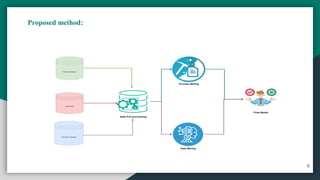
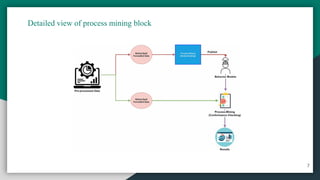
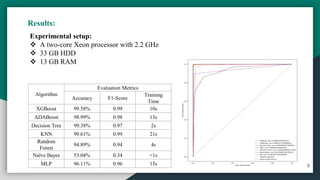
The document presents 'iot-shield,' a novel approach for detecting DDoS attacks on IoT devices, which are increasingly vulnerable due to their limited resources. It combines machine learning and process mining techniques to predict and mitigate such attacks, showcasing high accuracy in various algorithm evaluations. The authors aim to develop a real-time detection and mitigation platform for IoT and IIoT devices in the future.