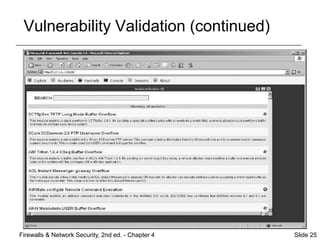
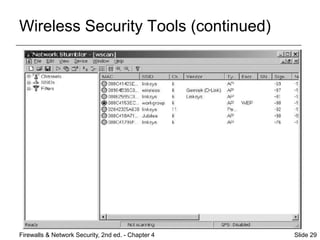
This document discusses tools for identifying network vulnerabilities. It describes common categories of vulnerabilities like defects in software/firmware and weaknesses in processes/procedures. Various scanning and analysis tools are outlined that can detect these vulnerabilities, including port scanners, firewall analysis tools, OS detection tools, vulnerability scanners, and packet sniffers. Regularly using these tools helps network administrators identify and address vulnerabilities before attackers can exploit them.