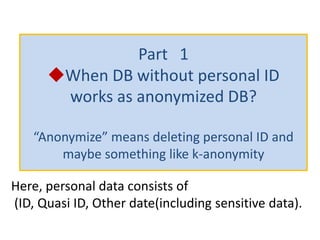
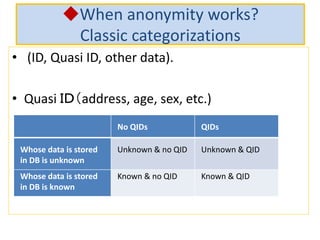
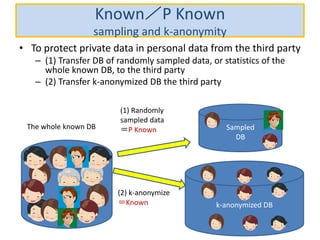
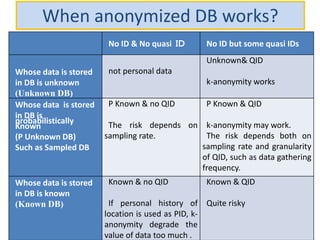
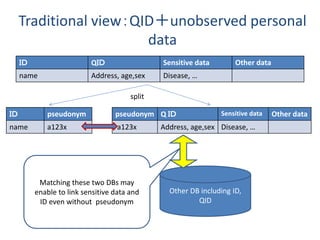
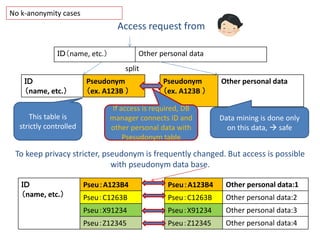
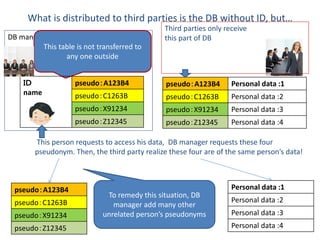
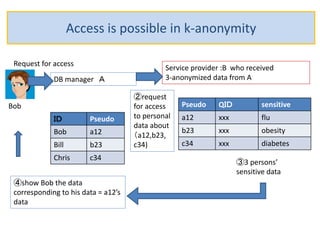
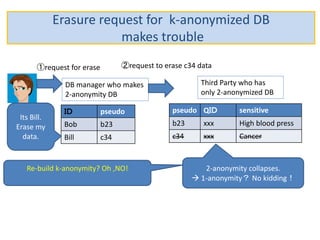
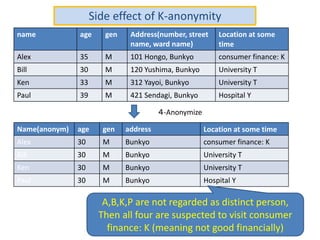
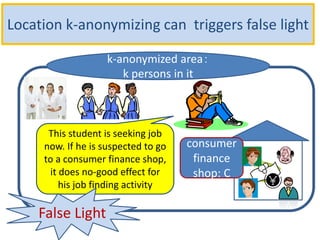
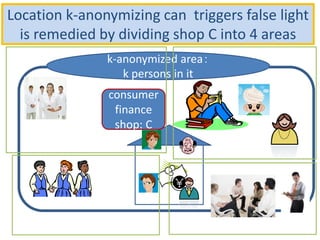
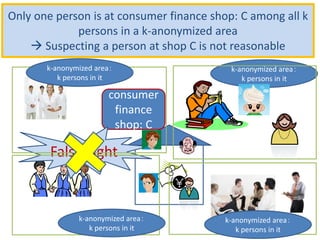
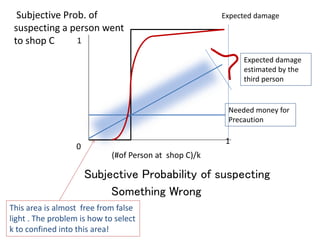
The document discusses the implications of anonymized personal data, focusing on privacy regulations, rights to be forgotten, and technical challenges associated with data anonymization. It highlights the EU's stance on Japanese data protection laws, the issues of k-anonymity, and the potential side effects of anonymization, such as false light. The paper suggests solutions to enhance privacy while maintaining data utility amidst legal and technical constraints.