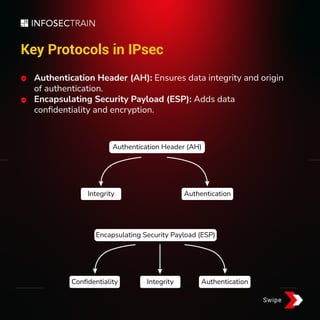
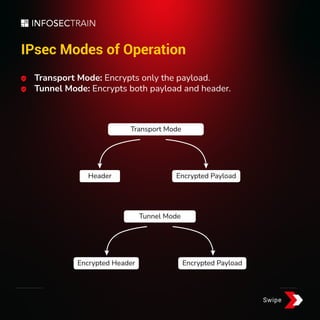
Internet Protocol Security (IPsec) is a set of technologies that ensures the safety and privacy of online data through authentication, integrity, and confidentiality. It utilizes protocols like IKE for mutual authentication and Diffie-Hellman for key negotiation, with two primary modes of operation: transport mode and tunnel mode. IPsec is commonly used in VPNs for secure remote access and protection against network attacks.