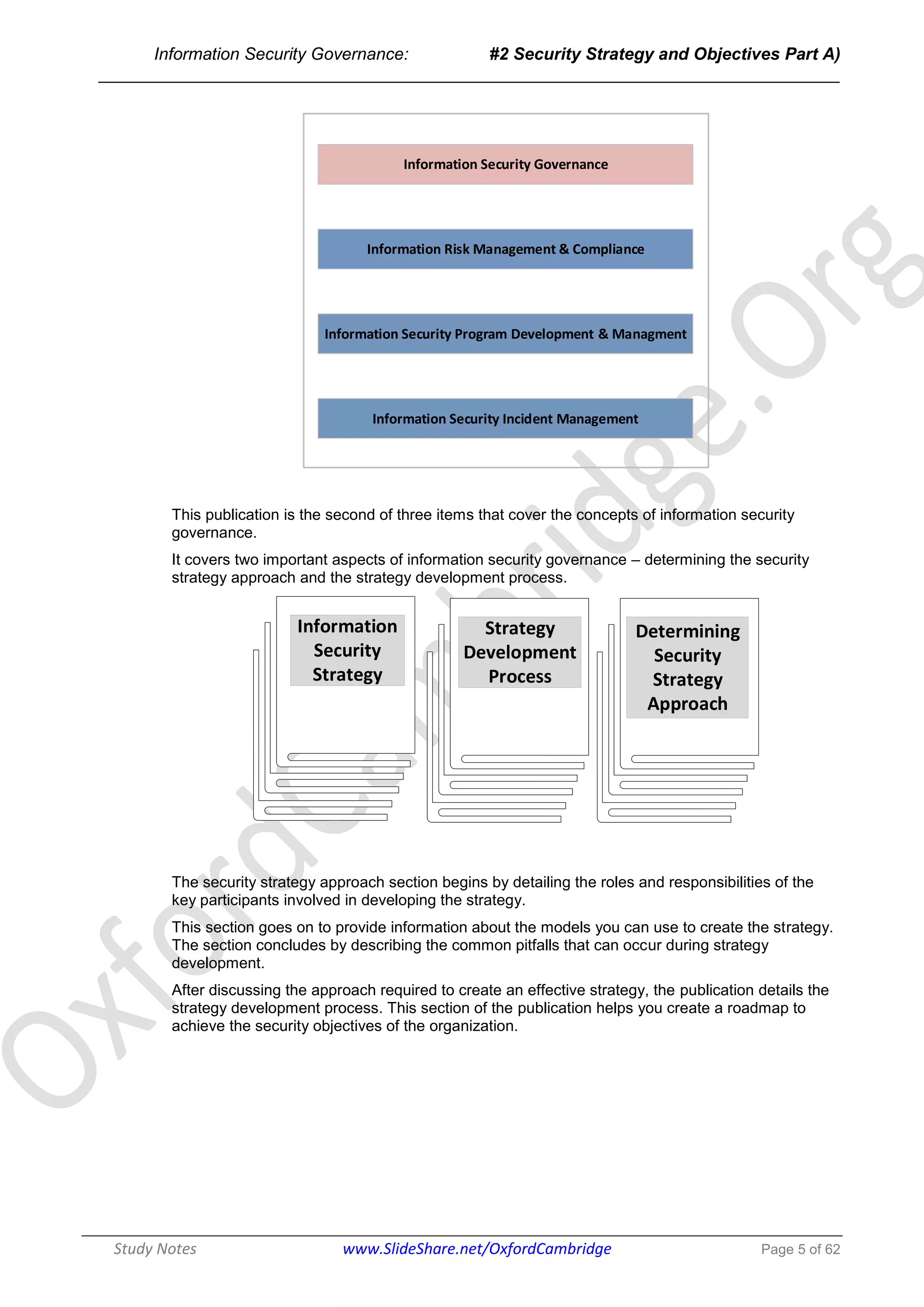
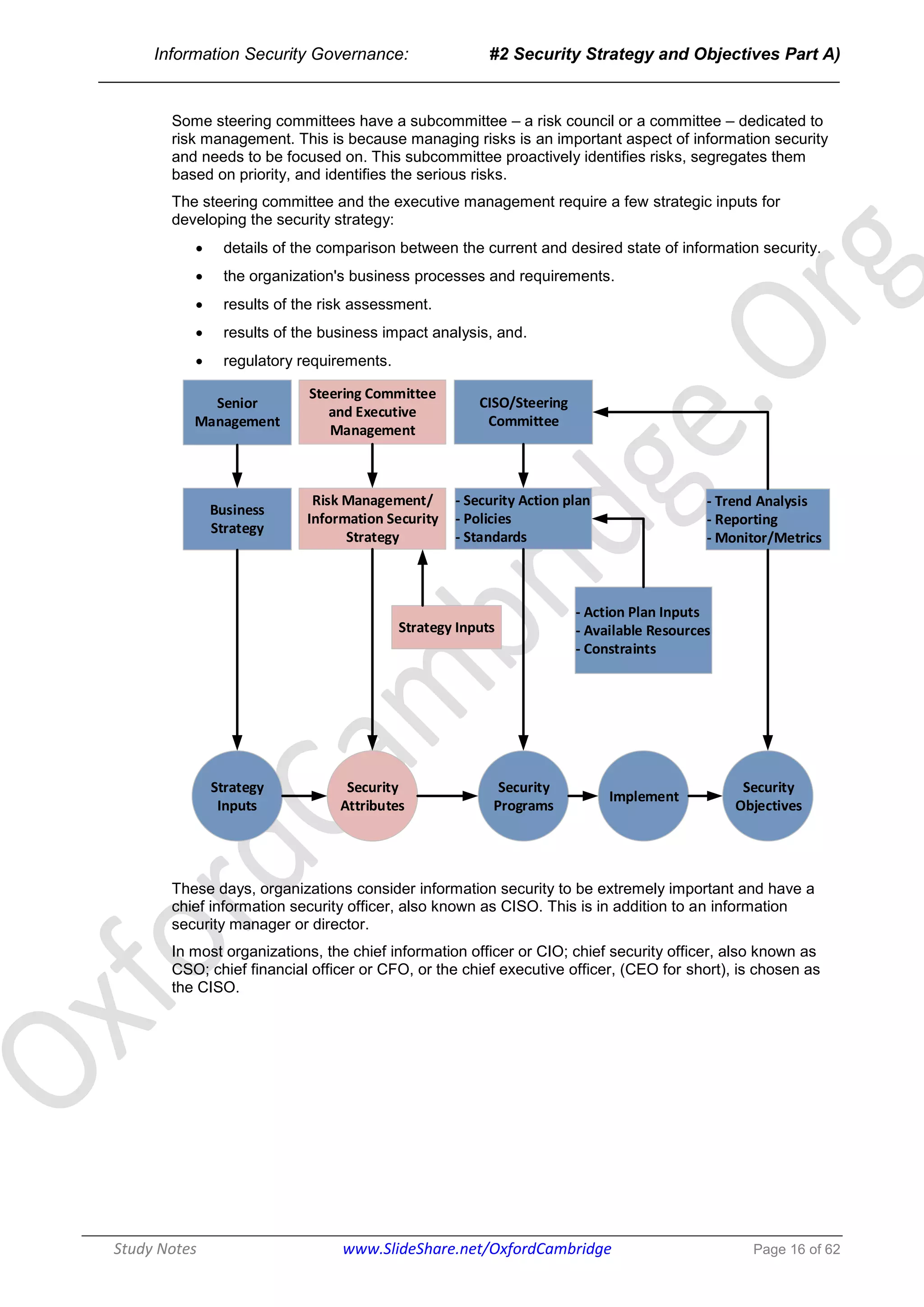
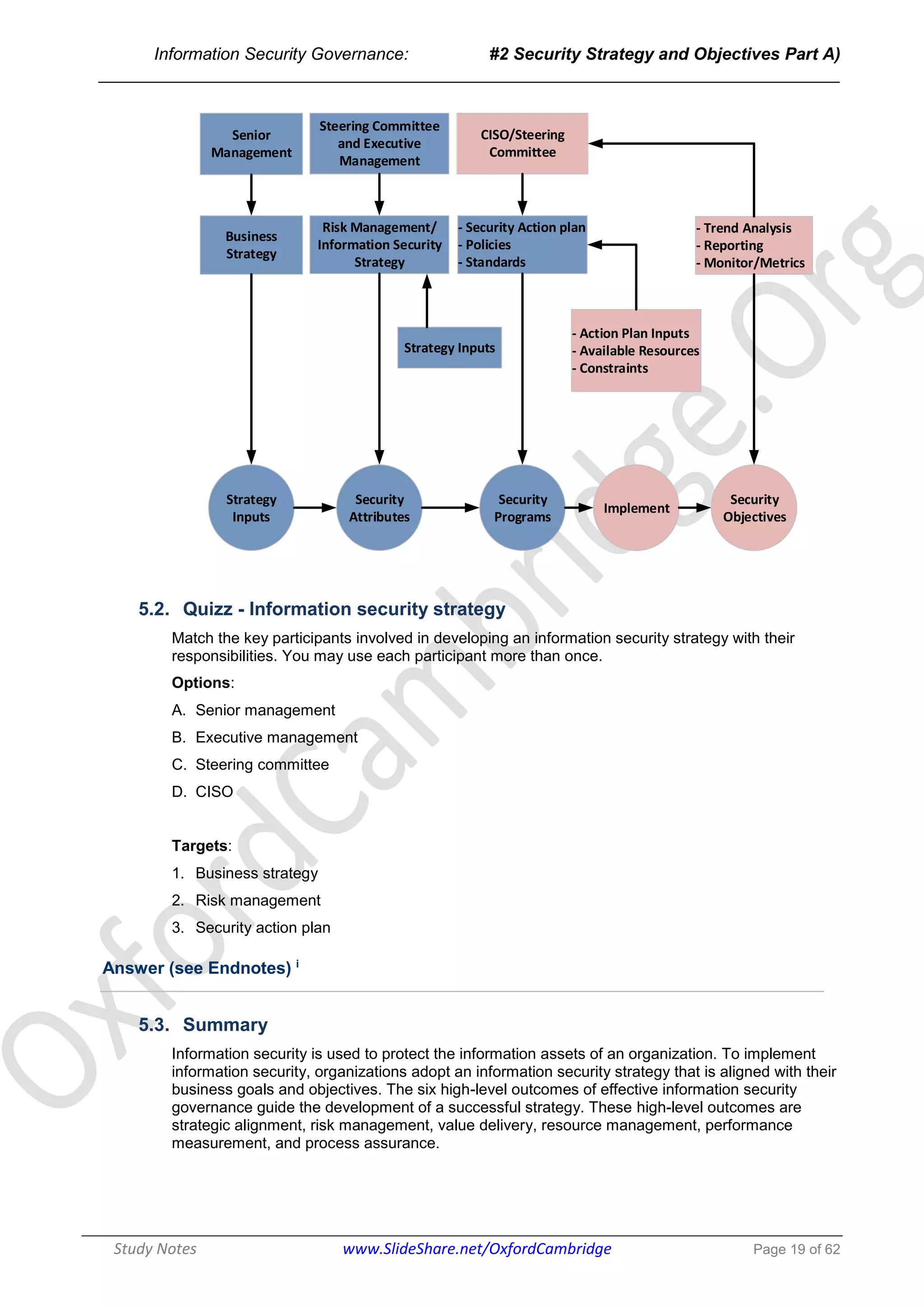
The document discusses the key participants and their responsibilities in developing an effective information security strategy. The three main participants are:
1. The board of directors/senior management who identify critical information assets and ensure strategy alignment with business objectives. Their responsibilities include approving policies and monitoring strategy implementation.
2. The executive management/steering committee who lead strategy implementation, ensure resource availability, and provide communication across stakeholders.
3. The chief information security officer/information security manager who develops security action plans, policies, and standards. They implement security programs and perform monitoring and reporting.
The information security strategy aims to securely protect information assets by aligning with business goals and moving security from its current to desired state through policies