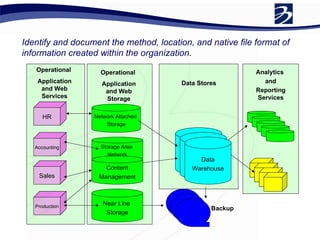
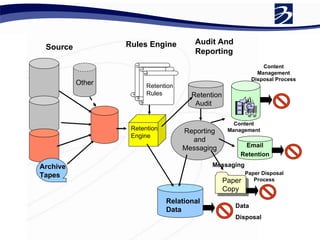
This document discusses the importance of developing a data retention policy and procedures for organizations. It covers key points such as legal requirements for data retention from various regulations, conducting a risk assessment to determine retention periods, implementing policies and controls for digital data management, establishing litigation hold procedures, and monitoring for compliance. The presentation emphasizes that a data retention policy is necessary to meet legal and business needs while balancing operational costs, and can help reduce sanctions and discovery costs if litigation occurs.