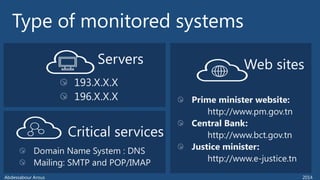
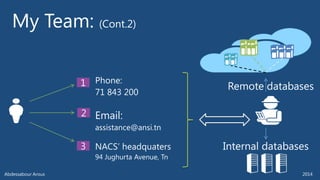
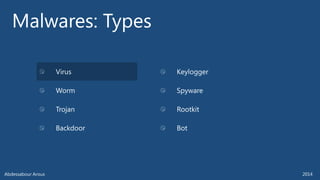
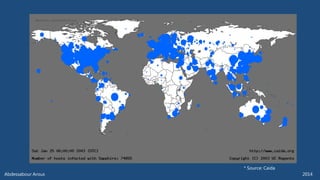
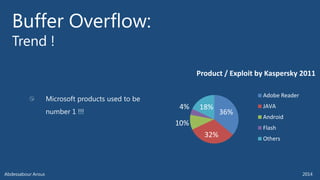
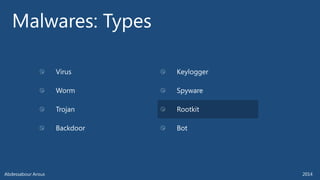
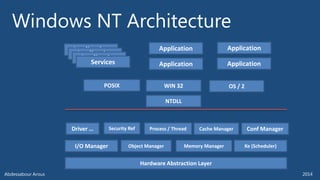
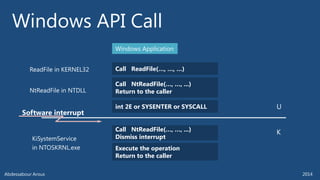
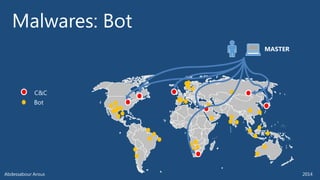
The document outlines various technical aspects related to cybersecurity, including monitoring teams, attack detection, and incident response. It references multiple cyber threats and their propagation speeds, along with associated vulnerabilities in software like Adobe Reader and Java. Additionally, it touches on international perspectives regarding cyber warfare and legal considerations.

![AbdessabourAROUSCritical InfrastructionsMonitoring Team -tunCERT
abdessabour.arous[x40]ansi.tn](https://image.slidesharecdn.com/abarous-introductiontomalware-themalwareshow10-2014-141004015756-conversion-gate02/85/Introduction-to-malwares-2-320.jpg)