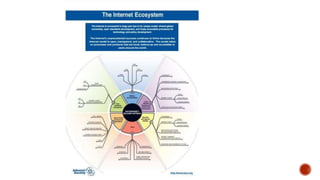
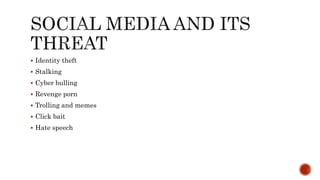
The document discusses the internet as a global network of interconnected computers and describes the internet ecosystem, which includes organizations and communities that support its functionality and evolution. It also highlights various online threats and issues such as identity theft, cyberbullying, and online violence against women. Additionally, it introduces programs like ICANN's Next Generation program and Asia Pacific Internet Governance Academy aimed at educating and involving youth in internet governance and related topics.