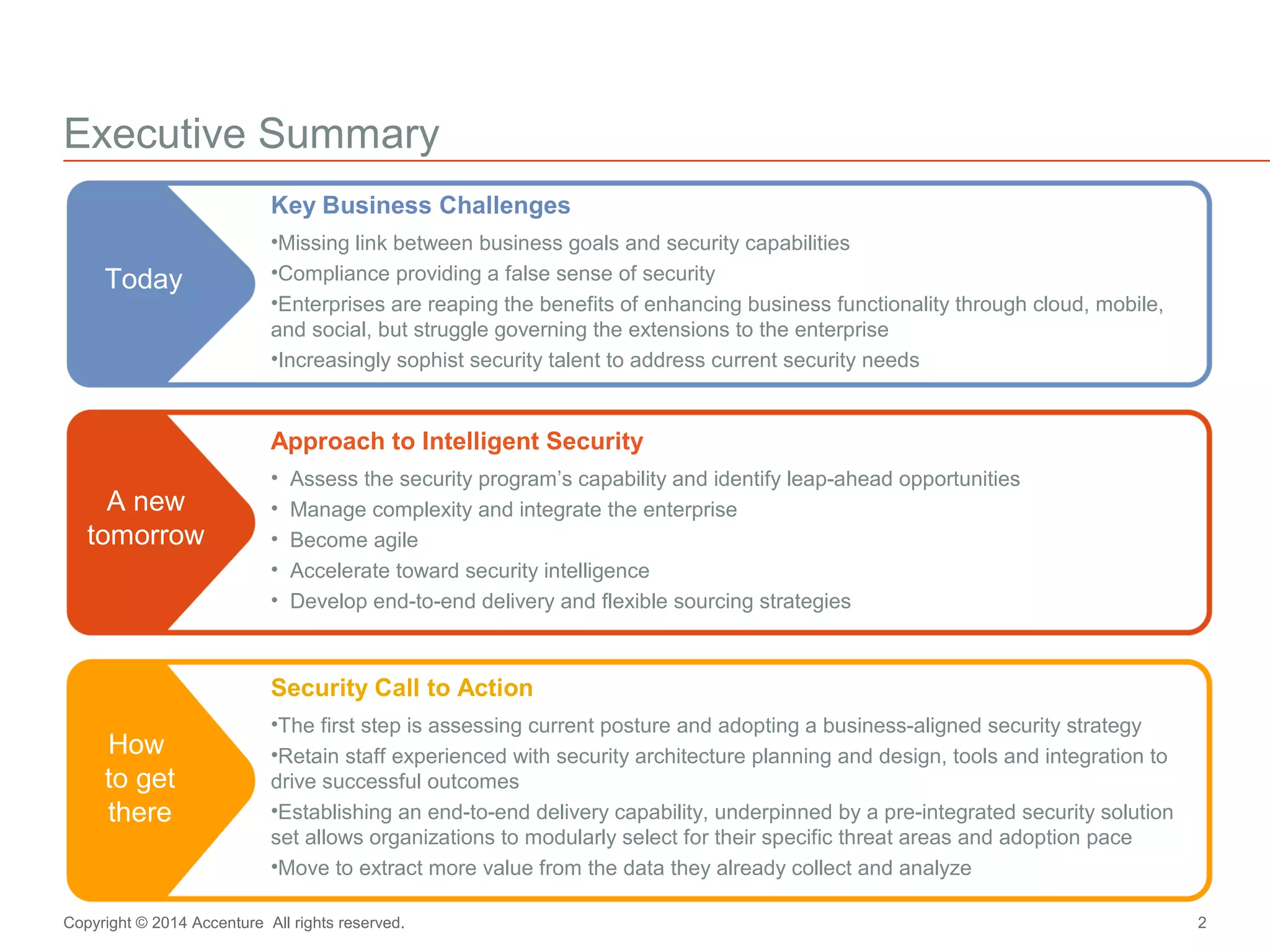
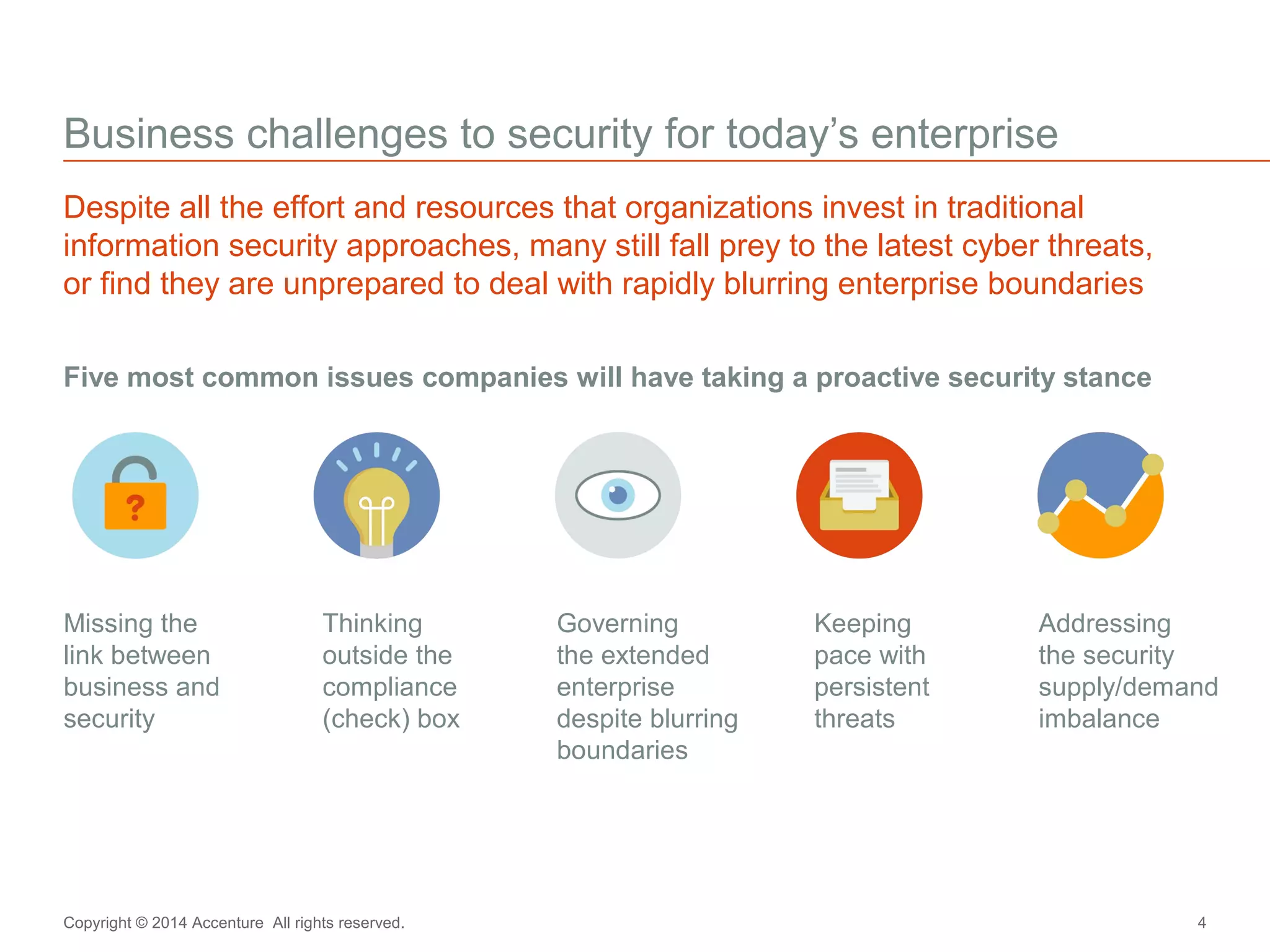
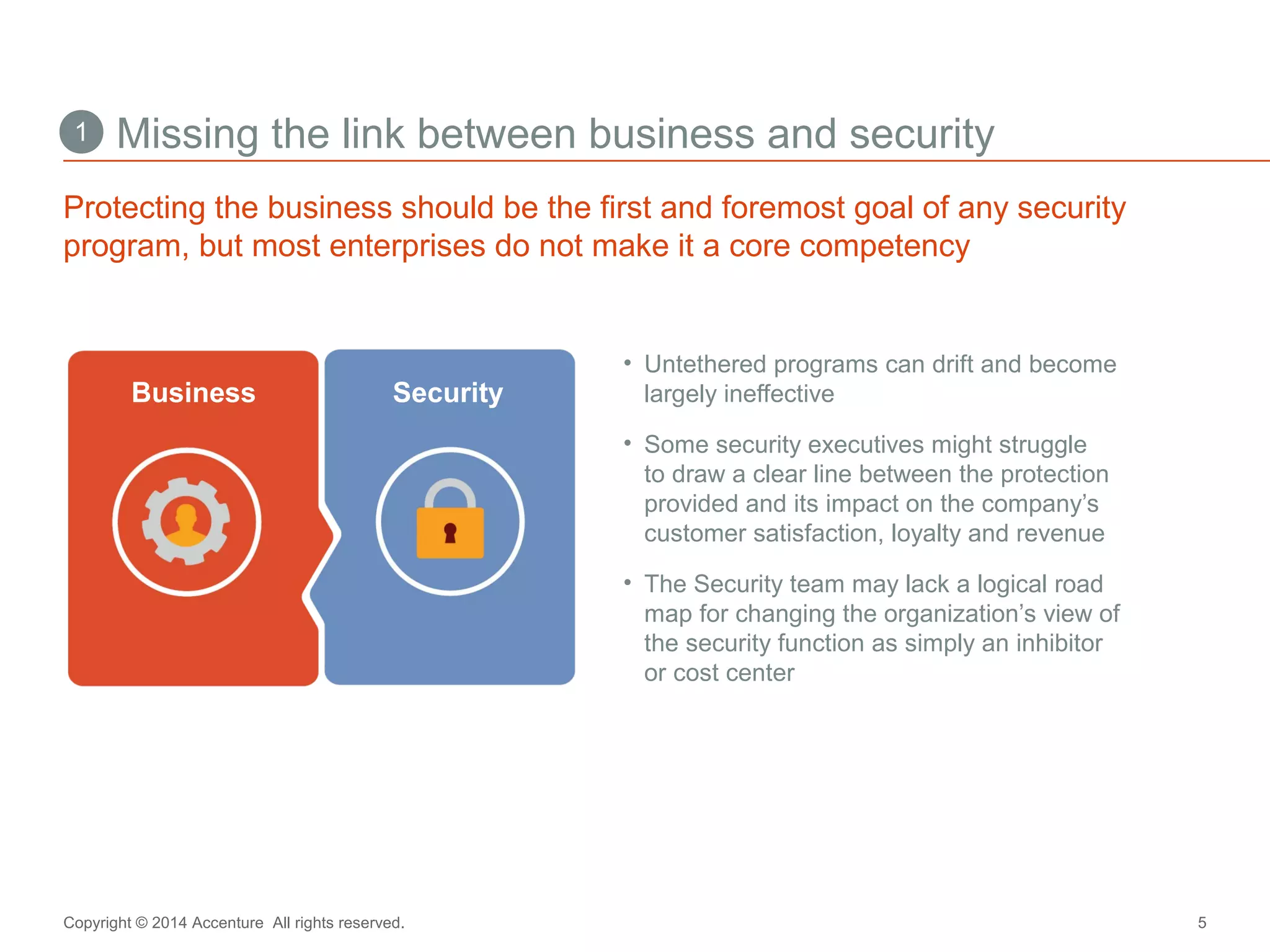
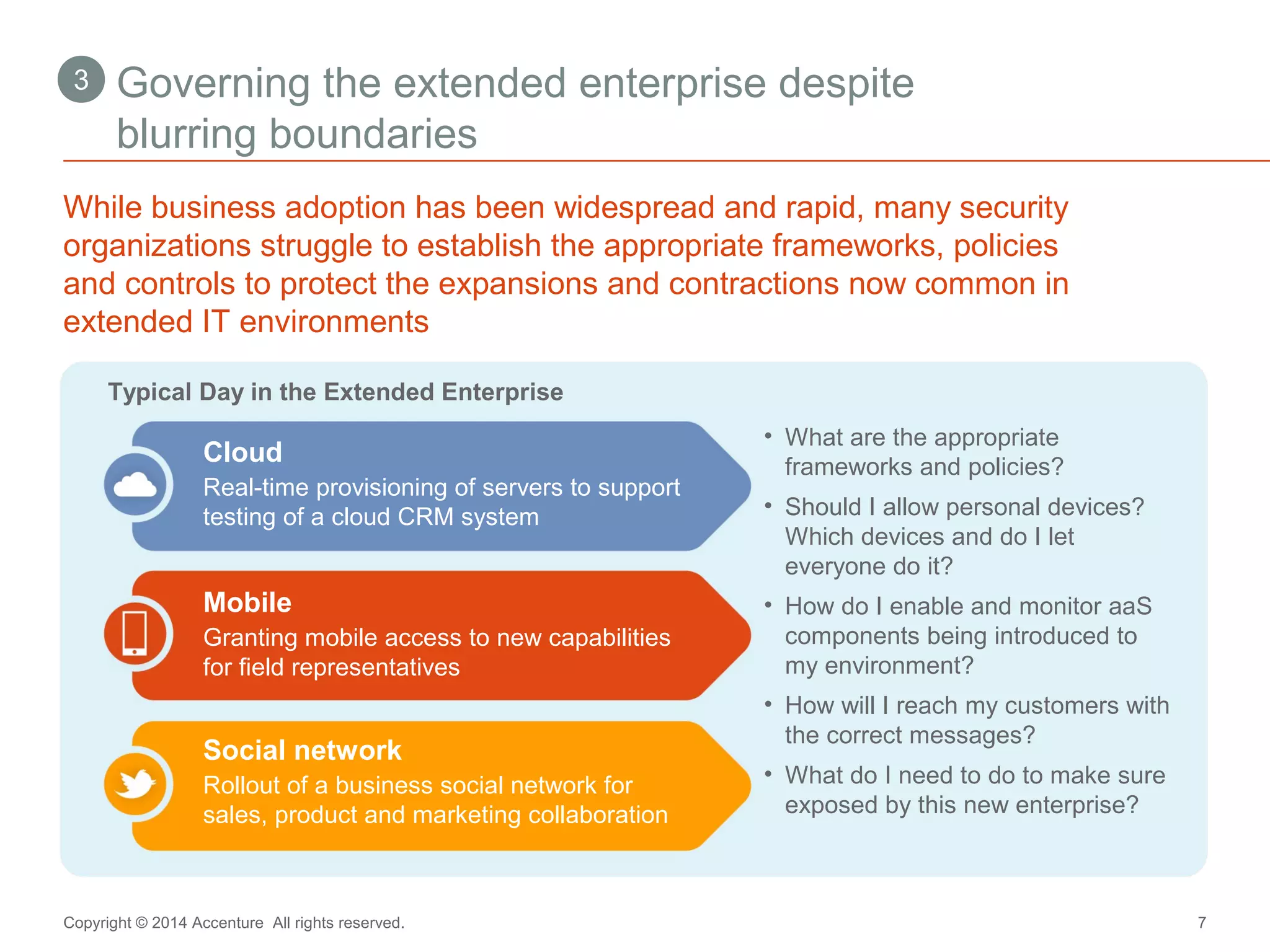
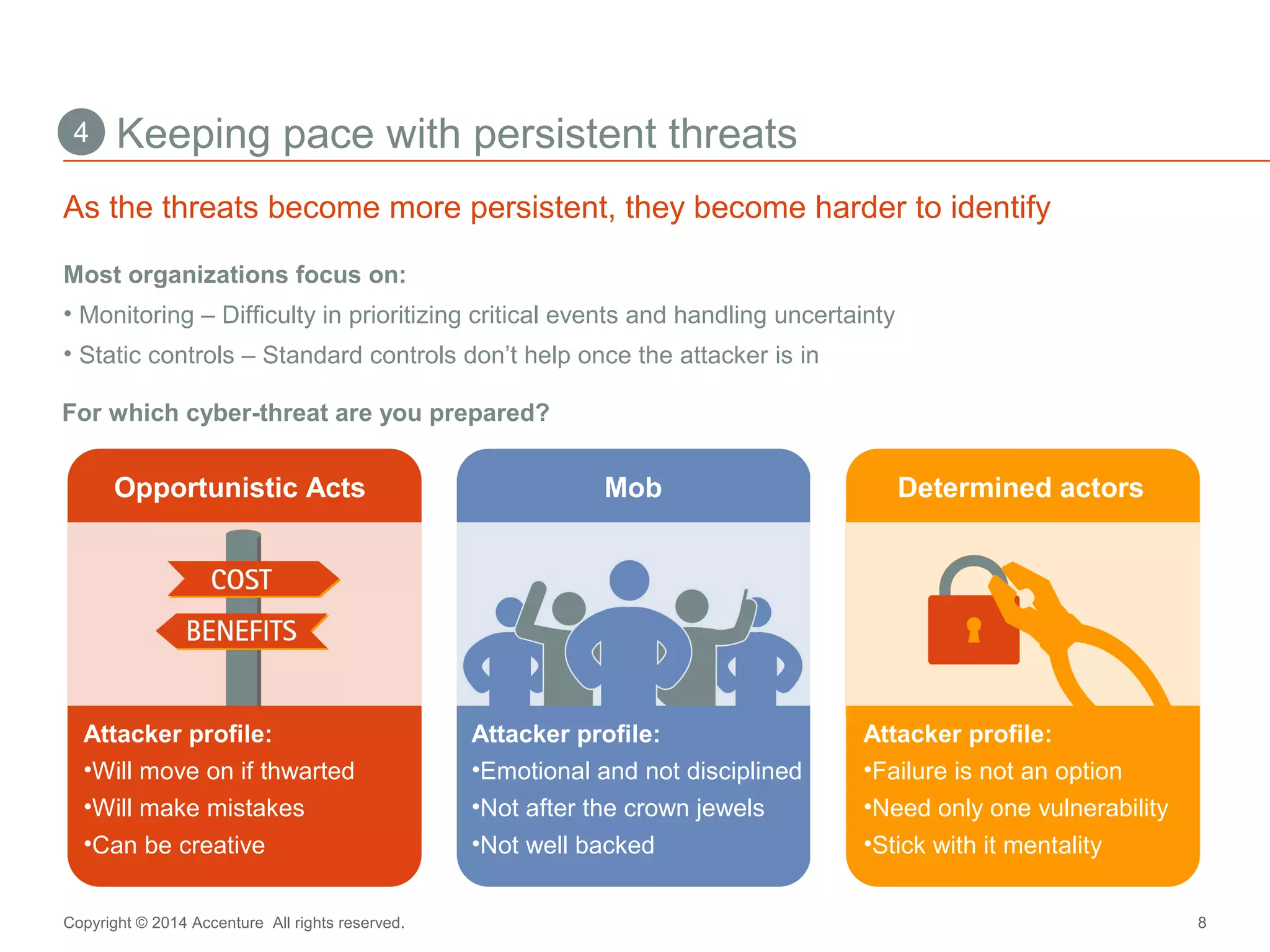
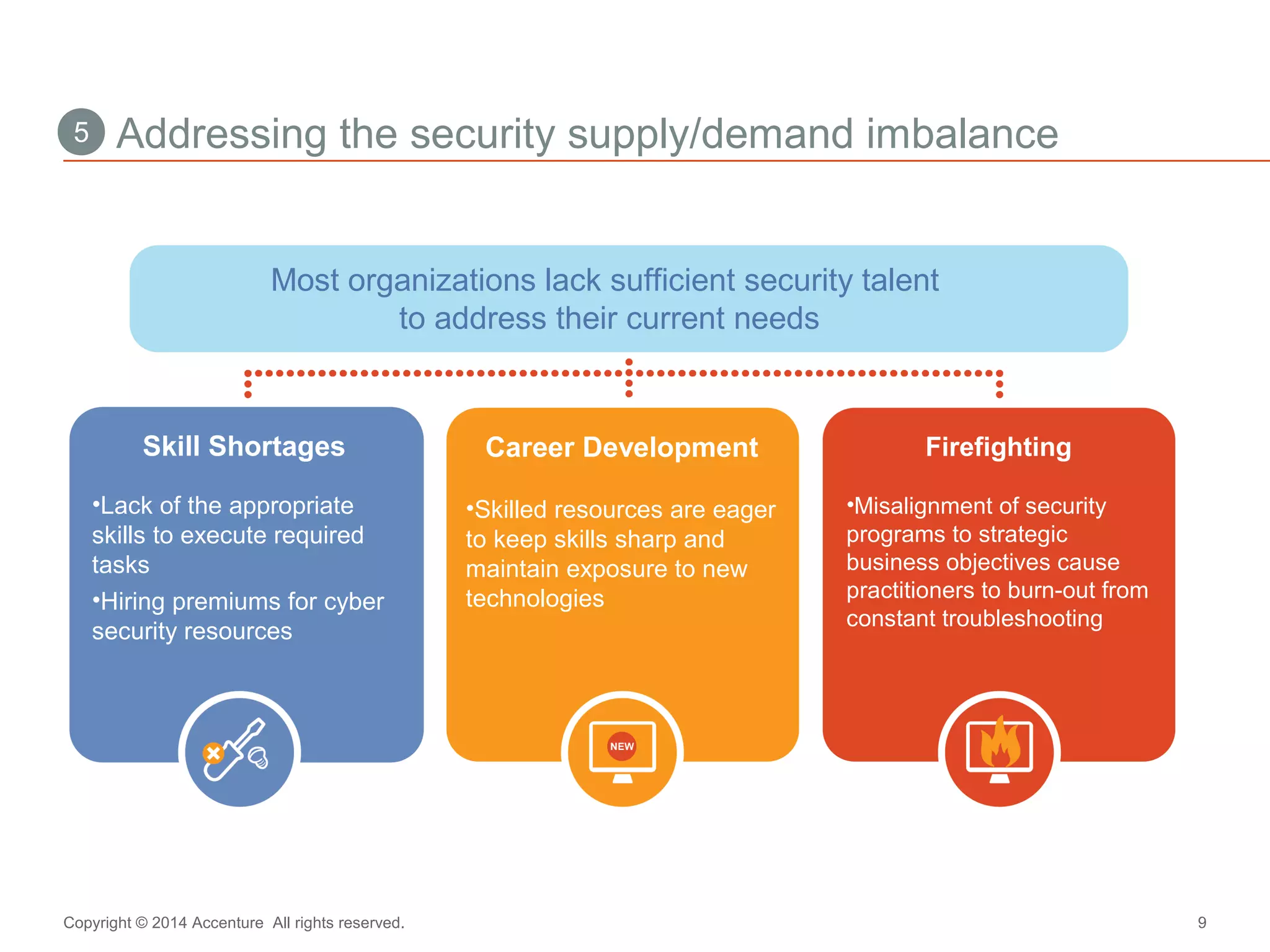
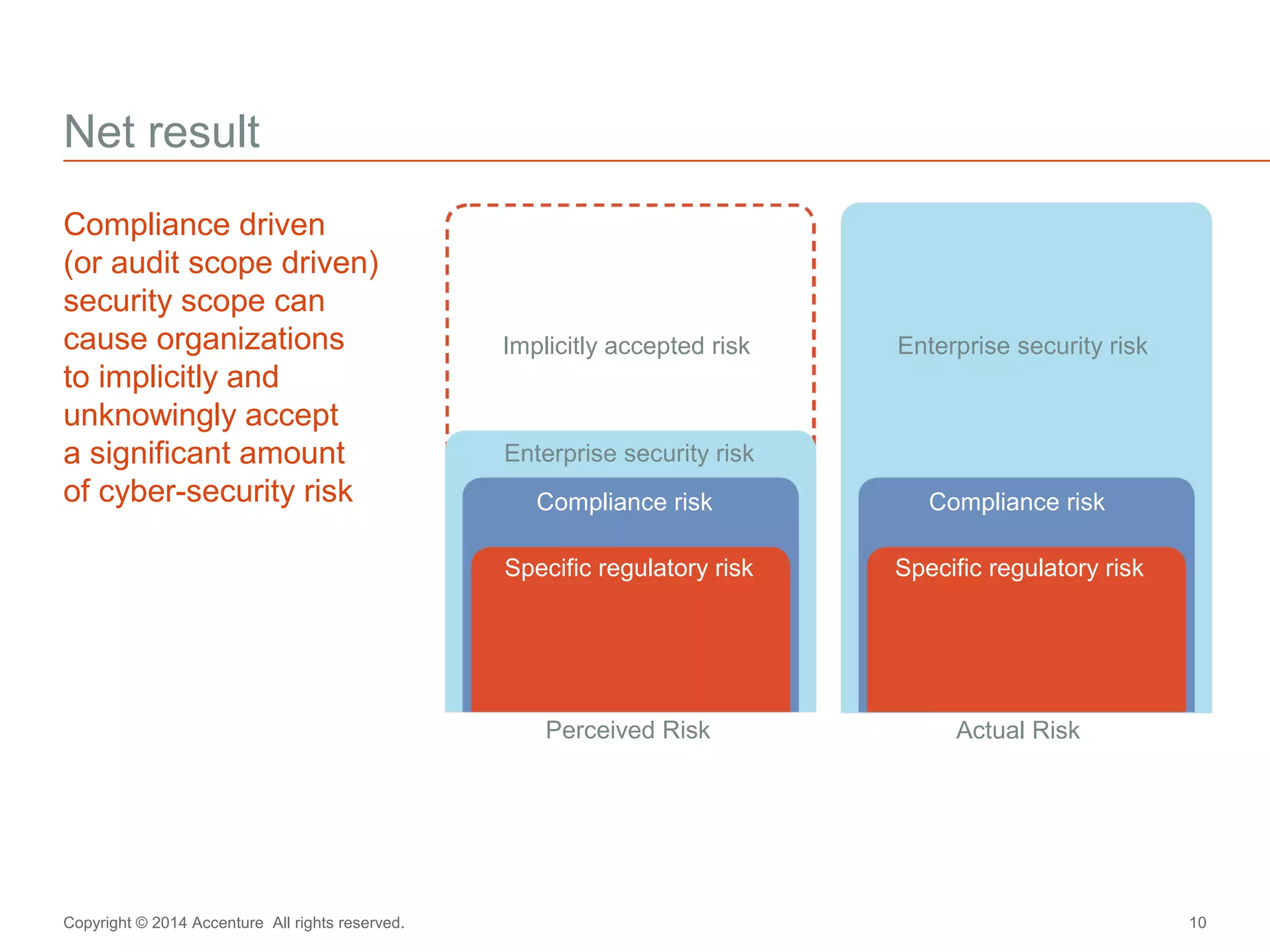
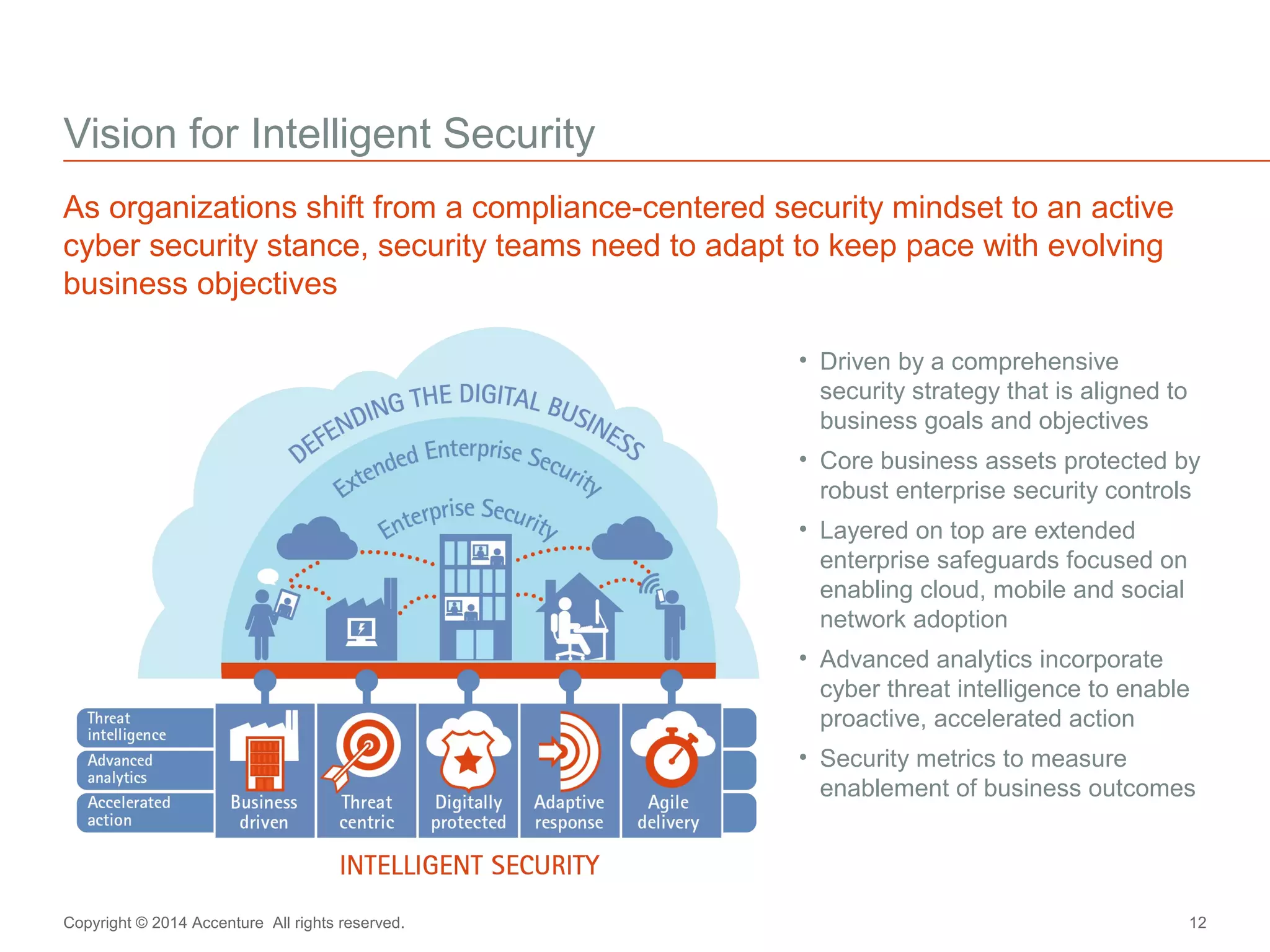
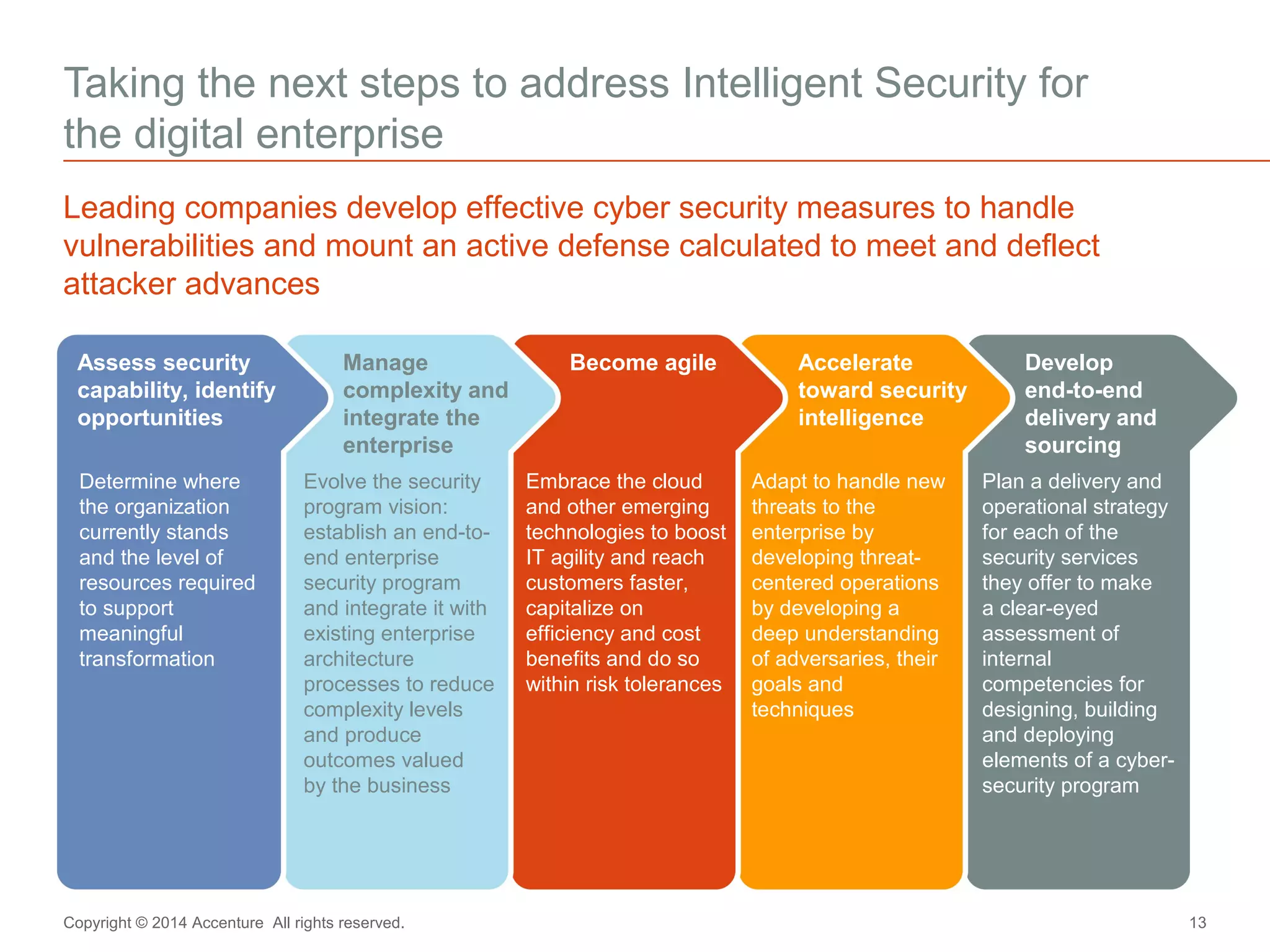
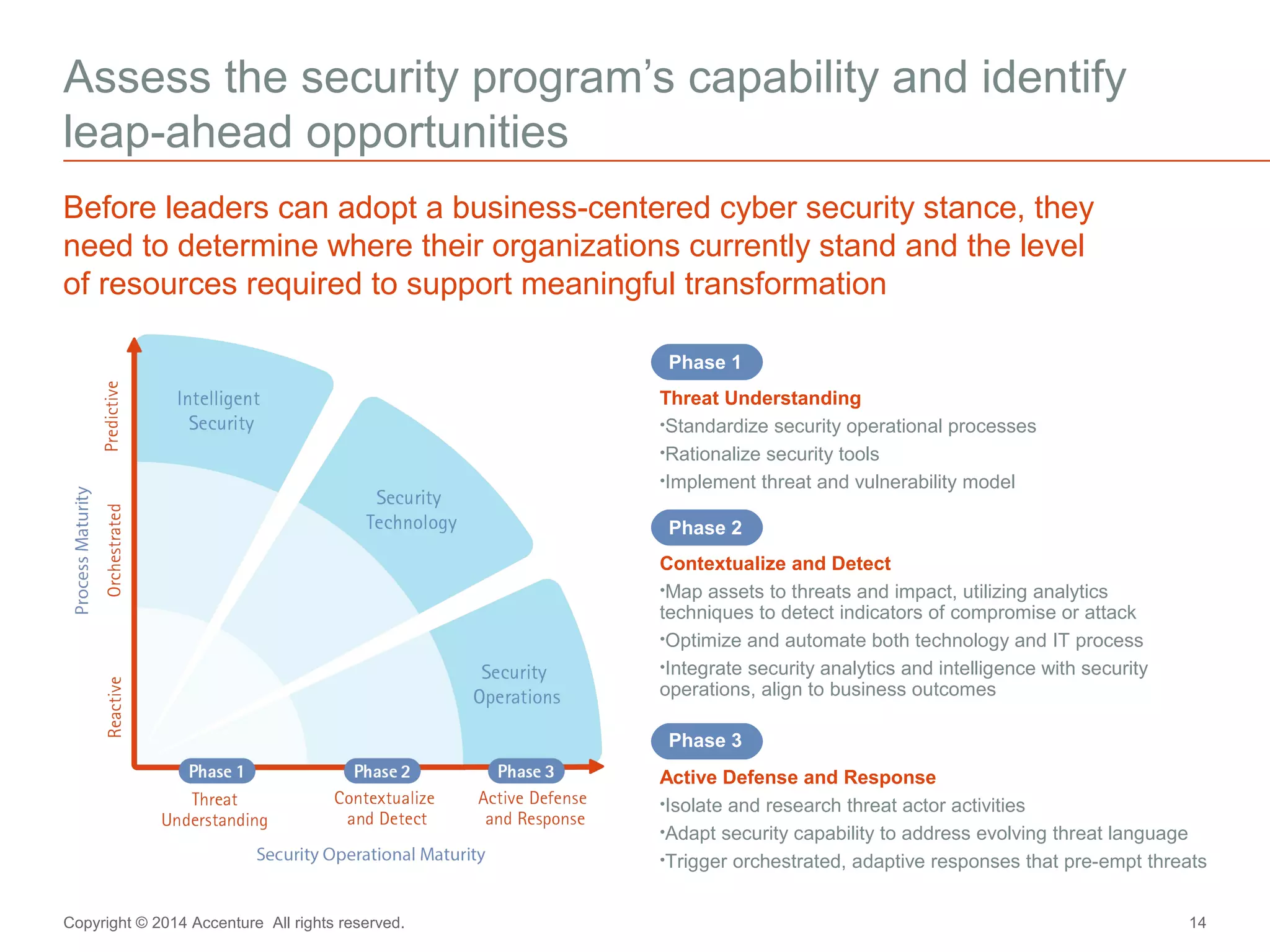
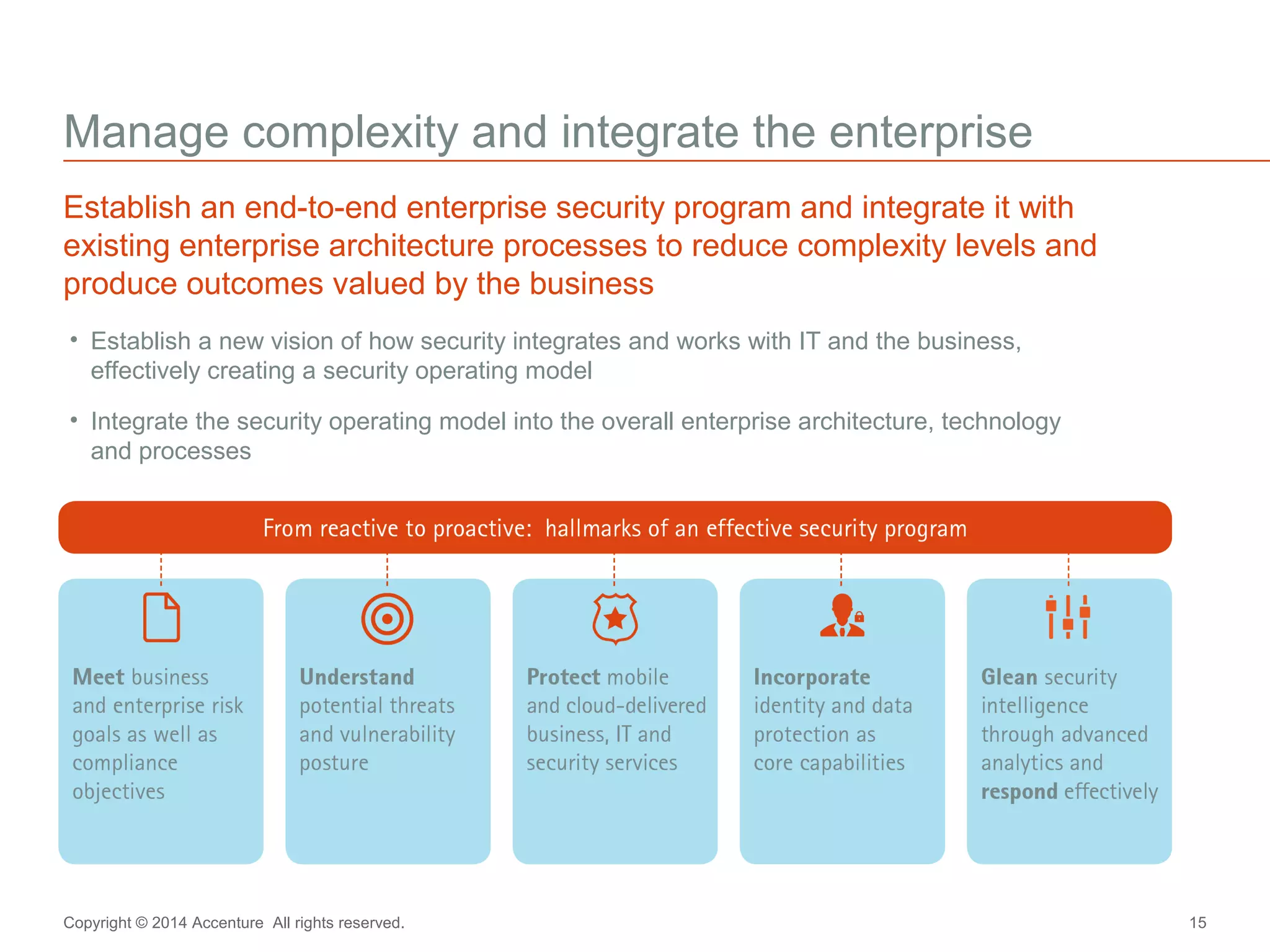
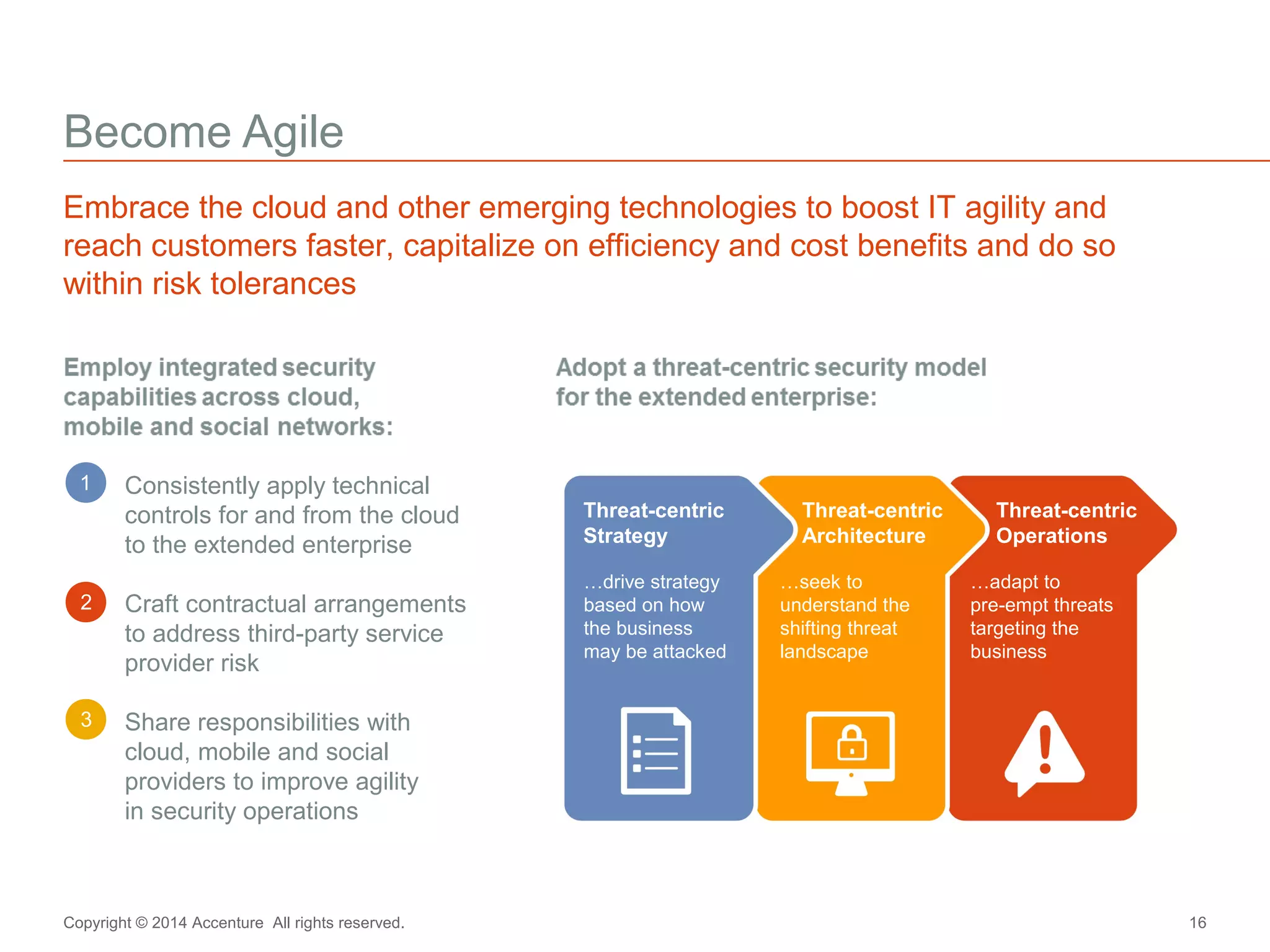
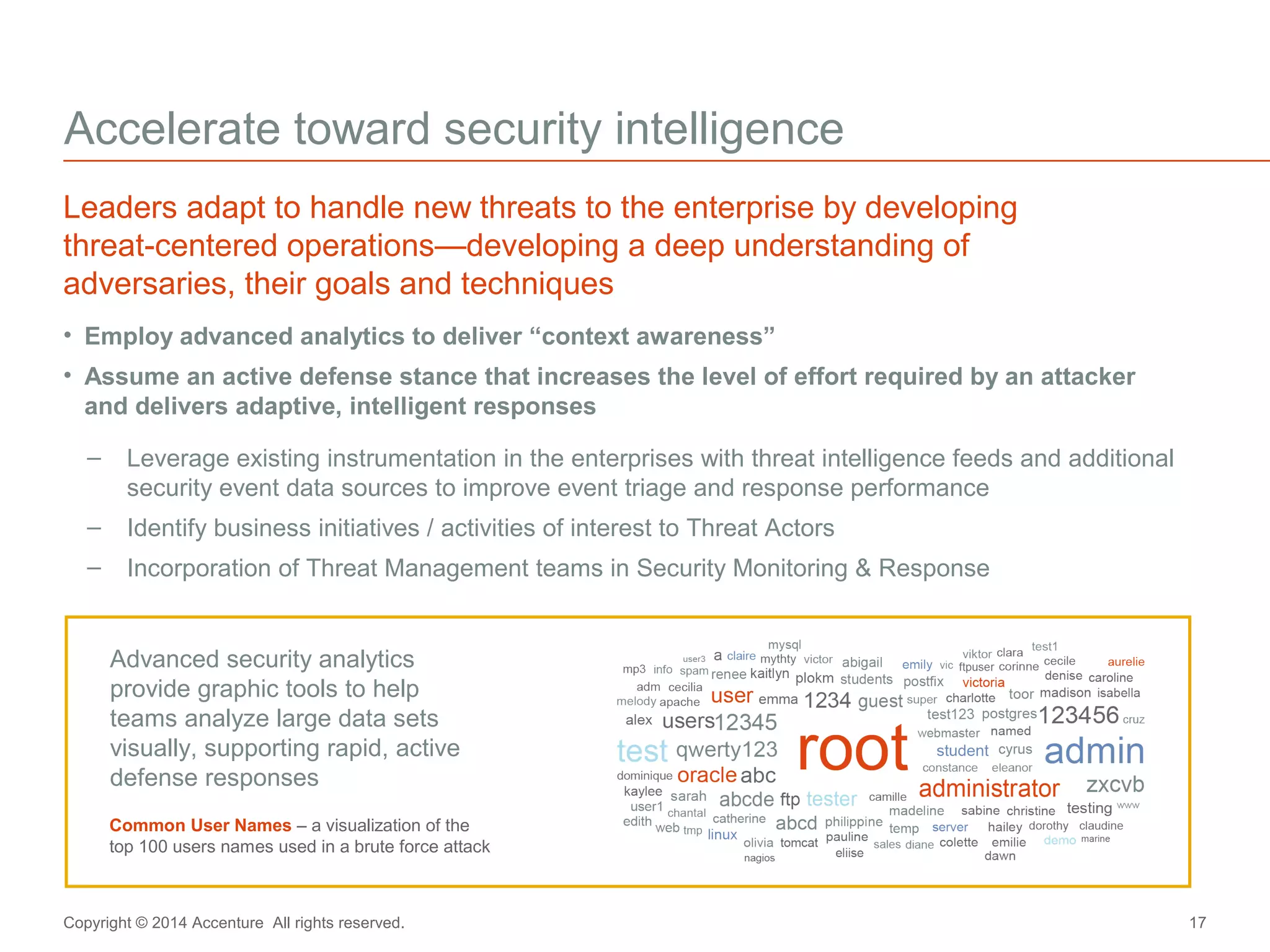
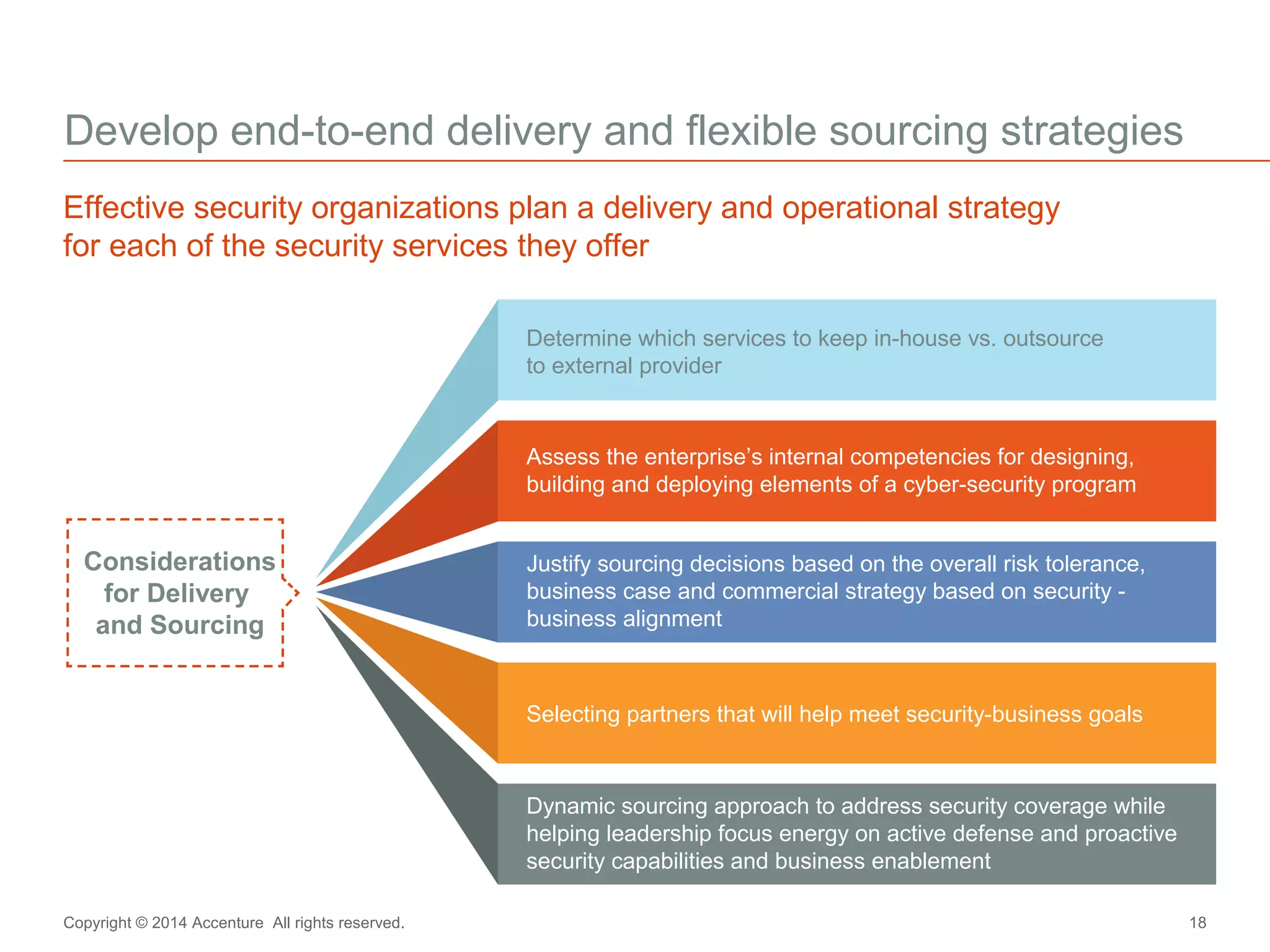
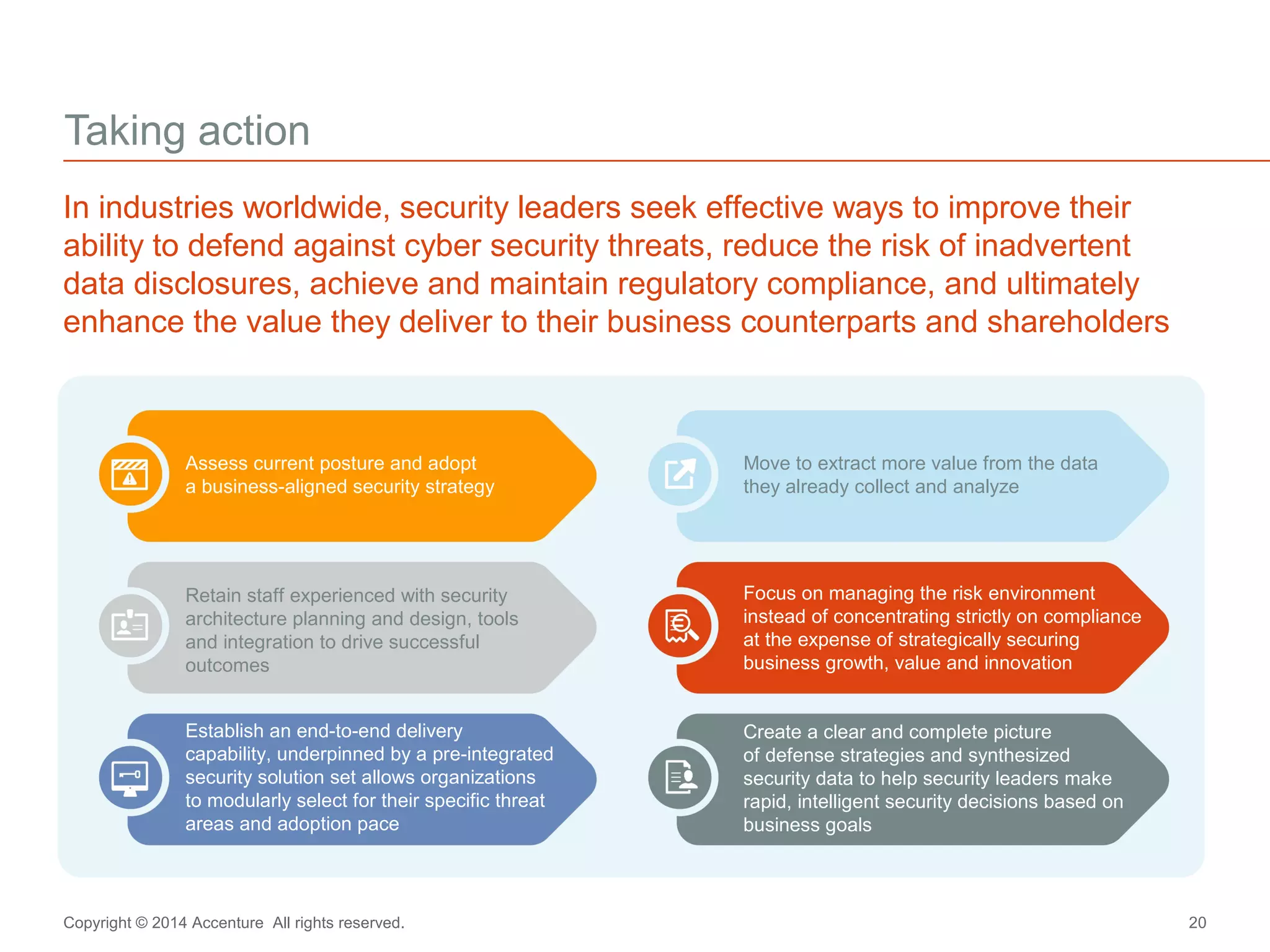
The document discusses key business challenges related to cybersecurity and proposes an approach to intelligent security. It identifies challenges such as a missing link between business goals and security capabilities, difficulties governing extensions to the enterprise like cloud and mobile, and keeping up with persistent threats. The proposed approach involves assessing security capabilities, managing complexity through enterprise integration, becoming agile, accelerating toward security intelligence through threat understanding and detection, and developing end-to-end delivery strategies. The first step is adopting a business-aligned security strategy by assessing the current security posture.