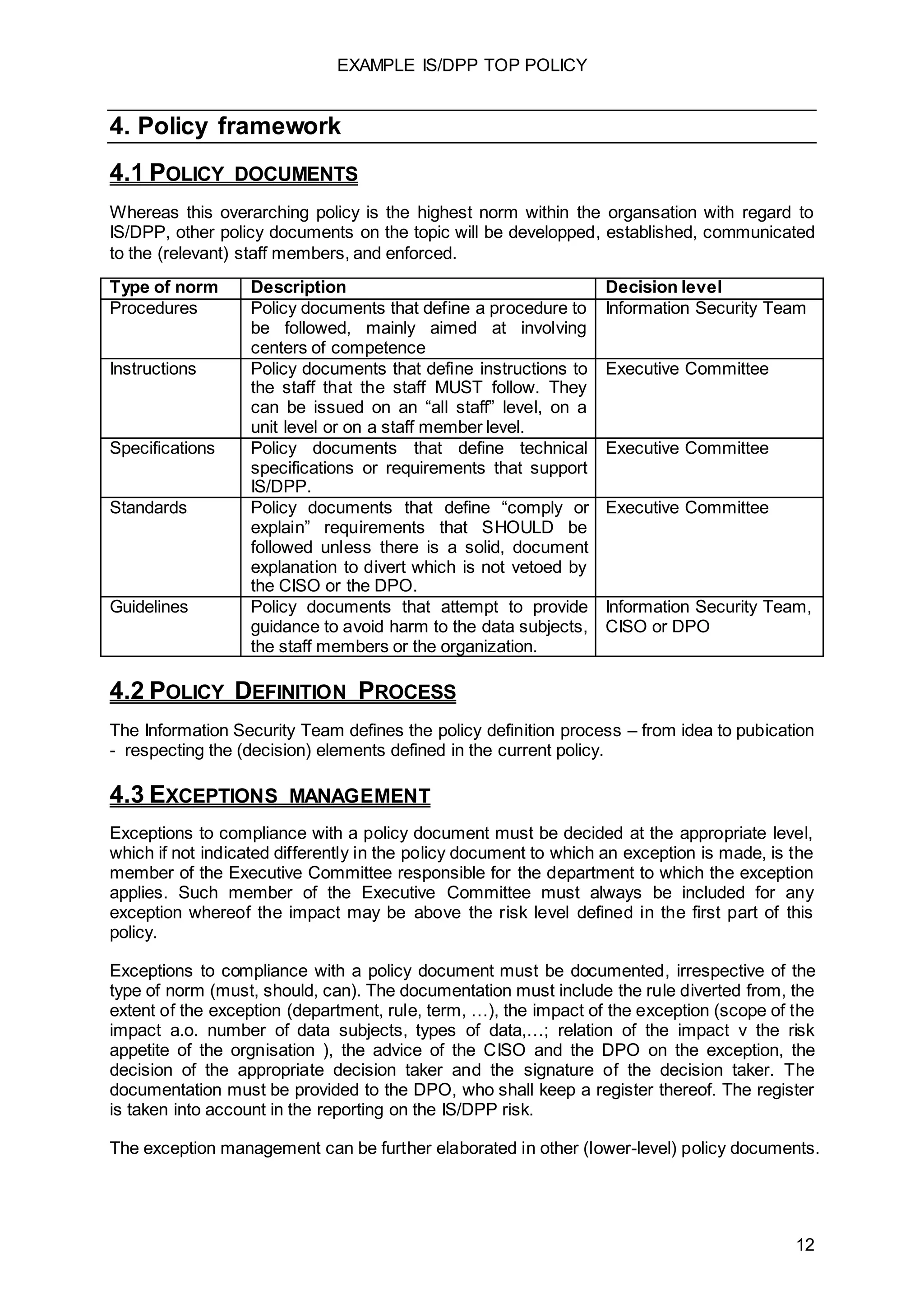
The document outlines the top policies regarding information security, data protection, and privacy (IS/DPP) for a corporation, emphasizing management commitment, accountability, governance, and communication. It defines key roles and responsibilities within the organization, including those of the executive committee, CISO, DPO, and legal department, to ensure compliance and effectiveness of IS/DPP practices. The principles underscore a proactive, ethical approach to risk management and implementing robust security measures aligned with legislation and best practices.