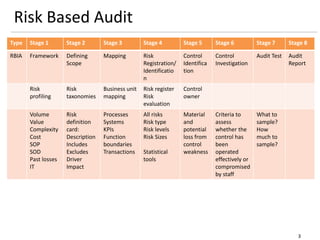
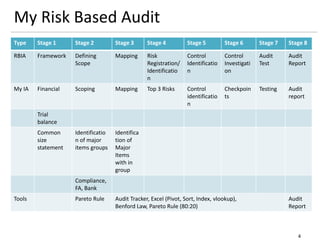
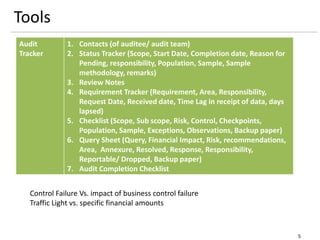
The document outlines a framework for a risk-based audit (RBA) approach, detailing stages from defining scope to producing audit reports. It emphasizes the importance of identifying material risks and controls, utilizing various sampling and testing techniques, and documenting findings effectively. Key components include mappings, risk evaluations, and audit tracking tools to assess control effectiveness and ensure comprehensive evaluations.