Embed presentation
Downloaded 279 times


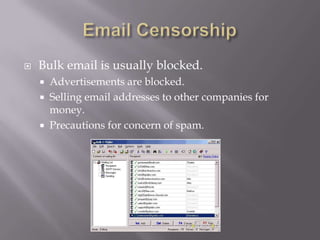


The document discusses different forms of censorship that occur online. It addresses censorship on Facebook regarding users' news feeds and personal information. It also discusses censorship of inappropriate images on Facebook. Next, it discusses censorship of emails, including spam blocking programs, government access to personal accounts, and concerns over privacy. Finally, it discusses censorship within Google, including issues in China and balancing values with profits. The challenges of censorship on YouTube are also mentioned.










