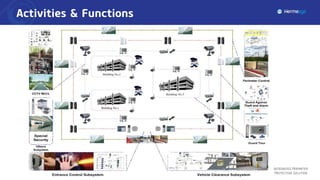
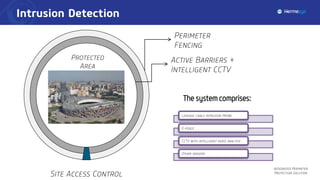
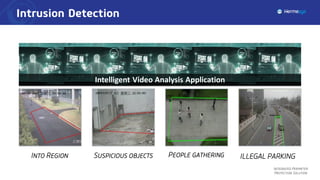
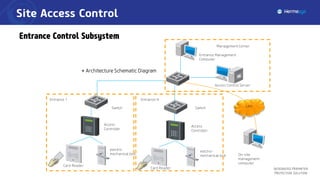
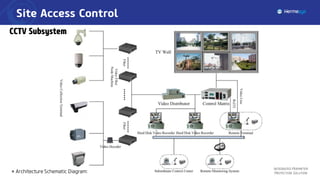
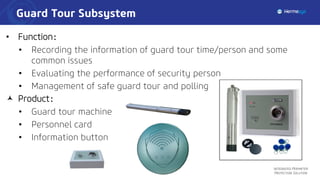
The document describes an integrated perimeter protection solution that includes several subsystems: intrusion detection, site access control, data fusion and recognition, command and control center, and special security subsystems. The solution aims to provide comprehensive perimeter protection through sensors that detect intrusions, control site access using identification and screening, fuse and correlate sensor data to identify threats, enable real-time monitoring and management from a central command center, and utilize mobile surveillance systems.