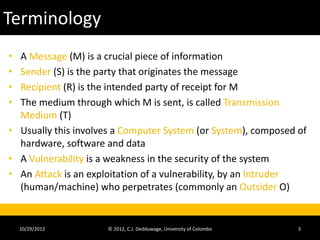
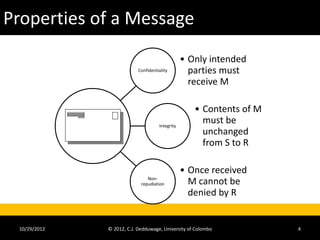
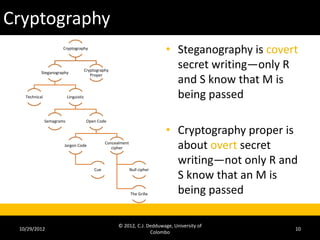
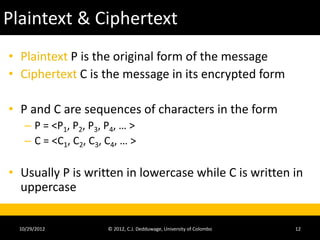
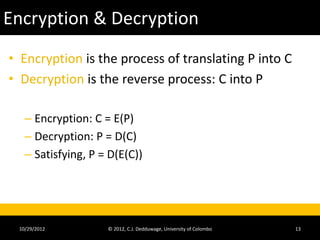
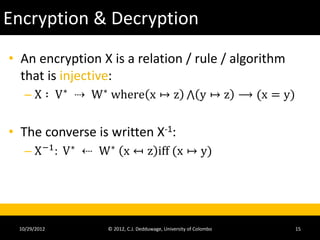
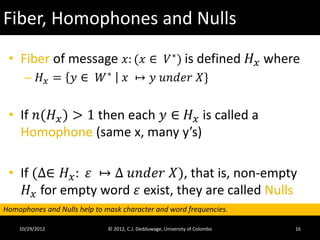
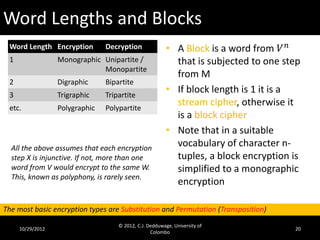
The document provides an introduction to cryptography and cryptanalysis. It defines basic terminology like plaintext, ciphertext, encryption, and decryption. Encryption is the process of translating plaintext into ciphertext, while decryption is the reverse process. The document also discusses concepts like character sets, keys, alphabets, word lengths, blocks, and the requirements for a successful cryptanalysis attack. The overall document serves as a high-level overview of cryptography fundamentals and concepts.