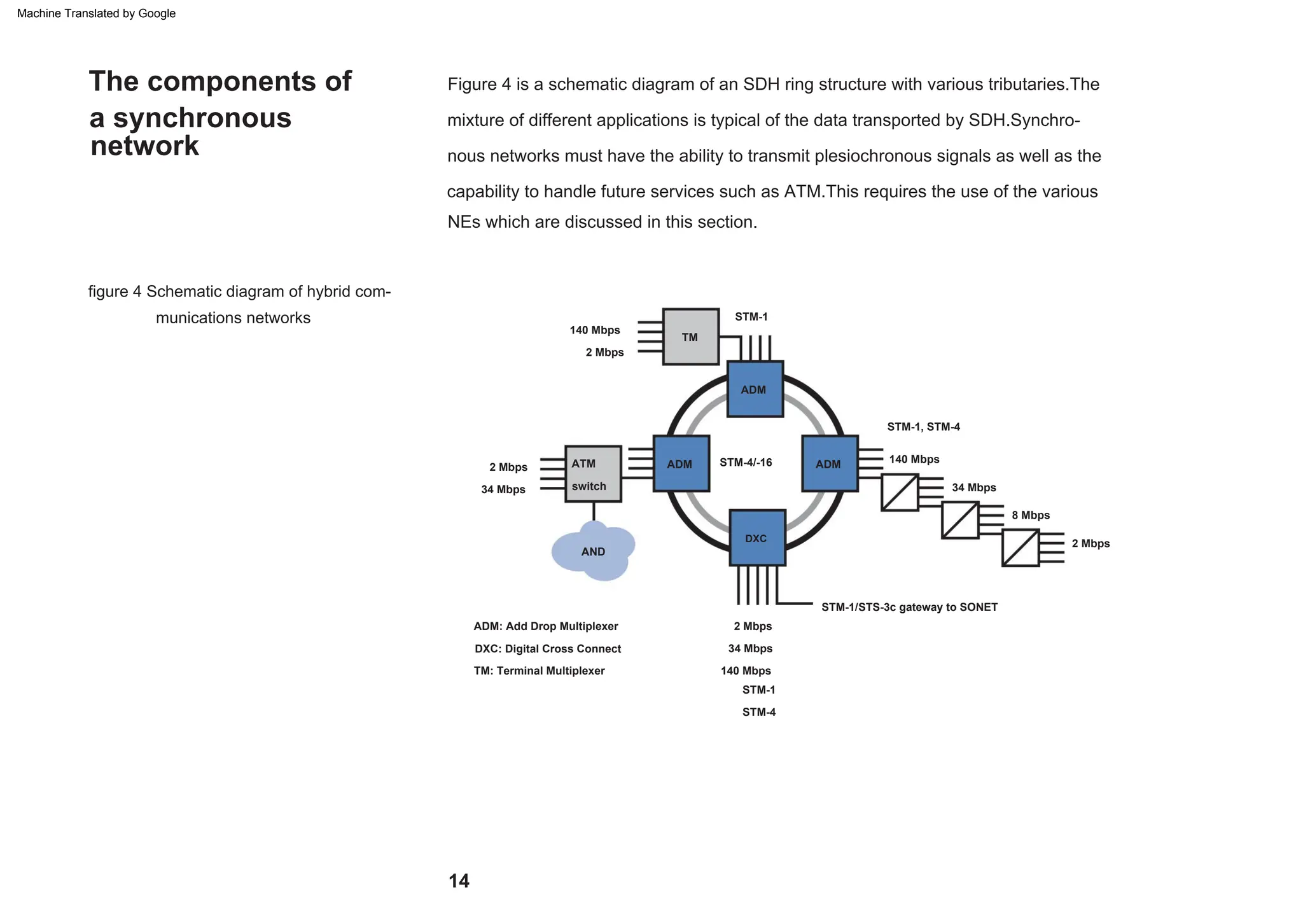
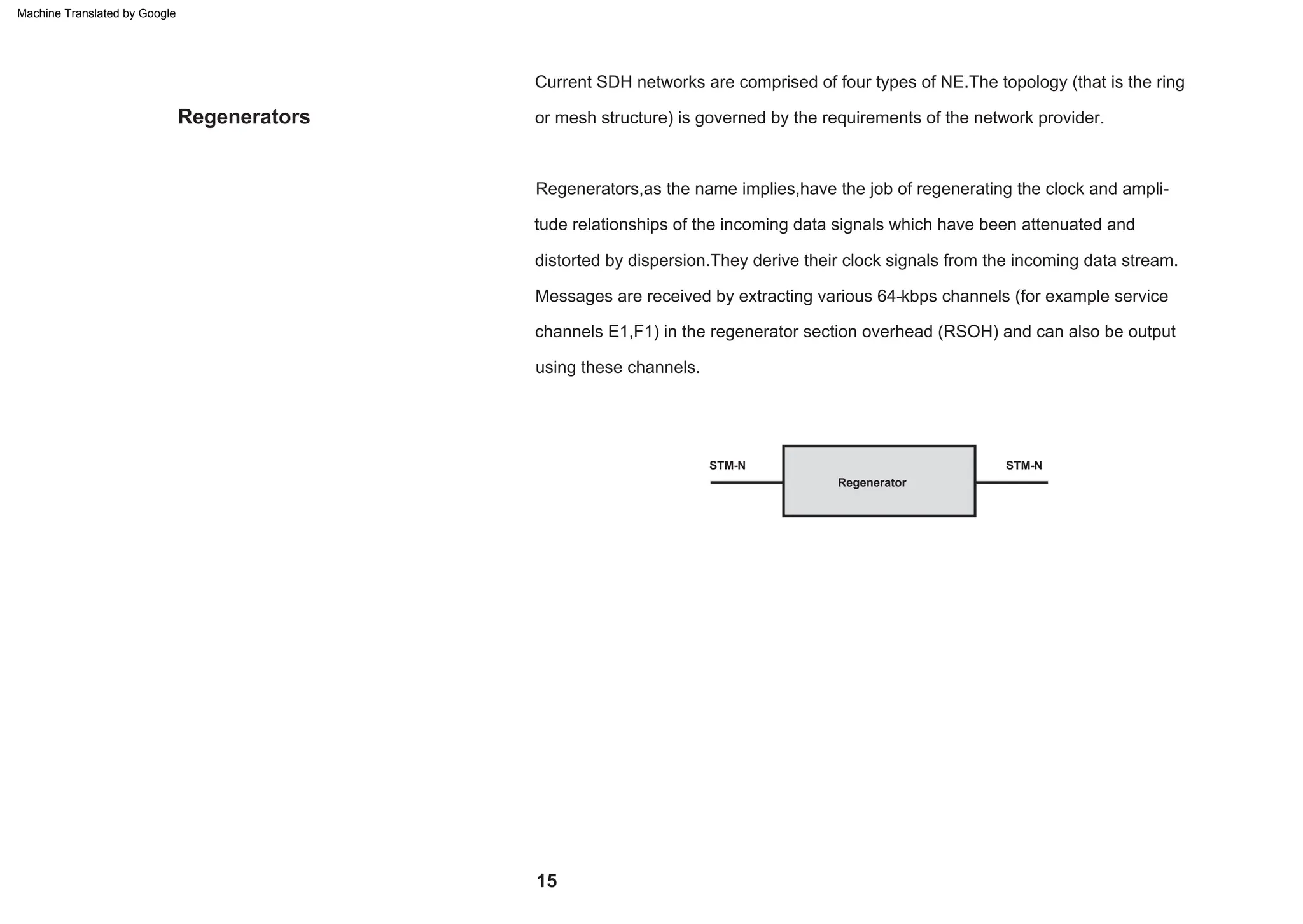
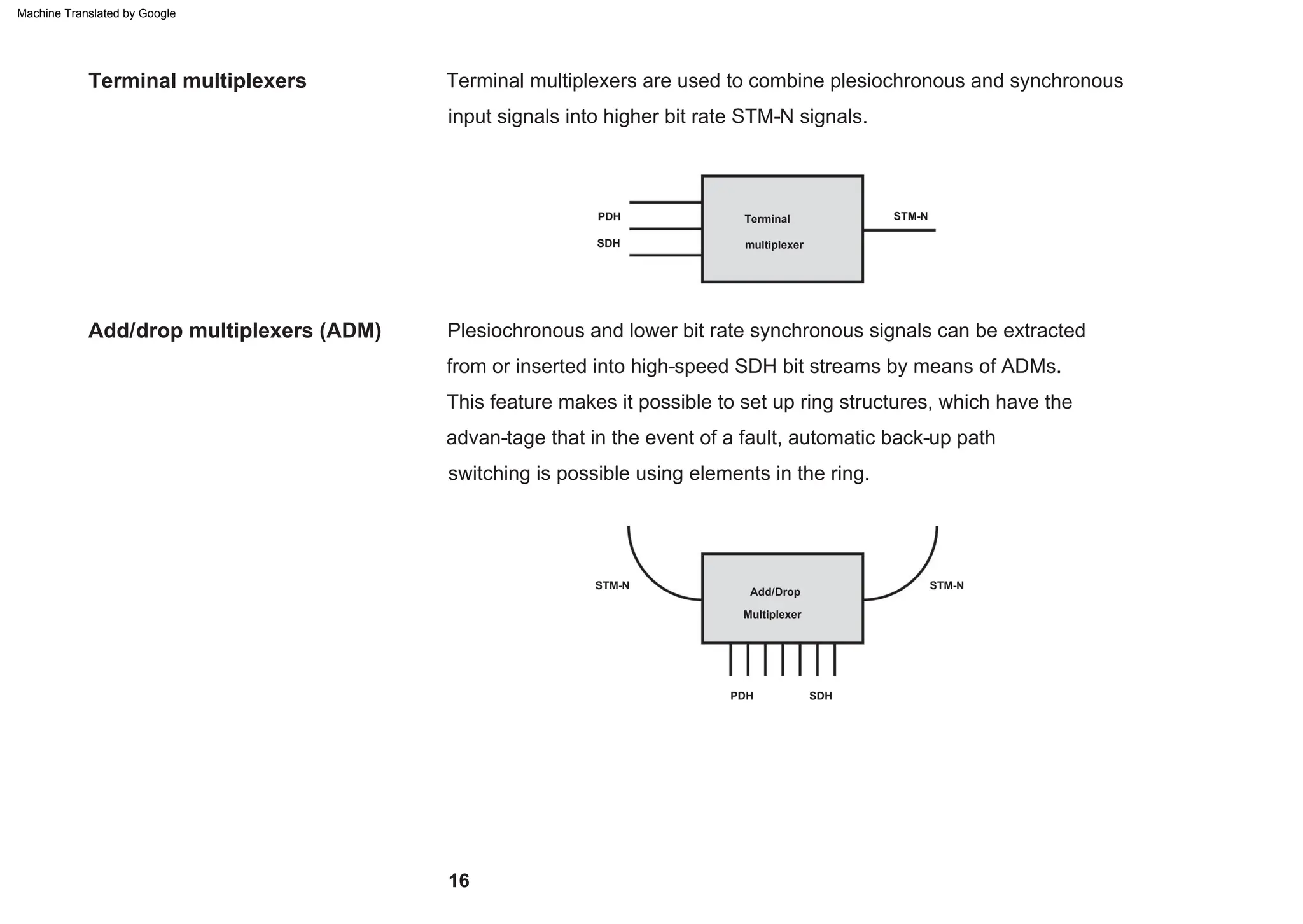
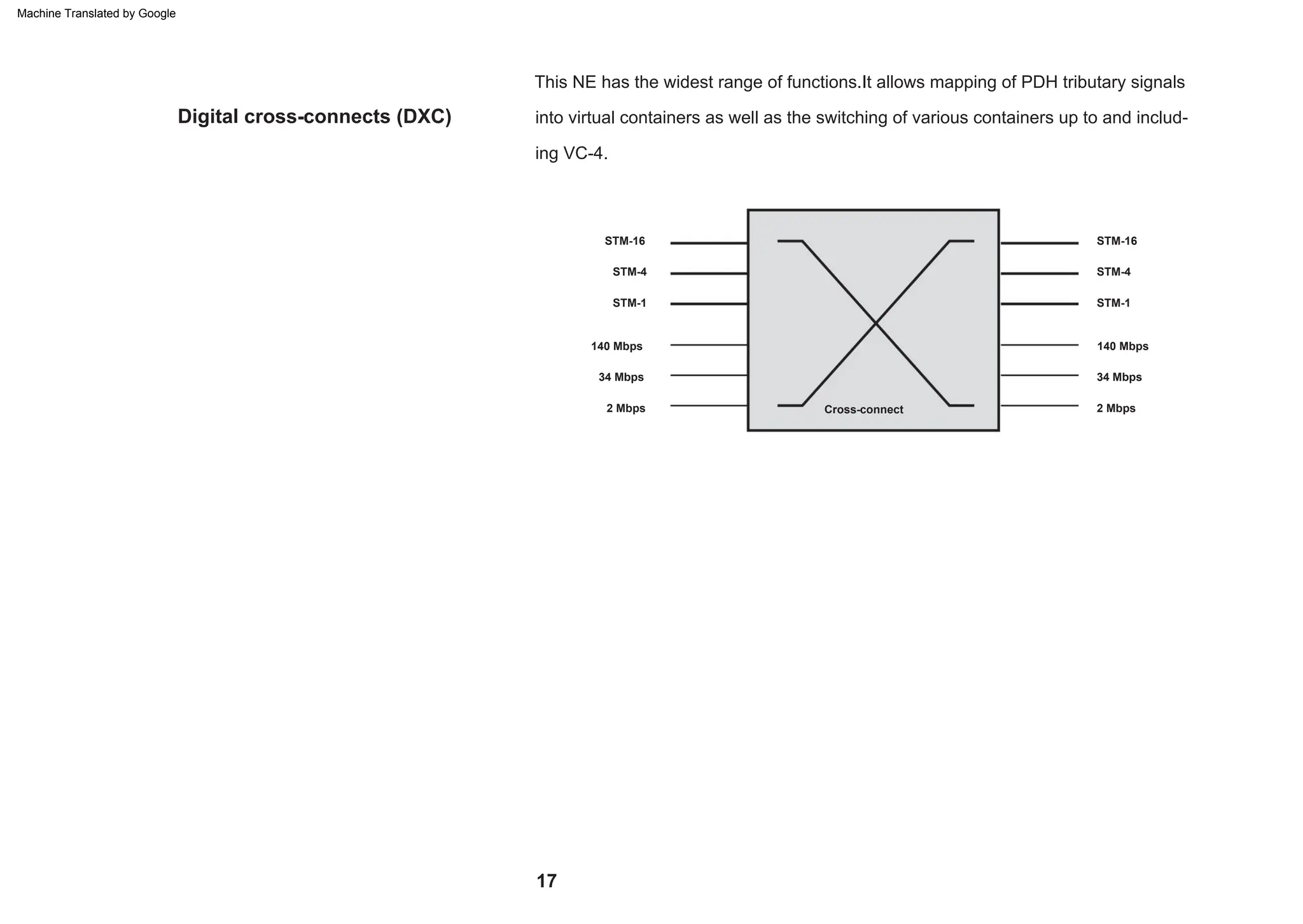
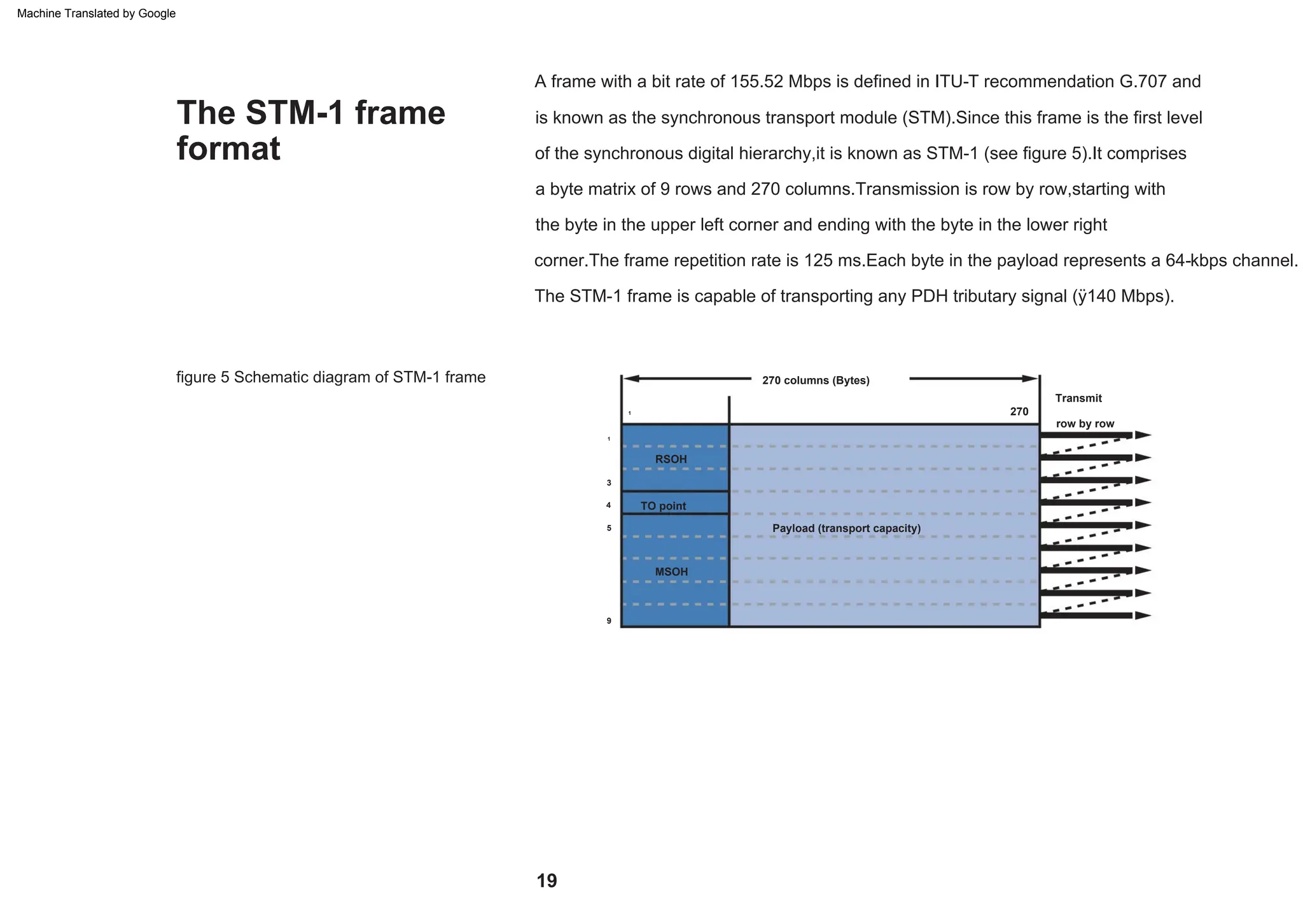
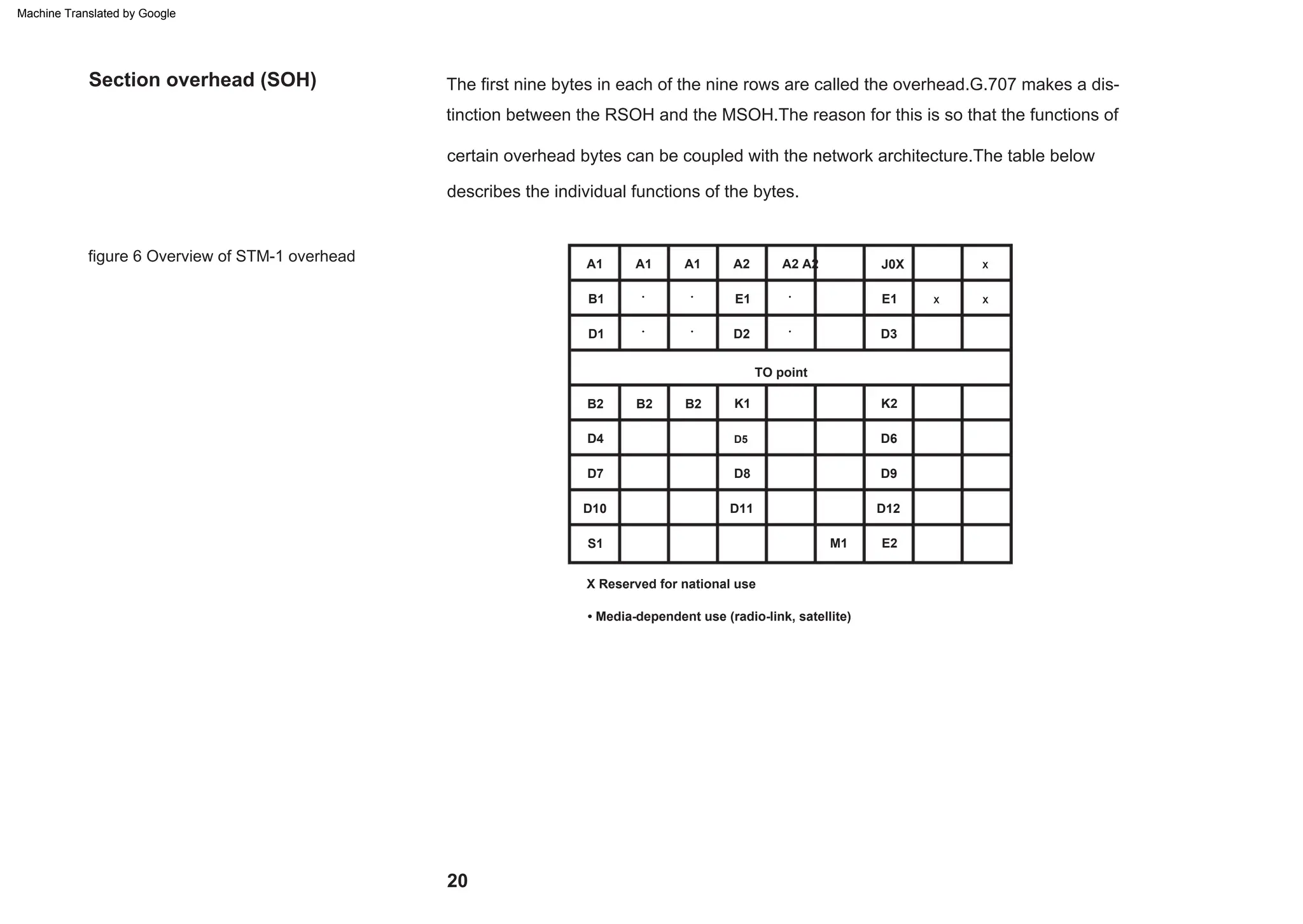
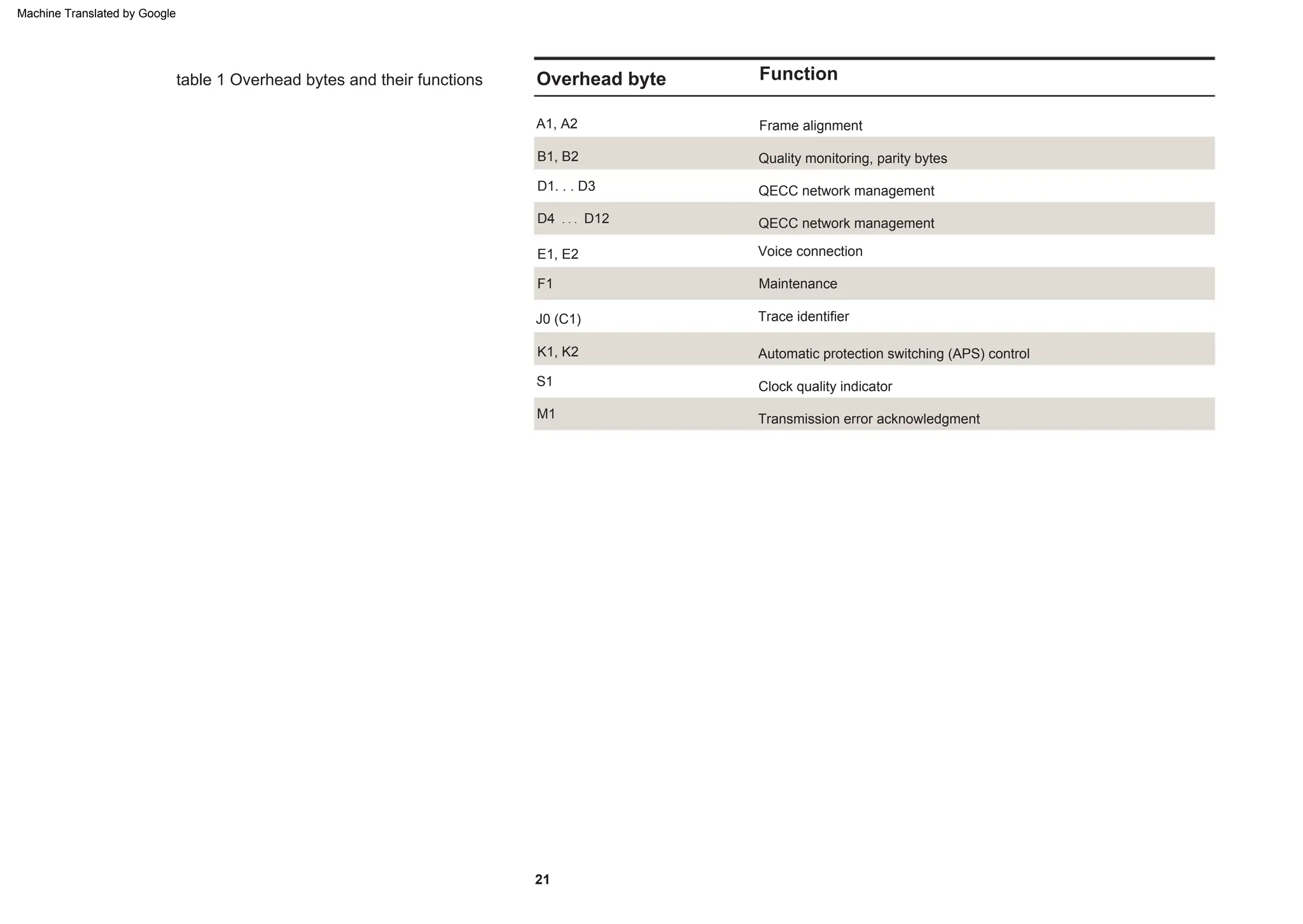
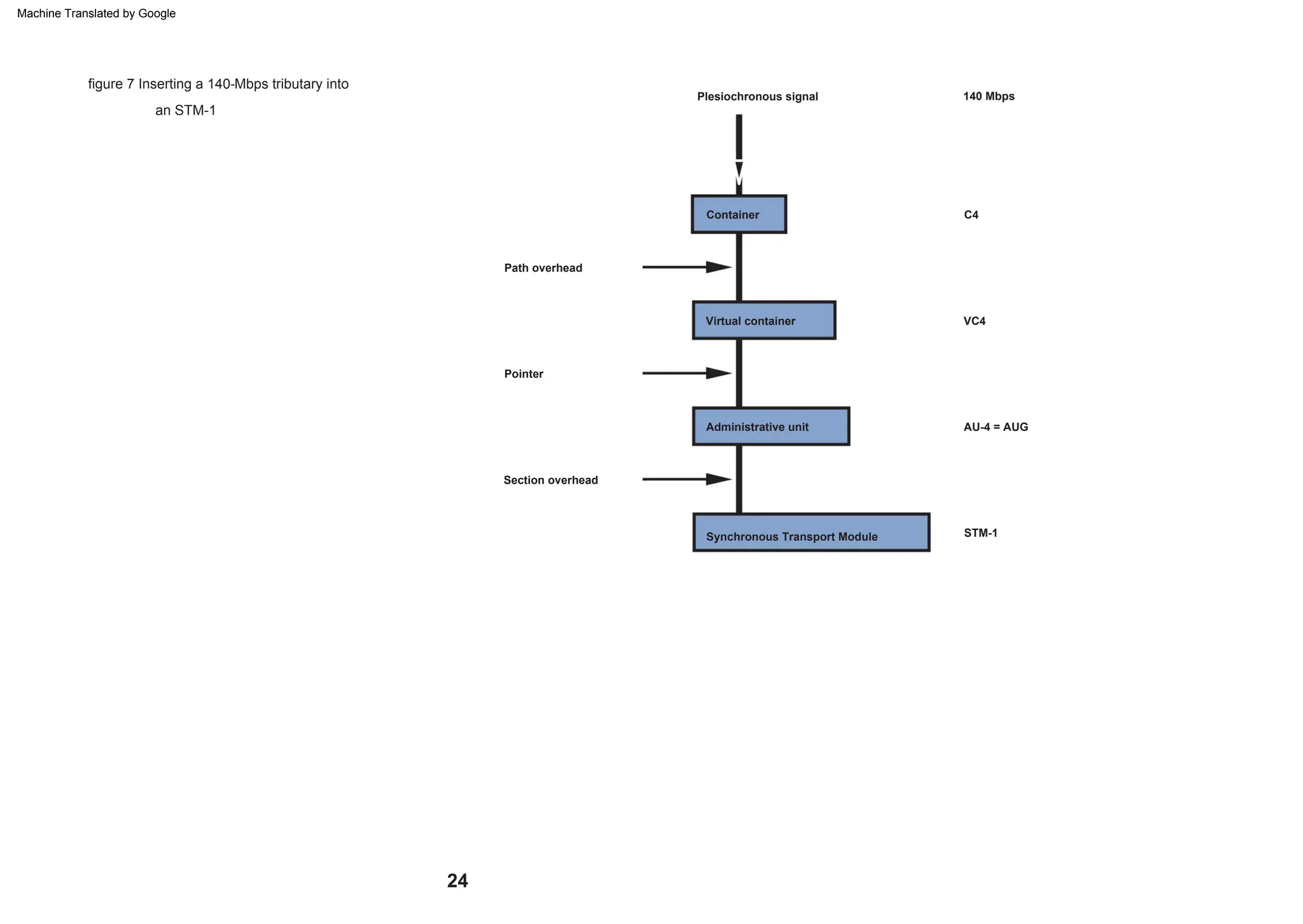
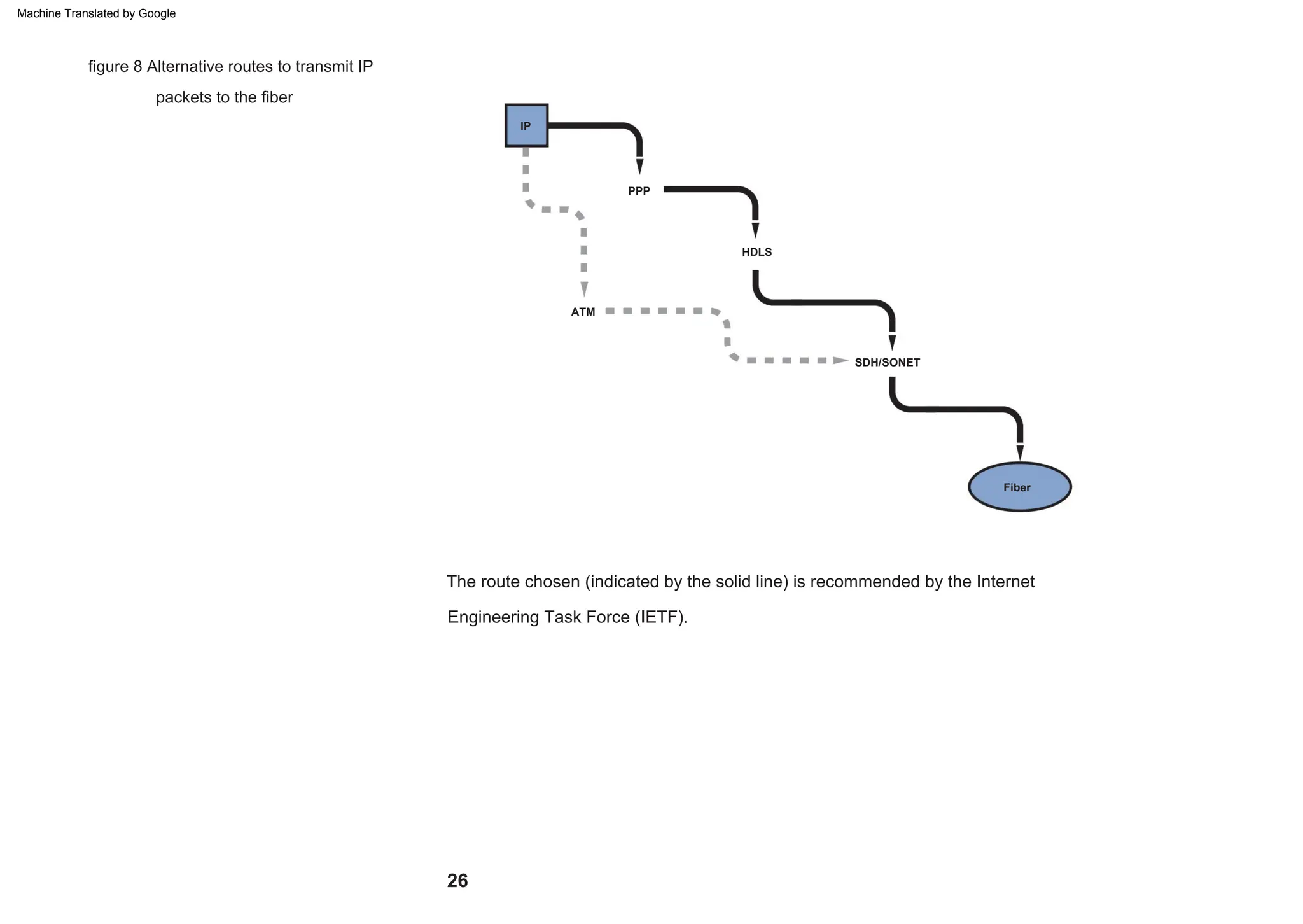
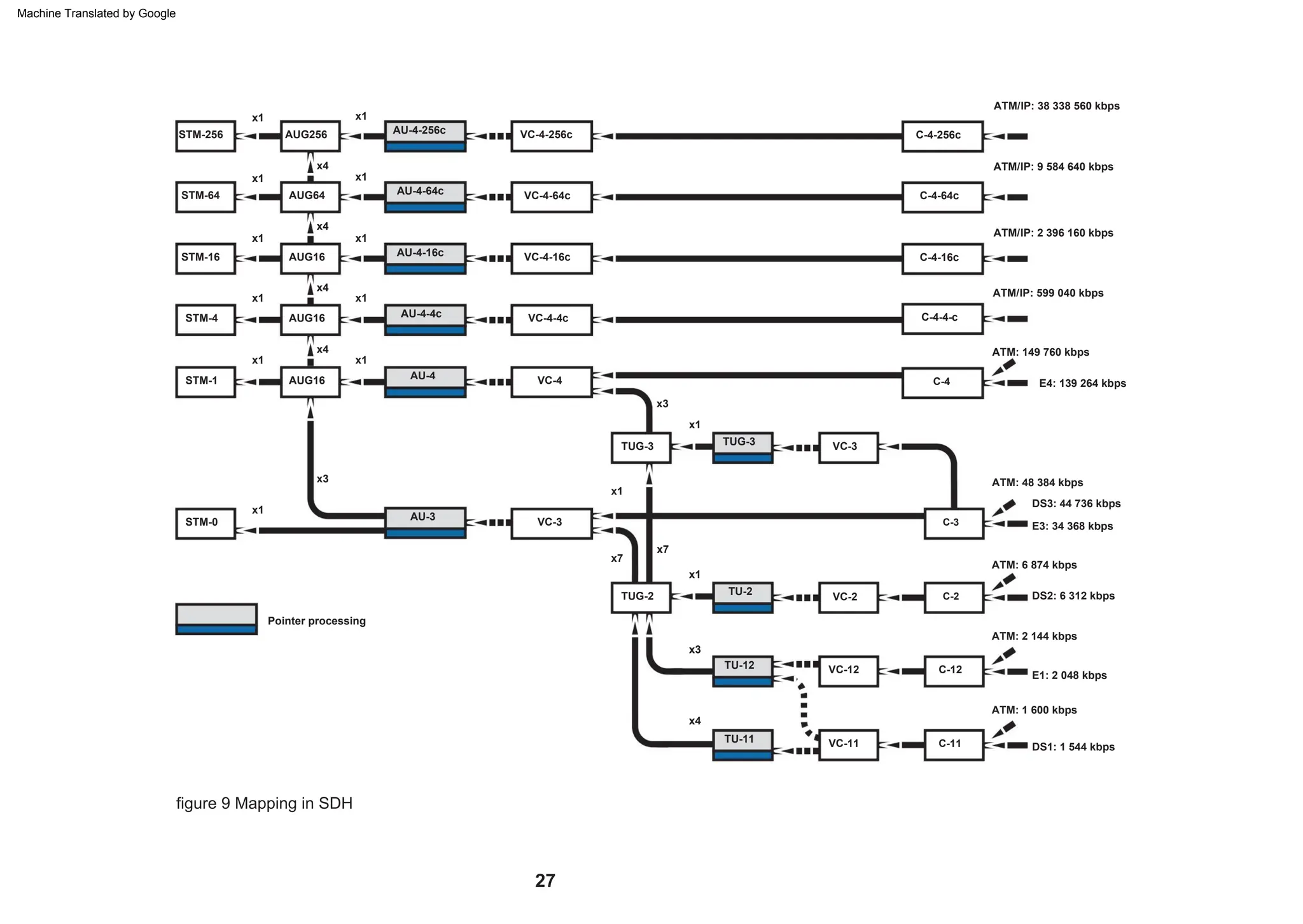
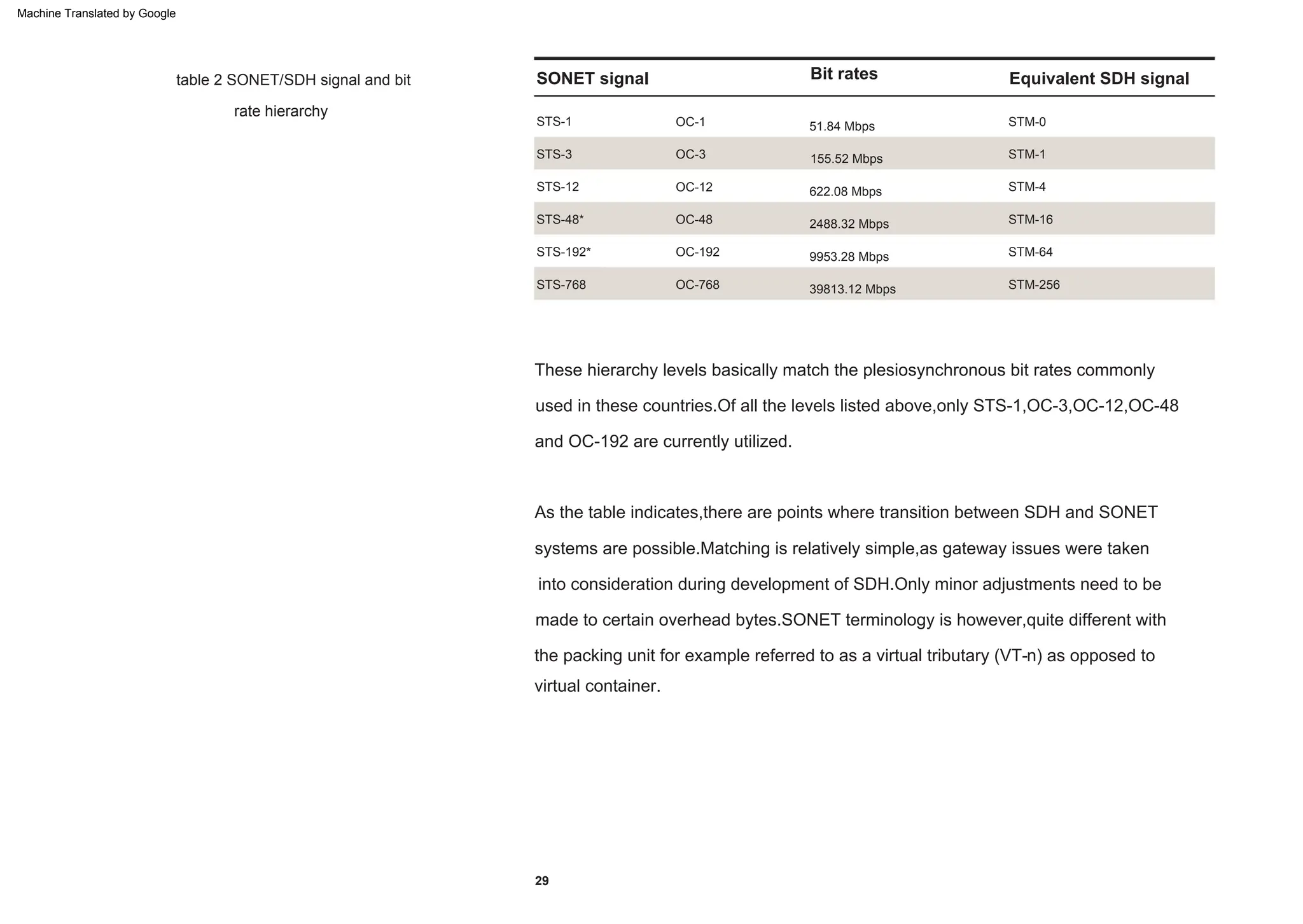
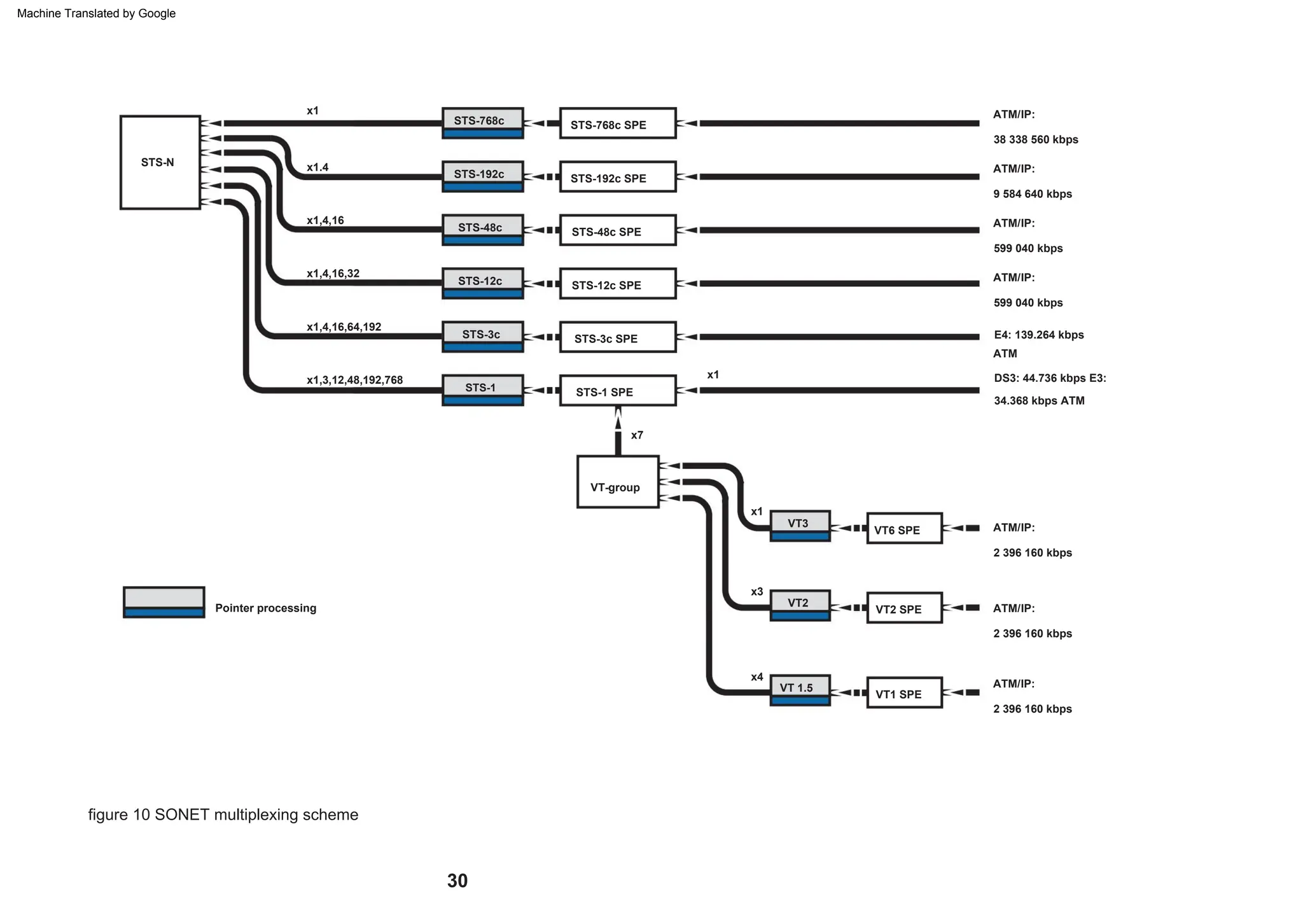
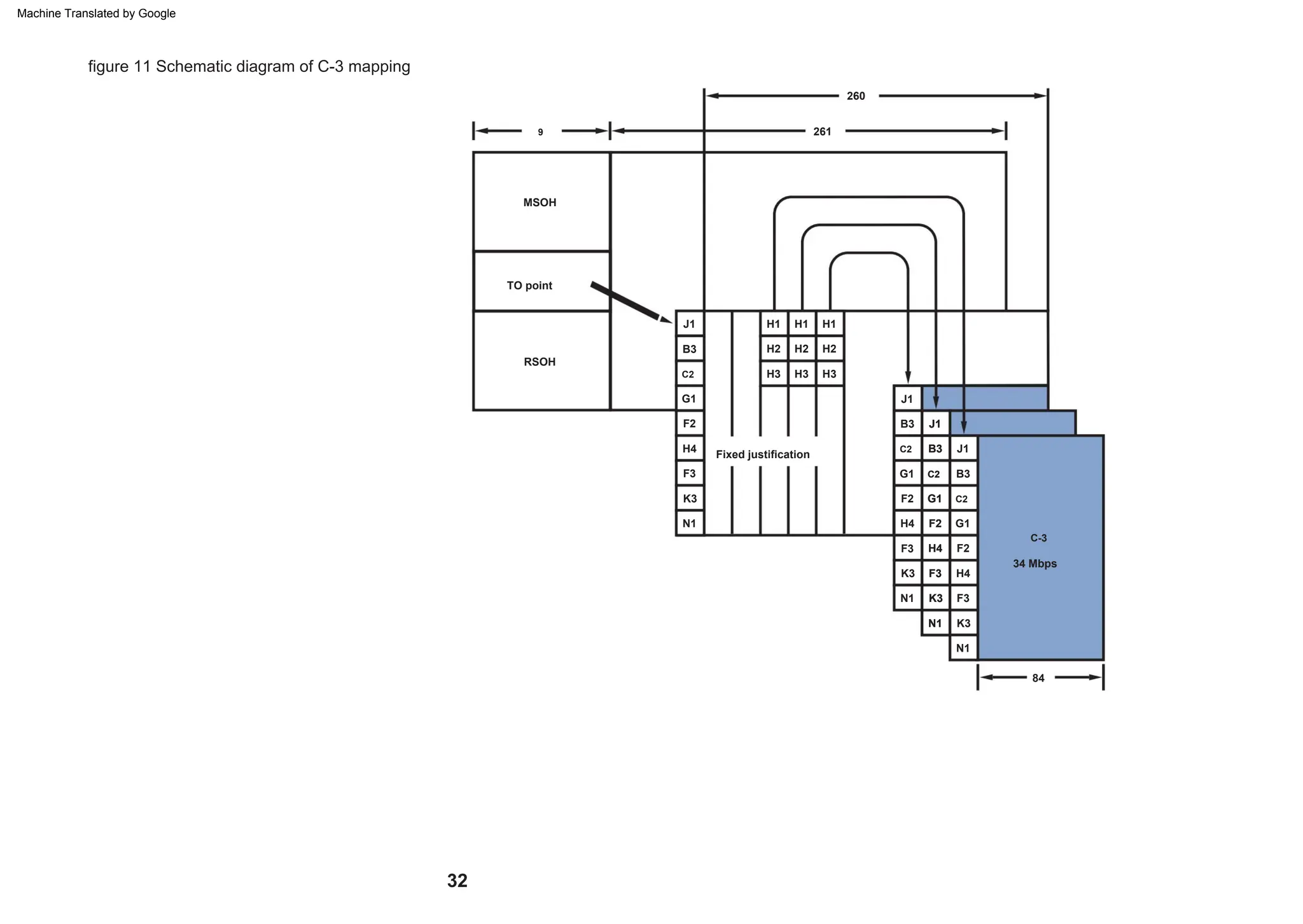
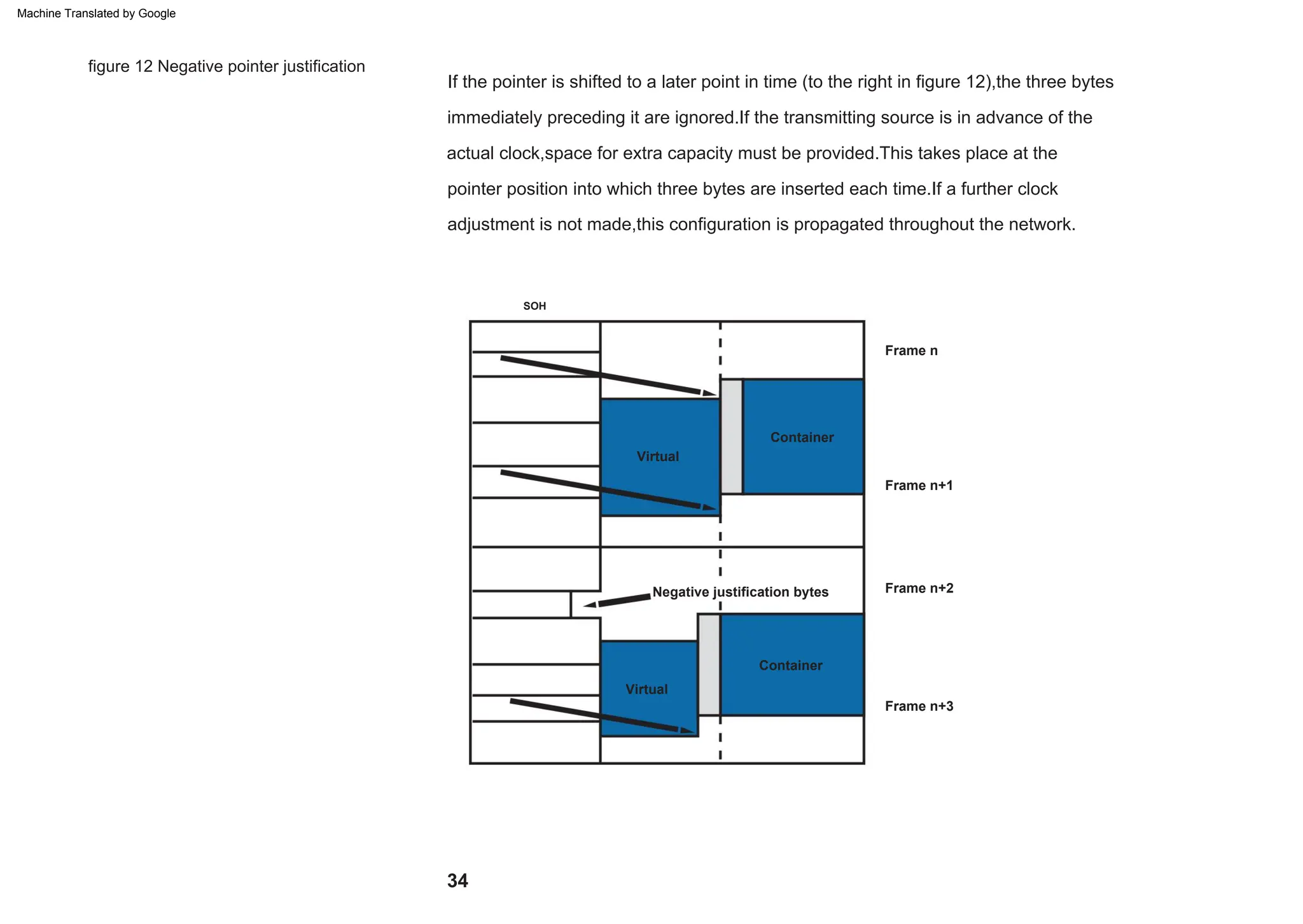
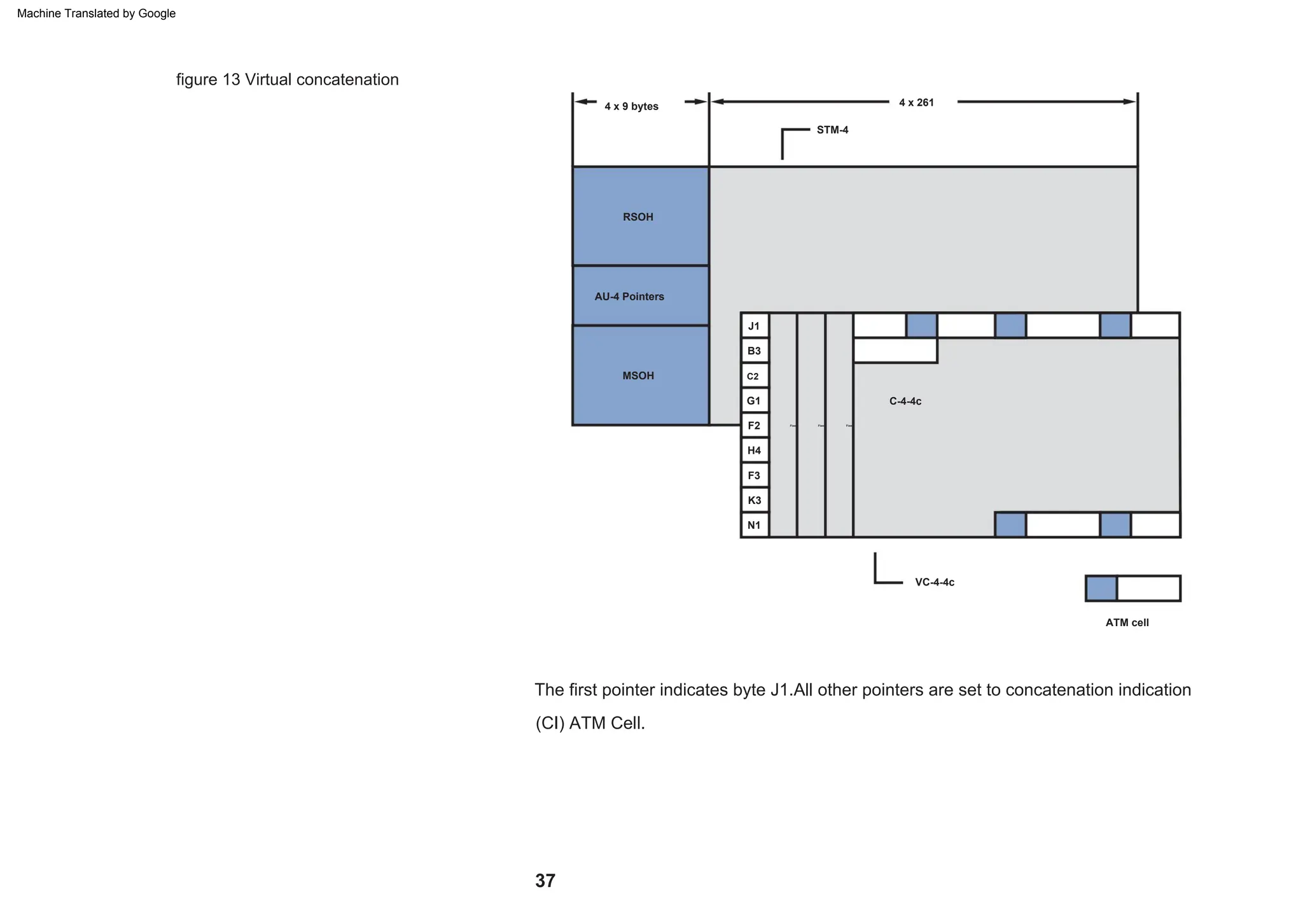
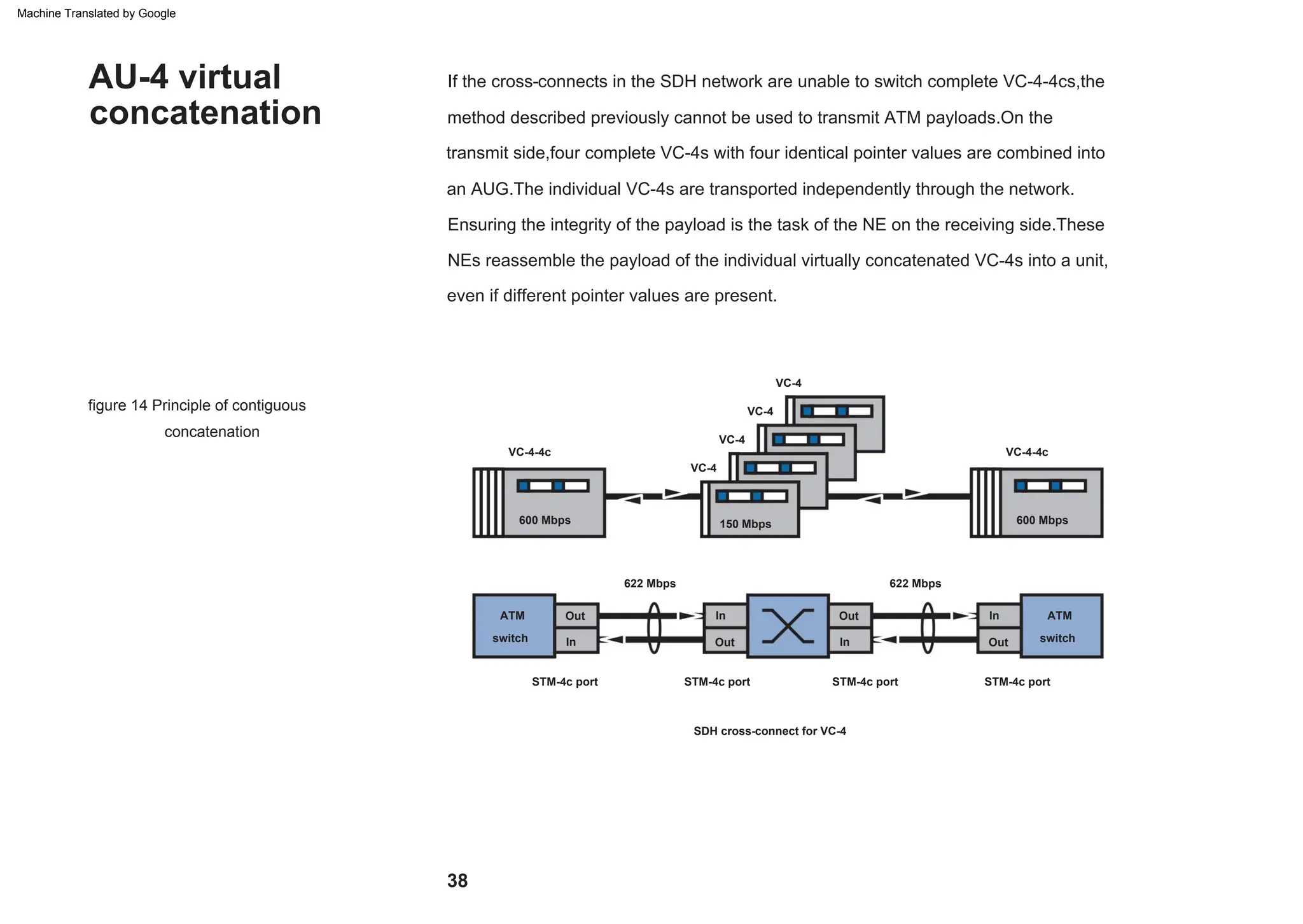
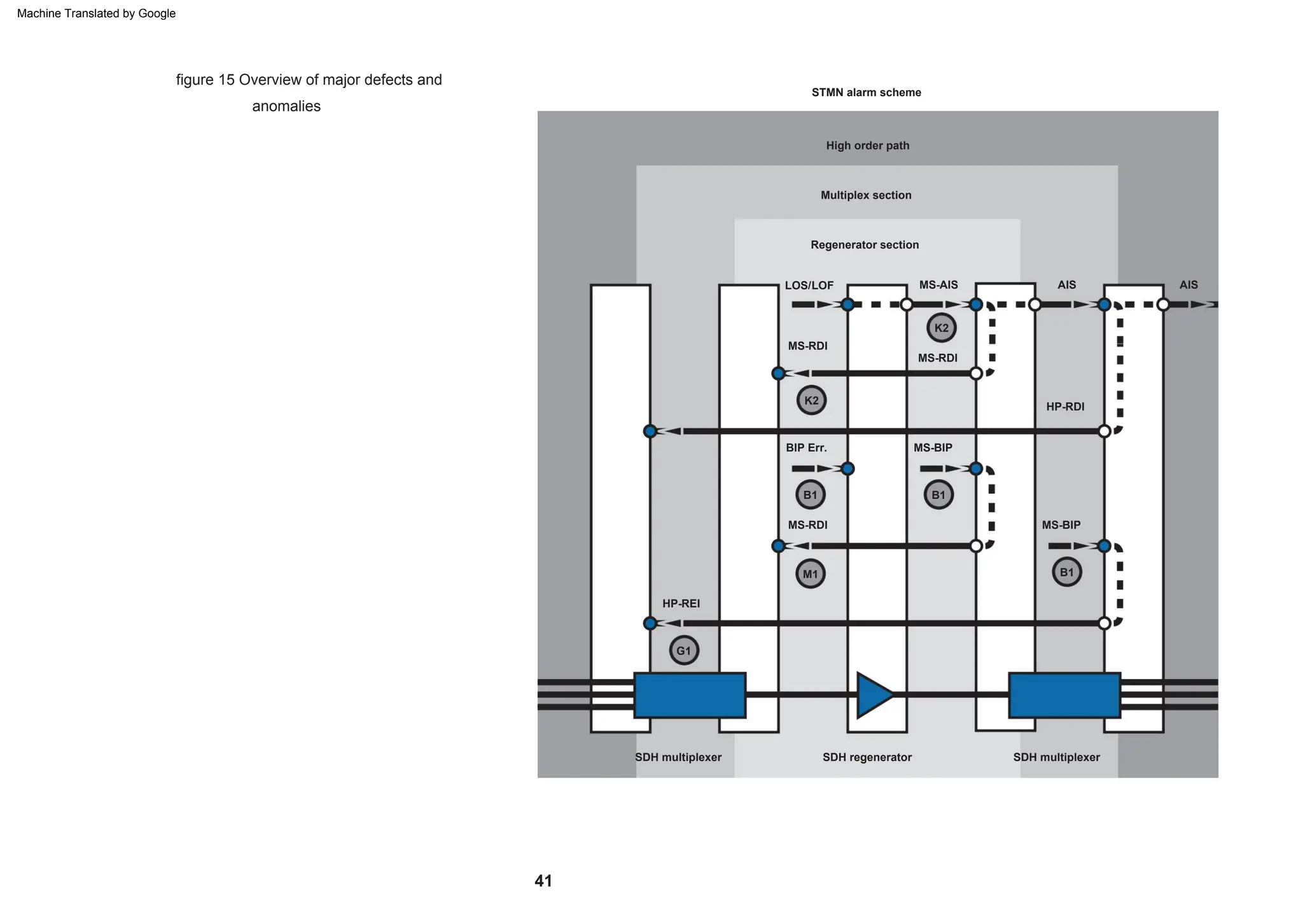
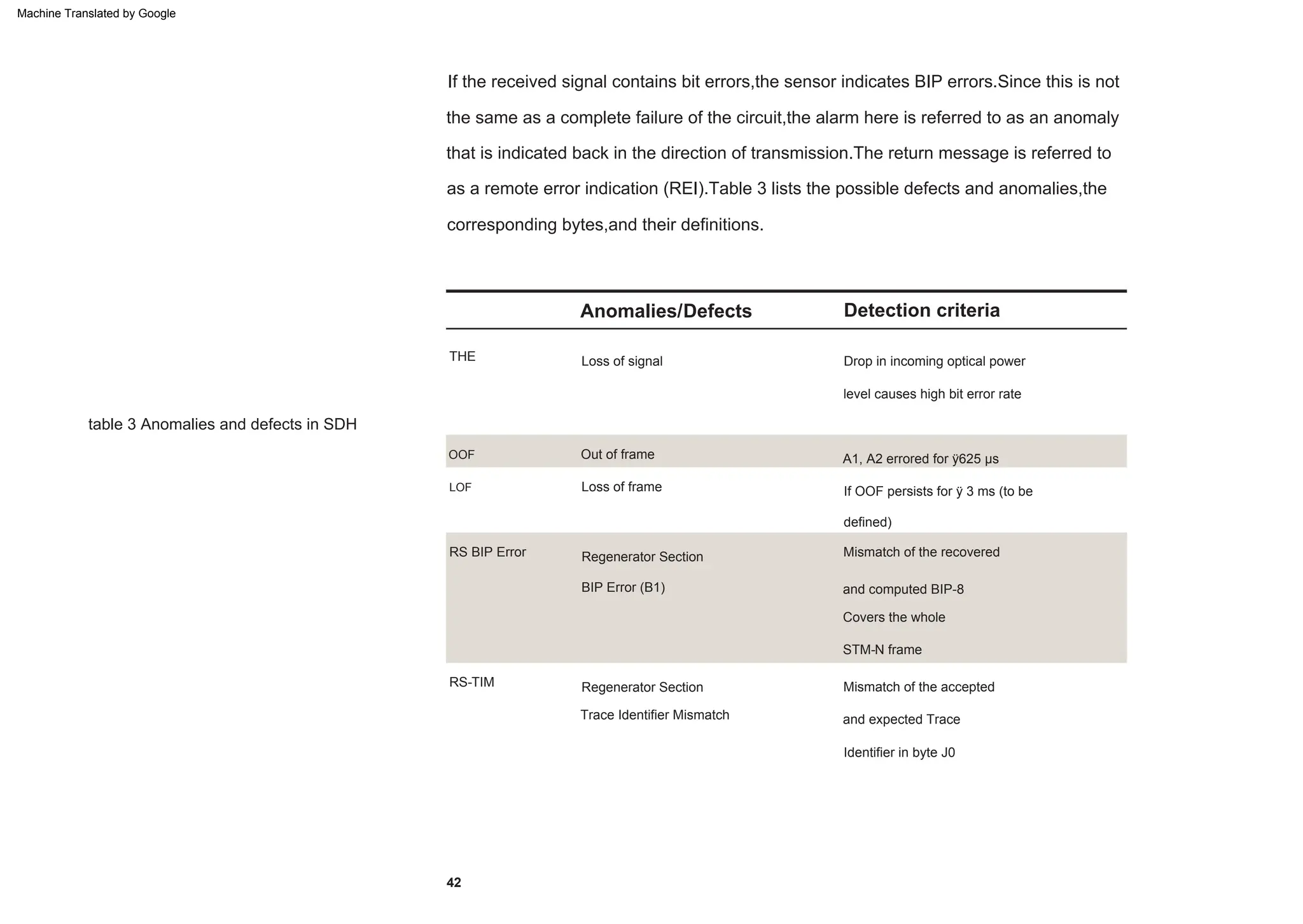
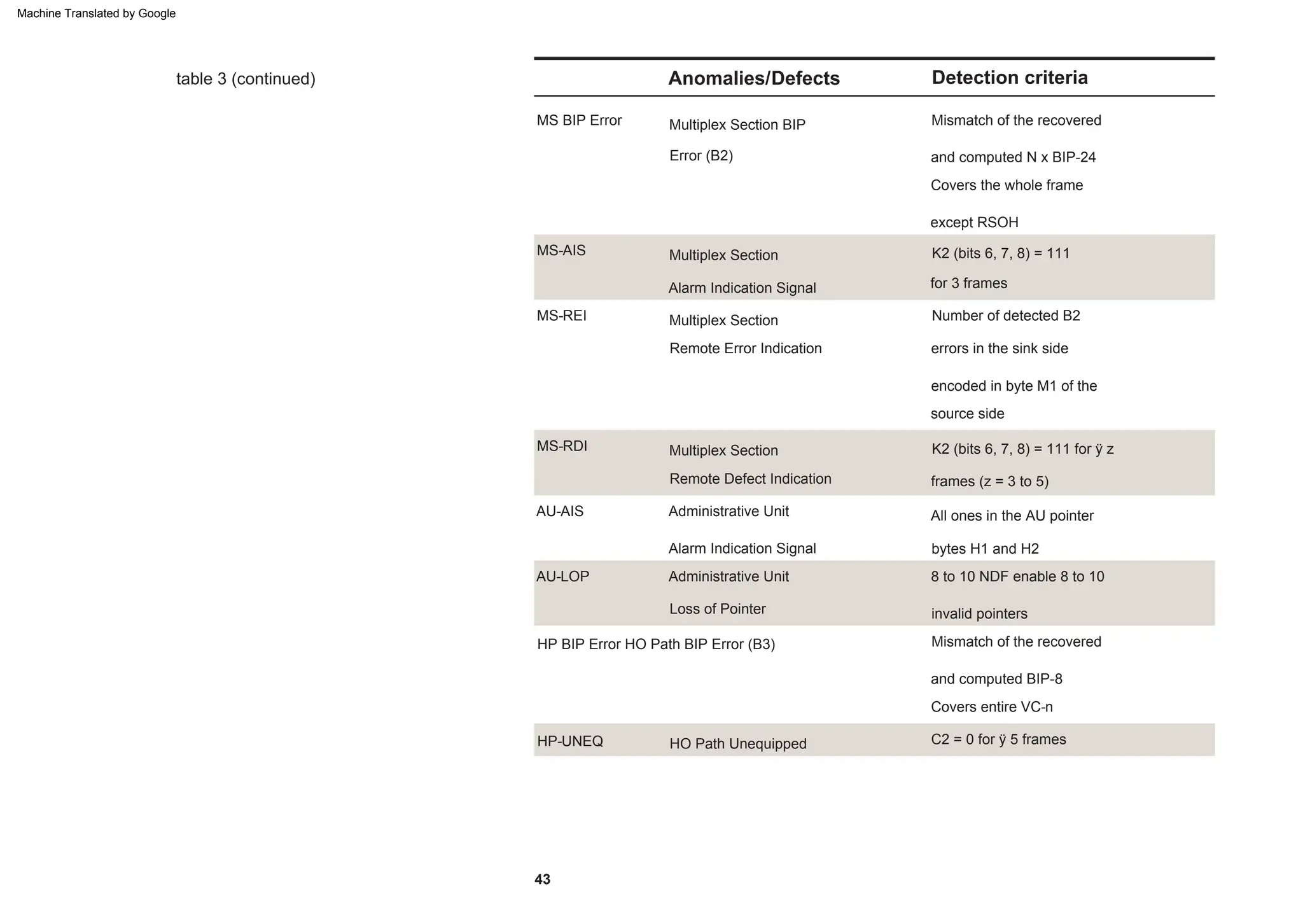
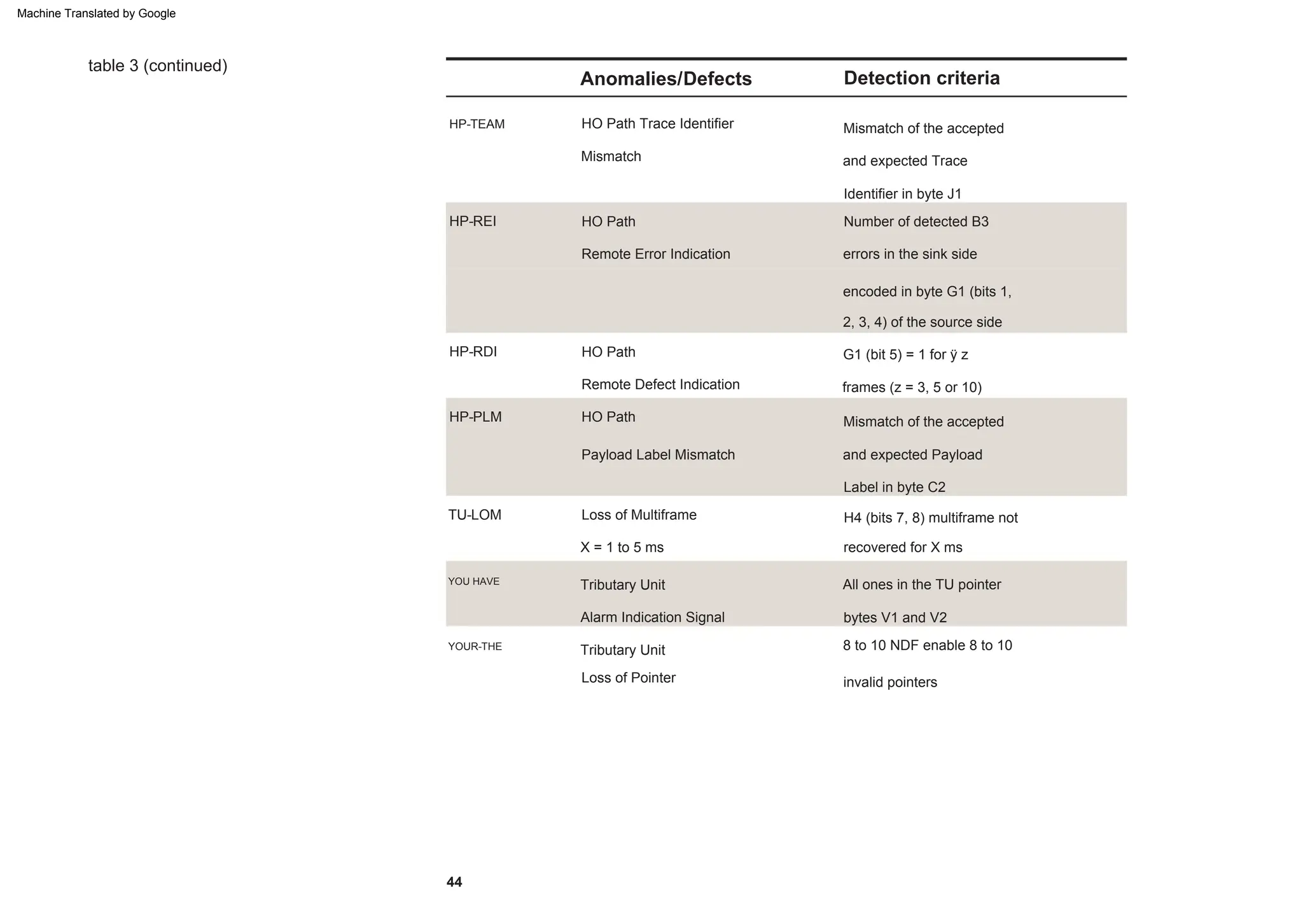
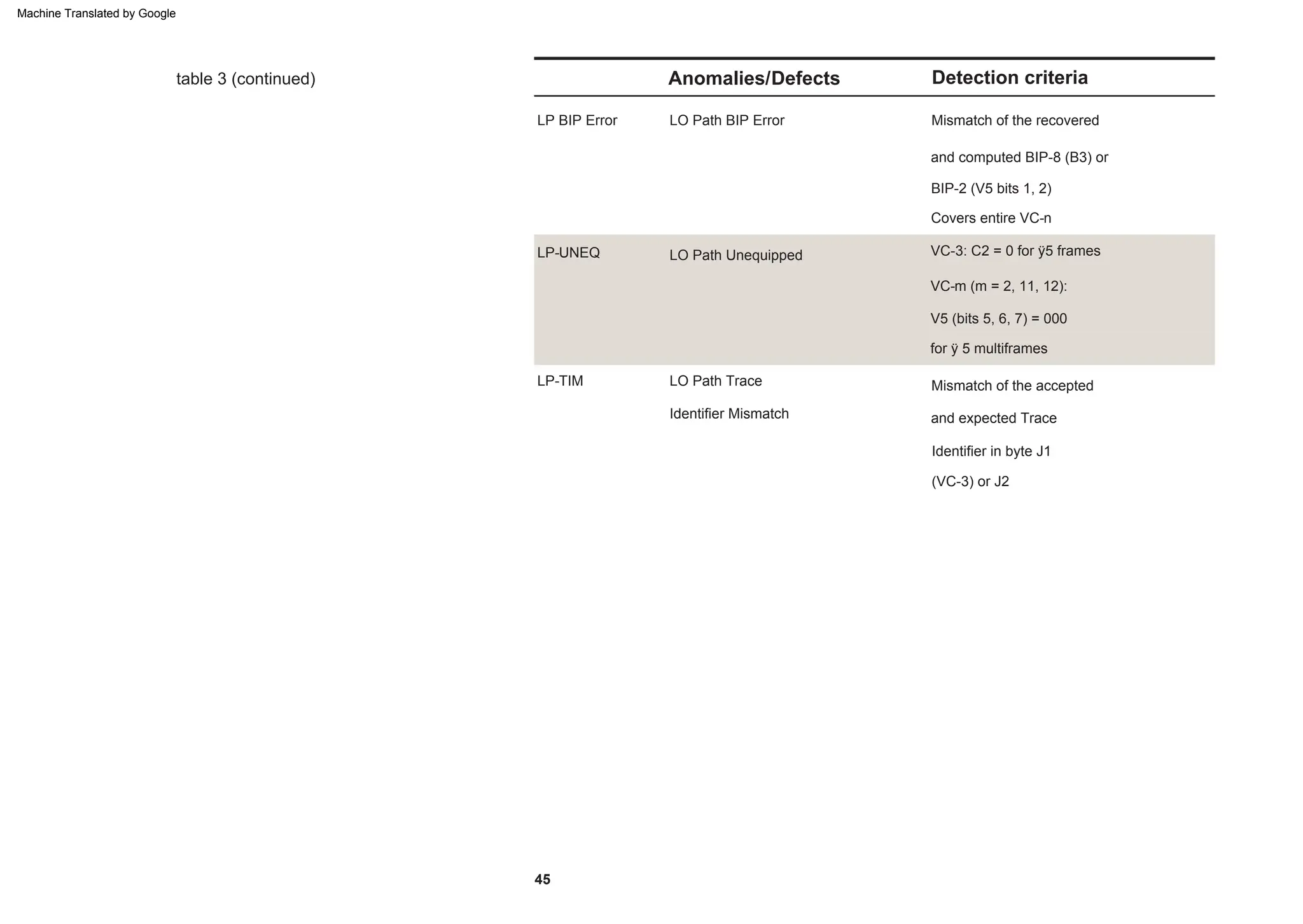
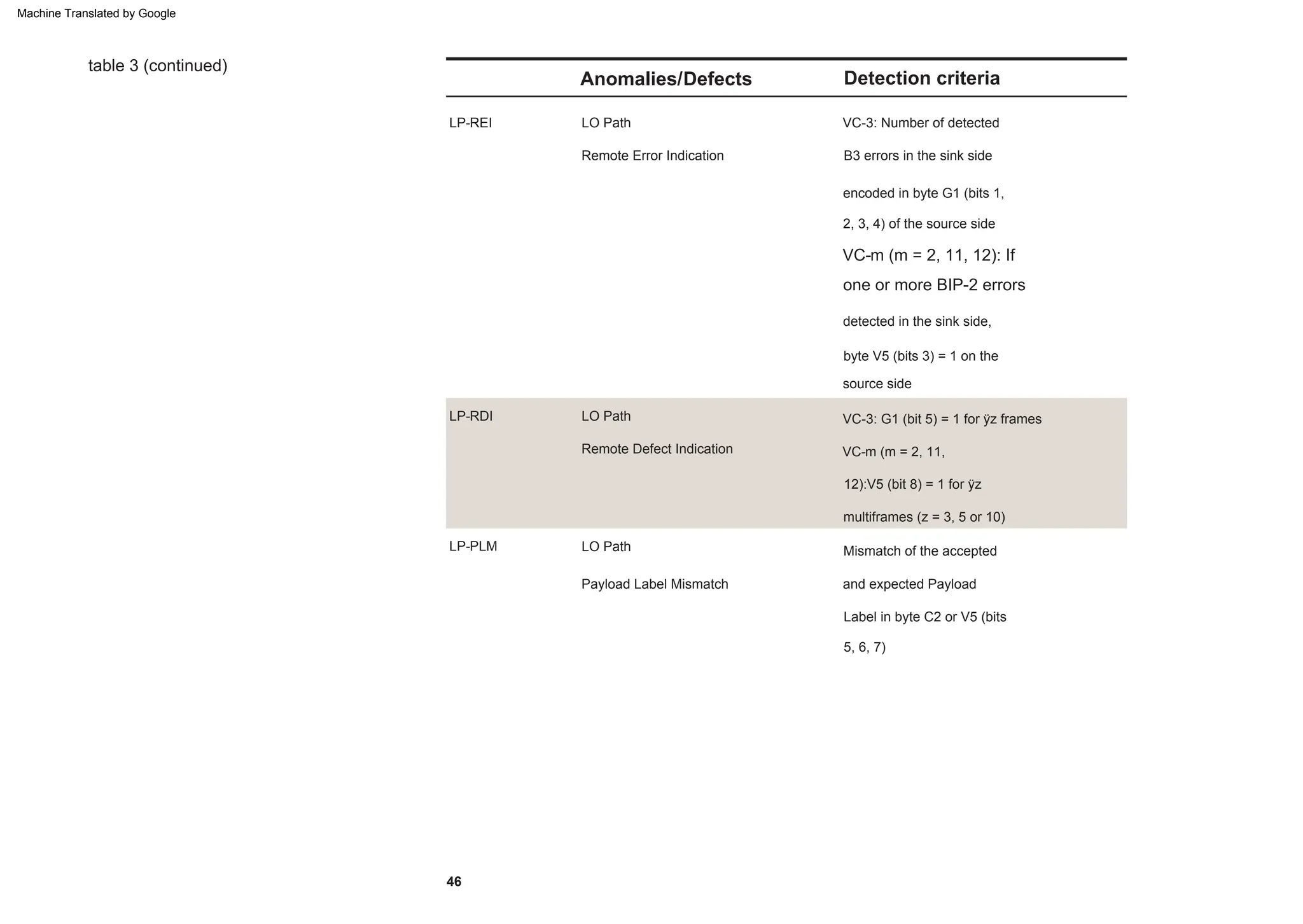
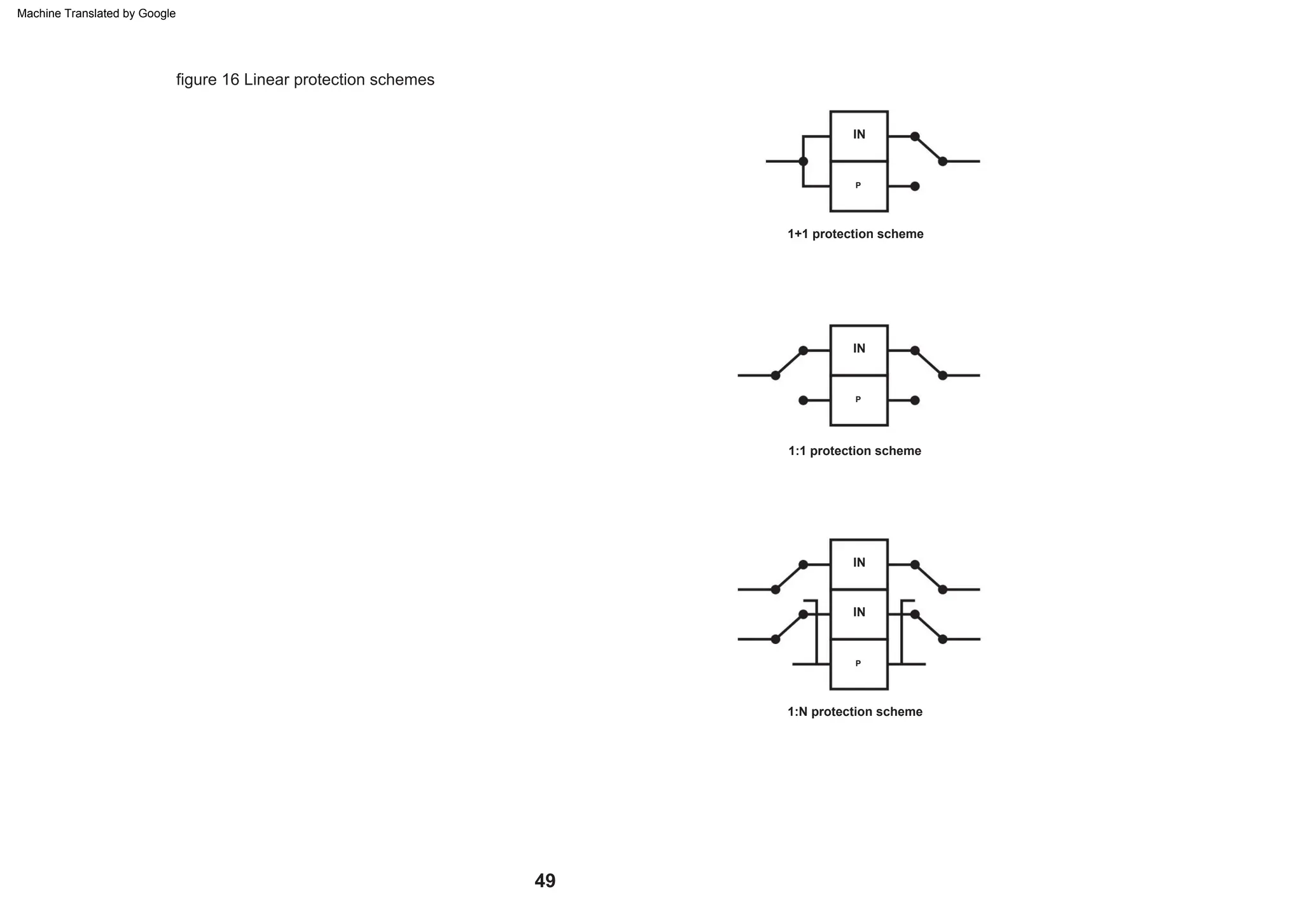
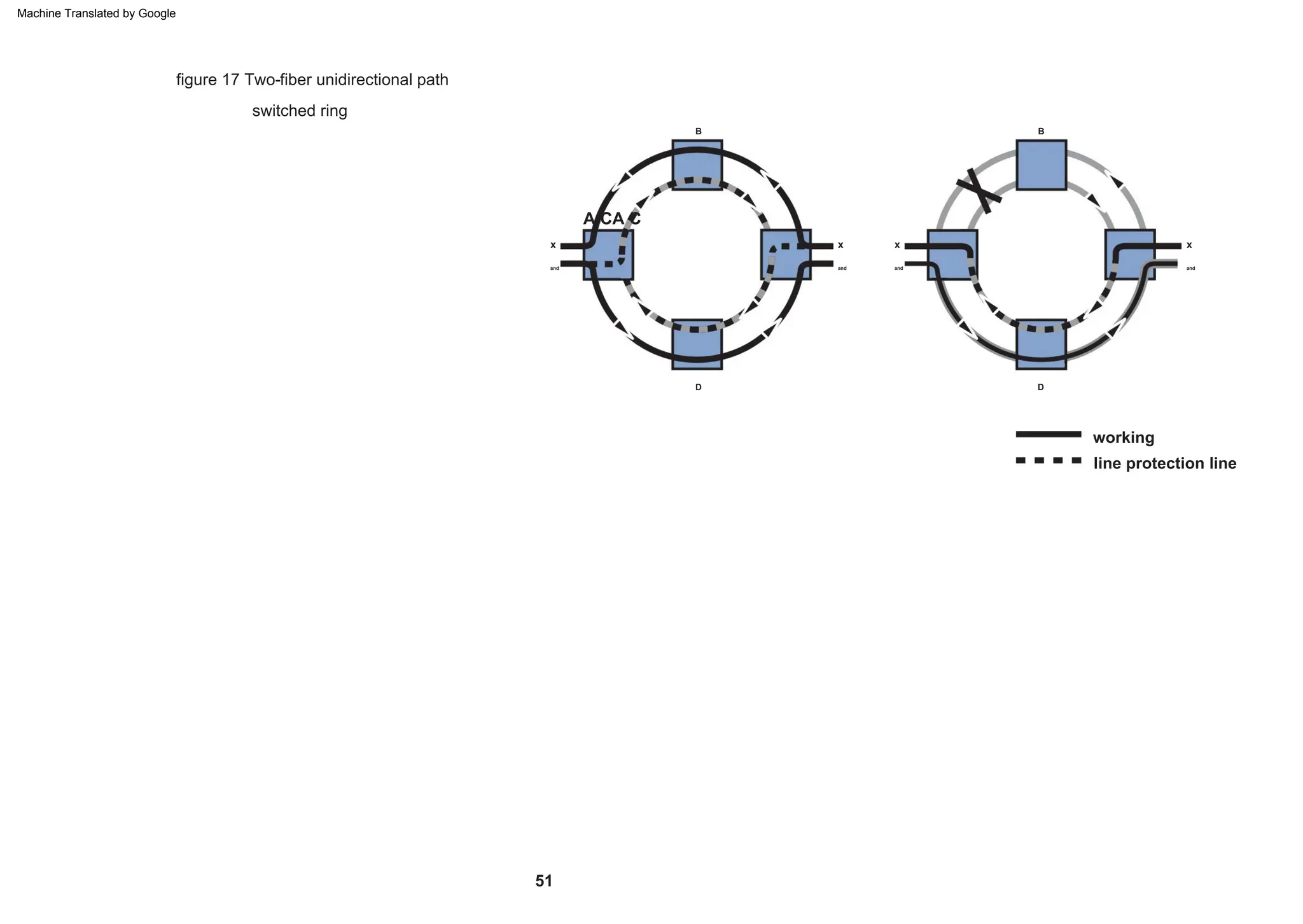
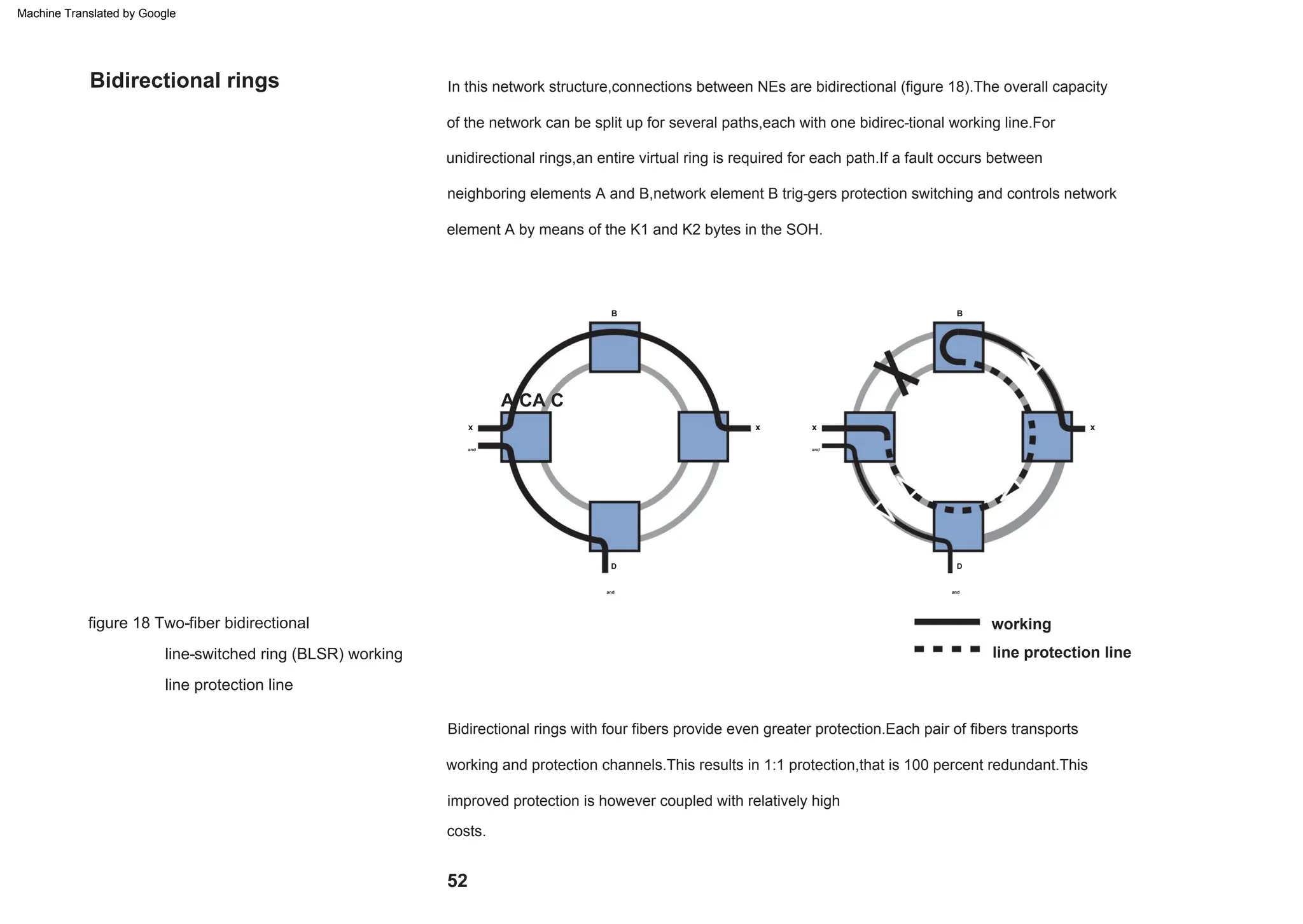
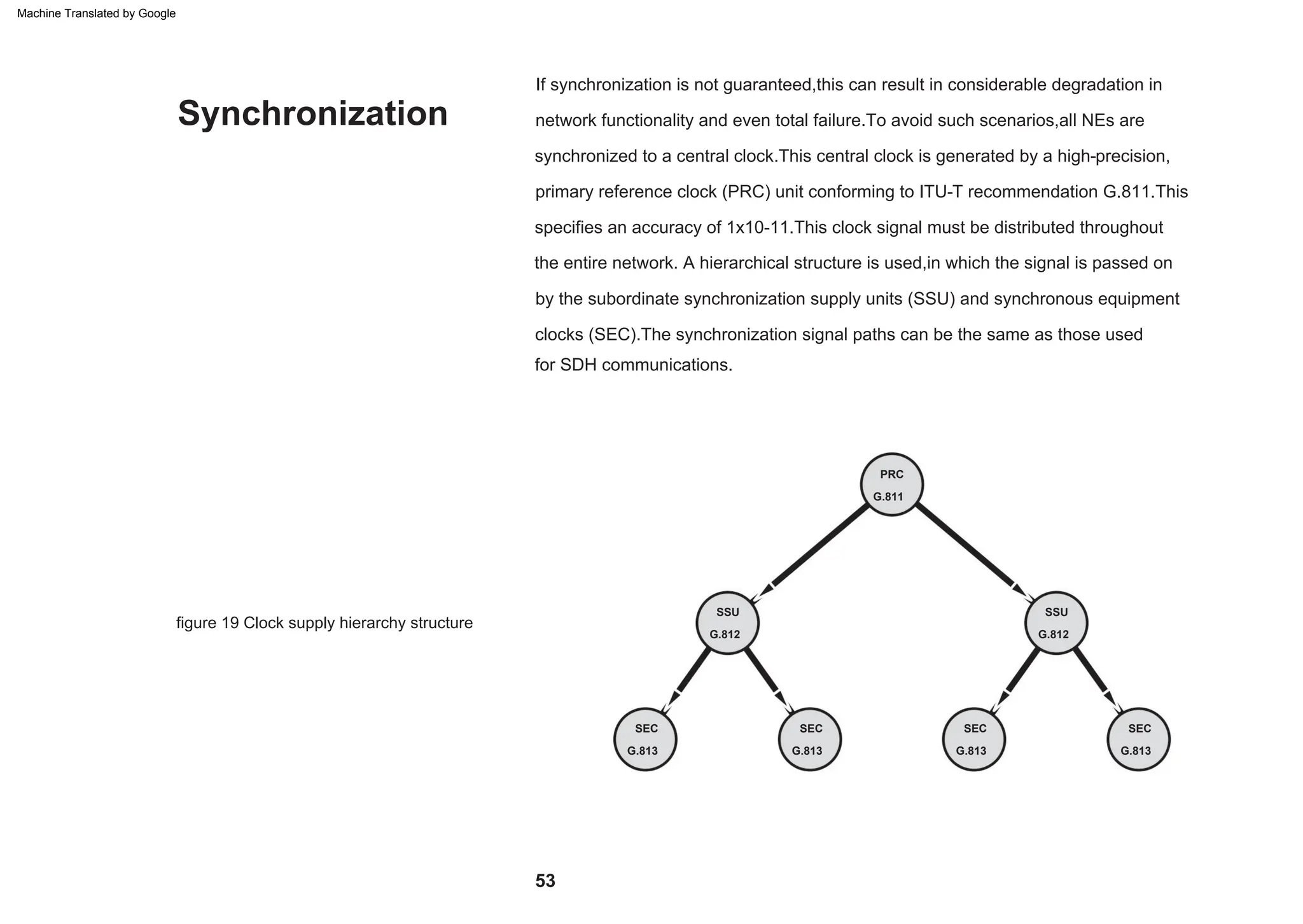
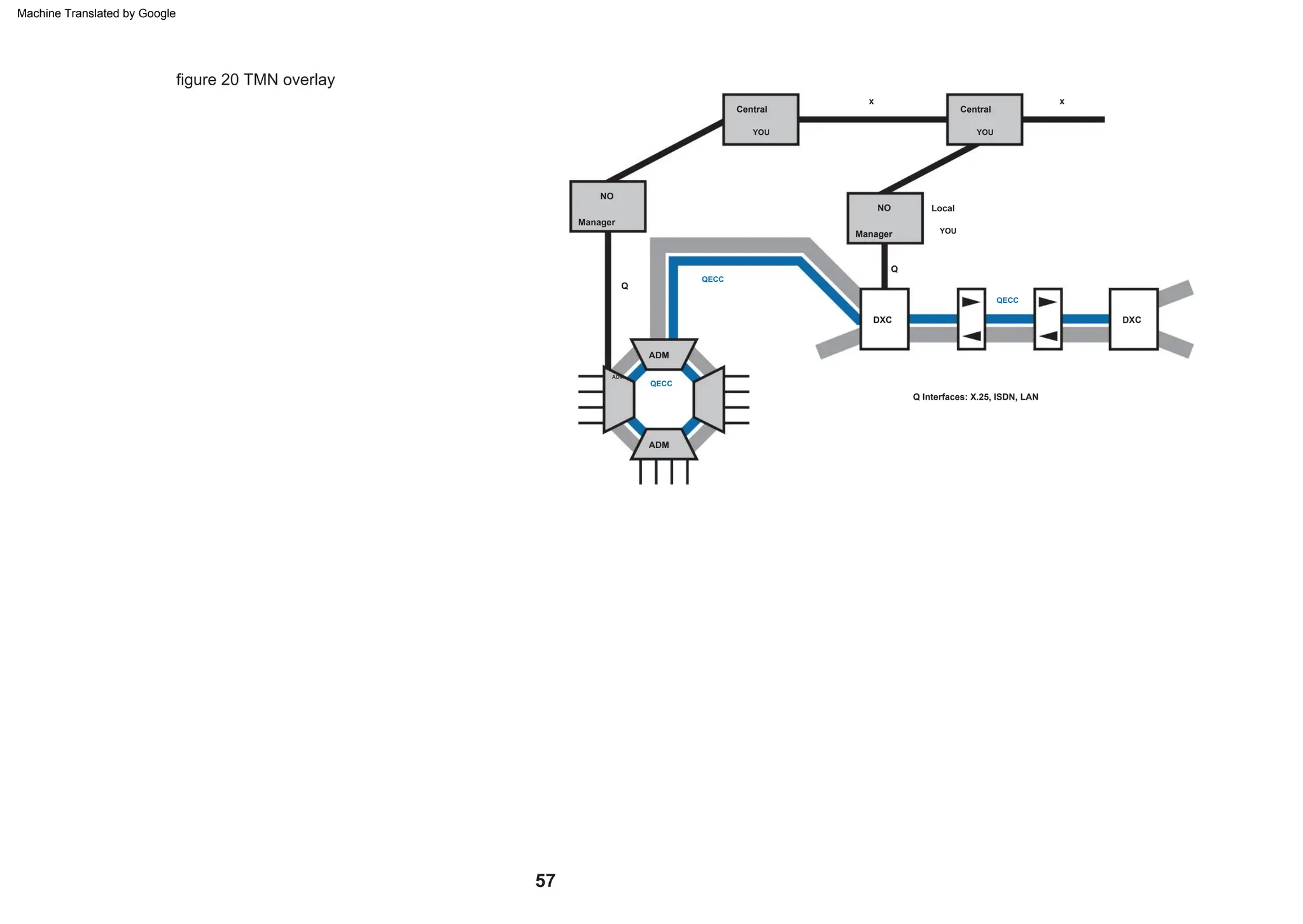
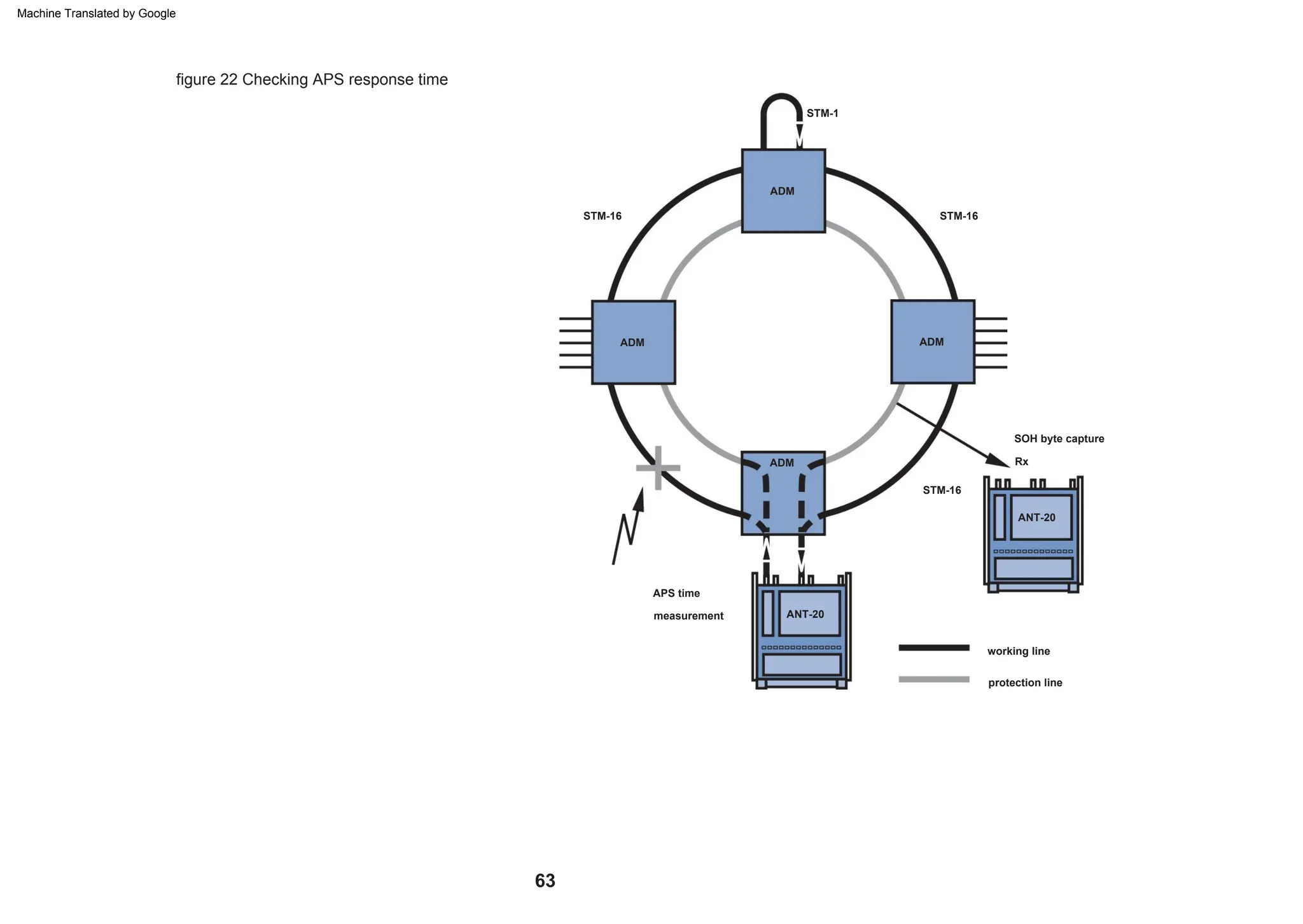
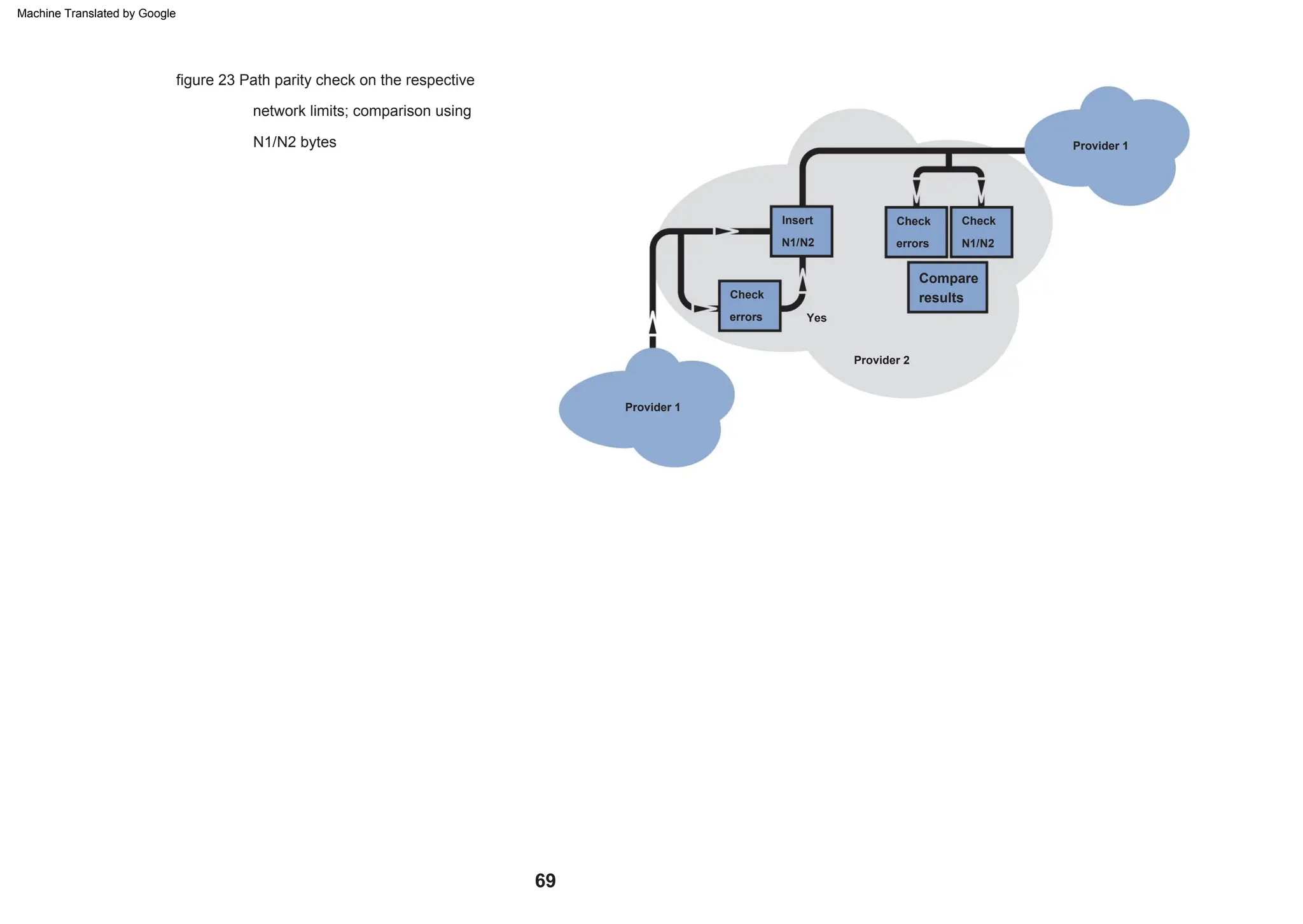
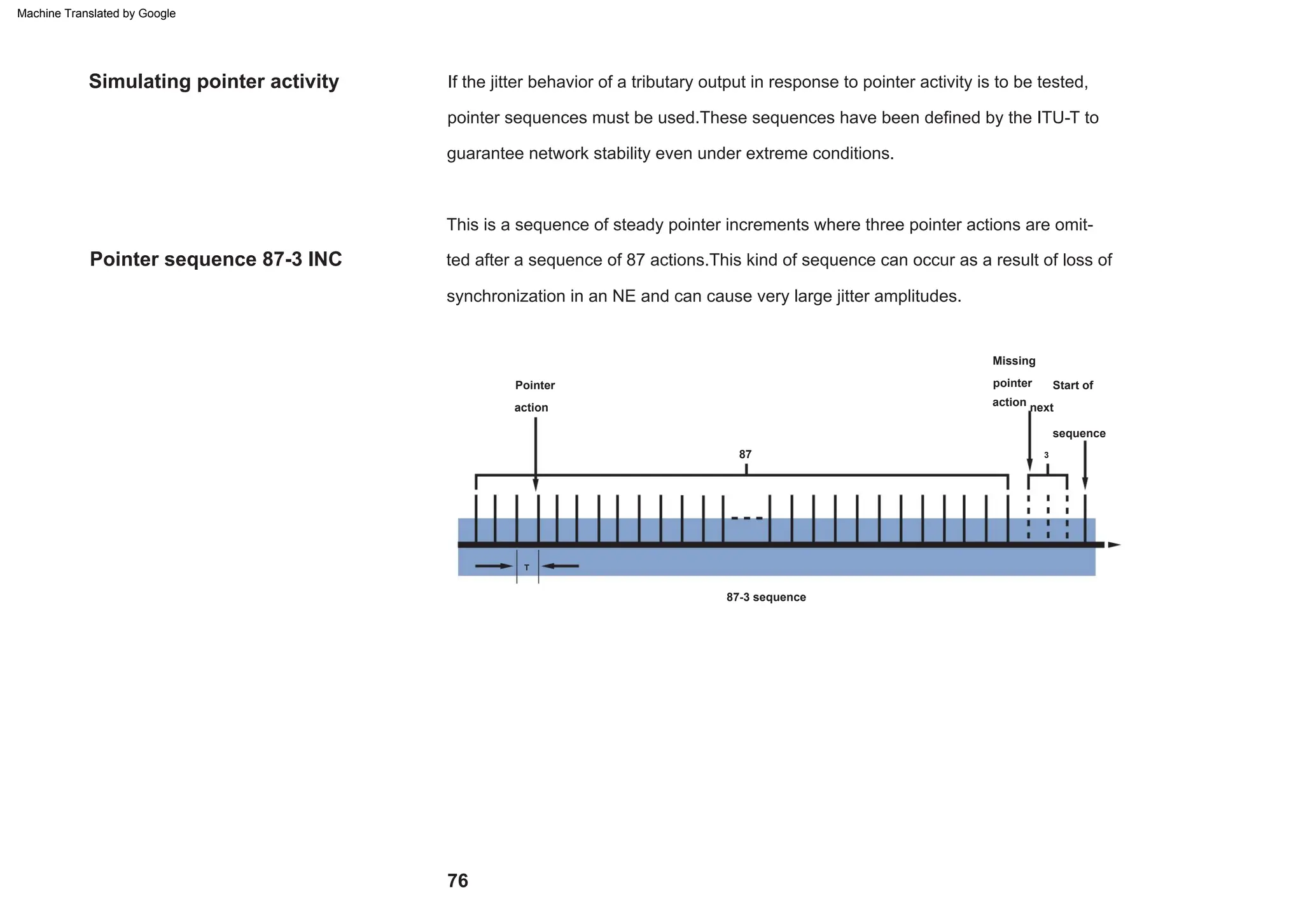
This document provides an overview of the Synchronous Digital Hierarchy (SDH) network components and frame format. It discusses the SDH layer model, components of a synchronous network including regenerator and multiplex sections, and the STM-1 frame format. It also briefly mentions AU-4 concatenation, differences between SDH and SONET, synchronization, and transmission at higher hierarchy levels.