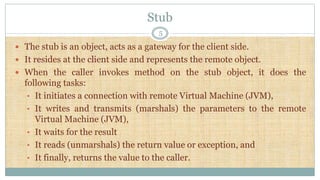
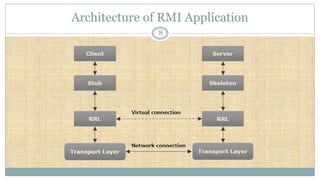
Remote Method Invocation (RMI) is an API in Java that facilitates remote communication between applications using stub and skeleton objects. The stub acts as a gateway on the client side, handling method invocations and communication with the remote virtual machine, while the skeleton serves as the server-side gateway, receiving requests and invoking methods on remote objects. The architecture involves a server program creating remote objects and a client program that requests and invokes methods on these objects, supported by multiple layers for connection management and remote reference handling.