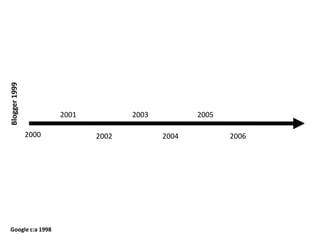
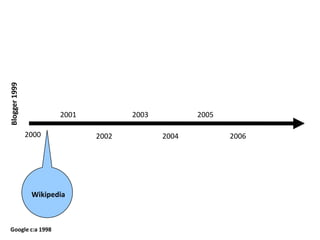
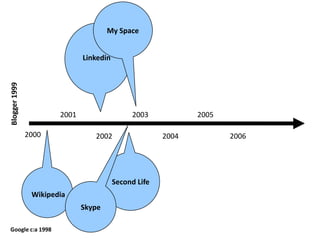
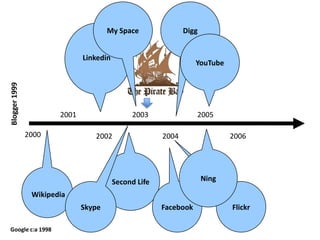
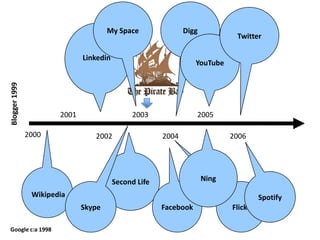
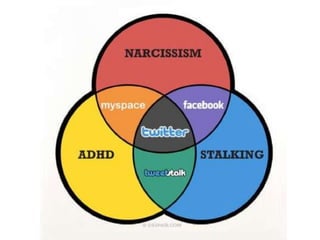
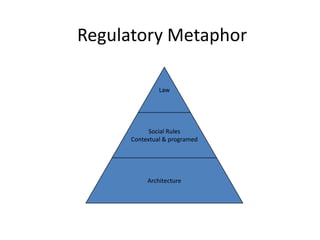
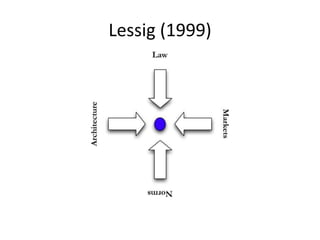
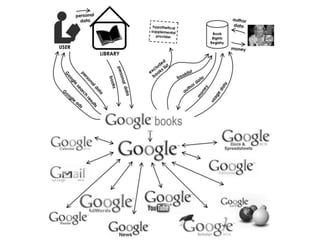
This document discusses the concept of information politics and censorship. It explores how control of information and communication has existed throughout history in various forms. Different arguments around censorship are presented, such as whether censorship is always wrong or if it depends on context. Emerging technologies are changing how information is shared and regulated, disrupting existing power structures. Regulation of technology can effectively be a regulation of democracy.